By properly auditing remote access to the third parties on your network. The best way to do this is to enlist the help of a vendor management solution that can automatically track each vendor user’s activity with videos and logs of files transferred, commands entered, and services accessed. Verify vendor access levels on your network
Full Answer
How do I view audit data in the remote control?
In the User Name list of the Remote Control - All computers remote controlled by a specific user, specify the user that you want to report audit information for, and then click View Report. When you have finished viewing the data in the report, close the report window.
Why audit remote vendor access?
Proper auditing of remote vendor access achieves three vital goals: 1 An ongoing audit ensures accountability and compliance. 2 An audit trail and access notifications can set off alarms when unusual activity occurs. 3 Granular audit records provide forensic details in the event of a breach or mistake to help track down the root cause... More ...
How to audit remote access to third parties on your network?
By properly auditing remote access to the third parties on your network. The best way to do this is to enlist the help of a vendor management solution that can automatically track each vendor user’s activity with videos and logs of files transferred, commands entered, and services accessed. There is an old saying: “Trust, but verify.”
What is remote access monitoring and accounting?
Use Remote Access Monitoring and Accounting. Remote Access monitoring reports remote user activity and status for DirectAccess and VPN connections. It tracks the number and duration of client connections (among other statistics), and monitors the operations status of the server.
How to mitigate remote vendor access?
What is audit trail?
What is vendor privileged access?
What is a security audit platform?
What are the features of a secure audit?
Why use outside vendors?
Why is it important to implement internal audits?
See more
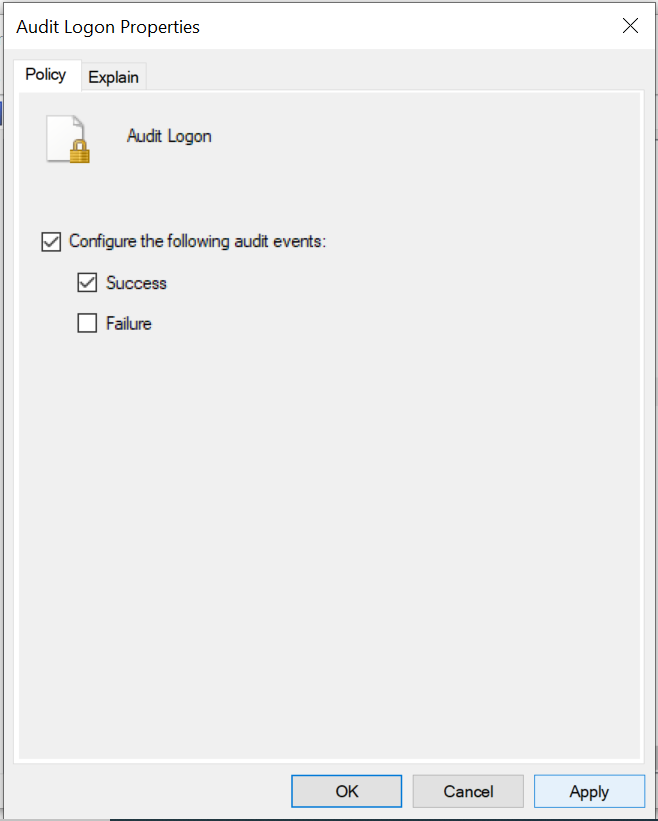
How do I audit Remote Desktop Connection?
Navigate to Computer Configuration -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> Audit Policies -> Logon Logoff access. Under Audit Policy, select 'Audit Logon' and turn auditing on for success.
What is a remote access audit?
Remote Desktop Audit is designed for monitoring the activity of users who access your servers via remote desktop. All information about remote desktop sessions across your servers will be collected in one place, thereby allowing for in-depth data analysis and providing valuable new insights.
How do I monitor remote access sessions?
To monitor remote client activity and statusIn Server Manager, click Tools, and then click Remote Access Management.Click REPORTING to navigate to Remote Access Reporting in the Remote Access Management Console.More items...•
How do you audit access control?
Identity and Access Management Audit ChecklistCreate a Security Policy. ... Develop Formal Procedures. ... User Review. ... Assign Appropriate User Privileges. ... Segregation of Duties. ... Manage Generic User Accounts. ... Disable Unnecessary User Accounts. ... Maintain Clear Documentation.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What is a best practice for compliance in the remote access domain?
Instead, a best practice is to adopt the principle of least privilege, which means that access for all users should be blocked by default and enabled only for the specific accounts that require it. This will require more configuration, but it is well worth the added security benefits.
Is there a log file for RDP connections?
Outgoing RDP Connection Logs in Windows You can also view outgoing RDP connection logs on the client side. They are available in the following event log: Application and Services Logs -> Microsoft -> Windows -> TerminalServices-ClientActiveXCore -> Microsoft-Windows-TerminalServices-RDPClient -> Operational.
How do I find Remote Desktop Connection history?
To view remote desktop history for individual computers, follow the steps given below:Click the Tools tab.In the Windows Tools section, click Remote Control.Click. against the name of a computer to view its remote-control history.
Can Remote Desktop be monitored?
A: YES, your employer can and has the right to monitor your Citrix, Terminal, and Remote Desktop sessions.
How do you audit user access to the network and data on the network?
How to perform a network auditRecord the details of the audit.Document all procedures and processes associated with the audit.Review the procedure management system.Assess the training logs and operations.Confirm the security patches for network software are up-to-date.More items...•
What is IAM audit?
Auditing Identity and Access Management, 2nd Edition. Executive Summary. Identity and access management (IAM) covers the policies, processes, and tools for ensuring users have appropriate access to information technology (IT) resources.
How do I monitor privileged accounts?
4 Steps to Monitor and Audit Privileged Users of Data StoresAccess for the privileged user. A privileged user is someone who has access to critical systems and data. ... Identify and manage privileged access. ... Monitor privileged user usage. ... Analyze Behavior. ... Provide Reports. ... The Imperva Solution.
What are the security requirements for remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is remote access control?
Remote access control refers to the ability to monitor and control access to a computer or network (such as a home computer or office network computer) anywhere and anytime. Employees can leverage this ability to work remotely away from the office while retaining access to a distant computer or network.
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
Which is more secure to use when connecting to a device virtually?
VPNs allow employees working remotely to connect to a corporate network by routing their activity through a secure server. VPN systems encrypt data transmitted over the network, so that data is unusable to an attacker eavesdropping on the connection.
Remote Auditing Best Practices & Checklist for Regulatory Compliance
The coronavirus (COVID-19) pandemic has prompted worldwide travel restrictions and remote work policies, disrupting routine in-person auditing and official inspection activities throughout the regulated life science industry.. In March of 2020, The U.S. Food and Drug Administration (FDA) announced it was scaling back foreign and domestic surveillance facility inspections and relying instead ...
Key elements for successful remote auditing
COVID-19 updates for tax and accounting firms. Looking for other information or guidance related to COVID-19? As an essential service to your clients and communities, this complete set of free COVID-19 resources for audit, tax, and accounting will help you guide your clients confidently through this time.
GUIDELINES FOR CONDUCTING REMOTE AUDITS - Rainforest Alliance
SA-G-GA-1-V1 3 1. INTRODUCTION Rainforest Alliance is a growing network of people inspired and committed to work together in order to achieve our mission to conserve biodiversity and ensure sustainable livelihood.
ISO 9001 Auditing Practices Group Guidance on: REMOTE AUDITS
© ISO & IAF 2020 – All rights reserved www.iaf.nu ; https://committee.iso.org/home/tc176/iso-9001-auditing-practices-group.html Editon1 2020-04-16
How to mitigate remote vendor access?
In order to mitigate the risks of remote vendor access, and gain better network access control, your organization should take steps to monitor third-party activity in greater detail. In vendor risk assessment, a good first step would be to create a vendor risk assessment checklist, which might include actions such as:
What is audit trail?
An audit trail and access notifications can set off alarms when unusual activity occurs. Granular audit records provide forensic details in the event of a breach or mistake to help track down the root cause and responsible party or parties.
What is vendor privileged access?
With the platform’s vendor privileged access features, enterprises can manage their vendors’ remote access efficiently and securely, while giving tech vendors just the right amount of access to the applications and systems needed to complete their job – and nothing more. You don’t have to be in the dark any longer. Now you can shine a light on who’s doing what on your network, at all times, to get a complete picture of all third-party activity.
What is a security audit platform?
A platform should offer network/IT security audit tools designed to give a total picture of all third-party remote access activity at the individual level. With its detailed audit functionality, organizations can ensure vendor accountability and compliance with industry regulations – and tech vendors can prove the “who, what, where, when, and why” of any remote support session.
What are the features of a secure audit?
Some features of a secure audit include: Real-time specific knowledge of each vendor connection, why they are connecting, and the activity associated with each individual user. Customizable, contextual labels and tags to identify ticket numbers, requestor, and other organization-specific data.
Why use outside vendors?
These third parties provide the ability to scale a business, bring new and vital expertise to bear on problems, and let you concentrate on core competencies . However, vendors can also bring a great deal of risk, especially when it comes to how they access your network and sensitive data.
Why is it important to implement internal audits?
For the sole purpose of risk management, it’s important to implement internal audits that identify and monitor all third-party vendors who have access to your network . Here’s how you can get started.
Who needs privileged accounts?
Many organizations need to provide privileged accounts for two types of users: employees and external users, such as technicians and contractors. However, organizations using external vendors or contractors must protect themselves from potential threats from these sources.
What is RDP server?
RDP is a protocol originally developed by Microsoft, which enables remote connection to a compute system. RDP is also available for MacOs, Linux and other operating systems. The RDP server listens on TCP port 3389 and UDP port 3389, and accepts connections from RDP clients.
What is SASE security?
SASE is a new security model, leveraging software-defined networking (SDN), that helps users connect securely to remote data centers. It includes technologies like cloud access security broker (CASB), secure web gateway (SWG), firewall as a service (FWaaS), and ZTNA (ZTNA, described above, can be a component within a SASE solution).
What is multifactor authentication?
Multi-factor authentication (MFA) is a secure access control process that combines multiple credentials to verify the identity of a user. It is especially important, and is commonly used, for secure remote access.
What is a VDI gateway?
VDI solutions provide dedicated gateway solutions to enable secure remote access.
Is remote access technology progressing?
Remote access technology made great progress. There are many new ways for users to access computing resources remotely, from a variety of endpoint devices. Here are some of the technologies enabling secure remote access at organizations today.
What is remote access monitoring?
Remote Access monitoring reports remote user activity and status for DirectAccess and VPN connections. It tracks the number and duration of client connections (among other statistics), and monitors the operations status of the server. An easy-to-use monitoring console provides a view of your entire Remote Access infrastructure. Monitoring views are available for single server, cluster, and multisite configurations.
What is direct access connection?
For DirectAccess, a connection is uniquely identified by the IP address of the remote client. For example, if a machine tunnel is open for a client computer, and a user is connected from that computer, these would be using the same connection. In a situation where the user disconnects and connects again while the machine tunnel is still active, it is a single connection.
What is monitoring in a network?
Monitoring shows actively connected users at a given point in time.
Is a machine tunnel a single connection?
For example, if a machine tunnel is open for a client computer, and a user is connected from that computer, these would be using the same connection. In a situation where the user disconnects and connects again while the machine tunnel is still active, it is a single connection.
Why is remote access important?
Proper remote access audit processes are important to any information security program . User accounts and rights should regularly be audited against employment records. Logs of router, firewall, and Intrusion Detection Systems (IDS) should be reviewed on a regular basis. Not so surprisingly, all of these reviews should be documented. Access to your networks and systems by third parties should be audited as well, even closer than internal employee activities since this type of access represents an outsized risk to your security. The security of vendors and other third parties may not be as high as your companies and unfortunately, if they are connected to your systems, their vulnerabilities become yours. Also, you don’t have as much information about their employees as you have on your own. Third-party data breaches are on the rise and many regulations now require covered entities to document and secure third-party remote access. For all these reasons, you should keep granular audit records on all third-party access and have a regular process to review them. Only by doing this can you catch a vendor who is breached or who has a malicious current or former employee.
Why is it important to audit third party access?
Doing audits of third-party remote access is important, but doing them right makes all the difference. If you have only cursory access reviews or only go to your logs when there is an issue, you stand little chance of stopping a breach in progress or before it starts. Get your third party review processes, procedures, and technology up to par, because if you are only using audits sporadically or after an issue crops up, it is probably too late. To learn more about the importance of auditing correctly, check out our blog that highlights how you can survive your next cybersecurity audit.
Why use SSOT in vendor audit?
Having an SSOT for vendor audit information will allow you to view the whole story of each session in one place and even connect multiple sessions. This is key to being able to “see the forest for the trees” in audit data.
What is SSOT in log audit?
In order for your log audits to be effective and efficient, strive to create a Single Source of Truth (SSOT) for all vendor activity. Whether you use a Syslog server just for this information or one of the VPAM systems mentioned previously, this will allow your reviewers to see the whole story in one place.
How many breaches are reported from outside the company?
According to M-Trend’s Report, 53% of breaches are reported from a source outside the company. This either means that the audit reviewers are asleep at the wheel, or don’t have the right tools to detect such breaches before they make it outside the company. It is no good having all the technology and logs in the world if you don’t review them on a regular basis. Set up a review schedule and make sure that it is done by auditing your audit from time to time (external auditors will also do this). Implementing real-time notifications and alerts are also a good practice to adhere to. Only by making effective use of your audit logs can you possibly keep an incident from turning into a breach.
What are the three principles of third party risk management?
I have written often about the three main principles of sound Third-Party Risk Management (TPRM); they are identify, control and audit . By using these three basic control areas, risk from third parties to organizations can be greatly reduced. Each area has more details to its proper implementation and I will do a deep dive on the third principle, audit, in this article.
Can a third party remote access be a hacker?
This is especially true of third-party remote access since it’s coming from an external source that is often not easily identifiable. Strange IP addresses could be a remote contractor or a hacker bent on destruction, but it’s hard to tell that from typical firewall or router logs that contain little else.
Provide secure, uninterrupted access to your networks
Take your infrastructure, for example.
Virtualized offices bring new cybersecurity risks
You’ll also want to review your company’s cybersecurity efforts.
Stay productive and collaborative, no matter where your team is located
It’s critical to ensure productivity and support remain high in virtualized offices.
Question
I suspect that an admin user is accessing my Work Computer by \\Hostname\C$ and checking my documents. Is there a way I can track this down?
Answers
I’m afraid that it’s yes. The security events will start appearing in your event viewer in the security log. As well as events 4624 (logon) and 4634 (logoff), I believe 4778 (session connect) and 4779 (session disconnect) are useful for monitoring remote desktop sessions.
All replies
Just found event ID 5140 in Security logs, is this the only way to check?
Why are firms turning to remote audits?
For quality and compliance teams, the sudden workforce disruption is complicating—and often preventing— in-person quality audits led by qualified third parties. To avoid compounding delays due to canceled or deferred audits, firms are increasingly turning to remote or “virtual” audits to maintain their assurance activities until normal operations can resume.
When incorporating remote facility review into a larger remote auditing plan, should auditors note the areas they feel need?
When incorporating remote facility review into a larger remote auditing plan, auditors should note the areas they feel need to be captured through visual media like photos and video during document review. As part of this document review, auditors should note known or possible process problems, such as complaints, CAPAs, and deviations, so that they can be evaluated remotely.
What should be checked during a Wi-Fi audit?
Connectivity and A/V checks: If a live facility walkthrough is included in the audit, the route should be checked with devices that will be used to livestream the audit prior to audit day to ensure wi-fi dead spots don’t threaten the process. This guide offers more detail on this point during its discussion of facility reviews.
How long should a remote closing meeting be?
A remote closing meeting shouldn’t be substantively different from that of an in- person audit. These should typically be scheduled a day or two following interviews—a timeframe that enables auditors to review their findings and meet as a team to gather preliminary audit results.
How long is a remote interview?
Barring technical difficulties, interview times should largely match those of a traditional audit: 30 to 90 minutes with program owners, 15 to 30 minutes with implementation personnel, and short er interviews with more general responsibilities.
How long should an audit be completed?
If an audit is typically completed in two days, for example, an additional half day may be needed to conduct the same activities remotely.
Is remote auditing as efficient as on-site auditing?
Remote auditing is rarely as efficient as on-site auditing, so consider whether sampling may be necessary. Especially in areas where a full data review is traditionally conducted, be sure to coordinate a sampling strategy with the auditor and review the strategy with audit participants so sampling can be done accurately and appropriately.
Where is the RDP authentication log?
Authentication shows whether an RDP user has been successfully authenticated on the server or not. The log is located in “Windows -> Security”. So you may be interested in the events with the EventID 4624 ( An account was successfully logged on) or 4625 ( An account failed to log on ). Please, pay attention to the LogonType value in the event description. If the Remote Desktop service has been use to create new session during log on, LogonType = 10. If the LogonType = 7, it means that a user has reconnected to the existing RDP session.
What does the RDP session ID return?
The command returns the session ID (ID), the name of user (USERNAME) and the session state (Active/Disconnect). It is convenient to use this command when you need to get the ID of the user RDP session in case shadow connection is used.
What does 9009 mean in RDP?
The event with the EventID 9009 ( The Desktop Window Manager has exited with code <X>) in the System log means that a user has initiated logoff from the RDP session with both the window and the graphic shell of the user have been terminated.
What is EventID 4778?
The event with the EventID 4778 in Windows -> Security log (A session was reconnected to a Window Station). A user has reconnected to an RDP session (a user is assigned a new LogonID).
What is a network connection?
Network Connection is the establishment of a network connection to a server from a user RDP client. It is the event with the EventID 1149 ( Remote Desktop Services: User authentication succeeded ). If this event is found, it doesn’t mean that user authentication has been successful. This log is located in “Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational”. Enable the log filter for this event (right-click the log -> Filter Current Log -> EventId 1149 ).
How to check RDP logs?
You can check the RDP connection logs using Windows Event Viewer ( eventvwr.msc ). Windows logs contain a lot of data, and it is quite difficult to find the event you need. When a user remotely connects to the remote desktop of RDS (RDP), a whole number of events appears in the Windows Event Viewer. There are several different logs where you can find the information about Remote Desktop connections. We’ll look at the logs and events on the main stages of an RDP connection that may be of interest to the administrator:
What does the logs do on a RDP server?
Then you will get an event list with the history of all RDP connections to this server. As you can see, the logs provide a username, a domain (in this case the Network Level Authentication is used; if NLA is disabled, the event text looks differently) and the IP address of the computer, from which the RDP connection has been initiated.
How to mitigate remote vendor access?
In order to mitigate the risks of remote vendor access, and gain better network access control, your organization should take steps to monitor third-party activity in greater detail. In vendor risk assessment, a good first step would be to create a vendor risk assessment checklist, which might include actions such as:
What is audit trail?
An audit trail and access notifications can set off alarms when unusual activity occurs. Granular audit records provide forensic details in the event of a breach or mistake to help track down the root cause and responsible party or parties.
What is vendor privileged access?
With the platform’s vendor privileged access features, enterprises can manage their vendors’ remote access efficiently and securely, while giving tech vendors just the right amount of access to the applications and systems needed to complete their job – and nothing more. You don’t have to be in the dark any longer. Now you can shine a light on who’s doing what on your network, at all times, to get a complete picture of all third-party activity.
What is a security audit platform?
A platform should offer network/IT security audit tools designed to give a total picture of all third-party remote access activity at the individual level. With its detailed audit functionality, organizations can ensure vendor accountability and compliance with industry regulations – and tech vendors can prove the “who, what, where, when, and why” of any remote support session.
What are the features of a secure audit?
Some features of a secure audit include: Real-time specific knowledge of each vendor connection, why they are connecting, and the activity associated with each individual user. Customizable, contextual labels and tags to identify ticket numbers, requestor, and other organization-specific data.
Why use outside vendors?
These third parties provide the ability to scale a business, bring new and vital expertise to bear on problems, and let you concentrate on core competencies . However, vendors can also bring a great deal of risk, especially when it comes to how they access your network and sensitive data.
Why is it important to implement internal audits?
For the sole purpose of risk management, it’s important to implement internal audits that identify and monitor all third-party vendors who have access to your network . Here’s how you can get started.
