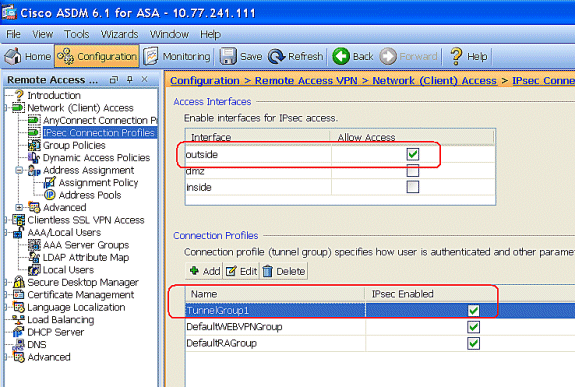
In ASDM, go to Configuration > VPN > Easy VPN Remote to configure the ASA as an Easy VPN Remote hardware client. Go to Configuration > Remote Access > Network (Client) Access > Group Policies > Advanced > IPsec (IKEv1) Client > Hardware Client to configure group policy attributes on the Easy VPN Server. Easy VPN Interfaces
- Check Cisco firewall ASA version. Make sure you have ASA 8.2. ...
- Start Cisco firewall IPsec VPN Wizard. Login to your Cisco firewall ASA5500 ASDM and go to Wizard > IPsec VPN Wizard ... and follow up the screens. ...
- Add Transform Set.
How do I enable IPsec on ASA?
System Options The Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > System Options pane (also reached using Configuration > Site-to-Site VPN > Advanced > System Options) lets you configure features specific to IPsec and VPN sessions on the ASA.
How do I configure an SSL VPN session in ASDM?
You configure the general attributes of an internal group policy in ASDM by selecting Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit > General. The following attributes apply to SSL VPN and IPsec sessions.
How to preview remote-access VPN configuration before sending to Cisco ASA?
If the Preview Command Before Sending to the Device option is enabled in ASDM, the entire remote-access VPN configuration is displayed to you before being sent to the security Cisco ASA. If the configuration looks accurate, click Send to push it to Cisco ASA. Example 21-2 shows the complete remote-access VPN configuration created by ASDM.
How do I configure IPsec over NAT-T with ASDM?
In ASDM, choose Configuration > Site-to-Site VPN > Connection Profiles . Select the interfaces you want to use IKEv1 and IKEv2 on. In ASDM, choose Configuration > Site-to-Site VPN > Advanced > IKE Parameters. IPsec over NAT-T lets IPsec peers establish both remote access and LAN-to-LAN connections through a NAT device.

How configure Cisco AnyConnect ASDM?
Setup AnyConnect From ASDM (Local Authentication) Launch the ASDM > Wizards > VPN Wizards > AnyConnect VPN Wizard > Next. Give the AnyConnect profile a name i.e PF-ANYCONNECT, (I capitalise any config that I enter, so it stands out when I'm looking at the firewall configuration). > Next > Untick IPSec > Next.
How do I configure IPSec on ASA firewall?
To configure the IPSec VPN tunnel on Cisco ASA 55xx:Configure IKE. Establish a policy for the supported ISAKMP encryption, authentication Diffie-Hellman, lifetime, and key parameters. ... Create the Access Control List (ACL) ... Configure IPSec. ... Configure the Port Filter. ... Configure Network Address Translation (NAT)
How do I access ASA through ASDM?
Open the shortcut and fill in the IP address (192.168. 1.1), leave the username blank and put in the password firewall. The ASDM will then connect to the ASA and load the java interface. You can now configure the ASA as per your requirements.
How configure Cisco ASA site to site VPN?
1:0814:10Cisco ASA Site-to-Site VPN Configuration (Command Line)YouTubeStart of suggested clipEnd of suggested clipFirst of all we need to go into configuration mode so config T and now we're going to enable ISOMoreFirst of all we need to go into configuration mode so config T and now we're going to enable ISO camp on the outside interface that ISO camp is the handshake part of the configuration.
How do I find my IPsec VPN in Asa?
Need to check how many tunnels IPSEC are running over ASA 5520....Please try to use the following commands.show vpn-sessiondb l2l.show vpn-sessiondb ra-ikev1-ipsec.show vpn-sessiondb summary.show vpn-sessiondb license-summary.and try other forms of the connection with "show vpn-sessiondb ?"
How do I setup a website for IPsec VPN?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
What is ASDM in ASA?
Cisco Adaptive Security Device Manager - Cisco.
How do I know if ASDM is enabled?
Commands: show run http [check if http server is enabled, and http access is allowed on the interface you are trying to access.] show run asdm [check that an asdm image is mentioned, and the version is compatible with the ASA image version.] show flash [check that the asdm image mentioned is present in the flash.]
What port does ASDM use?
Both SSL VPN and ASDM use the HTTPs protocol for communication which uses port 443 by default.
What is Cisco ASA site-to-site VPN?
Site-to-site IPsec VPNs are used to “bridge” two distant LANs together over the Internet. Normally on the LAN we use private addresses so without tunneling, the two LANs would be unable to communicate with each other.
What is site-to-site IPsec VPN?
A site-to-site VPN is a permanent connection designed to function as an encrypted link between offices (i.e., “sites”). This is typically set up as an IPsec network connection between networking equipment.
How does IPsec VPN Work?
IPsec is a group of protocols that are used together to set up encrypted connections between devices. It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from.
Does Cisco ASA supports route based VPN?
Policy-Based IPSEC VPN This VPN category is supported on both Cisco ASA Firewalls and Cisco IOS Routers. With this VPN type the device encrypts and encapsulates a subset of traffic flowing through an interface according to a defined policy (using an Access Control List).
How do I enable IKEv1 on Cisco ASA?
Enable IKEv1 on the the interfaceIntroduction.Define the Encryption Domain.Specify the Phase 1 Policy.Specify the Phase 2 Proposal.Define the connection profile.Configure the Crypto Map.Bind the Crypto Map to the interface.Enable IKEv1 on the the interface.
What is difference between IKEv1 and IKEv2?
IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication. IKEv2 has the Keep Alive option enabled as default.
How does IPsec VPN Work?
IPsec is a group of protocols that are used together to set up encrypted connections between devices. It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from.
What is IPsec over NAT-T?
IPsec over NAT-T lets IPsec peers establish both remote access and LAN-to-LAN connections through a NAT device. It does this by encapsulating IPsec traffic in UDP datagrams, using port 4500, thereby providing NAT devices with port information. NAT-T auto-detects any NAT devices, and only encapsulates IPsec traffic when necessary. This feature is enabled by default.
How to configure IKE parameters in ASDM?
In ASDM go to Configuration > Site-to-Site VPN > Advanced > IKE parameters.
What is IKE in VPN?
IKE, also called ISAKMP , is the negotiation protocol that lets two hosts agree on how to build an IPsec security association. To configure the ASA for Virtual Private Networks, you set global IKE parameters that apply system wide, and you also create IKE policies that the peers negotiate to establish a VPN connection.
How to prevent denial of service attacks?
You can prevent denial-of-service (DoS) attacks for IPsec IKEv2 connections by configuring Cookie Challenge, which challenges the identify of incoming Security Associations (SAs), or by limiting the number of open SAs. By default, the ASA does not limit the number of open SAs, and never cookie challenges SAs. You can also limit the number of SAs allowed, which stops further connections from negotiating to protect against memory and/or CPU attacks that the cookie-challenge feature may be unable to thwart and protects the current connections.
Does ASA work for LAN to LAN?
It does not work for LAN-to-LAN connections. The ASA can simultaneously support standard IPsec, IPsec over TCP, NAT-Traversal, and IPsec over UDP, depending on the client with which it is exchanging data. When enabled, IPsec over TCP takes precedence over all other connection methods.
Do you need a dynamic tunnel policy?
If you are only using your security appliance as a VPN client in relation to a remote VPN central-site device, you do not need to configure any dynamic tunnel policies. Dynamic tunnel policies are most useful for allowing remote access clients to initiate a connection to your network through a security appliance acting as ...
Does IKE v2 limit SAs?
Additional session controls are available for IKE v2, that limit the number of open SAs. By default, the ASA does not limit the number of open SAs:
What is Easy VPN Remote?
Upon tunnel establishment, the Easy VPN Remote specifies the tunnel group, configured on the Easy VPN Server, that will be used for the connection. The Easy VPN Server pushes group policy or user attributes to the Easy VPN Remote hardware client determining tunnel behavior. To change certain attributes, you must modify them on the ASAs configured as primary or secondary Easy VPN Servers.
What is the easiest VPN?
The physical interface with the lowest security level is used for the external connection to an Easy VPN server. The physical or virtual interface with the highest security level is used for the internal connection to secure resources. If Easy VPN determines that there are two or more interfaces with the same highest security level, Easy VPN is disabled.
What VPN uses IKEv1?
Easy VPN uses IPsec IKEv1 tunnels. The Easy VPN Remote hardware client's configuration must be compatible with the VPN configuration on the Easy VPN Server headend. If using secondary servers, their configuration must be identical to the primary server.
How does ASA work?
The ASA creates a Virtual Private Network by creating a secure connection across a TCP/IP network (such as the Internet) that users see as a private connection. It can create single-user-to-LAN connections and LAN-to-LAN connections.
What is phase 2 in IPsec?
In IPsec negotiations, Phase 2 keys are based on Phase 1 keys unless PFS is enabled. PFS uses Diffie-Hellman techniques to generate the keys. PFS ensures that a session key derived from a set of long-term public and private keys is not compromised if one of the private keys is compromised in the future.
What is IKEv2 remote access?
Use the IKEv2 Remote Access Wizard to configure secure remote access for VPN clients, such as mobile users, and to identify the interface that connects to the remote IPsec peer.
What happens when you connect to an ASA?
When users connect to the ASA, all traffic is tunneled through the connection and users cannot access resources on their local network. This includes printers, cameras, and Windows Mobile devices (tethered devices) that synchronize with the local computer. Enabling Local LAN Access in the client profile resolves this problem, however it can introduce a security or policy concern for some enterprises as a result of unrestricted access to the local network. You can use the ASA to deploy endpoint OS firewall capabilities to restrict access to particular types of local resources, such as printers and tethered devices.
What is VPN group policy?
A VPN group policy is a collection of user-oriented attribute/value pairs stored either internally on the device or externally on a RADIUS or LDAP server. Configuring the VPN group policy lets users inherit attributes that you have not configured at the individual group or username level. By default, VPN users have no group policy association. The group policy information is used by VPN tunnel groups and user accounts.
What is the Add TCP Service Group dialog box?
The Add TCP Service Group dialog box lets you configure a new a TCP service group or port to add to the browsable source or destination port list for this protocol in this rule. Selecting a member of either the Members not in Group or the Members in Group list activates the Add and Remove buttons.
What is the add/edit/paste ACE dialog box?
The Add/Edit/Paste ACE dialog box lets you create a new extended ACE, or modify an existing rule. The Paste option becomes available only when you cut or copy a rule.
How many client access rules can you see in thisdialog?
The Client Access Rules table in thisdialog box lets you view up to 25 client access rules. If you uncheck the Inherit check box, the Add, Edit, and Delete buttons become active and the following column headings appear in the table:
What are portal attributes?
The Portal attributes determine what appears on the portal page for members of this group policy establishing Clientless SSL VPN connections. In this pane, you can enable Bookmark lists and URL Entry, file server access, Port Forwarding and Smart Tunnels, ActiveX Relay, and HTTP settings.
Can Cisco devices be used for authentication?
Certain devices like Cisco IP phones, printers, and the like are incapable of performing authentication, and therefore of participating in individual unit authentication. To accommodate these devices, the device pass-through feature, enabled by the MAC Exemption attributes, exempts devices with the specified MAC addresses from authentication when Individual User Authentication is enabled.
Chapter: Easy VPN
This chapter describes how to configure any ASA as an Easy VPN Server, and the Cisco ASA with FirePOWER- 5506-X, 5506W-X, 5506H-X, and 5508-X models as an Easy VPN Remote hardware client.
Easy VPN Interfaces
Upon system startup, the Easy VPN external and internal interfaces are determined by their security level. The physical interface with the lowest security level is used for the external connection to an Easy VPN server. The physical interface with the highest security level is used for the internal connection to secure resources.
Easy VPN Connections
Easy VPN uses IPsec IKEv1 tunnels. The Easy VPN Remote hardware client's configuration must be compatible with the VPN configuration on the Easy VPN Server headend. If using secondary servers, their configuration must be identical to the primary server.
Easy VPN Tunnel Groups
Upon tunnel establishment, the Easy VPN Remote specifies the tunnel group, configured on the Easy VPN Server, that will be used for the connection. The Easy VPN Server pushes group policy or user attributes to the Easy VPN Remote hardware client determining tunnel behavior.
Easy VPN Mode of Operation
The mode determines whether the hosts behind the Easy VPN Remote are accessible or not from the enterprise network over the tunnel:
Easy VPN User Authentication
The ASA Easy VPN Remote can store the username and password for automatic login.
Remote Management
The ASA operating as an Easy VPN Remote hardware client supports management access using SSH or HTTPS, with or without additional IPsec encryption.
How to manage ASA?
To list the things you need to do to manage the ASA through the VPN connection you have to atleast do these things. Configure the VPN Client connection. Confirm that the interface IP address to which you want to connect to is included in the VPN so the users traffic to that IP gets forwarded to the VPN connection.
What is management access?
This command should not affect any existing management connection/configuration you have on the ASA already. The "management- access" command can be active only for a single interface at a time.
Can you create a VPN pool?
You can create the VPN Pool to be pretty much any subnet you want. Typically its some private IP address range. It should be something different from the LAN subnet atleast that you have behind the ASA. The ASA configured with a VPN Pool will give the VPN Client user the IP address from that pool.
Can I use SSH and ASDM to manage an ASA?
And I would like to point out that you can use both SSH and ASDM (HTTPS/SSL) to manage the ASA from the external network without using any form of VPN for this. You can connect to the external interface IP address of the ASA directly. In those cases you could simply add the "http" and "ssh" statements on the ASA to allow the management connections from specific hosts/subnets. Naturally if you dont manage the ASA externally from a specific IP address always then this might not be an option if you want to keep the ASA as secure as possible with regards to management connection options.
Can ASA use VPN?
Any ASA can be configured to use IPsec VPN Client as each unit has support for this. This however uses the older Cisco VPN Client which I guess is not really supported/updated by Cisco anymore. The current way of doing VPN Client connections would be to use the AnyConnect VPN Client.
Can you manage ASA through VPN?
But after you have configured the VPN there are still some configurations you would need to add to be able to manage the ASA through the VPN connections. These settings are not done through any Wizard on the ASDM. (Atleast to my understanding)
Can I use VPN on ASA 5545?
Yes it would be the first time i will be configuring VPN on my ASA 5545 9.1.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What is dynamic crypto map?
Dynamic crypto maps define policy templates in which not all the parameters are configured. This lets the ASA receive connections from peers that have unknown IP addresses, such as remote access clients.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.