
On the Windows machine : go to the properties of the VPN connection. Click on the Networking tab and double click Internet Protocol Version 4 (TCP/IPv4). Click Advanced and uncheck the box for "Use default gateway on remote network."
Full Answer
What is a VPN connection?
A VPN network does not provide users with remote access. d. A VPN connection utilizes private networks instead of the public network. e. A VPN client software encrypts messages to ensure secure transmissions. e. A VPN client software encrypts messages to ensure secure transmissions
What is a remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
Can I use a remote access VPN with Microsoft 365?
If your organization uses a remote access VPN solution, typically with VPN servers on the edge of your network and VPN clients installed on your users' devices, your users can use remote access VPN connections to access on-premises apps and servers. But you may need to optimize traffic to Microsoft 365 cloud-based services.
Can I use azure point-to-site VPN for remote workers?
If your remote workers are not using a traditional VPN client and you have apps that are not web-based, you can use an Azure Point-to-Site (P2S) VPN. A P2S VPN connection creates a secure connection from a remote worker’s device to your organization network through an Azure virtual network.
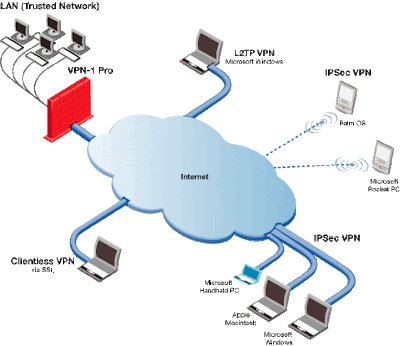
Does a VPN provide users with remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Can a VPN prevent remote access?
Virtual Private Network (VPN) Because internet traffic and user identity are protected with encryption, VPN is technically a security solution, although it does enable remote network access, whether users are working from home, a coffee shop, or an airport.
Is VPN same as remote access?
Flexibility. While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer.
How does VPN work for remote access?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What does a VPN not protect you from?
It's important to remember that VPNs do not work in the same way as comprehensive anti-virus software. While they will protect your IP and encrypt your internet history, but that is as much as they can do. They won't keep you safe, for instance, if you visit phishing websites or download compromised files.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What is remote access and site to site VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What do you need for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
How do VPN networks work?
A VPN masks your IP address by acting as an intermediary and rerouting your traffic. It also adds encryption, or a tunnel around your identity, as you connect. The combination of the VPN server and the encryption tunnel blocks your ISP, governments, hackers, and anyone else from spying on you as you navigate the web.
Do you need a VPN for Remote Desktop?
By default, Windows Remote Desktop will only work on your local network. To access Remote Desktop over the Internet, you'll need to use a VPN or forward ports on your router.
Why a VPN is not enough?
VPNs Add to Network Complexity Adding a VPN to manage and configure adds to the overall complexity of network configuration management which, in turn, could lead to greater security vulnerabilities.
Are firewalls and VPNs adequate to guarantee securing your organization?
Firewalls, VPNs, and endpoint security are simply not enough in today's threatscape. A Bring Your Own Network™ solution is needed to protect remote employees and all the traffic from home networks that are left vulnerable. This entails whole-home monitoring, AI-powered security, network topology, and more.
What is the advantage of virtual private network tunneling for remote users?
If you use a VPN, it can stop people, software, and web browsers from gaining access to your connection. This keeps the information you transmit and receive secure and anonymous.
What is site to site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
When do businesses use VPNs?
When a business uses VPNs to provide third-party vendors access to their network, those vendors either have full access to your network (for example, at the start of a job) or they don’t (when you revoke access after the job ends) – unless companies implement strict network segmentation with firewalls and switches, which adds additional complexity.
What is VPN for employees?
A Virtual Private Network (VPN) is perfect for internal employees who need to access the server (or section of the server) from anywhere besides the office. In fact, at SecureLink we use VPN client software on our laptops to do just that; if you need to work remotely and need to update something that’s on the server, just use your VPN and you can easily get it done. Generally, this type of network offers high-speed connections that help companies operate efficiently. In addition to allowing employees to work from home or on the road, VPN connections can also give vendors access to internal resources they need in order to support company operations.
Why do hackers use VPNs?
Hackers often use VPNs to gain access to networks. If your business has many third-party vendors, and each vendor has full access to your network, a hacker now has multiple potential routes to break into and exploit your network using VPN traffic.
Why does VPN speed decrease?
While using VPN software increases security over an unencrypted connection, connection speeds and application performance can decrease due to several factors – such as the time needed to provision and test the VPN, which usually involves other departments such as IT support.
What is SecureLink remote access?
With SecureLink, third-party remote access is given not to your entire network, but only specific areas, based on the (much safer) principle of least privilege: vendors can access only the resources they require to get their job done.
How can a hacker access a network?
Let’s face the facts: One of the easiest ways a hacker enters a network is through a third-party connection. Using a checklist to assess VPN risks and the vulnerability of your third parties’ remote access points can help reduce the probability of an attack.
What does P mean in VPN?
If your third-party vendors and VPN users have access to your network, you may believe that your company data and network are safe; after all, the “P” in VPN does stand for “private ”. However, history has proven otherwise.
How to configure a VPN?
Here are the primary configurations for remote access: 1 You are already using a remote access VPN solution. 2 You are not using a remote access VPN solution and you want your remote workers to use their personal computers. 3 You are not using a remote access VPN solution, you have hybrid identity, and you need remote access only to on-premises web-based apps. 4 You are not using a remote access VPN solution and you need access to on-premises apps, some of which are not web-based.
What is P2S VPN?
A P2S VPN connection creates a secure connection from a remote worker’s device to your organization network through an Azure virtual network.
How to optimize access to Microsoft 365 cloud?
To optimize access to Microsoft 365 cloud resources, configure your split tunneling VPN clients to exclude traffic to the Optimize category Microsoft 365 endpoints over the VPN connection. For more information, see Office 365 endpoint categories. See this list of Optimize category endpoints.
Does Microsoft 365 have P2S VPN?
Azure P2S VPN is not included with a Microsoft 365 subscription. You must pay for usage with a separate Azure subscription.
Does Microsoft 365 have an Azure AD proxy?
Azure AD Application Proxy is not included with a Microsoft 365 subscription. You must pay for usage with a separate Azure subscription.
Is Azure Virtual Desktop included with Microsoft 365?
Azure Virtual Desktop is not included with a Microsoft 365 subscription. You must pay for usage with a separate Azure subscription.
Can a VPN client be used to access a remote network?
If your remote workers are using a traditional VPN client to obtain remote access to your organization network, verify that the VPN client has split tunneling support.
