
What Nat do you use with ASA1 and asa2?
ASA1 and ASA2 use NAT to translate traffic from S1 and S2 to the IP address on their GigabitEthernet 0/0 interfaces. We use an IPSec IKEv2 VPN tunnel between ASA1 and ASA2 for traffic between S1 and S2. HTTP server runs on S1, S2, and S3, so that we have something to connect to. I use ASAv 9.9 (2) for this example. Want to take a look for yourself?
How do remote access clients connect to Asa?
As remote access clients connect to the ASA, they connect to a connection profile, which is also known as a tunnel group. We’ll use this tunnel group to define the specific connection parameters we want them to use.
What is the basic Asa configuration setup?
The basic ASA configuration setup is three interfaces connected to three network segments. The ISP network segment is connected to the Ethernet0/0 interface and labelled outside with a security level of 0.
What VPN tunnel do you use between ASA1 and asa2?
We use an IPSec IKEv2 VPN tunnel between ASA1 and ASA2 for traffic between S1 and S2. HTTP server runs on S1, S2, and S3, so that we have something to connect to. I use ASAv 9.9 (2) for this example.
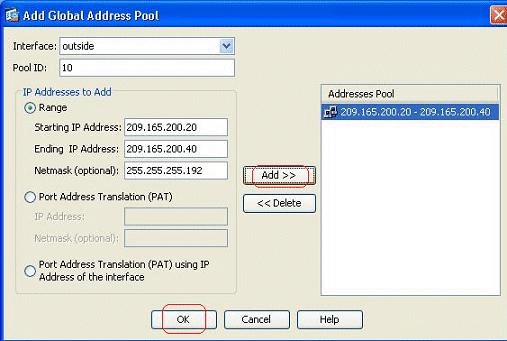
How NAT works on Cisco ASA?
Network Address Translation is used for the translation of private IP addresses into public IP addresses while accessing the internet. NAT generally operates on a router or firewall. In this type of NAT, multiple private IP addresses are mapped to a pool of public IP addresses.
How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
How do I make my NAT private to public in Cisco ASA?
Give the 'object' a name (I usually prefix them with obj-{name}) > It's a Host > Type in it's PRIVATE IP address > Tick the NAT section (press the drop-down if its hidden) > Static > Enter it's PUBLIC IP address > Advanced > Source = Inside > Destination > Outside > Protocol TCP.
What are different types of NAT in Asa?
Cisco ASA NAT – Contents:Static NAT.Static PAT.Dynamic PAT.Dynamic NAT.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I connect to Cisco ASA?
Complete the below steps.Configure the management interface. conf t. int e 0/2. ip address 192.168.100.2 255.255.255.0. nameif manage. security-level 80. exit. exit.Configure the username and privilege. username Test password Test@Cisco privilege 15.Configure the Cisco ASA to allow http connections.
What is auto NAT in Cisco ASA?
Auto NAT is configured using the following steps: Create a network object. Within this object define the Real IP/Network to be translated. Also within this object you can use the the nat commands to specify whether the translation will be dynamic or static.
How do I remove static NAT from Cisco ASA?
Clear all old NAT translations. router#clear ip nat translatiom *Disable old NAT pool settings. router(config)#no ip nat pool public_access 200.100.10.33 netmask 255.255.255.252.And finally, disable the translation:
What is identity NAT in Cisco ASA?
The identity NAT translates the source IP to itself so it maintains its IP through the ASA when there are dynamic NATs present on the ASA. An example of use for identity NAT would be for a site to site VPN or remote access VPN.
What is difference between auto NAT and manual NAT in Asa?
An Auto-NAT rule only uses the source address and port when matching and translating. Manual NAT can match and translate source and destination addresses and ports. In both cases, the Translated Source may be the IP of the egress interface or an object. The PAT Pool option is available when using dynamic translations.
What is source NAT and destination NAT in Asa?
Destination NAT enables the translation of one destination address to another, a destination address and port to another destination address and port, or a group of destination addresses to another group of equal size. Source NAT is the translation of source IP addresses and TCP/UDP ports in the headers of IP flows.
How many NAT types are there?
three different NAT typesThe three different NAT types are Open, Moderate, and Strict. Your NAT type is typically the result of the network you are using to connect to the Internet, and influenced by the settings or features of the router or gateway on that network.
How do I enable Cisco AnyConnect VPN through Remote Desktop?
The steps would be:Log into the ASDM.Go to Configuration, Remote Access VPN, Anyconnect Client Profile.Click Add and create a new profile and choose the Group Policy it should apply to.Click OK, and then at the Profile screen click "Apply" at the bottom (important)More items...•
How do I download AnyConnect from Asa?
Just load a new image to the ASA (under Configuration -> Remote-Access VPN -> Network (Client) Access -> AnyConnect Client Software) and the client will load the new software the next time when the client connects. Of course the client shouldn't have a setting applied to not download new software.
How do I enable telnet on ASDM?
Allow Telnet – Via ASDM (version shown 6.4(7)) Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select Telnet > Supply the IP and subnet > OK.
What is NAT on ASA?
NAT on the ASA in version 8.3 and later is broken into two types known as Auto NA T (Object NAT) and Manual NAT (Twice NAT). The first of the two, Object NAT, is configured within the definition of a network object. An example of this is provided later in this document. One primary advantage of this NAT method is that the ASA automatically orders the rules for processing in order to avoid conflicts. This is the easiest form of NAT, but with that ease comes a limitation in configuration granularity. For example, you cannot make a translation decision based on the destination in the packet as you could with the second type of NAT, Manual Nat. Manual NAT is more robust in its granularity, but it requires that the lines be configured in the correct order so that it can achieve the correct behavior. This complicates this NAT type, and as a result it will not be used in this configuration example.
What is ASA configuration?
The basic ASA configuration setup is three interfaces connected to three network segments. The ISP network segment is connected to the Ethernet0/0 interface and labelled outside with a security level of 0. The internal network has been connected to Ethernet0/1 and labelled as inside with a security level of 100. The DMZ segment, where the web server resides, is connected to Ethernet0/2 and labelled as DMZ with a security level of 50.
What does ASA 8.2 mean?
In earlier versions of ASA code (8.2 and earlier), the ASA compared an incoming connection or packet against the ACL on an interface without untranslating the packet first. In other words, the ACL had to permit the packet as if you were to capture that packet on the interface. In version 8.3 and later code, the ASA untranslates that packet before it checks the interface ACLs. This means that for 8.3 and later code, and this document, traffic to the host's real IP is permitted and not the host's translated IP.
What is object NAT?
The first thing to configure is the NAT rules that allow the hosts on the inside and DMZ segments to connect to the Internet. Because these hosts use private IP addresses, you need to translate them to something that is routable on the Internet.
What is an access control list?
Access Control Lists (Access-lists or ACLs for short) are the method by which the ASA firewall determines if traffic is permitted or denied. By default, traffic that passes from a lower to higher security level is denied. This can be overridden by an ACL applied to that lower security interface. Also the ASA, by default, allows traffic from higher to lower security interfaces. This behavior can also be overridden with an ACL.
What port is 192.168.1.100?
When a host that matches the IP address 192.168.1.100 on the DMZ segments establishes a connection sourced from TCP port 80 (www) and that connection goes out the outside interface, you want to translate that to be TCP port 80 (www) on the outside interface and translate that IP address to be 198.51.100.101.
What level can a host connect to a DMZ?
Hosts on the inside (security level 100) can connect to hosts on the DMZ ( security level 50).
Introduction
This document describes how to configure an Access Control List (ACL) on the Adaptive Security Appliance (ASA) for various scenarios.
Background Information
ACLs are used by the ASA to determine if traffic is permitted or denied. By default, traffic that passes from a lower security level interface to a higher security level interface is denied whereas traffic from a higher security level interface to a lower security level interface is allowed.
Configure
The client on the internet, located behind the outside interface wants to access a web server hosted behind the DMZ interface listening on TCP ports 80 and 443.
Logging
The log keyword sets logging options when an ACE matches a packet for network access (an ACL applied with the access-group command). If you enter the log keyword without any arguments, you enable system log message 106100 at the default level (6) and for the default interval (300 seconds).
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
What is the order of operation of ASA?
The ASA’s order of operation is that it first translates a packet with NAT, then checks if the packet should be encrypted or not. This packet doesn’t match our LAN1_LAN2 access-list, so it won’t be encrypted. ASA2 drops the packet because no access-list permits traffic from the outside to the inside.
What is NAT exemption?
NAT exemption allows you to exclude traffic from being translated with NAT. One scenario where you usually need this is when you have a site-to-site VPN tunnel. In this lesson, I’ll walk you through a scenario and explain what happens with and without NAT exemption.
Why does ASA2 drop packets?
ASA2 drops the packet because no access-list permits traffic from the outside to the inside.
What is S3 in ASA2?
S3 is a server on the Internet. ASA1 and ASA2 use NAT to translate traffic from S1 and S2 to the IP address on their GigabitEthernet 0/0 interfaces. We use an IPSec IKEv2 VPN tunnel between ASA1 and ASA2 for traffic between S1 and S2. HTTP server runs on S1, S2, and S3, so that we have something to connect to.

Introduction
Prerequisites
- Requirements
There are no specific requirements for this document. - Components Used
The information in this document is based on an ASA 5510 firewall that runs ASA code version 9.1(1). The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configurati…
Overview
- Goals
In this example configuration, you can look at what NAT and ACL configuration will be needed in order to allow inbound access to a web server in the DMZ of an ASA firewall, and allow outbound connectivity from internal and DMZ hosts. This can be summarized as two goals: 1. Allow hosts … - Access Control List Overview
Access Control Lists (Access-lists or ACLs for short) are the method by which the ASA firewall determines if traffic is permitted or denied. By default, traffic that passes from a lower to higher security level is denied. This can be overridden by an ACL applied to that lower security interface…
Configure
- Get Started
The basic ASA configuration setup is three interfaces connected to three network segments. The ISP network segment is connected to the Ethernet0/0 interface and labelled outside with a security level of 0. The internal network has been connected to Ethernet0/1 and labelled as insid… - Topology
Here is a visual look at how this is cabled and configured:
Verify
- Verification procedures are included in Step 4 - Testing Configuration with the Packet Tracer Feature.
Conclusion
- The configuration of an ASA to do basic NAT is not that daunting of a task. The example in this document can be adapted to your specific scenario if you change the IP addresses and ports used in the example configurations. The final ASA configuration for this, when combined, looks similar to this for an ASA 5510: On an ASA 5505, for example, with the interfaces connected as shown p…
Introduction
Prerequisites
- Requirements
Cisco recommends that you have knowledge of ASA. - Components Used
The information in this document is based on an ASA running a software version 8.3 and later. The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your netwo…
Background Information
- ACLs are used by the ASA to determine if traffic is permitted or denied. By default, traffic that passes from a lower security level interface to a higher security level interface is denied whereas traffic from a higher security level interface to a lower security level interface is allowed. This behavior can also be overridden by configuring an ACL. In the presence of NAT rules, in earlier v…
Configure
- Scenario 1. Configure an Ace to Allow Access to a Web Server Located behind the DMZ
The client on the internet, located behind the outside interface wants to access a web server hosted behind the DMZ interface listening on TCP ports 80 and 443. - Scenario 2. Configure an Ace to Allow Access to a Web Server Using an FQDN
Client with IP address 10.10.10.2 located in the local area network (LAN) is allowed to access facebook.com.
Logging
- The log keyword sets logging options when an ACE matches a packet for network access (an ACL applied with the access-group command). If you enter the logkeyword without any arguments, you enable system log message 106100 at the default level (6) and for the default interval (300 seconds). If you do not enter the log keyword, then the default system log message 106023 is g…