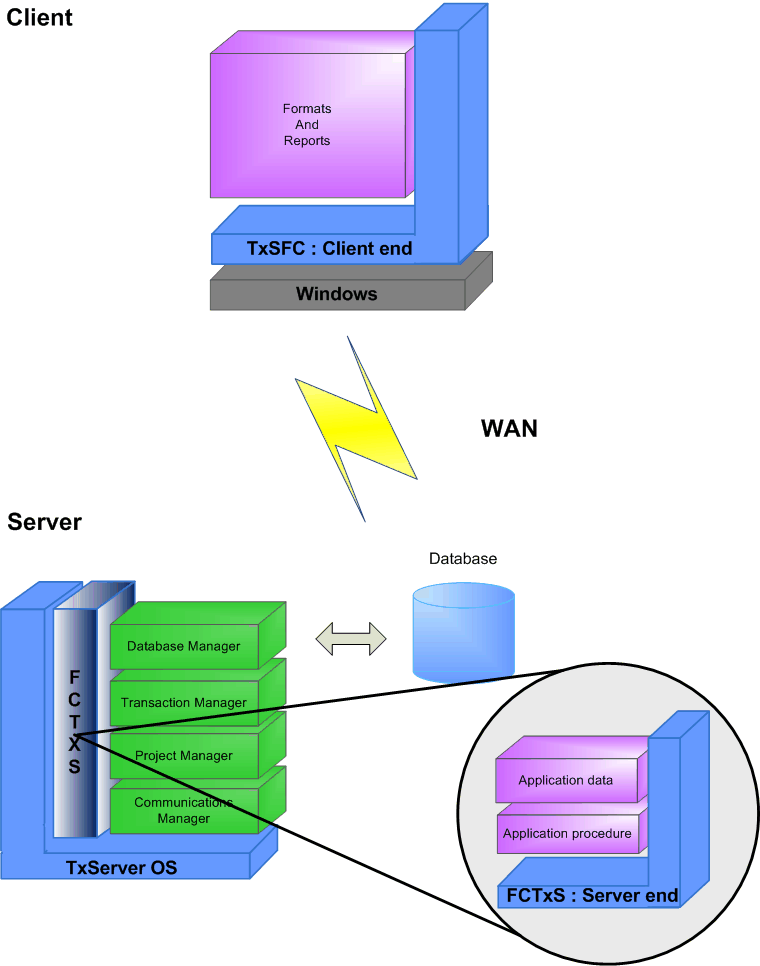
What are the different methods of remote access?
There are some remote access technologies that are widely used, but some new methods have recently emerged that have the ability to change how we work. Let’s look at a few of the common options for secure remote access: A common remote access technology in use today is the IPsec VPN.
How does the remote computer connect to the LAN?
The remote computer will instead use other kinds of connection methods to connect to the LAN, including the following: Public Switched Telephone Network (PSTN, also called plain old telephone service, or POTS) Other digital connection methods (including one of the digital subscriber lines, or DSLs, broadband cable, and T-series connections)
How do I connect to a remote access server without a script?
If you don’t use a script, you’ll need to establish the connection and then open a terminal window so you can manually log in to the remote access server. PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up).
How to protect your network from remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly. Adopting two-factor authentication for remote access through VPN further boosts your network security.
Why is POTS a popular remote access connection method?
Why is remote access not part of my network?
How many channels are there in an ISDN line?
How to connect a cable modem to a computer?
How to connect Ethernet to modem?
What is the name of the service that runs from your house to the rest of the world?
See more
About this website

What are remote access methods?
Remote access control refers to the ability to monitor and control access to a computer or network (such as a home computer or office network computer) anywhere and anytime. Employees can leverage this ability to work remotely away from the office while retaining access to a distant computer or network.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What is the most common form of remote access?
remote access virtual private network (VPN)One common method of providing remote access is via a remote access virtual private network (VPN) connection. A VPN creates a safe and encrypted connection over a less secure network, such as the internet.
What are two types of remote access servers?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
What is a remote access website?
Remote Web Access is a feature of Windows Servers Essentials that enables you to access file/folders and computers on your network via a web browser from anywhere with Internet connectivity. Remote Web Access helps you stay connected to your Windows Server Essentials network when you are away.
How can I remotely access a computer?
Set up remote access to your computerOn your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What is a VPN connection?
A VPN, which stands for virtual private network, is a service that establishes a secure and private connection to the internet. A VPN creates an encrypted tunnel to protect your personal data and communications, hide your IP address, and let you safely use public Wi-Fi networks.
What is remote access security?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What are different type of servers?
There are many types of servers, including web servers, mail servers, and virtual servers. An individual system can provide resources and use them from another system at the same time. This means that a device could be both a server and a client at the same time.
What are remote services?
What is a Remote Service? A remote service is a process that resides outside of the application server and provides a service to the application. An example of a remote service is a web service, message queue, or caching server.
What are the five elements of a remote access security readiness review?
The review examined cybersecurity at the governance layer and identified five critical pillars key to cybersecurity readiness: culture, people, structure, processes, and resources.
How does Microsoft Quick Assist work?
Quick Assist opens on the sharer's device. The user enters the provided code in the Code from assistant box, and then selects Share screen. The helper receives a dialog offering the opportunity to take full control of the device or just view its screen. After they choose an option, the helper selects Continue.
How do I connect to my work network outside the office?
How does it work?Download your firewall's VPN client software - usually available for free from the vendors website (SonicWall, Checkpoint, WatchGuard, Meraki, etc).Install the software.Enter your organisation's public IP address.Enter your username and password and connect.
What is the preferred method to configure clients to use work folders?
There are several ways to configure clients for accessing Work Folders. Automatic discovery is the most preferred method because it supports devices that are not domain joined. Automatic discovery of the Work Folders URL is based on the email address of the user.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
What is PPP protocol?
PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host ...
What is managed services provider?
As a managed services provider (MSP), you likely already work with remote access protocols on a daily basis. But learning how to best explain the various types of remote access protocols and their advantages and disadvantages to customers is critical in helping them understand your decisions—and why they should trust you and your services.
Can you use a RAS modem on a Windows server?
With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, dial-up only, or a combination of the two. RAS can only provide LAN access to remote users. It doesn’t let LAN users use the modem to, for example, dial their AOL account.
Is RDP the same as ICA?
RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients only, while ICA can provide access for numerous platforms. ICA also offers support for automatic client updates, publishing an app to a web browser, and more.
What is remote access?
In fact, Remote access is simply the ability to access a computer or network, at home or in an office, from a remote location. Remote access connection allows users to access a network or computer remotely via an internet connection or telecommunications. This post is dedicated to secure remote access.
What is remote desktop connection?
Remote Desktop Connection (RDC) is a Microsoft technology that allows a local computer to connect to and control a remote PC over a network or the Internet. The host computer can see and interact with the target computer through the target computer’s actual desktop interface—allowing the host user to see exactly what the target user sees. It is done through a Remote Desktop Service (RDS) or a terminal service. Microsoft Windows, Linux, and MacOS have the software available that allows for remote desktop access.
What is remote assistant?
The remote assistant can be considered a subset of the remote desktop. When you connect to another computer using the remote desktop, the current user of that computer is forced to sign-out. In other words, if an employee asks you for help with a problem and you use a remote desktop to connect to his computer, it is not possible for both of you to be able to view the desktop at the same time and do the necessary work. In terms of technical support, this is a huge problem. To solve this problem, remote assistant technology was introduced. In remote assistant, technical support person and an employee with a problem are able to connect to a computer at the same time.
What is remote access technology?
A common remote access technology in use today is the IPsec VPN. A piece of software called a VPN client is installed on the end user’s computer and is configured with details about the target network, such as the gateway IP address and a pre-shared security key. Each time the user wants to connect to the corporate network, they start the VPN client, which creates a secure connection to the corporate firewall.
Is VPN required for telecommuting?
Being able to connect securely to your corporate network from a remote location using a Virtual Private Network (VPN) is important, and it may be required by your job if you are a telecommuter. There are some remote access technologies that are widely used, but some new methods have recently emerged that have the ability to change how we work.
Is DirectAccess going to be widespread?
DirectAccess is not going to gain widespread adoption until the OS licensing requirements are revised and the networking is reworked to be more straightforward. While IPv6 is the future of networking, we currently live and work in an IPv4 world, especially on the LAN (as of May 2014, IPv4 still carried more than 96% of Internet traffic worldwide, according to Google ). Setting up a new remote access technology should not require one or more potentially expensive projects before it can be deployed.
Is there more configuration required on the firewall when setting up the client to be published?
There is more configuration required on the firewall when setting up the client to be published.
Does a firewall include VPN?
When a firewall is purchased, it typically includes plenty of licenses for IPsec VPN connections.
IIoT driving OEM business models
The IIoT has revolutionized the way business owners view their production environment by providing the capability to acquire real-time data from machines and devices in the field so that business owners can efficiently monitor and control production processes.
Challenges using VPN & RDC
Virtual Private Network (VPN) and Remote Desktop Connection (RDC), the latter using Virtual Network Computing (VNC), are two common methods used to remotely access machines and equipment at field sites.
Cloud-based secure remote access
Cloud-based remote access is a new type of remote access solution that enables flexible remote access to field machines. The network topology of a cloud-based remote access solution is composed of three components: remote gateway, cloud server, and client software.
Ease of use
Plug and play remote access without technical configuration. In a cloud-based remote access solution, security parameters, such as the hash functions, encryption/decryption algorithms, etc., are configured automatically.
Flexibility and scalability
Client software isn’t limited to a specific hardware platform. As long as they have an active client account, users can download the client software to any laptop/PC and have remote access from anywhere and at any time.
Conclusion
OEMs and machine builders require a secure, easy-to-use, and scalable remote access solution to enable on-demand remote access to machines deployed in the field. The traditional VPN and RDC solutions are cumbersome and require IT/networking knowledge as well as changes in the security/firewall policies.
Why is POTS a popular remote access connection method?
POTS is a popular remote access connection method because few minor disadvantages are associated with it. The disadvantages are limited bandwidth, and thus a limited maximum data transfer rate, and the inferior analog signal when compared to digital methods, such as ISDN and DSL.
Why is remote access not part of my network?
Because a computer using remote access is not a part of your network, it will not use local area network (LAN) technologies to connect to the network. The remote computer will instead use other kinds of connection methods to connect to the LAN, including the following: Other digital connection methods (including one of the digital subscriber lines, ...
How many channels are there in an ISDN line?
An ISDN line has two types of channels. The data is carried on special Bearer channels, or B channels, each of which can carry 64Kbps of data. A BRI ISDN line has two B channels. One channel can be used for a voice call while the other is being used for data transmissions, and this occurs through time division multiplexing on one pair of copper wires. The second type of channel is also multiplexed onto the one copper pair, is used for call setup and link management, and is known as the signaling channel, or D channel (also referred to as the Delta channel ). This channel has only 16Kbps of bandwidth.
How to connect a cable modem to a computer?
If you are going to connect the cable modem via USB, simply install the software driver for the cable modem on the computer, and then plug in the cable modem. The computer will detect the modem and configure it automatically.
How to connect Ethernet to modem?
If you are using Ethernet to connect, you must have an Ethernet NIC in your computer that is properly installed and configured. Then, once the NIC is installed, all you need to do is connect the cable modem to the NIC with an appropriate 10Base-T patch cable (RJ-45 connector on both ends, usually supplied with the cable modem). The thing to keep in mind is that the cable modem’s Ethernet connection is physically and electronically the same as a medium dependent interface-crossover (MDI-X) port on a hub or switch, meaning that you can connect your computer, which has a medium dependent interface (MDI) to the cable modem with a straight-though cable.
What is the name of the service that runs from your house to the rest of the world?
The portion of the PSTN that runs from your house to the rest of the world is known as plainold telephone service (POTS). It is the most popular method for connecting a remote user to a local network because of its low cost, ease of installation, and simplicity. However, your connection to the PSTN may be ISDN, DSL, cellular, or some other method.
Serial Line Internet Protocol (Slip)`
Point-To-Point Protocol
- PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client configuration, to communicate between h…
Point-To-Point Tunneling Protocol
- PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it’s simple and secure. To use PPTP, you’ll ha...
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…