
How To Enable Remote Access to MySQL via SSH / Command Line In Linux
- Edit the MySQL configuration file, to tell the MySQL server to listen on all available IP addresses. We recommend...
- Restart MySQL Server Now that the configuration file is updated, you will need to restart MySQL for this to take...
- Create a remote MySQL user. You will need to create a remote...
- To enable remote root login, enter the following command: /etc/ssh/sshd_config: PermitRootLogin yes #enabled.
- To disable remote root login, enter the following command: /etc/ssh/sshd_config: PermitRootLogin no #disabled.
How do I connect to a remote server with SSH?
For this method to work, you must already have password-based SSH access to your server. To use the utility, you simply need to specify the remote host that you would like to connect to and the user account that you have password SSH access to. This is the account where your public SSH key will be copied.
How do I enable SSH on a Linux server?
Start by opening a terminal and opening the SSH server configuration file. You can use nano or your preferred text editor for this, as long as you open the file with root permissions. At the end of this file, use the directive AllowUsers to specify which user accounts you want to enable SSH access for. List all your users separated by a space.
How to disable or deny SSH access to any user?
To disable or deny SSH access to any user or group, you need to add/edit the following directives in your remote server's sshd_config file. To deny SSH access to specific user called "sk", edit sshd_config file: $ sudo vi /etc/ssh/sshd_config. Add/edit the following line in sshd_config file. DenyUsers sk.
How do I access a Linux server remotely?
There are two forms of remote access on RHEL and most Unix and other Linux systems: Secure Shell (SSH) provides a text console on a server, with the option to forward graphics as needed. Virtual Network Computing (VNC) provides a graphical login to a system, with a full desktop in a VNC client.
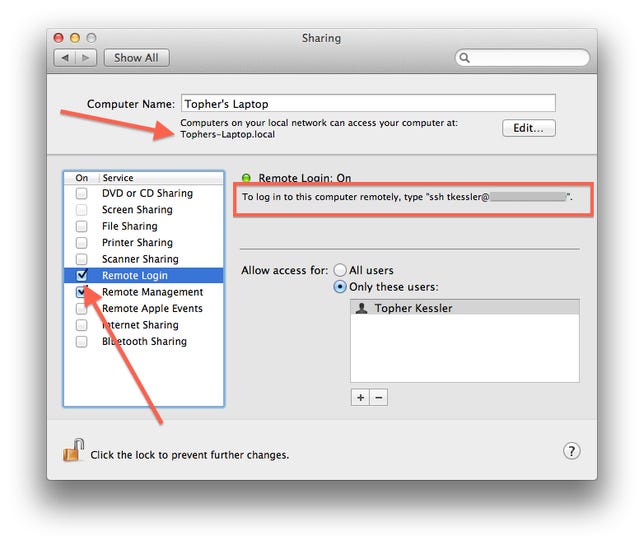
How do I enable SSH remotely?
How to Connect via SSHOpen the SSH terminal on your machine and run the following command: ssh your_username@host_ip_address. ... Type in your password and hit Enter. ... When you are connecting to a server for the very first time, it will ask you if you want to continue connecting.More items...•
How do I enable remote access in Linux?
To enable remote desktop sharing, in File Explorer right-click on My Computer → Properties → Remote Settings and, in the pop-up that opens, check Allow remote connections to this computer, then select Apply.
How do I give SSH permission to user in Linux?
Granting SSH access to a userLocate the following OpenSSH file: /etc/ssh/sshd_config.Make a backup of this file so you can revert if necessary. For example: cp /etc/ssh/sshd_config{,.' date +%s'}Edit the file by using the OpenSSH keywords.
How do I enable SSH on Linux server?
Enable the ssh service by typing: # sudo systemctl enable ssh. Start the ssh service by typing: # sudo systemctl start ssh. Test it by login into the system using:# ssh userName@Your-server-name-IP.
How do I know if RDP is enabled Linux?
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server and to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services.If the value of the fDenyTSConnections key is 0, then RDP is enabled.If the value of the fDenyTSConnections key is 1, then RDP is disabled.
How do I enable remote access in Ubuntu?
Enabling Remote Desktop: You can enable remote desktop on Ubuntu Desktop 22.04 LTS from the Settings app. To open the Settings app, click on Settings from the system tray as marked in the screenshot below. From the Sharing tab1, enable Sharing using the toggle button2. Click on Remote Desktop.
How do I give permission to SSH?
Enable root login over SSH:As root, edit the sshd_config file in /etc/ssh/sshd_config : nano /etc/ssh/sshd_config.Add a line in the Authentication section of the file that says PermitRootLogin yes . ... Save the updated /etc/ssh/sshd_config file.Restart the SSH server: service sshd restart.
How do I give someone access to my Linux server?
RHEL or CentOS create a new user account with admin (sudo) accessOpen the terminal application.For remote CentOS server use the ssh command and log in as the root user using either su or sudo.Create a new CentOS user named vivek, run: useradd vivek.Set the password, execute: passwd vivek.More items...•
How do I give SSH permission to user in Ubuntu?
Install open-ssh Package During the installation process, a dialog will prompt you in the terminal. Enter 'y' to proceed with the installation. If the following output is received in the terminal, the SSH service is running and enabled. Move to the command-line shell and press 'q.
What is the SSH command in Linux?
SSH (Secure Shell) is a network protocol that enables secure remote connections between two systems. System admins use SSH utilities to manage machines, copy, or move files between systems. Because SSH transmits data over encrypted channels, security is at a high level.
How can I tell if SSH is running?
Use the ps command to list all the processes and filter the output using grep to check if the SSH process is running. Depending on the state of the process, the output will differ.
Where is .SSH Linux?
By default, the keys will be stored in the ~/. ssh directory within your user's home directory. The private key will be called id_rsa and the associated public key will be called id_rsa. pub .
How do I connect Linux desktop to Windows?
The RDP Method The easiest way to set up a remote connection to a Linux desktop is to use Remote Desktop Protocol, which is built into Windows. Once this is done, type “rdp” in the search function and run the Remote Desktop software on your Windows machine.
How do I enable Gnome Remote Desktop?
Log into GNOME desktop. Run gnome-control-center sharing and enable "Sharing ” switch button. Open "Remote Login" submenu on the “ Sharing" setting and enable the “ On" switch button and bring back to the "Sharing" setting. Open “ Screen Sharing ” submenu on the "Sharing" setting and enable the “ Active" switch button.
How to exit insert mode in SSH?
Press ESC key to exit insert mode and type :wq to save and quit the SSH config file. Restart SSH service to take effect the changes.
Can you limit a user's access to Linux?
A while ago, we discussed how to limit a user's access to Linux system using Restricted shell. Once we have put the users in restricted mode, they can't do anything except what they are allowed to do.
How does SSH work in Linux?
In Linux, the SSH service works a method called end-to-end encryption, where one user has a public key, and another user holds a private key. Data transmission can occur when both users enter the right encryption keys. The SSH functions through the terminal command-line interface.
What is SSH in Linux?
In Linux, the Secure Shell (SSH) is a method where you can access another computer through a secure and two-way encrypted communication system over the internet. By enabling the SSH service in Linux, you can use the SSH protocol as an FTP (File Transfer Protocol) server or, you can get remote access to another Pc.
How to install OpenSSH on Arch Linux?
First, you need to update the system repository of Arch Linux. Then you can install the OpenSSH service on Arch Linux through the packman commands. You can start or stop any SSH service, check the SSH status, and disable the SSH service on Arch Linux using the systemctl terminal command.
What port is used for Firefox?
To allow the port mapping application for specific software, you can use the SSH service in your Linux machine. Here, I am using port 15169 for Firefox. Then, you may need to configure the Firefox Networking too.
What is SSH service?
Enabling SSH service can connect your device to another device or server through a secure tunnel where your identity and data transmissions are totally safe and encrypted. If you are a network administrator, you must know how to enable and configure the SSH service in Linux.
What port is used for SSH?
If you are using a static IP address for the secure shell connection, you can set rules for the specific network and port. For SSH service, the default port is 22. You can change the port if necessary. We will run the vvv command to check and set the SSH protocol against a specific IP address. In my case, I am trying to connect the localhost network. Those who don’t know how to get a localhost network in Linux can see the procedures of how to install the Apache server on Linux.
What port does Red Hat use?
Here are the terminal command lines to check, install, start, and enable the SSH service on Red Hat Linux. Like other Linux distros, Red Hat also uses the port 22 to establish SSH service. You may also need to allow the firewall access for SSH service on CentOS and Red Hat Linux.
Where is username in Linux?
If your login is successful, you will see username@machinename at bottom of terminal.
What is username in a server?
username is the name of the root user of your server and ipaddress is also of your server. Next, it will prompt you for the password which is the server’s root user’s password. Again, if you are successful, your prompt will change to username@machinename and now you will be able to access all your files of server PC into the client PC.
Can I use a Mac to SSH into Linux?
Now, your machine is ready for SSH access. Grab another machine with any OS. I will be using a mac machine to ssh into my Linux PC. You will not require any extra configuration for Linux and Mac, but if you are on Windows, you will require to download an ssh client. What I recommend is install puTTY which is the most popular free SSH client.
Can you use ssh-keygen to generate passwords?
You can use ssh-keygen, puttygen, etc. to generate the keys. Alternatively, you can enable sshd password authentication. Edit the "/etc/ssh/sshd_config" file and ensure that the "PasswordAuthentication" directive is set to yes: PasswordAuthentication yes.
Can you enable sshd authentication?
Alternatively, you can enable sshd password authentication. Edit the "/etc/ssh/sshd_config" file and ensure that the "PasswordAuthentication" directive is set to yes:
How to use SSH utility?
To use the utility, you need to specify the remote host that you would like to connect to, and the user account that you have password-based SSH access to. This is the account where your public SSH key will be copied.
What is SSH in Linux?
SSH, or secure shell, is an encrypted protocol used to administer and communicate with servers. When working with a Linux server, chances are, you will spend most of your time in a terminal session connected to your server through SSH.
How Do SSH Keys Work?
An SSH server can authenticate clients using a variety of different methods. The most basic of these is password authentication, which is easy to use, but not the most secure.
What is a SSH key pair?
SSH key pairs are two cryptographically secure keys that can be used to authenticate a client to an SSH server. Each key pair consists of a public key and a private key. The private key is retained by the client and should be kept absolutely secret. Any compromise of the private key will allow the attacker to log into servers ...
What are the advantages of SSH?
You may be wondering what advantages an SSH key provides if you still need to enter a passphrase. Some of the advantages are: 1 The private SSH key (the part that can be passphrase protected), is never exposed on the network. The passphrase is only used to decrypt the key on the local machine. This means that network-based brute forcing will not be possible against the passphrase. 2 The private key is kept within a restricted directory. The SSH client will not recognize private keys that are not kept in restricted directories. The key itself must also have restricted permissions (read and write only available for the owner). This means that other users on the system cannot snoop. 3 Any attacker hoping to crack the private SSH key passphrase must already have access to the system. This means that they will already have access to your user account or the root account. If you are in this position, the passphrase can prevent the attacker from immediately logging into your other servers. This will hopefully give you time to create and implement a new SSH key pair and remove access from the compromised key.
How to add multiple SSH keys to a server?
You can embed multiple keys on a single server: If you do not already have a public SSH key uploaded to your account, or if you would like to add a new key to your account, click on the “+ Add SSH Key” button. This will expand to a prompt: In the “SSH Key content” box, paste the content of your SSH public key.
How to copy public key to server?
The simplest way to copy your public key to an existing server is to use a utility called ssh-copy-id. Because of its simplicity, this method is recommended if available.
