How do I install the AnyConnect VPN client on a remote computer?
The AnyConnect client can be downloaded from the security appliance, or it can be installed manually on the remote PC by the system administrator. For more information on how to install the client manually, refer to the Cisco AnyConnect VPN Client Administrator Guide.
How do I enable WebVPN for remote access?
Enable WebVPN. Choose Configuration > Remote Access VPN > Network (Client) Access > SSL VPN Connection Profiles and under Access Interfaces, click the check boxes Allow Access and Enable DTLS for the outside interface.
Does asa2 Packet Tracer show Nat drop?
ASA1 has a noNAT rule(NAT exemption) ASA2 packet tracer shows ACL drop - this is were the NAT (10.10.10.0 to 192.168.0.0)rule is applied. 0 Helpful Reply Karsten Iwen VIP Mentor In response to buffkata
Is the AnyConnect VPN pool included on the split-tunnel ACL?
However the Anyconnect VPN Pool must be included on the Split-Tunnel ACL. This is a common scenario when Anyconnect Clients use phone services and should be able to call each other.
How do I enable NAT on ASA?
There are four steps involved in enabling static NAT:Create the network object and static NAT statement. ... Create a NAT statement identifying the outside interface. ... Build the Access-Control List. ... Apply the ACL to the outside interface using the Access-Group command: access-group OutsideToWebServer in interface outside.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
What is NAT exempt Cisco ASA?
NAT exemption allows you to exclude traffic from being translated with NAT. One scenario where you usually need this is when you have a site-to-site VPN tunnel.
How NAT works in ASA firewall?
Network Address Translation is used for the translation of private IP addresses into public IP addresses while accessing the internet. NAT generally operates on a router or firewall. In this type of NAT, multiple private IP addresses are mapped to a pool of public IP addresses.
Does Cisco ASA supports route based VPN?
Policy-Based IPSEC VPN This VPN category is supported on both Cisco ASA Firewalls and Cisco IOS Routers. With this VPN type the device encrypts and encapsulates a subset of traffic flowing through an interface according to a defined policy (using an Access Control List).
What are the four types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs....How Personal VPNs WorkInstall software from your VPN service provider onto your device. ... Connect to a server in your VPN provider's network.More items...•
What are different types of NAT in Asa?
Cisco ASA NAT – Contents:Static NAT.Static PAT.Dynamic PAT.Dynamic NAT.
What is identity NAT on ASA?
Identity NAT is a form of twice NAT, which allows us to specify both source and destination in our NAT statements. In the above configuration example, we define two network objects: inside-network and remote-network. We then configure an identity NAT statement that tells the ASA not to NAT the traffic.
How disable NAT in Cisco ASA?
Just remove all nat rules and the ASA won't do any translation. The option you are looking for is default in recent ASA releases. Now the ASA behaves more like a router when it comes to NAT: If you have a translation rule matching your traffic, the traffic will be translated.
What is difference between auto NAT and manual NAT in Asa?
An Auto-NAT rule only uses the source address and port when matching and translating. Manual NAT can match and translate source and destination addresses and ports. In both cases, the Translated Source may be the IP of the egress interface or an object. The PAT Pool option is available when using dynamic translations.
What is source NAT and destination NAT in Asa?
Destination NAT enables the translation of one destination address to another, a destination address and port to another destination address and port, or a group of destination addresses to another group of equal size. Source NAT is the translation of source IP addresses and TCP/UDP ports in the headers of IP flows.
How do I use NAT in firewall?
2:119:24NAT and Firewall Explained - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd the second part of this topic is firewalls a NAT. Device typically goes along with a firewallMoreAnd the second part of this topic is firewalls a NAT. Device typically goes along with a firewall function and it's usually employed. And in some kind of a routing device a routing device connects.
What is an ASA VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
What version of Cisco AnyConnect is compatible with Windows 10?
The minimum supported version is Windows 10 RS4 (1803).
Does Cisco AnyConnect support OpenVPN?
OpenVPN does not support some of the additional protocols that Pulse Secure and Cisco AnyConnect support.
Is Cisco AnyConnect VPN free?
Cisco AnyConnect is a free, easy to use, and worthwhile VPN client for Microsoft Windows computers. It's secure and doesn't require a lot of maintenance.
Is Cisco hosting the IT Blog Awards 2021?
The 2021 IT Blog Awards, hosted by Cisco, is now open for submissions. Submit your blog, vlog or podcast today. For more information, including category details, the process, past winners and FAQs, check out: https://www.cisco.com/c/en/us/t... view more
Does NAT have to be placed before the NAT-exemption?
Here you have to think about the order of the NAT processing. If you want to NAT a specific host through the VPN, this statement has to be placed before the NAT-exemption in section 1. The specific NAT to the internet has to be placed before the general PAT to your interface or PAT pool.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
How to enable SSL VPN on Cisco AnyConnect?
Choose Configuration > Remote Access VPN > Network (Client) Access > SSL VPN Connection Profiles and under Access Interfaces , click the check boxes Allow Access and Enable DTLS for the outside interface. Also, check the Enable Cisco AnyConnect VPN Client or legacy SSL VPN Client access on the interface selected in the table below check box in order to enable SSL VPN on the outside interface.
How to add NAT rule to Anyconnect?
Choose Configuration > Firewall > NAT Rules > Add NAT Rule Before "Network Object" NAT Rules so the traffic that comes from the outside network (Anyconect Pool) and it's destined to another Anyconnect Client from the same pool does not get translated with outside IP address 172.16.1.1.
What is Cisco AnyConnect VPN?
The Cisco AnyConnect VPN Client provides secure SSL connections to the security appliance for remote users. Without a previously installed client, remote users enter the IP address in their browser of an interface configured to accept SSL VPN connections. Unless the security appliance is configured to redirect http:// requests to https://, users must enter the URL in the form https://<address>.
What is hub and spoke VPN?
For example, if you have a hub-and-spoke VPN network where the security appliance is the hub and the remote VPN networks are spokes, in order for one spoke to communicate with another spoke traffic must go to the security appliance and then out again to the other spoke.
What does the security appliance do when a client is authenticated?
In the case of a previously installed client, when the user authenticates, the security appliance examines the revision of the client and upgrades the client as necessary.
How does a security appliance download client?
The security appliance downloads the client based on the group policy or username attributes of the user that establishes the connection. You can configure the security appliance to automatically download the client, or you can configure it to prompt the remote user about whether to download the client. In the latter case, if the user does not respond, you can configure the security appliance to either download the client after a timeout period or present the login page.
Why assign a completely different pool of IP addresses to the VPN Client?
Note: In order to avoid an overlap of IP addresses in the network , assign a completely different pool of IP addresses to the VPN Client (for example, 10.x.x.x , 172.16.x.x, and 192.168.x.x). This IP addressing scheme is helpful in order to troubleshoot your network.
Why is ASA allowed back through firewall?
The ASA is a stateful firewall, and return traffic from the web server is allowed back through the firewall because it matches a connection in the firewall connection table. Traffic that matches a connection that preexists is allowed through the firewall without being blocked by an interface ACL.
How to configure NAT rules?
Choose Configuration > Firewall > NAT Rules. Click Add and then choose Network Object in order to configure a dynamic NAT rule.
How to add NAT exempt rule?
Choose Configuration > Firewall > NAT Rules. Click Add in order to configure a NAT Exempt rule.
How to add automatic address translation rules?
Check the Add Automatic Address Translation Rules check box. In the Type drop-down list, choose Static. In the Translated Addr field, enter the IP address. Click Advanced in order to select the source and destination interfaces.
What level does ASA generate syslogs?
The syslogs range in verbosity based on the logging configuration. The output shows two syslogs that are seen at level six, or the 'informational' level.
How to add dynamic PAT in NAT?
Expand NAT. Check the Add Automatic Address Translation Rules check box. In the Type drop-down list, choose Dynamic PAT (Hide). In the Translated Addr field, choose the option to reflect the outside interface. Click Advanced.
What is Cisco CLI Analyzer?
The Cisco CLI Analyzer ( registered customers only) supports certain show commands. Use the Cisco CLI Analyzer in order to view an analysis of show command output.
Introduction
This document describes how to configure the Cisco 5500 Series Adaptive Security Appliance (ASA) to act as a remote VPN server using the Adaptive Security Device Manager (ASDM) or CLI and NAT the Inbound VPN Client traffic.
Prerequisites
This document assumes that the ASA is fully operational and configured to allow the Cisco ASDM or CLI to make configuration changes. The ASA is also assumed to be configured for Outbound NAT. Refer to Allow Inside Hosts Access to Outside Networks with the use of PAT for more information on how to configure Outbound NAT.
Background Information
Remote access configurations provide secure remote access for Cisco VPN clients, such as mobile users. A remote access VPN lets remote users securely access centralized network resources. The Cisco VPN Client complies with the IPSec protocol and is specifically designed to work with the security appliance.
Configurations
Complete these steps in order to configure the Cisco ASA as a remote VPN server with ASDM:
Verify
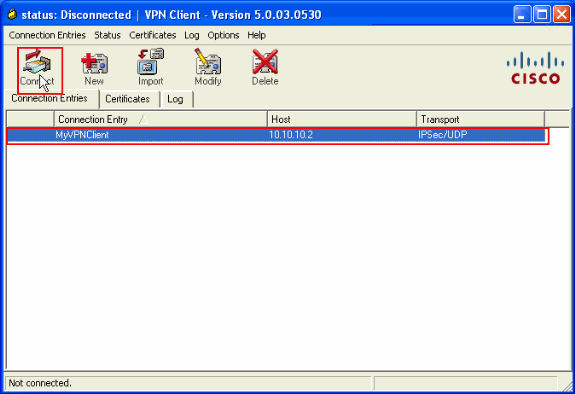
Attempt to connect to the Cisco ASA through the Cisco VPN Client in order to verify that the ASA is successfully configured.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.