Launch ASDM and log into the ASA you wish to create VPN access to. Click on Wizards, VPN Wizard and select the type of VPN you will like to create Click on the VPN Type if it is not available as part of the menu options
How do I configure a VPN policy in ASDM?
Step 1 Start ASDM and choose Configuration > Remote Access VPN > AAA/Local Users > Local Users . Step 2 Select the user you want to configure and click Edit . The Edit User Account dialog box appears. Step 3 In the left-hand pane, click VPN Policy .
How do I change the DNS setting on the ASDM?
Note This setting overrides the DNS setting configured on the ASDM in the Configuration > Remote Access VPN > DNS window. Step 1 Select Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit > Servers .
How do I configure identity Nat with ASDM?
Each Identity NAT configuration requires one NAT rule. Step 1 Log into the ASDM and select Configuration > Firewall > NAT Rules. Step 2 Create a NAT rule so that the hosts in the Engineering VPN address pool can reach the hosts in the Sales VPN address pool.
How to enable AnyConnect protocols on remote access VPN?
Go to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles , Access Interfaces section. In the Interface table, in the row for the interface you are configuring for AnyConnect connections, check the protocols you want to enable on the interface.
How configure Cisco AnyConnect ASDM?
Setup AnyConnect From ASDM (Local Authentication) Launch the ASDM > Wizards > VPN Wizards > AnyConnect VPN Wizard > Next. Give the AnyConnect profile a name i.e PF-ANYCONNECT, (I capitalise any config that I enter, so it stands out when I'm looking at the firewall configuration). > Next > Untick IPSec > Next.
How do I connect to Cisco ASA VPN?
Eight easy steps to Cisco ASA remote access setupConfigure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.Configure User Accounts.
How do I access Cisco firewall through ASDM?
Complete the below steps.Configure the management interface. conf t. int e 0/2. ip address 192.168.100.2 255.255.255.0. nameif manage. security-level 80. exit. exit.Configure the username and privilege. username Test password Test@Cisco privilege 15.Configure the Cisco ASA to allow http connections.
What is the default IP address of ASDM?
The HTTP server is enabled for ASDM and is accessible to users on the 192.168. 1.0 network. command, then the IP address and mask are 192.168. 1.1 and 255.255.
How is Cisco VPN configured?
5 Steps to Configure Cisco AnyConnect VPNConfigure AAA authentication. The first thing to configure is AAA authentication. ... Define VPN protocols. When users connect their VPN, they'll need an IP address for the VPN session. ... Configure tunnel groups. ... Set group policies. ... Apply the configuration. ... Authenticating logic flow.
How do I setup a Cisco VPN?
ConnectOpen the Cisco AnyConnect app.Select the connection you added, then turn on or enable the VPN.Select a Group drop-down and choose the VPN option that best suits your needs.Enter your Andrew userID and password.Tap Connect.
How configure Cisco ASA 5505 firewall with ASDM?
0:417:27ASDM installation on Cisco ASA 5505 Firewall - YouTubeYouTubeStart of suggested clipEnd of suggested clipThe device so we first want to go into privilege mode from previous mode we'll go into global configMoreThe device so we first want to go into privilege mode from previous mode we'll go into global config mode.
How do I enable ASDM on ASA firewall?
Open the shortcut and fill in the IP address (192.168. 1.1), leave the username blank and put in the password firewall. The ASDM will then connect to the ASA and load the java interface. You can now configure the ASA as per your requirements.
How do I access ASA firewall through browser?
ASDM Web Access Guide:On the PC connected to the ASA, launch a web browser. (Verify that Java and JavaScript are enabled in your web browser)In the Address field, enter the following (default) URL: https://192.168.1.1/admin.Run Startup Wizard.
How do I assign an IP address to a firewall in ASA?
Set a Static IP for your Cisco ASA5505 FirewallOpen the ASDM and log into your device.Under Configuration, Interfaces, select the Outside interface and hit Edit.In the 'IP Address' box, click the radio for 'Use Static IP'Select an IP address, and use '255.255. ... Hit ok, then apply.More items...•
How configure Cisco ASA management IP?
In order to enable the Management 1/1 interface to act as a normal Firewall interface, use the following configuration:ASA(config)# interface Management 1/1. ASA(config-if)# no management-only.! Enable local authentication for SSH access: ... !
What is ASDM Cisco?
Cisco's Adaptive Security Device Manager (ASDM) is the GUI tool used to manage the Cisco ASA security appliances.
How do I find the IP address of my Cisco VPN?
Open the Cisco AnyConnect Client from the dock. Click on the Statistics button in the lower left corner of the window. The IP Address is in the line that reads “Client Address (IPv4).”
How does Cisco AnyConnect VPN client work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
How do I download AnyConnect from Asa?
Just load a new image to the ASA (under Configuration -> Remote-Access VPN -> Network (Client) Access -> AnyConnect Client Software) and the client will load the new software the next time when the client connects. Of course the client shouldn't have a setting applied to not download new software.
What is Cisco VPN AnyConnect?
The Cisco AnyConnect Secure Mobility Client is a web-based VPN client that does not require user configuration. VPN, also called IP tunneling, is a secure method of accessing USC computing resources.
What is VPN setup?
General VPN Setup. A virtual private network is a network of virtual circuits that carry private traffic over a public network such as the Internet. VPNs can connect two or more LANS, or remote users to a LAN. VPNs provide privacy and security by requiring all users to authenticate and by encrypting all data traffic.
What is Cisco AnyConnect VPN?
The Cisco AnyConnect VPN client provides secure SSL or IPsec (IKEv2) connections to the ASA for remote users. The client gives remote users the benefits of a VPN client without the need for network administrators to install and configure clients on remote computers.
What is VPN group policy?
A VPN group policy is a collection of user-oriented attribute/value pairs stored either internally on the device or externally on a RADIUS or LDAP server. Configuring the VPN group policy lets users inherit attributes that you have not configured at the individual group or username level.
What is an advanced endpoint assessment?
Advanced Endpoint Assessment includes all of the Endpoint Assessment features and lets you configure an attempt to update noncompliant computers to meet version requirements. You can use ASDM to activate a key to support Advanced Endpoint Assessment after acquiring it from Cisco, as follows:
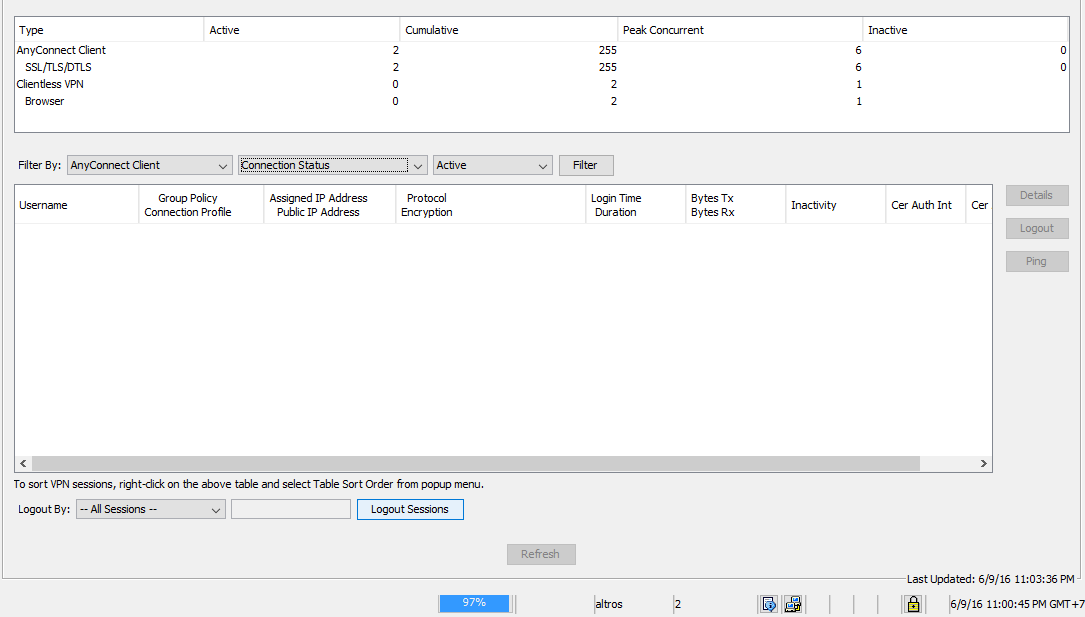
How many client access rules can you see in a table?
The Client Access Rules table on this dialog box lets you view up to 25 client access rules. If you uncheck the Inherit check box, the Add, Edit, and Delete buttons become active and the following column headings appear in the table:
How to configure customization for a group policy?
To configure customization for a group policy, select a preconfigured portal customization object, or accept the customization provided in the default group policy. You can also configure a URL to display
Does Cisco IronPort support AnyConnect?
Note This feature requires a release of the Cisco IronPort Web Security appliance that provides AnyConnect Secure Mobility licensing support for the Cisco AnyConnect secure mobility client. It also requires an AnyConnect release that supports the AnyConnect Secure Mobility feature.
What is SAML 2.0?
SAML 2.0-based service provider IdP is supported in a private network. When the SAML IdP is deployed in the private cloud, ASA and other SAML-enabled services are in peer positions, and all in the private network. With the ASA as a gateway between the user and services, authentication on IdP is handled with a restricted anonymous webvpn session, and all traffic between IdP and the user is translated. When the user logs in, the ASA modifies the session with the corresponding attributes and stores the IdP sessions. Then you can use service provider on the private network without entering credentials again.
Does ASA support SAML 2.0?
The ASA supports SAML 2.0 so that Clientless VPN end users will be able to input their credentials only one time when they switch between Clientless VPN and other SAAS applications outside of the private network.
Configure an IP Address Assignment Policy
The ASA can use one or more of the following methods for assigning IP addresses to remote access clients. If you configure more than one address assignment method, the ASA searches each of the options until it finds an IP address. By default, all methods are enabled.
Configure Local IP Address Pools
To configure IPv4 or IPv6 address pools for VPN remote access tunnels, open ASDM and choose Configuration > Remote Access VPN > Network (Client) Access > Address Management > Address Pools > Add/Edit IP Pool.
Configure DHCP Addressing
To use DHCP to assign addresses for VPN clients, you must first configure a DHCP server and the range of IP addresses that the DHCP server can use. Then you define the DHCP server on a connection profile basis. Optionally, you can also define a DHCP network scope in the group policy associated with a connection profile or username.
Assign IP Addresses to Local Users
Local user accounts can be configured to use a group policy, and some AnyConnect attributes can also be configured. These user accounts provide fallback if the other sources of IP address fail, so administrators will still have access.
How to do DNS lookup for clientless VPN?
For example, go to Configuration > Device Management > DNS > DNS Client, then in the DNS Lookup table, click the DNS Enabled cell in the inside interface row and select True.
What is clientless VPN?
Clientless SSL VPN includes an Application Profile Customization Framework (APCF) option that lets the ASA handle non-standard applications and Web resources so they display correctly over a Clientless S SL VPN connection. An APCF profile contains a script that specifies when (pre, post), where (header, body, request, response), and what (data) to transform for a particular application. The script is in XML and uses sed (stream editor) syntax to transform strings/text.
How to find APCF file?
Select Flash file to locate an APCF file stored on the ASA flash memory. Then click Upload to get an APCF file from a local computer to the ASA flash file system, or Browse to upload choose an APCF file that is already in flash memory. Select URL to retrieve the APCF file from an HTTP, HTTPS, FTP, or TFTP server.
Where to store APCF?
You can store APCF profiles on the ASA flash memory or on an HTTP, HTTPS, FTP, or TFTP server. Use this pane to add, edit, and delete APCF packages, and to put them in priority order.
Why is cache important in VPN?
The use of the cache reduces traffic , with the result that many applications run more efficiently.
1. Check Cisco firewall ASA version
Make sure you have ASA 8.2.2 and up. You cannot connect your Windows clients if you have ASA 8.2.1 because of the Cisco software bug.
2. Start Cisco firewall IPsec VPN Wizard
Login to your Cisco firewall ASA5500 ASDM and go to Wizard > IPsec VPN Wizard ... and follow up the screens.
3. Add Transform Set
Go to Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPSec > Crypto Maps. Edit the IPSec rules and add "TRANS_ESP_3DES_SHA" and click "Ok" button.
