From ASDM: Choose Configuration > Remote Access VPN > AAA/Local Users > Local Users. Select the user you want to configure and click Edit.
How do I enable remote users to access the AnyConnect portal?
You can enable the ASA to prompt remote users to download the AnyConnect client or go to a Clientless SSL VPN portal page. See Internal Group Policy, AnyConnect Login Settings . To configure single sign-on servers and Auto sign-on servers, see Internal Group Policy, Clientless SSL VPN Access Portal .
How do I enable Dead Peer Detection on AnyConnect VPN?
Go to Configuration > Remote Access VPN > Network (Client) Access > Group Policies, Add or Edit the desired group policy, then open the Advanced > AnyConnect Client > Dead Peer Detection pane.
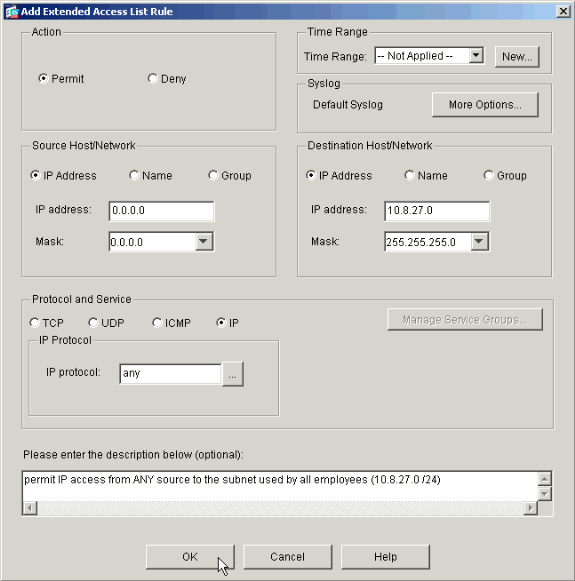
How do I manage ACLs and Aces in remote access VPN?
To configure filters and rules, choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit > General > More Options > Filter. Click Manage to display the ACL Manager pane, on which you can add, edit, and delete ACLs and ACEs.
How do I set basic attributes for an AnyConnect VPN connection?
To set the basic attributes for an AnyConnect VPN connection, choose Add or Edit in the AnyConnect Connection Profiles section. The Add (or Edit) AnyConnect Connection Profile > Basic dialog box opens. Name—For Add, specify the name of the connection profile you are adding. For Edit, this field is not editable.

What is DPD in ASA?
Dead Peer Detection (DPD) ensures that the ASA (gateway) or the client can quickly detect a condition where the peer is not responding, and the connection has failed. To enable dead peer detection (DPD) and set the frequency with which either the AnyConnect client or the ASA gateway performs DPD, do the following:
How long do you have to notify ASDM before password expiration?
The range is 1 through 180 days.
What are portal attributes?
The Portal attributes determine what appears on the portal page for members of this group policy establishing Clientless SSL VPN connections. In this pane, you can enable Bookmark lists and URL Entry, file server access, Port Forwarding and Smart Tunnels, ActiveX Relay, and HTTP settings.
What is ACL AnyConnect_Client_Local_Print?
The ACL AnyConnect_Client_Local_Print is provided with ASDM to make it easy to configure the client firewall. When you choose that ACL for Public Network Rule in the Client Firewall pane of a group policy, that list contains the following ACEs:
What version of ASA is AnyConnect?
The ASA supports the AnyConnect client firewall feature with ASA version 8.3 (1) or later, and ASDM version 6.3 (1) or later. This section describes how to configure the client firewall to allow access to local printers, and how to configure the client profile to use the firewall when the VPN connection fails.
What is dynamic split tunneling?
With dynamic split tunneling, you can dynamically provision split exclude tunneling after tunnel establishment based on the host DNS domain name. Dynamic split tunneling is configured by creating a custom attribute and adding it to a group policy.
How to enable end users to print to their local printer?
To enable end users to print to their local printer, create a standard ACL in the group policy. The ASA sends that ACL to the VPN client, and the VPN client modify the client’s firewall configuration.
Configure an IP Address Assignment Policy
The ASA can use one or more of the following methods for assigning IP addresses to remote access clients. If you configure more than one address assignment method, the ASA searches each of the options until it finds an IP address. By default, all methods are enabled.
Configure Local IP Address Pools
To configure IPv4 or IPv6 address pools for VPN remote access tunnels, open ASDM and choose Configuration > Remote Access VPN > Network (Client) Access > Address Management > Address Pools > Add/Edit IP Pool.
Configure DHCP Addressing
To use DHCP to assign addresses for VPN clients, you must first configure a DHCP server and the range of IP addresses that the DHCP server can use. Then you define the DHCP server on a connection profile basis. Optionally, you can also define a DHCP network scope in the group policy associated with a connection profile or username.
Assign IP Addresses to Local Users
Local user accounts can be configured to use a group policy, and some AnyConnect attributes can also be configured. These user accounts provide fallback if the other sources of IP address fail, so administrators will still have access.
What is SAML 2.0?
SAML 2.0-based service provider IdP is supported in a private network. When the SAML IdP is deployed in the private cloud, ASA and other SAML-enabled services are in peer positions, and all in the private network. With the ASA as a gateway between the user and services, authentication on IdP is handled with a restricted anonymous webvpn session, and all traffic between IdP and the user is translated. When the user logs in, the ASA modifies the session with the corresponding attributes and stores the IdP sessions. Then you can use service provider on the private network without entering credentials again.
Does ASA support SAML 2.0?
The ASA supports SAML 2.0 so that Clientless VPN end users will be able to input their credentials only one time when they switch between Clientless VPN and other SAAS applications outside of the private network.
Can SAML 2.0 be used with AAA?
This SAML SSO SP feature is a mutual exclusion authentication method. It cannot be used with AAA and certificate together.
Does AnyConnect use IPv6?
For example, while AnyConnect might prefer an IPv4 connection over an IPv6 connection, the embedded browser might prefer IPv6, or vice versa.
Chapter: Clientless SSL VPN Remote Users
This chapter summarizes configuration requirements and tasks for the user remote system. It also helps users get started with Clientless SSL VPN. It includes the following sections:
Usernames and Passwords
Depending on your network, during a remote session users may have to log on to any or all of the following: the computer itself, an Internet service provider, Clientless SSL VPN, mail or file servers, or corporate applications.
Communicate Security Tips
Always log out from a Clientless SSL VPN session, click the logout icon on the Clientless SSL VPN toolbar or close the browser.
Configure Remote Systems to Use Clientless SSL VPN Features
The following table includes the tasks involved in setting up remote systems to use Clientless SSL VPN, requirements/prerequisites for the task and recommended usage:
Capture Clientless SSL VPN Data
The CLI capture command lets you log information about websites that do not display correctly over a Clientless SSL VPN connection. This data can help your Cisco customer support engineer troubleshoot problems. The following sections describe how to use the capture command: