Adwind RAT, also known as AlienSpy, Frutas, Unrecom, Sockrat, JSocket, and jRAT, is a remote access trojan that was first spotted in 2012 as Frutas. Kaspersky has tracked more than 150 attack campaigns against more than 60,000 targets from 2013 till early 2016. What are the capabilities of Adwind? The remote access trojan’s capabilities include:
Full Answer
What is adwind rat?
Amazing how things have changed—these days malware is everywhere, and this unmistakable trend is troubling. Last week, news circulated about a new threat, called Adwind RAT, a multi-platform remote access trojan written in Java and that is fully functional on Windows, and partially functional on OS X.
Should I remove the adwind rat Trojan?
If you have ever been infected with AdWind RAT, there is no doubt that you should immediately take actions to remove the Trojan horse and any associated scripts in order to prevent the malware from causing serious harm.
What is the adwind rat malware on Mac?
According to Catalin Cimpanu over at Softpedia.com, security researchers discovered a version of Adwind RAT that was “distributed as part of a malware distribution campaign spotted at the start of the month, which actually dropped a Mac-specific payload when infecting Mac devices.”
Can adwind virus infect my Computer?
But all computers users must be aware that because Adwind is written in Java, it is capable of infecting all major operating systems where Java is supported, including: Windows, Mac, Linux, and Android.

What is Adwind malware?
adwind trojan. Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015.
Can remote access Trojans be detected?
AIDE—short for Advanced Intrusion Detection Environment—is a HIDS designed specifically to focus on rootkit detection and file signature comparisons, both of which are incredibly useful for detecting APTs like Remote Access Trojans.
Is remote access Trojan a malware?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
Can antivirus detect RAT?
Antivirus systems don't do very well against RATs. Often the infection of a computer or network goes undetected for years. The obfuscation methods used by parallel programs to cloak the RAT procedures make them very difficult to spot.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
Is someone using my computer remotely?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer. Windows – Press Ctrl + Shift + Esc. Mac – Open the Applications folder in Finder, double-click the Utilities folder, and then double-click Activity Monitor.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
Can someone RAT an Iphone?
So someone would need direct physical access to your iOS device and a computer to install a RAT exploit into it. Even if you accessed a web site or email with a RAT package hidden in it, it cannot execute or do anything on a normal iOS installation.
What is a malware RAT?
A Remote Access Trojan, otherwise known as a RAT, is a type of spyware that allows a cybercriminal to take control of the computer or other device it's installed on. RATs are malicious software that constitute a major cybersecurity threat.
Which connection is most commonly used in rats?
RAT infections are typically carried out via spear phishing and social engineering attacks. Most are hidden inside heavily packed binaries that are dropped in the later stages of the malware's payload execution.
How do you know if your PC is infected?
How to Spot a Computer VirusSlow computer performance (taking a long time to start up or open programs)Problems shutting down or restarting.Missing files.Frequent system crashes and/or error messages.Unexpected pop-up windows.New applications (toolbars, etc.)More items...•
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
Which virus that Cannot be detected by antivirus software is?
A stealth virus has an intelligent architecture, making it difficult to eliminate it completely from a computer system. The virus is smart enough to rename itself and send copies to a different drive or location, evading detection by the system's antivirus software.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
Can Norton detect RATs?
Antivirus software like Bitdefender, Kaspersky, Webroot, or Norton, can detect RATs and other types of malware if they infect your devices.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
Where does Adwind malware install, and how?
Regardless of the Gatekeeper settings preferences, any user—whether carelessly or intentionally—can override its protection.
What does Adwind do when it is executing?
On OS X or macOS, when executing the Adwind dropper—meaning that when the rogue file is executed, it will “drop” its infection on the target—it creates a launch agent, which it uses to start a loader that is devoted to download malicious files from the Internet or connect to rogue servers.
How to remove Java app from Finder?
To remove the Java app via Finder, choose Go > Go to Folder menu, enter /.UQnxIJkKPii/UQnxIJkKPii and then click Go. If it exists, you are infected: Move BgHSYtccjkN.ELbrtQ to the trash. (The files are dropped in the Home Folder. It requires a path, such as /Users/intego/.UQnxIJkKPii/UQnxIJkKPii/ BgHSYtccjkN.ELbrtQ.)
What is the launch agent on Mavericks?
This file is the main loader, which connects to a rogue server to download additional files.
How to override Gatekeeper?
To override Gatekeeper, users could Control-Click or Right-Click on the file . And that’s not the only way to get around Gatekeeper’s protection. Gatekeeper’s quarantine attribute is not applied if a user drops a file locally from one Mac to another; for instance, if you download the Adwind RAT sample on your Mac, ...
How to remove launch agent?
To remove the Launch Agent via Finder, choose Go > Go to Folder, enter /Library/LaunchAgents and then click Go. Move org.yrGfjOQJztZ.plist to the Trash. (Example path: /Users/intego/Library/LaunchAgents/org.yrGfjOQJztZ.plist.)
When did Adwind start?
Adwind malware has been circulating for years, dating back to 2012, distributed under several different names, such as jRAT and others with similar capabilities.
What is Adwind malware?
This calls for a multilayered approach to security that covers the gateway , endpoints , networks, servers, and mobile devices. IT/system administrators and information security professionals, as well as developers/programmers that use Java should also adopt best practices for using and securing Java and regularly keep it patched and updated.
What is Trend Micro?
Trend Micro endpoint solutions such as Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security can protect users and businesses from these threats by detecting malicious files, and spammed messages as well as blocking all related malicious URLs. Trend Micro Deep Discovery™ has an email inspection layer that can protect enterprises by detecting malicious attachment and URLs.
Targets home and enterprise users
This allows its operators to successfully compromise their targets' computers without raising suspicion, and perform a wide range of malicious tasks from stealing sensitive info like VPN certificates and credentials from Chrome, IE, and Edge to collecting and exfiltrating the victims' keystrokes.
Malicious URLs camouflaged as a PDF attachment
The emails used to infect the victims of this specific campaign were found in the inboxes of staff employed by entities from the utilities sector, landing there after successfully bypassing the companies' email gateways.
Switching methods and baits
Cofense's researchers have also observed several other coordinated attacks employing a large array of techniques and baits to phish various types of targets.
What is Adwind RAT?
AdWind RAT is a malicious Trojan horse that is actively used to spread harmful viruses on the Internet and cause various types of harm to the infected computers. This virus has recently been reported to be associated with infections of the Ransomware type, as well as many other online fraud and theft activities.
How to protect against Trojan horses?
To increase the security of your system, you need to use a reliable antivirus, to regularly update your software with the latest security patches and keep all of your important data safe by backing it up on external hard drives, CDs, DVDs, or just rely on online backup like Google Drive, Dropbox, and so on. This way, even if a nasty malware attacks you, you will prevent major data loss and will be able to easily recover.
What is a Trojan horse?
Trojan horses like the AdWind RAT (Remote Access Trojan) are considered to be some of the most cunning online threats. The AdWind RAT can be used for a number of criminal purposes and ever since it was created, it has been infecting unsuspecting online users.
What is Adwind malware?
Adwind is a paid malware platform that allows attackers to log keystrokes, steal passwords, capture webcam video, and more. Nasty stuff, for sure. Let’s break down what happened when the victim downloaded a so-called “important document” containing the Adwind RAT.
What is the payload of Adwind?
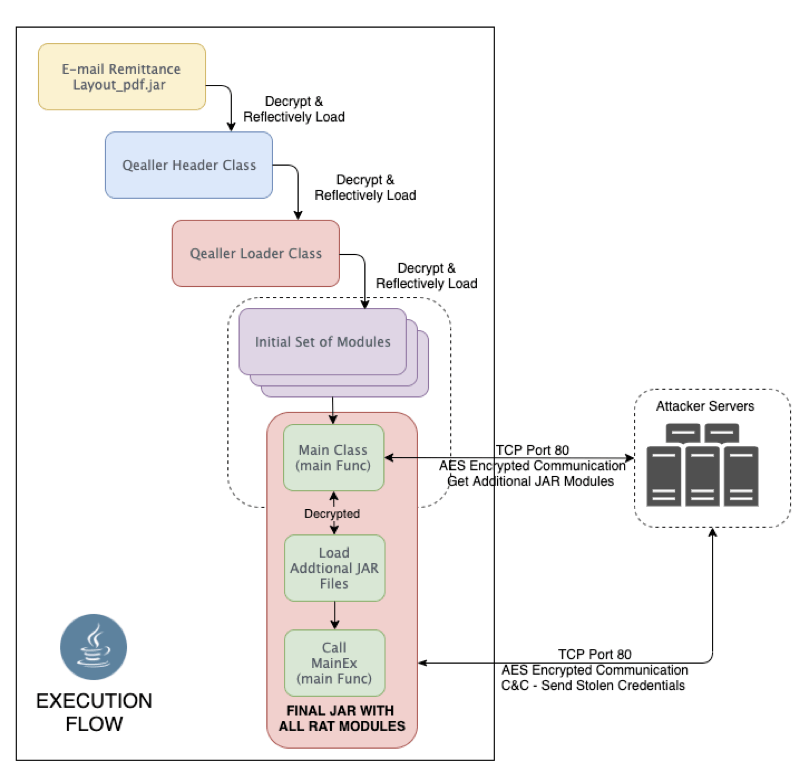
The payload of this attack was the Adwind Remote Access Trojan (RAT). Adwind is a paid malware platform that allows attackers to log keystrokes, steal passwords, capture webcam video, and more. Nasty stuff, for sure. Let’s break down what happened when the victim downloaded a so-called “important document” containing the Adwind RAT. We’ll use telemetry from the attack to illustrate its progression.
Is Threat Detection Report available for 2021?
All 2021 Threat Detection Report content is fully available through this website. If you prefer to download a PDF, just fill out this form and let us know what email to send it to.
Do you need administrator privileges to write files to AppData?
Since AppData is owned by the user, an attacker doesn’t need to have Administrator privileges in order to write files there. In addition, many legitimate applications launch processes from AppData, so the file location alone isn’t likely to raise many red flags to defenders.
How many attacks has Adwind been used?
Earlier this year, it was reported that Adwind was used in at least 443,000 attacks. Adwind has rebranded itself multiple times in the past, using the names “Frutas,” “AlienSpy,” and “Unrecom,” to name a few.
What is a RAT?
The Adwind Remote Access Trojan (RAT) is a popular Java-based backdoor capable of infecting Windows, Linux, Mac OS and Android operating systems. Its cross-platform nature, elaborate backdoor features, and relatively cheap price makes it a favourite choice for many cybercriminals today. Earlier this year, it was reported that Adwind was used in at least 443,000 attacks.
What is Adwind RAT?
As with any trojan software, phishing email campaigns are used to encourage any who receive them to click or download something containing the harmful virus. Once Adwind RAT is on your Mac, it connects to the command-and-control server to download further malicious payloads.
How to remove Adwind?
One way to protect yourself is to watch out for emails containing .CSV and .XLT attachments. Also watch out for any attachments with extensions including .HTM, .XCL and .DB. Especially if you don't recognize the email or sender.
Or take a shortcut: Use a dedicated app uninstaller
There are many fake Mac cleaner tools that claim to remove viruses but only a few of them do work as advertised. One from the legit camp is CleanMyMac. I've been using it since the first version and confirm that it does remove junk quite effectively. It goes after those small virus leftovers that ordinary user can't access.

General Description of Adwind
- Initially discovered for the first time in 2012, the malware was known as Frutas and presumably originated in Mexico. For the initial year of Adwind’s existence, the creator released multiple versions, all distributed on Spanish hacker forums for free. The feature-set of the original versio…
Adwind Rat Malware Analysis
- ANY.RUN interactive service enables researchers to perform the analysis of the execution process of Adwind Trojan in a secure environment in multiple formats, including video. Figure 1: Visual process graphs generated by ANY.RUNhelp to simplify and speed up research work Figure 2: ANY.RUN creates customizable text reportsallowing researchers to share the results of the simu…
Adwind Execution Process
- In the case of our simulation, after a user opened the malicious .jar file, the malware started execution through Java virtual machine. This initial process executed the js script, which ran one more js script and another .jar file. JS script also used Task Scheduler to run itself later. Jar file started a series of malicious activities such as using attrib.exe to mark files or folders as hidden…
How to Avoid Infection by Adwind?
- Exhibiting caution when handling emails from unknown senders is a reliable way to prevent contamination since Adwind trojan requires a victim to interact with the malicious file to enter an active phase. Therefore, never downloading attachments in suspicious emails is a sure way to stay safe when you are dealing with any malicious objects such as ransomware, RAT, or others. …
Distribution of Adwind
- Adwind RAT is distributed in mail spam campaigns the same as AZORult or Remcosand has two general attack vectors. It can be delivered to the victim's machine as an email attachment in the form of a malicious file such as a PDF or a Microsoft Office file. The other attack vector is a malicious URL that redirects the victim to a website from where Adwind is downloaded.
How to Export Process Graph from The Analysis of Adwind Malware Using Any.Run?
- Analysts can export the process graph from a task to SVG format if they want it to share. Just click on the "Export" button and choose "Export Process Graph (SVG)" in the drop-down menu. Figure 3: Adwind's process graph exported in SVG format
Conclusion
- Distributed as a malware-as-a-service, the Adwind RAT v3.0 has become one of the most popular RATs and targets users of all major operating systems worldwide. Not only is the “official” paid version of the malware is known to have created a massive following, but several slightly outdated but still very powerful cracked, free-to-use versions are readily available online on the undergrou…