
How to enable two-factor authentication for the user?
Available authentication methods: OTP applications: Google Authenticator or Yandex. Key Prerequisites: Install and configure MultiFactor Radius Adapter to allow two-factor authentication. The component or Check Point NGFW checks the user's login and password in Active Directory or Network Policy Server and requests the second authentication factor;
What is Remote Desktop Services multi-factor authentication?
Remote Desktop Services - Multi-Factor Authentication. Leverage the power of Active Directory with Multi-Factor Authentication to enforce high security protection of your business resources.
How does multi-factor authentication protect third parties?
One of the benefits of multi-factor authentication is having a layered defense that makes it harder for an unauthorized individual to gain access to any sensitive information, like personally identifiable information (PII) and protected health information (PHI). So, how does this relate to your third parties, vendors, and contractors?
What is MFA for remote access and why is it important?
For example, MFA for remote access should be used in situations that involve relationships between third parties and organizations. For both, MFA is great (and very important) to implement because it is a means of controlling access to a network and keeping sensitive data safe.
What is two factor identification in remote access?
The first one is usually something the user knows – a password for an online account, or the PIN to a credit card. The second factor can be anything the user has or is – a text to a device, a physical card, a fingerprint, or any of the other options listed above (and more!).
What is the second factor in two-factor authentication?
Two-factor authentication methods rely on a user providing a password as the first factor and a second, different factor -- usually either a security token or a biometric factor, such as a fingerprint or facial scan.
Does RDP support two-factor authentication?
Two factor authentication for Remote Desktop (RDP) and Local Windows Logon. The LoginTC Windows Logon and RDP Connector integrates natively with Windows Server and Windows Client operating systems to add two-factor authentication for both remote desktop and local logins.
What are the two most commonly used authentication factors?
Two-factor authentication (2FA) usually combines a knowledge factor with either a biometric factor or a possession factor, such as a security token or key. In the past, MFA systems have relied on 2FA.
How does a 2 factor authentication work?
Two-Factor Authentication (2FA) works by adding an additional layer of security to your online accounts. It requires an additional login credential – beyond just the username and password – to gain account access, and getting that second credential requires access to something that belongs to you.
What is additional factor of authentication?
The e-mandate framework prescribed an Additional Factor of Authentication (AFA), inter alia, while processing the first transaction in case of e-mandates / standing instructions on cards, prepaid payment instruments, and Unified Payments Interface. Earlier, on recurring payments valuing up to ₹5,000, AFA was waived.
How do I enable 2FA on Remote Desktop?
0:331:53Enable 2FA when opening Remote Desktop Manager - RDM Pro Tip 001YouTubeStart of suggested clipEnd of suggested clipAnd head down to options. And in the options menu there's a security tab.MoreAnd head down to options. And in the options menu there's a security tab.
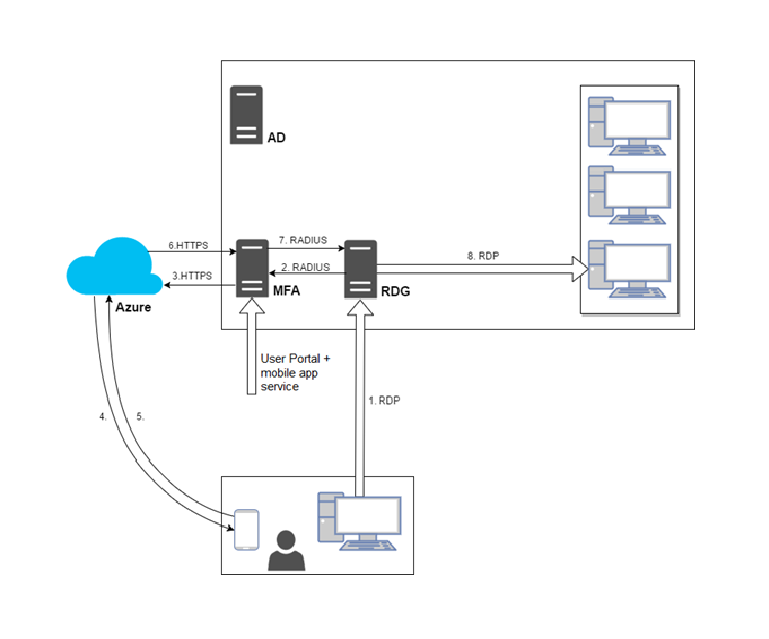
How do I use MFA in Remote Desktop?
Launch a desktop or RemoteApp from an RDP file or through a Remote Desktop client application. Upon connecting to the RD Gateway for secure, remote access, receive an SMS or mobile application MFA challenge. Correctly authenticate and get connected to their resource!
How do I enable MFA on RDS?
To configure integration of Azure AD MFA with RDS, you need to specify the use of a central store.On the RD Gateway server, open Server Manager.On the menu, click Tools, point to Remote Desktop Services, and then click Remote Desktop Gateway Manager.More items...•
What are the 3 factors of authentication?
Three-factor authentication (3FA) is the use of identity-confirming credentials from three separate categories of authentication factors – typically, the knowledge, possession and inherence categories. Multifactor authentication dramatically improves security.
What are the 5 factors of authentication?
Here are the five main authentication factor categories and how they work:Knowledge Factors. Knowledge factors require the user to provide some data or information before they can access a secured system. ... Possession Factors. ... Inherence Factors. ... Location Factors. ... Behavior Factors.
What are examples of two-factor authentication?
Using two knowledge factors like a password and a PIN is two-step authentication. Using two different factors like a password and a one-time passcode sent to a mobile phone via SMS is two-factor authentication.
What is the most commonly used form of authentication?
Passwords are the most common methods of authentication. Passwords can be in the form of a string of letters, numbers, or special characters.
What are the different types of authentication factors?
There are three authentication factors that can be used: something you know, something you have, and something you are. Something you know would be a password, a PIN, or some other personal information.
What are the 3 types classifications of authentication?
There are three common factors used for authentication:Something you know (such as a password)Something you have (such as a smart card)Something you are (such as a fingerprint or other biometric method)
What are the 4 general forms of authentication?
Four-factor authentication (4FA) is the use of four types of identity-confirming credentials, typically categorized as knowledge, possession, inherence and location factors.
Setting up Remote Access VPN in Check Point
Open the Check Point Security Gateway object settings in the VPN Clients/Mobile Access -> Authentication section:
Configure new Access Role
Under objects section select New > More > User > Access Role. Set the parameters for the new object and specify the source of user data.
Configure Access Policy
Under Security Policies > Policy > create a new policy for Remote Access VPN users to access the internal network:
Why does biometric verification fail in the movie?
Biometric verification fails in these movies because it was used as the only factor.
Is a debit card a multifactor authentication?
A debit card is a relatively basic example of multi-factor authentication, but the principle should be used in both your personal and professional life. For example, MFA for remote access should be used in situations that involve relationships between third parties and organizations.
What are the third parties that send OTPs?
First, there are the internet protocols, wireless networks, and email service providers that deliver the OTPs, and then there are the various third parties that messages can be relayed through (SMS middleware, telephone companies, mobile OS companies, VOIP companies, internet service providers, app authors, and so on).
Can OTPs be read by multiple devices?
Finally, the OTPs can be delivered to multiple devices (phone, computer, smartwatch, tablet, and so forth) and accessed and read by multiple apps on each device. The more links in the chain, the more points of weakness there are to exploit.
Is OTP 2FA?
Additionally, although on-demand OTPs may appear to be 2FA, where the OTP is the “something you know” and the mobile device is the “something you have,” this isn’t necessarily the case. With email and SMS delivery methods, the “something you have” is really “something sent to you.”.
