Accessibility/Remoteness Index of Australia (ARIA) The Accessibility/Remoteness Index of Australia (ARIA+), like its predecessor ARIA, is an unambiguously geographical approach to defining remoteness. ARIA was created as a joint project with the Australian Department of Health and Ageing in 1998.
Full Answer
What is ARIA (accessible rich Internet applications)?
ARIA Accessible Rich Internet Applications (ARIA) is a set of attributes that define ways to make web content and web applications (especially those developed with JavaScript) more accessible to people with disabilities.
What is Aria and how does it work?
Accessible Rich Internet Applications (ARIA) is a set of attributes that define ways to make web content and web applications (especially those developed with JavaScript) more accessible to people with disabilities.
What is ARIA-body rat (remote access trojan)?
What is Aria-body? Aria-body is malicious software also known as the Aria-body RAT (Remote Access Trojan). RATs allow remote access and control over an infected machine. Aria-body malware has various capabilities/features that enable likewise varied misuse.
What does ARIA+ mean for Australia?
The Accessibility/Remoteness Index of Australia (ARIA+), like its predecessor ARIA, is an unambiguously geographical approach to defining remoteness. ARIA was created as a joint project with the Australian Department of Health and Ageing in 1998.
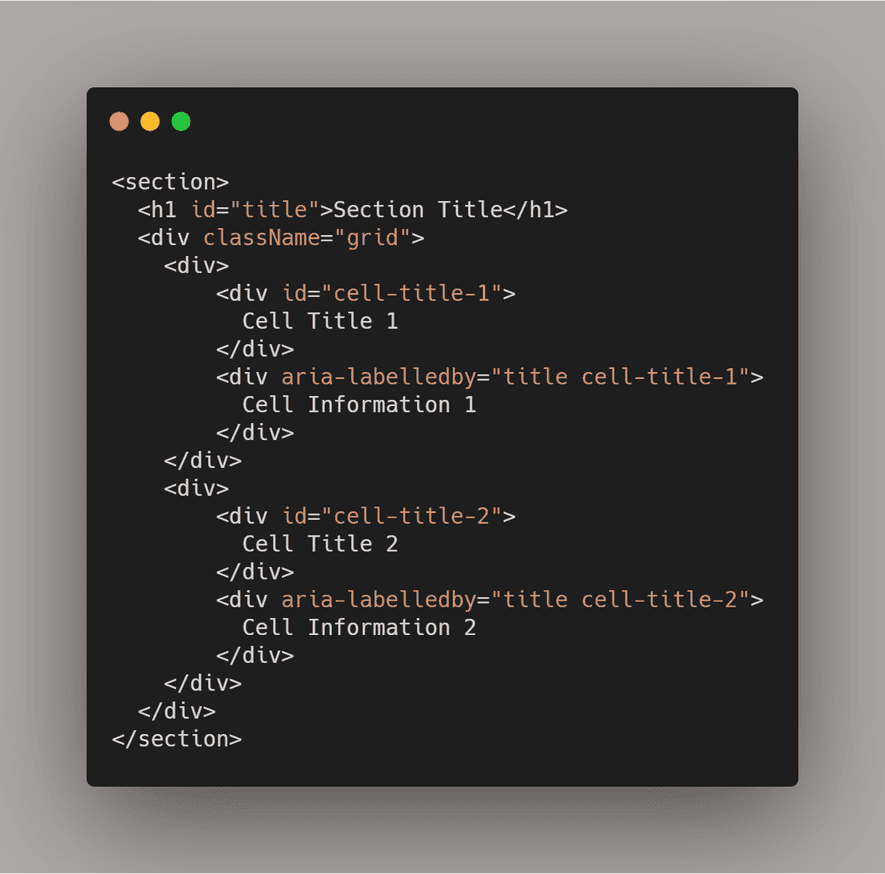
What is ARIA in web development?
Accessible Rich Internet Applications (ARIA) is a set of attributes that define ways to make web content and web applications (especially those developed with JavaScript) more accessible to people with disabilities.
What is ARIA in HTML?
For example, ARIA enables accessible navigation landmarks in HTML4, JavaScript widgets, form hints and error messages, live content updates, and more.
What browsers support live regions?
A quick summary of live regions, by the makers of JAWS screen reader software. Live regions are also supported by NVDA with Firefox, and VoiceOver with Safari.
Can older versions of ARIA be used?
Older software versions may not support certain ARIA roles, have only partial support, or misreport its functionality. It is also important to acknowledge that some people who rely on assistive technology are reluctant to upgrade their software, for fear of losing the ability to interact with their computer and browser.
Is ARIA just for dynamic content?
ARIA is not just for dynamic content! Learn how to improve accessibility of HTML forms using additional ARIA attributes. ARIA for Scripted Widgets. Writing keyboard-navigable JavaScript widgets. Built-in elements like <input>, <button> etc have built-in keyboard accessibility.
Can ARIA be added to JavaScript?
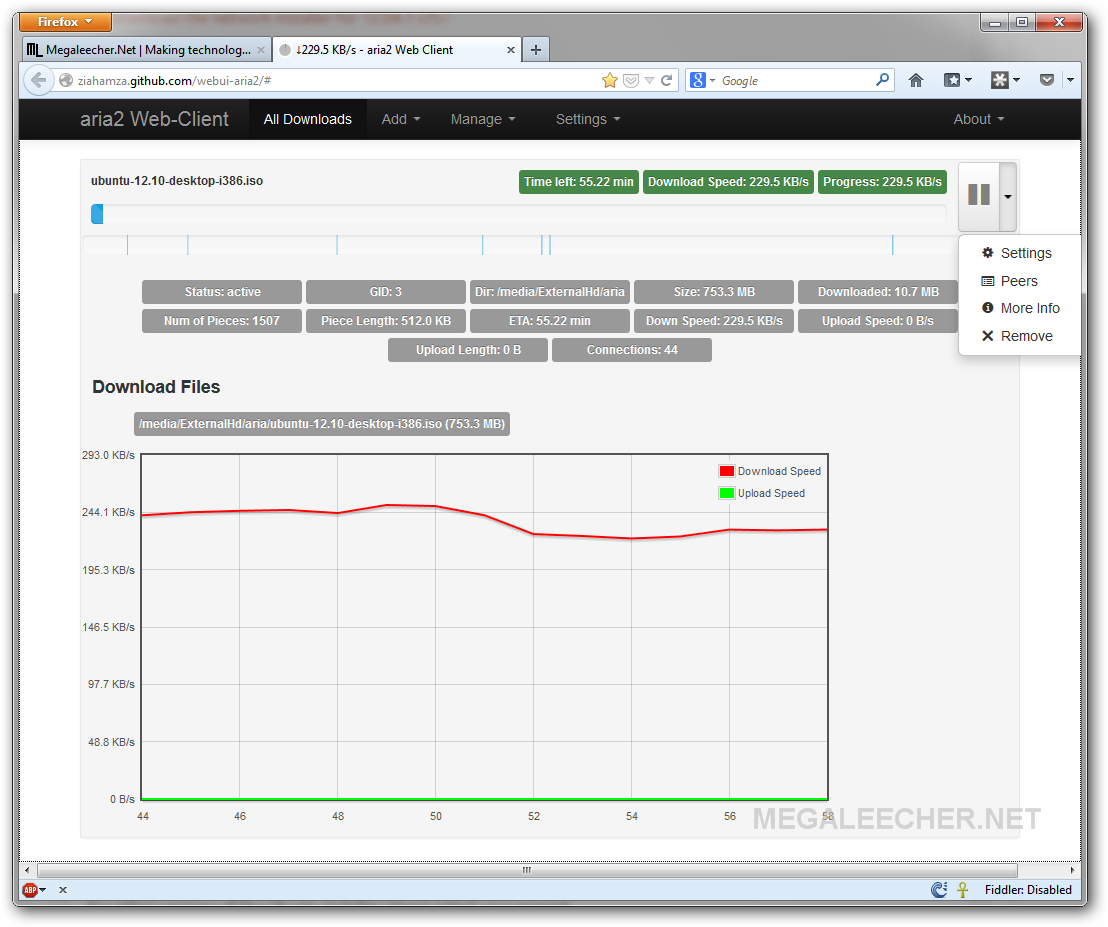
Along with placing them directly in the markup, ARIA attributes can be added to the element and updated dynamically using JavaScript code like this:
Is ARIA used in HTML5?
Many of these widgets were later incorporated into HTML5, and developers should prefer using the correct semantic HTML element over using ARIA, if such an element exists. For instance, native elements have built-in keyboard accessibility, roles and states. However, if you choose to use ARIA, you are responsible for mimicking (the equivalent) browser behavior in script.
What is ARIA Cybersecurity?
ARIA Cybersecurity Solutions are purpose built to move the data on and off servers and network storage faster, at lower power, and with greater reliability.
What is ARIA ADRCloud?
The ARIA ADRCloud monitors all threat surfaces to detect known and novel cyberattacks. It uses ML-based threat detection models, driven by AI, to automatically find and stop threats by their tell-tale behaviors both within the threat analytics, as well as the network data.
What is ARIA ADR dashboard?
With the easy-to-read ARIA ADR dashboard providing metrics and trends related to their overall security posture including a summary of total alerts by status and severity, top hosts and users associated with alerts and 6 month trend information among other analytics.
What is ARIA CloudADR?
The ARIA CloudADR solution is a fully AI-driven, cloud-based SOC for companies that need to protect on-premises and public cloud infrastructure, yet do it much less expensively—and more effectively—than operating a traditional, physical SOC. Another advantage is out-of-the-box functionality of seven different security tools.
What is cloud based security?
Enjoy all the benefits of a cloud-based security solution that is easy to deploy, manage, and use. A cloud solution that can protect the entire enterprise: public cloud, on-premises infrastructure, remote devices. Any resource in charge of cybersecurity, even IT staff, can operate ARIA CloudADR, and on a part-time basis.
What is alert in AI?
Alerts are presented in order of criticality and in easy to understand language to quickly prioritize and focus investigation efforts. Underlying indicators of compromise, correlated by AI, are a click away as you drill down into the alert.
Is ARIA CloudADR a cybersecurity company?
Being fully cloud-based, ARIA CloudADR can be operated anywhere by resources with little to no cybersecurity expertise. With ARIA CloudADR organizations improve the monitoring and enforcement of all security controls, policies, and procedures.
How did Aria-body infiltrate my computer?
Several infection chains of Aria-body have been observed. They were initiated through different infectious files, the delivery methods of which differs as well.
What is the purpose of Aria Body?
Following successful infiltration, and after Aria-body establishes contact with the cyber criminals' C&C (Command and Control) server, it begins investigating the infected device. It collects data concerning the compromised computer : Operating System version and architecture; network details; public IP addresses (through verification on checkip.amazonaws.com); etc.
Is Aria Body malware?
Aria-body is a highly dangerous piece of malicious software, which poses a significant threat to confidential information. Therefore, if it is suspected or known that this, or other malware, has already infected the system, it is crucial to eliminate it immediately.
