
Cisco ASA – Enable Split Tunnel for Remote Clients
- Launch the ASDM > Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Select your policy.
- Edit > Select Advanced > Split Tunneling.
- Next to Policy > Untick “Inherit” > Change to “Tunnel Network List Below”.
- Next to “Network List” remove the tick from Inherit > Click Manage.
- Choose Configuration > VPN > General > Group Policy and select the Group Policy that you wish to enable local LAN access in. ...
- Go to the Client Configuration tab.
- Uncheck the Inherit box for Split Tunnel Policy and chose Tunnel Network List Below.
How to configure split tunneling for remote access VPN?
Complete these steps in order to configure your tunnel group to allow split tunneling for the users in the group. Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies, and choose the Group Policy in which you want to enable local LAN access. Then click Edit.
How do I enable split tunneling in a tunnel group?
Complete these steps in order to configure your tunnel group to allow split tunneling for the users in the group. Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies, and choose the Group Policy in which you want to enable local LAN access. Then click Edit. Click Split Tunneling.
How to configure WebVPN as tunneling protocol?
Under the General tab, select the SSL VPN Client check box in order to enable the WebVPN as tunneling protocol. In the Advanced > Split Tunneling tab, choose Tunnel All Networks from the Policy drop-down list of the Policy in order to make all the packets coming from the remote PC through a secure tunnel.
How do I set up a split tunneling ACL?
Click Split Tunneling. Uncheck the Inherit box for Split Tunnel Policy, and chose Tunnel Network List Below. Uncheck the Inherit box for Split Tunnel Network List, and then click Manage in order to launch the ACL Manager. Within the ACL Manager, choose Add > Add ACL... in order to create a new access list. Provide a name for the ACL, and click OK.
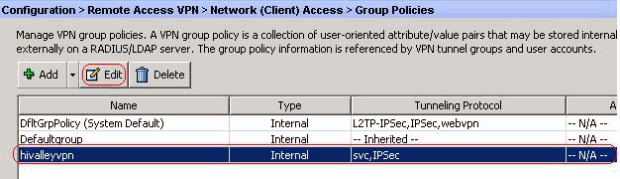
Where is split tunneling defined for remote access clients on an ASA?
1. Launch the ASDM > Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Select your policy. 2. Edit > Select Advanced > Split Tunneling. 3.
What is split tunneling in remote access VPN?
VPN Split Tunneling Definition Virtual private network (VPN) split tunneling lets you route some of your application or device traffic through an encrypted VPN, while other applications or devices have direct access to the internet.
How do I split tunnel VPN?
Get a VPN client with split tunneling Go to Settings > Network. Enable Split Tunnel and Allow LAN Traffic. Click Add Application and select a program. Select Bypass VPN if you want the program to stay connected to your home network.
Does Cisco AnyConnect allow split tunneling?
Dynamic Split Tunnel Include AnyConnect will send only the domains listed in the configuration over the secure vpn tunnel and all other traffic will be sent in the clear.
What is the difference between full tunnel and split tunnel?
VPN Connection Types Full tunnel is generally recommended because it is more secure. Split Tunnel - Routes and encrypts all OSU-bound requests over the VPN. Traffic destined to sites on the Internet (including Zoom, Canvas, Office 365, and Google) does not go through the VPN server in split tunnel mode.
Is VPN split tunneling safe?
Split tunneling introduces some security challenges. Any data that does not traverse a secure VPN is not protected by the corporate firewall, endpoint detection and response system, antimalware and other security mechanisms, so it may be accessible and/or intercepted by ISPs and malicious hackers.
Does OpenVPN support split tunneling?
How do I set it up in OpenVPN Access Server? In the Admin Web UI, you can start split tunneling with a simple click of a toggle button.
Does Cisco AnyConnect route all traffic?
With AnyConnect, the client passes traffic to all sites specified in the split tunneling policy you configured, and to all sites that fall within the same subnet as the IP address assigned by the ASA. For example, if the IP address assigned by the ASA is 10.1.
What is split exclude tunneling?
A split tunnel configured to only tunnel traffic destined to a specific set of destinations is called a split-include tunnel. When configured to accept all traffic except traffic destined to a specific set of destinations, it is called a split-exclude tunnel.
How does a split tunnel work?
Split tunneling is a VPN feature that divides your internet traffic and sends some of it through an encrypted virtual private network (VPN) tunnel, but routes the rest through a separate tunnel on the open network. Typically, split tunneling will let you choose which apps to secure and which can connect normally.
What is split tunnel in Palo Alto?
Split Tunneling is a computer networking concept that allows users to access different security domains at the same time.
How do I know if my split tunnel is enabled?
You can check that split tunneling is enabled by entering the Get-VPNConnection command again. The split tunneling field should now be set to True.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is split tunneling?
This is the process of letting a remote VPN user browse the web, and access local resources etc, from their location whilst connected to your VPN in this case via SSLVPN, but also from WebVPN or IPSEC VPN.
How to create an ACL for ASA?
1. Connect to the ASA > Go to enable mode > Then to global configuration mode > Create an ACL that permits traffic from the network behind the ASA to any. ( Note: Add additional ACL’s for additional internal networks).
How does VPN work with ASA?
In a basic VPN Client to ASA scenario, all traffic from the VPN Client is encrypted and sent to theASA no matter what its destination is. Based on your configuration and the number of userssupported, such a set up can become bandwidth intensive. Split tunneling can work to alleviatethis problem since it allows users to send only that traffic which is destined for the corporatenetwork across the tunnel. All other traffic such as instant messaging, email, or casual browsing issent out to the Internet via the local LAN of the VPN Client.
How many ACE entries are needed for split tunnel?
There is a restriction with the number of entries in an ACL used for split tunnel. It is recommendednot to use more than 50-60 ACE entries for satisfactory functionality. You are advised toimplement the subnetting feature to cover a range of IP addresses.
How to enable SSL VPN on Cisco AnyConnect?
Choose Configuration > Remote Access VPN > Network (Client) Access > SSL VPN Connection Profiles and under Access Interfaces , click the check boxes Allow Access and Enable DTLS for the outside interface. Also, check the Enable Cisco AnyConnect VPN Client or legacy SSL VPN Client access on the interface selected in the table below check box in order to enable SSL VPN on the outside interface.
What is Cisco AnyConnect VPN?
The Cisco AnyConnect VPN Client provides secure SSL connections to the security appliance for remote users. Without a previously installed client, remote users enter the IP address in their browser of an interface configured to accept SSL VPN connections. Unless the security appliance is configured to redirect http:// requests to https://, users must enter the URL in the form https://<address>.
How to add NAT rule to Anyconnect?
Choose Configuration > Firewall > NAT Rules > Add NAT Rule Before "Network Object" NAT Rules so the traffic that comes from the outside network (Anyconect Pool) and it's destined to another Anyconnect Client from the same pool does not get translated with outside IP address 172.16.1.1.
What is hub and spoke VPN?
For example, if you have a hub-and-spoke VPN network where the security appliance is the hub and the remote VPN networks are spokes, in order for one spoke to communicate with another spoke traffic must go to the security appliance and then out again to the other spoke.
What does the security appliance do when a client is authenticated?
In the case of a previously installed client, when the user authenticates, the security appliance examines the revision of the client and upgrades the client as necessary.
How does a security appliance download client?
The security appliance downloads the client based on the group policy or username attributes of the user that establishes the connection. You can configure the security appliance to automatically download the client, or you can configure it to prompt the remote user about whether to download the client. In the latter case, if the user does not respond, you can configure the security appliance to either download the client after a timeout period or present the login page.
Why assign a completely different pool of IP addresses to the VPN Client?
Note: In order to avoid an overlap of IP addresses in the network , assign a completely different pool of IP addresses to the VPN Client (for example, 10.x.x.x , 172.16.x.x, and 192.168.x.x). This IP addressing scheme is helpful in order to troubleshoot your network.
Introduction
Prerequisites
- Requirements
This document assumes that a working remote access VPN configuration already exists on the ASA. Refer to PIX/ASA 7.x as a Remote VPN Server using ASDM Configuration Exampleif one is not already configured. - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco ASA 5500 Series Security Appliance Software version 7.x and later 2. Cisco Systems VPN Client version 4.0.5 Note: This document also contains the PIX 6.x CLI configuration that is compatibl…
Background Information
- In a basic VPN Client to ASA scenario, all traffic from the VPN Client is encrypted and sent to the ASA no matter what its destination is. Based on your configuration and the number of users supported, such a set up can become bandwidth intensive. Split tunneling can work to alleviate this problem since it allows users to send only that traffic which is destined for the corporate ne…
Verify
- Follow the steps in these sections in order to verify your configuration. 1. Connect with the VPN Client 2. View the VPN Client Log 3. Test Local LAN Access with Ping
Troubleshoot
- Limitation with Number of Entries in a Split Tunnel ACL
There is a restriction with the number of entries in an ACL used for split tunnel. It is recommended not to use more than 50-60 ACE entries for satisfactory functionality. You are advised to implement the subnetting feature to cover a range of IP addresses.
Related Information