Full Answer
What are the contents of the default remote-access tunnel group?
The contents of the default remote-access tunnel group are as follows: The general attributes are common across more than one tunnel-group type. IPSec remote access and WebVPN tunnels share most of the same general attributes. IPSec LAN-to-LAN tunnels use a subset.
How do I configure tunnel-group general-attributes?
Step 1 Enter tunnel-group general-attributes mode by specifying the general-attributes keyword: The prompt changes to indicate that you are now in config-general mode, in which you configure the tunnel-group general attributes. For example, for the tunnel group named docs, enter the following command:
What is a AAA Tunnel Group?
A tunnel group is a collection of tunnel connection policies. You configure a tunnel group to identify AAA servers, specify connection parameters, and define a default group policy. The ASA stores tunnel groups internally.
How do I restrict remote users to a specific tunnel group?
Configure the group-lock attribute with the value keyword to restrict remote users to access only through the specified, preexisting tunnel group. Group-lock restricts users by checking whether the group configured in the VPN client is the same as the tunnel group to which the user is assigned.

What is tunnel group in ASA?
Tunnel groups are the part of EzVPN technology. When you configure your VPN this way you are allways providing group-name/password or certificate with mapping data to group. At the site to site (or lan to lan) VPN usually uses a crypto maps with IPSec profiles without tunnel groups.
How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
What is tunnel Group in IPSec?
Tunnel Groups have two main elements which are Attributes and Types. It helps to visualize these in a hierarchy. Types. ipsec-l2l – L2L Configurations. ipsec-ra – The old IPSec Client VPN type (Deprecated)
Where is split tunneling defined for remote access clients on an ASA?
1. Launch the ASDM > Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Select your policy. 2. Edit > Select Advanced > Split Tunneling. 3.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
What is group policy in Cisco ASA?
Summary. The Cisco ASA firewall includes the ability to assign a user to a group policy based on their OU group. This is achieved via the use of the IETF RADIUS Attribute 25. This attribute contains the users OU and is sent by the Radius server (to the ASA) during the RADIUS Authentication and Authorization process.
How do I enable IKEv1 on Cisco ASA?
Enable IKEv1 on the the interfaceIntroduction.Define the Encryption Domain.Specify the Phase 1 Policy.Specify the Phase 2 Proposal.Define the connection profile.Configure the Crypto Map.Bind the Crypto Map to the interface.Enable IKEv1 on the the interface.
What is crypto map in Asa?
Crypto maps pull together the various parts configured for IPsec, including: ■ Which traffic should be protected by IPsec. ■ Where IPsec-protected traffic should be sent. ■ The local address to be used for the IPsec traffic. ■ Which IPsec type should be applied to this traffic.
What is split tunnel ACL?
The split tunneling feature allows you to optimize traffic flow by directing only corporate traffic back to the controller, while local application traffic remains local.
What is split tunneling AnyConnect?
What is Split Tunneling? VPN split tunneling lets you send some of your application or device traffic through an encrypted VPN, while other applications or devices have direct access to the internet.
What is tunnel mode split exclude?
A split tunnel configured to only tunnel traffic destined to a specific set of destinations is called a split-include tunnel. When configured to accept all traffic except traffic destined to a specific set of destinations, it is called a split-exclude tunnel.
How do I connect to Cisco ASA?
Complete the below steps.Configure the management interface. conf t. int e 0/2. ip address 192.168.100.2 255.255.255.0. nameif manage. security-level 80. exit. exit.Configure the username and privilege. username Test password Test@Cisco privilege 15.Configure the Cisco ASA to allow http connections.
How do I enable Cisco AnyConnect VPN through Remote Desktop?
The steps would be:Log into the ASDM.Go to Configuration, Remote Access VPN, Anyconnect Client Profile.Click Add and create a new profile and choose the Group Policy it should apply to.Click OK, and then at the Profile screen click "Apply" at the bottom (important)More items...•
How do I download AnyConnect from Asa?
Just load a new image to the ASA (under Configuration -> Remote-Access VPN -> Network (Client) Access -> AnyConnect Client Software) and the client will load the new software the next time when the client connects. Of course the client shouldn't have a setting applied to not download new software.
How do I enable telnet on ASDM?
Allow Telnet – Via ASDM (version shown 6.4(7)) Connect via ASDM > Navigate to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH > Add > Select Telnet > Supply the IP and subnet > OK.
What is split tunneling?
Split tunneling lets a remote-access IPSec client conditionally direct packets over an IPSec tunnel in encrypted form or to a network interface in clear text form. With split tunnel ing enabled, packets not bound for destinations on the other side of the IPSec tunnel do not have to be encrypted, sent across the tunnel, decrypted, and then routed to a final destination. This command applies this split tunneling policy to a specific network.
How to set an idle timeout for individual users behind hardware clients?
Set an idle timeout for individual users behind hardware clients by entering the user-authentication-idle-timeout command in group-policy configuration mode. If there is no communication activity by a user behind a hardware client in the idle timeout period, the security appliance terminates the client's access:
What is IPSec over UDP?
IPSec over UDP, sometimes called IPSec through NAT, lets a Cisco VPN client or hardware client connect via UDP to a security appliance that is running NAT. It is disabled by default. IPSec over UDP is proprietary; it applies only to remote-access connections, and it requires mode configuration. The security appliance exchanges configuration parameters with the client while negotiating SAs. Using IPSec over UDP may slightly degrade system performance.
How does a firewall protect a computer?
A firewall isolates and protects a computer from the Internet by inspecting each inbound and outbound individual packet of data to determine whether to allow or drop it. Firewalls provide extra security if remote users in a group have split tunneling configured. In this case, the firewall protects the user's PC, and thereby the corporate network, from intrusions by way of the Internet or the user's local LAN. Remote users connecting to the security appliance with the VPN client can choose the appropriate firewall option.
What is a VPN group?
Groups and users are core concepts in managing the security of virtual private networks (VPNs) and in configuring the security appliance. They specify attributes that determine user access to and use of the VPN. A group is a collection of users treated as a single entity. Users get their attributes from group policies. Tunnel groups identify the group policy for a specific connection. If you do not assign a particular group policy to a user, the default group policy for the connection applies.
What command enforces complex passwords?
To enforce complex passwords—for example, to require that a password contain upper- and lowercase letters, numbers, and special characters—specify the password-management command in tunnel-group general-attributes configuration mode on the security appliance and do the following steps under Active Directory:
How do external group policies work?
External group policies take their attribute values from the external server that you specify. For an external group policy, you must identify the AAA server group that the security appliance can query for attributes and specify the password to use when retrieving attributes from the external AAA server group. If you are using an external authentication server, and if your external group-policy attributes exist in the same RADIUS server as the users that you plan to authenticate, you have to make sure that there is no name duplication between them.
What is Cisco Secure Endpoint?
Cisco Secure Endpoint New packages fit for every organization Every Cisco Secure Endpoint (formerly AMP for Endpoints) package comes with Cisco SecureX built-in. It’s our cloud-native platform that integrates all your security solutions into one view wit... view more
Can you have group alias and group URL?
You can have group-alias and group-url simultaneously in the configuration so that phones can connnect with group-url and users can click on drop down menu to select the right connection profile. tunnel-group <tunnel-group-name> webvpn-attributes. group-alias <tunnel-group-alias> enable. group-url <url> enable.
What is the IP address of AnyConnect?
You can see that we received IP address 192.168.10.100 (the first IP address from the VPN pool). Anyconnect creates an additional interface, just like the legacy Cisco VPN client does.
When remote users connect to our WebVPN, do they have to use HTTPS?
The following option is not required but useful, whenever someone accesses the ASA through HTTP then they will be redirected to HTTPS:
What happens when a VPN user terminates a session?
Normally when the remote VPN user terminates the session, the anyconnect installer will be uninstalled. The anyconnect keep-installer installed command leaves it installed on the user’s computer.
What happens when you have an inbound access list?
When you have an inbound access-list on the outside interface then all your decrypted traffic from the SSL WebVPN has to match the inbound access-list. You can either create some permit statements for the decrypted traffic or you can just tell the ASA to let this traffic bypass the access-list:
What is AnyConnect VPN?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. AnyConnect VPN. The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, ...
Why does my client tries to download AnyConnect?
The client tries to download the Anyconnect automatically, this is because of the anyconnect ask none default anyconnect command that we used. Since we are using a self-signed certificate you will get the following error message:
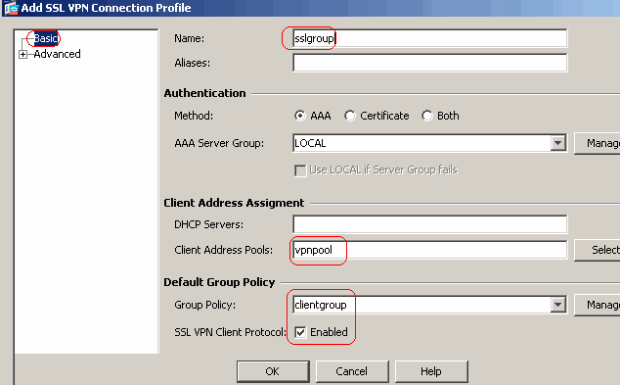
What happens after group policy configuration?
After the group policy configuration we have to create a tunnel group which binds the group policy and VPN pool together:
What is a tunnel group?
Summary – Tunnel groups are what I consider the base of VPN configuration. They are very easy to configure in the CLI. You simply define a tunnel group by giving it a name and a type and then you add attributes to it based on what sort of VPN you are configuring (L2L or remote-access).
Do you need to define authentication in a tunnel group?
Since we didn’t specify a different authentication group in our WebVPN setup, it defaults to Local authentication. There isn’t any need to define authentication in the tunnel group unless you are configuring Radius or some other type of user authentication.
Can group policies be configured?
Summary – There are a lot of features that can be configured in group policies. I’m not even go to try to get into them during this post. My objective here was to give you a brief description of group policies and tunnel groups. Hopefully now you have a better understanding of how they interact with each other and as a whole are part of the Anyconnect and WebVPN solutions. In the next post we are actually going to talk about portal customizations and how they relate to group policies and tunnel groups.
