Even though the address pool under the tunnel-group is local, ASA will still try to allocate IP address from AAA Server Group if the command vpn-addr-assign aaa. This command can't be ignored. The only way to override it is to authenticate that tunnel-group with local ASA DB instead of AAA Server.
Full Answer
What is Cisco ASA remote access VPN?
Cisco ASA Remote Access VPN. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network. The Cisco VPN client is end-of-life and has been replaced by the Cisco Anyconnect Secure Mobility Client.
How do I connect to the ASA from another computer?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
How does Asa connect to the Active Directory domain controller?
The user is authenticated by the Active Directory domain controller via LDAP. The ASA uses the inside interface to connect to the Active Directory domain controller on the corporate network.
How to reactivate a failed AAA server in ASA?
There are two different AAA server reactivation modes in ASA: timed mode and depletion mode. The command below is the timed mode. With the timed mode, it reactivates a failed server after 30 seconds of downtime. In my limited testing, it continuously tried to reactivate the server after 30 seconds when I bring the TACACS+ server down.
What is ASA in Cisco 5500?
How to assign IP address to VPN?
What does show crypto isakmp SA mean?
How to enable IKE on VPN?
See more
About this website
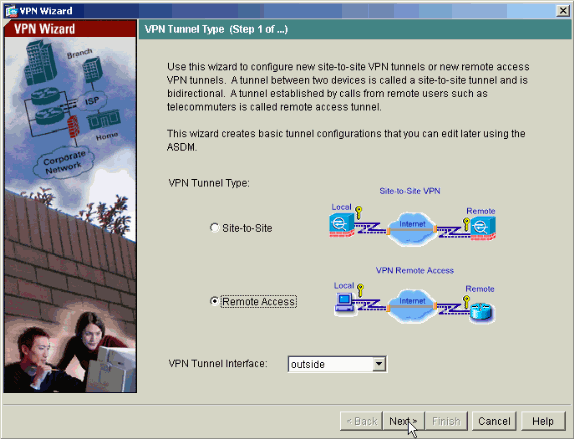
How do I assign a static IP address to AnyConnect?
AD Account ModificationTick the “Assign Static IP Address” box.Click the “Static IP Address” button.Tick “Assign a static IPv4 address” box and enter and IP address from within the IP address range defined on the Cisco ASA appliances.
How do I enable AAA on ASA?
Complete the following steps to configure authentication for serial console connections to the Cisco ASA, using ASDM:Log in to ASDM and navigate to Configuration > Device Management > Users/AAA > AAA Access > Authentication.Select Serial under the Require Authentication for the Following Types of Connections section.More items...•
How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
How do I assign an IP address to Asa?
Set a Static IP for your Cisco ASA5505 FirewallOpen the ASDM and log into your device.Under Configuration, Interfaces, select the Outside interface and hit Edit.In the 'IP Address' box, click the radio for 'Use Static IP'Select an IP address, and use '255.255. ... Hit ok, then apply.More items...•
How do I find my AAA configuration?
Log into the ADSM > Configuration > Device Management > Users/AAA > Select the Server Group > Select the Server > Test. Select 'Authentication' > Enter Username/Password > OK.
How do you set up a AAA server?
Configuring AAA ServersGo to Admin & Services > Services > AAA Servers.In Authentication Servers, click Create New.Select the server type: Active Directory: If you use a Microsoft AD server, configure the following settings: ... Click OK to save your AAA server entry.
How do I connect to Cisco ASA?
Complete the below steps.Configure the management interface. conf t. int e 0/2. ip address 192.168.100.2 255.255.255.0. nameif manage. security-level 80. exit. exit.Configure the username and privilege. username Test password Test@Cisco privilege 15.Configure the Cisco ASA to allow http connections.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I configure AnyConnect on ASA 5505?
Quick guide: AnyConnect Client VPN on Cisco ASA 5505Click on Configuration at the top and then select Remote Access VPN.Click on Certificate Management and then click on Identity Certificates.Click Add and then Add a new identity certificate.Click New and enter a name for your new key pair (ex: VPN)More items...•
What is Nameif on ASA?
The nameif command is used to specify a name for the interface, unlike the description command the name of your interface is actually used in many commands so pick something useful. As you can see the ASA recognizes INSIDE, OUTSIDE and DMZ names. It uses a default security level of 100 for INSIDE and 0 for OUTSIDE/DMZ.
How configure firewall in ASA step by step?
Cisco ASA 5505 configurationStep1: Configure the internal interface vlan. ... Step 2: Configure the external interface vlan (connected to Internet) ... Step 3: Assign Ethernet 0/0 to Vlan 2. ... Step 4: Enable the rest interfaces with no shut. ... Step 5: Configure PAT on the outside interface. ... Step 6: Configure default route.
How configure DHCP in Asa?
0:3511:2813 Configure DHCP server in cisco ASA firewall | ASA Training - YouTubeYouTubeStart of suggested clipEnd of suggested clipService for this interface gigabit ethernet zero slash one and gigabit ethernet zero slash. Two. SoMoreService for this interface gigabit ethernet zero slash one and gigabit ethernet zero slash. Two. So this is five one will provide ip address automatically to all the clients. As they are leaving.
How do I enable Cisco AnyConnect VPN through Remote Desktop?
The steps would be:Log into the ASDM.Go to Configuration, Remote Access VPN, Anyconnect Client Profile.Click Add and create a new profile and choose the Group Policy it should apply to.Click OK, and then at the Profile screen click "Apply" at the bottom (important)More items...•
How do I download AnyConnect from Asa?
Just load a new image to the ASA (under Configuration -> Remote-Access VPN -> Network (Client) Access -> AnyConnect Client Software) and the client will load the new software the next time when the client connects. Of course the client shouldn't have a setting applied to not download new software.
How do I enable telnet on ASDM?
Allow Telnet – Via ASDM (version shown 6.4(7)) Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select Telnet > Supply the IP and subnet > OK.
assign a static IP to a specific VPN client - Cisco Community
hey , as the subject, i want to assign a static IP to a specific vpn client. so everytime the user account dial in the ASA, will got the same VPN IP. i am using l2tp over ipsec vpn, and integrated with windows NPS server (as aaa server). below is my configuration: ip local pool xhdcvpn_addr 10.25.0...
Solved: Anyconnect user static IP - Cisco Community
Guys, looking for DC-DR static IP solution for Anyconnect VPN clients. Current architecture is Anyconnect <> DC ASA <> DC ISE <> Corp AD Anyconnect user gets a static IP. IP is binded to static IP properties of AD user in Dial-in Tab. DC ISE fetches this IP (192.168.31.x range) and passes on to ...
Set a Static IP for your Cisco ASA5505 Firewall
11 thoughts on “ Set a Static IP for your Cisco ASA5505 Firewall ” Ted Trerice December 8, 2017 at 9:02 am. I have a similar setup, followed your advice, but still does not pass traffic. It assigns the ip address, and the dns and dhcp is setup, but it appears there is a nat firewall issue of some kind.
Cisco ASA VPN - Returning IETF-Framed-IP-Address | Security
Hi Tim, this looks like an old post but we are trying to do this now for our VPN setup with Clearpass and static IPs in AD. In clearpass, I am able to see the dialin IP of the user coming from AD (following your instructions) however when it gets time to send it with the enforcement profile, Clearpass isn't sending it to our ASA.
Configure Static IP Address Assignment to AnyConnect Users via RADIUS ...
The debug radius all command output on FTD shows: firepower# SVC message: t/s=5/16: The user has requested to disconnect the connection. webvpn_svc_np_tear_down: no ACL
What does ASA do on Telnet?
For Telnet and FTP, the ASA generates an authentication prompt.
Why is ASA cut through proxy important?
The ASA uses “cut-through proxy” to significantly improve performance compared to a traditional proxy server. The performance of a traditional proxy server suffers because it analyzes every packet at the application layer of the OSI model. The ASA cut-through proxy challenges a user initially at the application layer and then authenticates with standard AAA servers or the local database. After the ASA authenticates the user, it shifts the session flow, and all traffic flows directly and quickly between the source and destination while maintaining session state information.
How to configure ACL netmask conversion?
You configure ACL netmask conversion on a per-server basis: CLI: using the acl-netmask-convert command, available in the aaa-server configuration mode; when you add a server to a server group in the Configuration > Device Management > Users/AAA > AAA Server Groups > AAA Server Groups area.
What is an AAA rule?
An authentication rule (also known as “cut-through proxy”) controls network access based on the user. Because this function is very similar to an access rule plus an identity firewall, AAA rules can now be used as a backup method of authentication if a user AD login expires or a valid user has not yet logged into AD. For example, for any user without a valid login, you can trigger a AAA rule. To ensure that the AAA rule is only triggered for users that do not have valid logins, you can specify special usernames in the extended ACL that are used for the access rule and for the AAA rule: None (users without a valid login) and Any (users with a valid login). In the access rule, configure your policy as usual for users and groups, but then include a rule that permits all None users before deny any any; you must permit these users so they can later trigger a AAA rule. Then, configure a AAA rule that does not match Any users (these users are not subject to the AAA rule, and were handled already by the access rule), but matches all None users only to trigger AAA authentication for these users. After the user has successfully logged in via cut-through proxy, the traffic will flow normally again.
How many times does a user need to authenticate for a given IP address?
A user at a given IP address only needs to authenticate one time for all rules and types, until the authentication session expires. ( CLI: See the timeout uauth command in the command reference for timeout values.) ( ASDM: See the Configuration > Firewall > Advanced > Global Timeouts pane for timeout values.) For example, if you configure the ASA to authenticate Telnet and FTP, and a user first successfully authenticates for Telnet, then as long as the authentication session exists, the user does not also have to authenticate for FTP.
How to configure Uauth session limit?
You can manually configure the uauth session limit by setting the maximum number of concurrent proxyconnections allowed per user.
Can you download ACLs on Cisco Secure ACS?
You can configure downloadable ACLs on Cisco Secure ACS as a shared profile component and then assign the ACL to a group or to an individual user.
What does ASA do during authentication?
During authentication, the ASA retrieves the value of physicalDeliveryOfficeName from the server, maps the value to the Cisco attribute Banner1, and displays the banner to the user.
How to enforce a banner on LDAP?
To enforce a simple banner for a user who is configured on an AD LDAP server use the Office field in the General tab to enter the banner text. This field uses the attribute named physicalDeliveryOfficeName. On the ASA, create an attribute map that maps physicalDeliveryOfficeName to the Cisco attribute Banner1.
What happens after LDAP authentication?
After LDAP authentication for VPN access has succeeded, the ASA queries the LDAP server, which returns LDAP attributes. These attributes generally include authorization data that applies to the VPN session.
How to place LDAP user into a group policy?
To place an LDAP user into a specific group policy use the Department field of the Organization tab to enter the name of the group policy. Then create an attribute map, and map Department to the Cisco attribute IETF-Radius-Class.
What is LDAP attribute?
LDAP attributes are a subset of the Radius attributes, which are listed in the Radius chapter.
What is authorization in LDAP?
Authorization refers to the process of enforcing permissions or attributes. An LDAP server defined as an authentication or authorization server enforces permissions or attributes if they are configured.
What is the AV number?
The Cisco Attribute Value (AV) pair (ID Number 26/9/1) can be used to enforce access lists from a RADIUS server (like Cisco ACS), or from an LDAP server via an LDAP attribute map.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
What is serial port in ASA?
Don’t get confused with the keyword console and serial console. The serial is the actual physical console port in the ASA. If you do not issue this command, ASA will use the user local user database for authentication. Same thing as above, if TACACS+ is available then it will always use the stored account on the server before using the local account.
How long does a tacs server stay down?
With the depletion mode shown below, the failed TACACS+ server will stay down until all servers in the group are in the failed state. The default deadtime is 10 minutes.
About External AAA Servers
This ASA can be configured to use an external LDAP, RADIUS, or TACACS+ server to support Authentication, Authorization, and Accounting (AAA) for the ASA. The external AAA server enforces configured permissions and attributes.
Guidelines For Using External AAA Servers
The ASA enforces the LDAP attributes based on attribute name, not numeric ID. RADIUS attributes, are enforced by numeric ID, not by name.
Configure Multiple Certificate Authentication
You can now validate multiple certificates per session with AnyConnect SSL and IKEv2 client protocols. For example, you can make sure that the issuer name of the machine certificate matches a particular CA and therefore that the device is a corporate-issued device.
What is ASA in Cisco 5500?
This document describes how to configure the Cisco 5500 Series Adaptive Security Appliance (ASA) to provide the Static IP address to the VPN client with the Adaptive Security Device Manager (ASDM) or CLI. The ASDM delivers world-class security management and monitoring through an intuitive, easy-to-use Web-based management interface. Once the Cisco ASA configuration is complete, it can be verified with the Cisco VPN Client.
How to assign IP address to VPN?
Choose Advanced > Client Addressing and check the Use address pool check box to assign the IP Address to the VPN clients.
What does show crypto isakmp SA mean?
show crypto isakmp sa —Shows all current IKE Security Associations (SAs) at a peer.
How to enable IKE on VPN?
Choose Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPSec > IKE Parameters to enable the IKE on the Outside Interface.

Prerequisites
- Requirements
This document assumes that the ASA is fully operational and configured to allow the Cisco ASDM or CLI to make configuration changes. Note: Refer to Allowing HTTPS Access for ASDM or PIX/ASA 7.x: SSH on the Inside and Outside Interface Configuration Exampleto allow the device t…
Configure
- In this section, you are presented with the information to configure the features described in this document. Note: Use the Command Lookup Tool (registeredcustomers only) in order to obtain more information on the commands used in this section.
Verify
- show Commands
Use this section to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of showcommand output. 1. show crypto isakmp sa—Shows all current IKE Security As…
Troubleshoot
- This section provides information you can use to troubleshoot your configuration. Sample debug output is also shown. Note: For more information on troubleshooting Remote Access IPSec VPN refer Most Common L2L and Remote Access IPSec VPN Troubleshooting Solutions.
Related Information