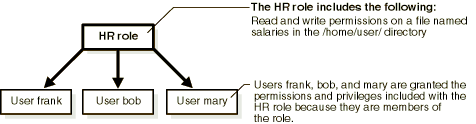
A remote access policy is a document designed to protect the company’s network from external access. This is a written file with guidelines for connecting to the company’s network from outside the office. It helps organizations secure corporate data and supervise users logging in from unsecured locations such as their home networks.
What is a remote access policy?
A remote access policy is a document that protects your company's network and data when employees or other authorized users are accessing it while telecommuting or working remotely.
What behavior constitutes acceptable use of remote access connections?
What behavior constitutes acceptable use of remote access connections Acknowledgement that any organization equipment provided to employees remains the organization's property Potential penalties resulting from violations of the organization's remote access policy Just rolling out the policy won't eliminate risks, however.
How to limit the abilities of remote access users?
The abilities of remote access users should be limited by allowing only certain operations to users, and there should be a policy for removal of authority and access, along with the return of equipment when the teleworking activities are terminated or no longer required.
What is Remote Access Management (RAM)?
It applies to scenarios where employees connect remotely to in-house data centers as well as offsite facilities, such as cloud providers. Secure remote access to company systems and networks is now a way of life for most companies.
What is in a remote access policy?
A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in the office, e.g., password policy.
What is remote access policy in cyber security?
Remote access policy is a document which outlines and defines acceptable methods of remotely connecting to the internal network. It is essential in large organization where networks are geographically dispersed and extend into insecure network locations such as public networks or unmanaged home networks.
What is the meaning of remote access?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
Why is a remote access policy important?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What is an access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
What are the benefits of remote access?
Here, we discuss the most common flexible working benefits that can be supported by your remote access strategy.A more productive workforce. ... Better talent acquisition. ... IT support from anywhere. ... Improved security for remote workers. ... Lower overhead cost. ... Business continuity planning.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are three examples of remote access locations?
What Is Remote Access?Queens College.Harvard University Extension School.
What is the purpose of a password policy?
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organization's official regulations and may be taught as part of security awareness training.
How do you implement remote access?
How to use Remote DesktopSet up the PC you want to connect to so it allows remote connections: Make sure you have Windows 11 Pro. ... Use Remote Desktop to connect to the PC you set up: On your local Windows PC: In the search box on the taskbar, type Remote Desktop Connection, and then select Remote Desktop Connection.
What does remote access to email mean?
If you send email using the web interface while you're traveling that doesn't happen, or it's saved in a separate web-only “sent mail” folder. Remote Access. Another approach is to continue to send and receive email on your desktop at home or at the office, even when you're not there, by accessing the machine remotely.
What does remotely mean in a sentence?
Definition of remotely distantly or indirectly; not immediately: He's remotely related to my wife. We consulted everyone closely or remotely involved with the project before deciding how to proceed.
What Is a Remote Access Policy?
For example, sales personnel can now use tablets and other mobile devices to connect remotely to their office networks while on client calls and bring up data that may be important for closing deals . Recent events have further boosted the number of remote workers to an estimated 42% of the US workforce.
Why Is a Remote Access Policy Important?
If a remote access policy is not in place, such risky behavior could go on unmitigated, without the organization finding out about it until after the occurrence of a breach.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
Why is password policy important?
It helps ensure that only those users who need it are given network access, as long as their devices are also compliant with the guidelines. When implemented properly, it helps safeguard the network from potential security threats.
What is RAS in IT?
Parallels® Remote Application Server (RAS) provides secure remote access for your networks out of the box. It features granular permission policies that enable administrators to enforce access restrictions and settings based on the end-users device or Active Directory group, helping ease the workloads of IT administrators by not requiring any further configuration.
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
How to ensure that you do not miss anything when updating your remote access policy?
To ensure that you do not miss anything when updating your remote access policy, consider your organizational, legal, contractual and regulatory obligations when you compile the list of policy requirements. After that, identify the procedural and technical controls required to fulfill the policy, making sure to reinforce or replace existing controls that have not been effective.
What is remote access policy?
Remote access policies are an ordered set of rules that define how connections are either authorized or rejected. For each rule, there are one or more conditions, a set of profile settings, and a remote access permission setting. If a connection is authorized, the remote access policy profile specifies a set of connection restrictions. The dial-in properties of the user account also provide a set of restrictions. Where applicable, user account connection restrictions override the remote access policy profile connection restrictions.
How to verify remote access server?
1. Either use the Rqc.exe notification component or create a notification component that provides verification to the remote access server that the remote access client computer complies with network policy requirements. 2. Create a validation script that authorizes the client configuration.
How to enable EAP authentication?
Follow these steps to enable EAP authentication:#N#1.#N#Select Start | Administrative Tools | Internet Authentication Service.#N#2.#N#The IAS management console is displayed. Click to highlight Remote Access Policies in the left column.#N#3.#N#In the right column, select Connections to Microsoft Routing and Remote Access Server .#N#4.#N#Select Action | Properties from the menu, or right-click and select Properties from the context menu. #N#5.#N#The Properties dialog box is displayed. Click the Edit Profile button .#N#6.#N#The Edit Dial-in Profile dialog box is displayed. Select the Authentication tab.#N#7.#N#The authentication methods supported by IAS are displayed, as shown in Figure 5.14. You can enable or disable the non-EAP authentication methods here. You can also change the order in which the selected EAP types are negotiated by moving them up or down in the list, using the Move Up and Move Down buttons.#N#Sign in to download full-size image#N#Figure 5.14. Authentication Methods#N#8.#N#Click the EAP Methods button. A list of the currently enabled EAP types is displayed.#N#9.#N#Click Add and select MD5-Challenge from the list.#N#10.#N#Click OK, then click OK in the EAP types list.#N#11.#N#Click OK to exit the Edit Profile dialog box.#N#12.#N#Click OK to exit the Properties dialog box.
How to enable EAP on IAS?
To enable EAP authentication on an IAS server, you create a Remote Access Policy that allows EAP authentication, or you modify an existing policy. Exercise 5.07 demonstrates how to modify a policy to allow the use of MD5 CHAP authentication through EAP.
How to delete VPN policy?
You can delete the other policies if you require only VPN connections to your ISA firewall. Right-click on Connections to other access servers, and click Delete. Repeat with Connections to Microsoft Routing and Remote Access server.
What is VPN quarantine in Windows 2003?
A new feature that comes with a new set of utilities for Windows Server 2003 is Network Access Quarantine Control. Using either the Connection Manager Administration Kit (CMAK) or the Windows Deployment and Resource Kits, administrators can configure special policies that restrict VPN client access using a quarantine mode until the client system is either brought into compliance with corporate VPN client specifications or determined to already be in accordance with specifications. This is a new feature for Windows Server 2003 that will help to increase network security.
What is PPP protocol?
The official implementation, as used by Microsoft, comes from RFP 1990. Capabilities were added and subsequent modifications to the standard were made leading up to PPP as it exists today. In 1994, a documented standard was proposed for “The PPP Multilink Protocol” in RFC 1717. At the time, other proposals existed to combine streams of data at the bit level (basically a hardware solution). This proposal described a software-based solution for the need to combine multiple streams of data into one. This solution was well-suited to the twin bearer channels of ISDN (2B+D).
What is remote access?
Definition (s): Access to an organizational information system by a user (or an information system) communicating through an external, non-organization-controlled network (e.g., the Internet). Source (s):
What is an access system?
Access by users (or information systems) communicating external to an information system security perimeter. Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network.
What is access to an organizational system?
Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network (e.g., the Internet).
What is remote access policy?
A remote access policy can specify one or more of these attributes that should be checked before allowing access. If a policy specifies multiple conditions, then all of the conditions need to match in order for the policy to find a match. For example, let's say that a remote access policy will only allow VPN connections on Saturdays and Sundays, ...
What is the type of media used by the access client?
The type of media that is used by the access client, such as a plain old telephone line, ISDN, wireless, or VPN connection.
What is authentication type?
Authentication Type The type of authentication that is being used by the access client. Authentication types include CHAP, EAP, MS-CHAP, and MS-CHAP v2.
What is NAS authentication?
The vendor of the network access server (NAS) that is requesting authentication—this is most often used in a site-to-site VPN like the ones discussed in Chapter 7. You can use this attribute to configure separate policies for different NAS manufacturers who are connecting via IAS.
What does "in number" mean in a connection attempt?
in number, the connection attempt is rejected. By default, this property is not set so that all dial-in numbers are allowed.
Do you need a separate remote access policy for each group?
The names of the groups to which the user or computer account that is attempting the connection belongs. You don't need to have a separate remote access policy for each group. Instead, you can use multiple groups or nested groups to consolidate and delegate the administration of group membership.
How to secure remote access?
Remote access must be secured and strictly controlled with encryption by using firewalls and secure 2FA Virtual Private Networks (VPNs).
Why is remote access important?
Remote access to your corporate IT infrastructure network is essential to the functioning of your business and the productivity of the working unit. There are external risks that must be mitigated to the best of your ability by designing a secure access policy and implementing ISO compliance controls. The purpose of the policy defines and states the rules and requirements for accessing the company’s network. Rules must be defined to eliminate potential exposure due to unauthorized use, which could cause a loss of the company’s sensitive data and intellectual property, a dent in its public image, and the compromise of resources. Here are the guidelines for defining the rules to eliminate potential exposure due to unauthorized use:
Why do we need to tamper proof VPN?
Unauthorized access to these logs must be taken care of. Tamper-proof logging of firewall and VPN devices enhances the reliability of the audit trail.
Why should firewall operation mode be stateful?
The firewall operation mode should be configured as stateful rather than stateless, in order to have the complete logs.
How many people work remotely?
A study by one Switzerland-based service office provider says that 70% of people globally work remotely at least once a week, and so telecommuting is more popular than ever.
Is remote access to the organization's network a risk?
Giving your employees the possibility to work from anywhere has myriad advantages, but measures of wariness need to be taken. This is why remote access to the organization’s network needs to be interpreted as a risk, and hence there is a need to have appropriate controls for it. Therefore, it should be allowed only in the cases where required and with adequate security controls required by ISO 27001.
Should remote access be limited?
The abilities of remote access users should be limited by allowing only certain operations to users, and there should be a policy for removal of authority and access, along with the return of equipment when the teleworking activities are terminated or no longer required.
How to implement a remote access policy?
You can quickly implement a remote access policy in your organization by downloading TechRepublic's Remote Access Policy. Included you'll find a risk assessment spreadsheet that will help you determine the importance of such a policy to your organization's security along with a basic policy that you can use and modify. You can purchase it from the TechRepublic Catalog or download it for free as part of your TechRepublic Pro membership.
Why is remote access important?
Enabling remote access to an organization's network, systems and data can benefit most any organization. Whether a small nonprofit seeks to enable volunteers to work from home, a small business' employees require flexible work schedules or a global multinational corporation needs to link engineers working in distant locations, remote access can prove a key feature in empowering communication and productivity.
Who should make telecommuting decisions?
For this reason, telecommuting and remote assignment decisions are best left to departmental managers. Most organizations will want to let departments extend telecommuting and remote access privileges as they deem appropriate.
Is remote access for everyone?
Not for everyone. Remote access, despite the advantages, is just not for everyone. Employees requiring access to student or medical records may likely find it best to work from a secure location using data access methods consistent with federal legislation and industry guidelines governing the use of that data.
