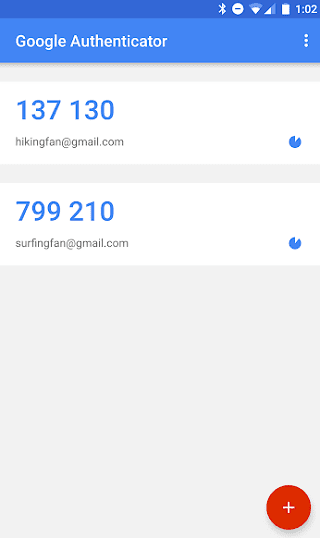
What is 2FA for Microsoft Remote Desktop Gateway (Rd gateway)?
2FA for Microsoft Remote Desktop Gateway The SecSign ID log-in integration into RD Web Access alone only protects the RD Web Access log-in in a browser. A user who knows the necessary details to create an RDP file could log-in directly at the RD Gateway using the Remote Desktop Client.
How to use 2FA (two factor authentication)?
How to Use 2FA 1 Use an RDP file or a Remote Desktop client application to initiate the remote connection. 2 Get an SMS or mobile application 2FA (or MFA) challenge. 3 Verify your identity using the received info, now you are successfully connected to the intended remote system. See More....
What is 2FA and how does it work?
2FA relies on users to have a device with which to authenticate. If that smartphone or laptop is lost or stolen, there’s a heightened risk that unauthorized entities will be able to access your important data.
What is SMS 2FA and how does it work?
SMS 2FA simply sends a confirmation code to a user's mobile phone. Just enter the code and gain access to your information. Speed and access. If suspicious activity occurs, SMS 2FA sends a one-time password (OTP) to a user's device, so only the user with that device can log in and verify that their account hasn't been compromised.
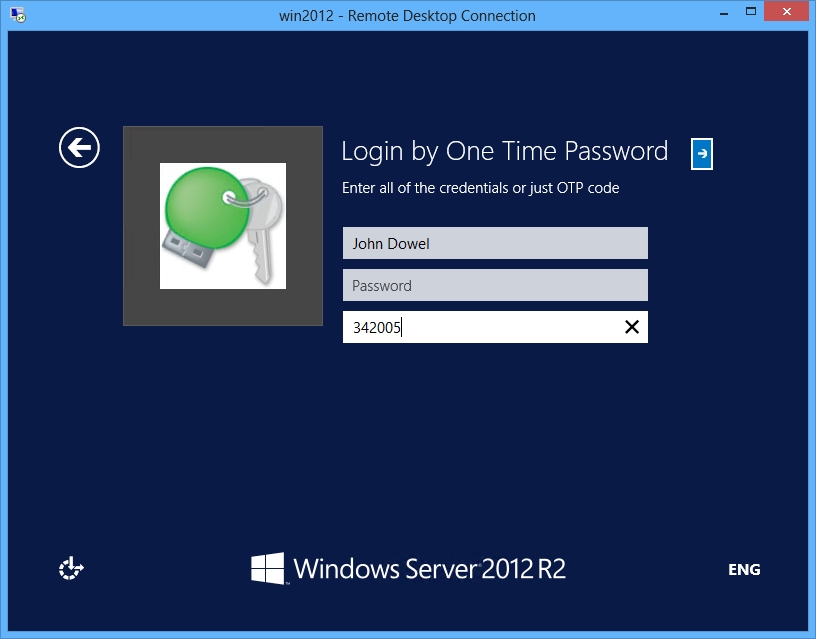
What is MFA remote access?
Multi-factor authentication (MFA) is a more secure access control procedure that combines multiple credentials unique to an individual to verify the user's identity.
Can hackers access 2FA?
A new study says that 2FAs are not safe and are being hacked with no intervention from the user. The attack is known as "Man-in-the-Middle". Two-Factor authentication is considered the most effective security method, but a new study says it may not be as safe as it seems.
How do I enable 2FA on Remote Desktop?
0:331:53Enable 2FA when opening Remote Desktop Manager - RDM Pro Tip 001YouTubeStart of suggested clipEnd of suggested clipAnd head down to options. And in the options menu there's a security tab.MoreAnd head down to options. And in the options menu there's a security tab.
Can you use MFA with RDP?
On the highest level, multi factor authentication can be added on top of RDP by using: A multi factor authentication vendor/product such as Duo Security, OKTA MFA, … and many more; Using an external Identity Provider (IdP) and the MFA services linked to this IdP.
How do hackers get past 2FA?
Bypassing 2FA with SIM-Jacking. SIM-jacking occurs when an attacker takes control of someone's phone number by tricking a mobile phone carrier into transferring the number to their phone. Control over the phone number means the hacker can intercept the OTP sent via SMS.
Can you brute force 2FA?
This lab's two-factor authentication is vulnerable to brute-forcing. You have already obtained a valid username and password, but do not have access to the user's 2FA verification code. To solve the lab, brute-force the 2FA code and access Carlos's account page.
How do I secure my remote desktop connection?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
Does Windows support 2FA?
Windows Hello for Business Replace your passwords with strong two-factor authentication (2FA) on Windows 10 devices. Use a credential tied to your device along with a PIN, a fingerprint, or facial recognition to protect your accounts.
What is remote desktop Gateway?
Remote Desktop Gateway (RDG or RD Gateway) is a Windows Server role that provides a secure encrypted connection to the server via RDP. It enhances control by removing all remote user access to your system and replaces it with a point-to-point remote desktop connection.
Can hackers bypass 2FA discord?
For some reason, discord user tokens are plaintext, easy to steal, and let hackers bypass 2fa. Discord, your application is becoming a lawless wasteland of phishing and hackers.
How secure is 2FA?
2FA can be vulnerable to several attacks from hackers because a user can accidentally approve access to a request issued by a hacker without acknowledging it. This is because the user may not receive push notifications by the app notifying them of what is being approved.
Does 2FA protect?
Two-factor authentication adds an additional layer of security to the authentication process by making it harder for attackers to gain access to a person's devices or online accounts because, even if the victim's password is hacked, a password alone is not enough to pass the authentication check.
How to use 2FA for RDP ?
Many security-conscious users of Microsoft Remote Desktop Connection believe in using 2FA for RDP. Two-Factor Authentication or 2FA is a powerful authentication method that adds a strong security layer to the traditional login process. In this article, we explain how you can use 2FA for RDP and why it matters.
What is 2FA ?
Two-factor authentication (aka 2FA) is a type of multi-factor authentication. Multi-factor authentication (MFA) is an authentication method in which a computer user’s claimed identity is verified only after successfully providing two or more pieces of evidence required by the authentication mechanism.
What is 2FA?
Two-factor authentication (2FA) is a specific type of multi-factor authentication (MFA) that strengthens access security by requiring two methods (also referred to as authentication factors) to verify your identity. These factors can include something you know - like a username and password - plus something you have - like a smartphone app - to approve authentication requests.
How does 2FA protect against hacking?
2FA protects against this by validating the location and IP of every login attempt after a password has been entered.
What are the Factors of Authentication?
Factors are the pieces of information a user can provide to verify their identity. 2FA is the most commonly used, but there are, in fact, five factors of authentication used by security professionals today.
What Threats Does 2FA Address?
The need for two-factor authentication has increased as companies, governments, and the public realize that passwords alone are not secure enough to protect user accounts in the current technical landscape. In fact, the average cost of data breaches today is over two trillion dollars annually. While 2FA protects against a multitude of threats, the most common threats include:
Why is 2FA important?
2FA is an effective way to protect against many security threats that target user passwords and accounts , such as phishing, brute-force attacks, credential exploitation and more.
Why do social media companies use 2FA?
Social media platforms and agencies use 2FA to protect the personal data of billions of users worldwide. To protect these users, social media companies like Facebook use Duo’s push-based authentication to shield their developers from hacking attempts when working on the company’s internal networks.
What is the most obvious inherence factor used today?
Inherence factors of authentication verify the identity of a user by using attributes that would belong only to that user. Fingerprint scanning is the most obvious inherence factor used today. Fingerprints are unique to individuals, so many organizations use them as a way to confirm who their users are.
