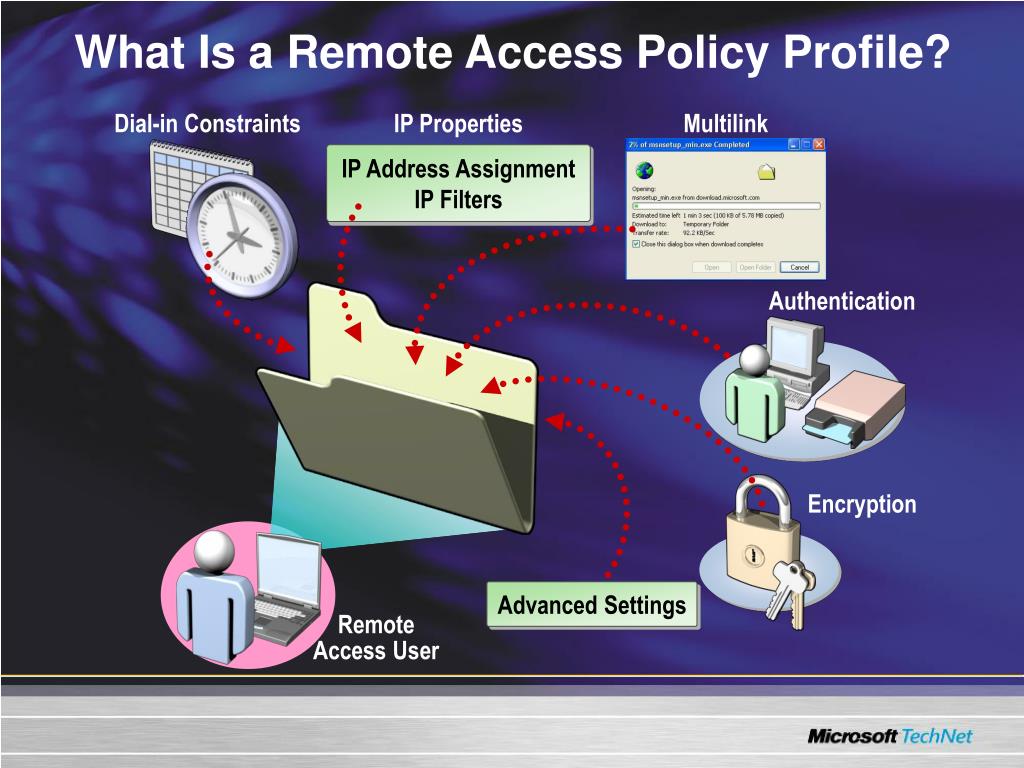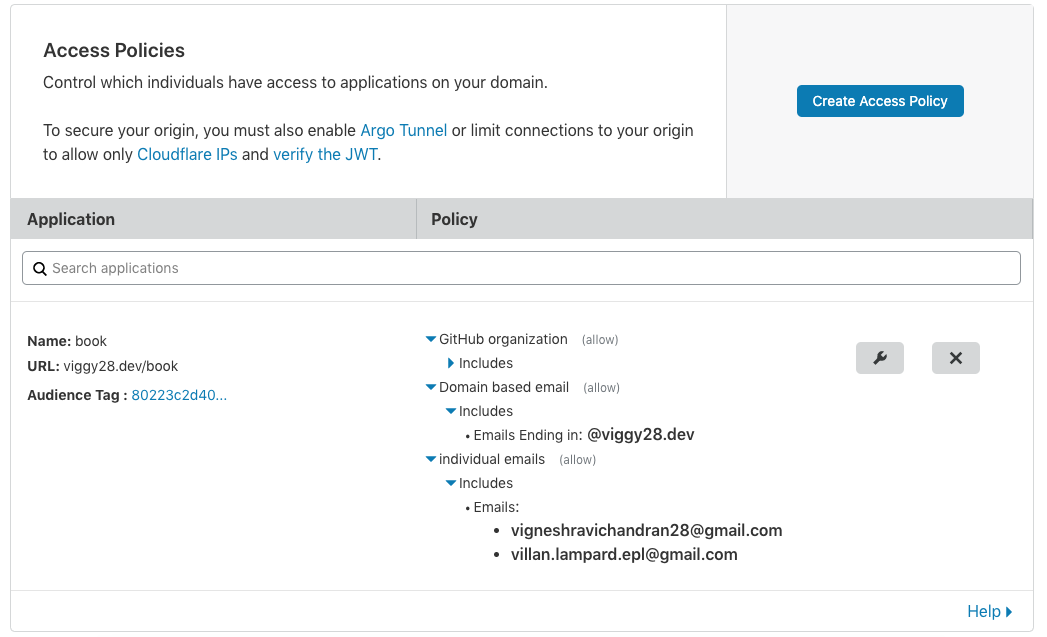
A remote access policy should also lay down who can assign remote access to users and what constitutes acceptable use of a remote access connection. It is recommended to leave the task of assigning users to direct managers. Acceptable use guidelines ensure that users keep their frivolous tasks off the network.
What are the different types of policies for remote access?
Policies for using company systems involve security, confidentiality, the integrity of information, and a hierarchy of access or availability. Remote policies have guidelines for access that can include the following: Hardware and software configuration standards for remote access, including anti-malware, firewalls, and antivirus
What is a remote access policy (rap)?
What Is a Network Security Policy? A remote access policy is commonly found as a subsection of a more broad network security policy (NSP). The network security policy provides the rules and policies for access to a business’s network.
What are the benefits of having a strong remote access policy?
A strong remote access policy can mitigate a plethora of potential hazards. The policy informs off-site employees of their responsibilities in the security protocols to keep information systems secure. Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access.
What happens if a remote access policy is not in place?
If a remote access policy is not in place, such risky behavior could go on unmitigated, without the organization finding out about it until after the occurrence of a breach. With a comprehensive remote access policy, employees are made aware of the need to safeguard the network using best practices.

What should be in a remote access policy?
A remote access policy should cover everything—from the types of users who can be given network access from outside the office to device types that can be used when connecting to the network. Once written, employees must sign a remote access policy acceptance form.
What is an example of acceptable use policy?
Refrain from monopolizing systems, overloading networks with excessive data, degrading services, or wasting computer time, connection time, disk space, printer paper, manuals, or other resources.
What is acceptable use policy in cyber security?
An acceptable use policy (AUP) is a document stipulating constraints and practices that a user must agree to for access to a corporate network, the internet or other resources. Many businesses and educational institutions require employees or students to sign an AUP before being granted a network ID.
Why should an organization have a remote access policy even if IT already has an acceptable use policy AUP for employees?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What should not be part of an acceptable use policy?
1 Answer. Encryption policies not be part of an acceptable use policy.
What are acceptable use policies for workplace technology?
An acceptable use policy (AUP) is a document that outlines the rules and restrictions employees must follow in regard to the company's network, software, internet connection and devices.
Do I need an acceptable use policy?
An Acceptable Use Policy is an important document that can demonstrate due diligence with regards to the security of your IT network and the protection of sensitive data in the event of a breach or regulatory audit. This importantly protects the organisation from legal actions.
Who owns the acceptable use policy?
The Deputy Director of Administration owns this Acceptable Use Policy and is responsible for ensuring that all personnel with access to state information assets are aware of this policy and acknowledge their individual responsibilities. 6.2.
Why do we need an acceptable use policy?
An 'Acceptable Use' policy ensures that employees understand the way in which information should be used. It enables both employees and the business organisation to gain the maximum value from the internet. It alerts all users to the technical and commercial risks that can arise if the technology is misused.
What is the difference between an acceptable use policy and a fair use policy?
One consequence of sharing is that an AUP typically goes into detail about etiquette and respect for fellow users of the resource, which is not applicable for single-user software applications. An acceptable use policy is also known as a fair use policy or terms of use.
Which of the following best describes an acceptable use policy?
Which of the following statements best defines an acceptable use policy (AUP)? It defines acceptable uses of the firm's information resources and computing equipment, including desktop and laptop computers, wireless devices, telephones, and the Internet, and it specifies consequences for noncompliance.
How a remote access policy may be used and its purpose?
The purpose of a remote access policy is to outline the expectations of those users' behaviors while connecting to your network in an attempt to safeguard that network from viruses, threats or other security incidents.
Which of the following best describes an acceptable use policy?
Which of the following statements best defines an acceptable use policy (AUP)? It defines acceptable uses of the firm's information resources and computing equipment, including desktop and laptop computers, wireless devices, telephones, and the Internet, and it specifies consequences for noncompliance.
What is the difference between an acceptable use policy and a fair use policy?
One consequence of sharing is that an AUP typically goes into detail about etiquette and respect for fellow users of the resource, which is not applicable for single-user software applications. An acceptable use policy is also known as a fair use policy or terms of use.
Why do companies have acceptable use policies?
An 'Acceptable Use' policy ensures that employees understand the way in which information should be used. It enables both employees and the business organisation to gain the maximum value from the internet. It alerts all users to the technical and commercial risks that can arise if the technology is misused.
What is an acceptable use policy in schools?
An AUP is an agreement between the student and the district designed to keep students safe online. This agreement allows them to explore the digital world as part of their education, instead of accessing inappropriate or harmful sites, such as bullying, school violence, pornography, etc.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
What is VPN policy?
Policies for VPN remote access can be standardized. These policies “shore up” and prevent the use of rogue devices and access by non-authorized users , including the worker's family members or housemates. The policy also enforces proper email protocols to protect information from being sent through unsecured or untrusted sources, and also provides rules that limit or prohibit split tunnel configurations that allow mobile users to access both secure and unsecure networks simultaneously.
What is telecommuting?
“Telecommuting,” a term coined in the 1970s, has experienced explosive growth in today’s era of mobile connectivity. Now called distributed offices, remote work, telework, mobile work, smart work, and work shifting, many people are finding flexibility and increased productivity conducting business away from a centralized office environment. Researchers have long studied the benefits of remote work - from the successes that remote work had on traffic reduction during the 1984 Los Angeles Olympics to the 2016 findings by a Gallup survey on the increased hours for remote work.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.