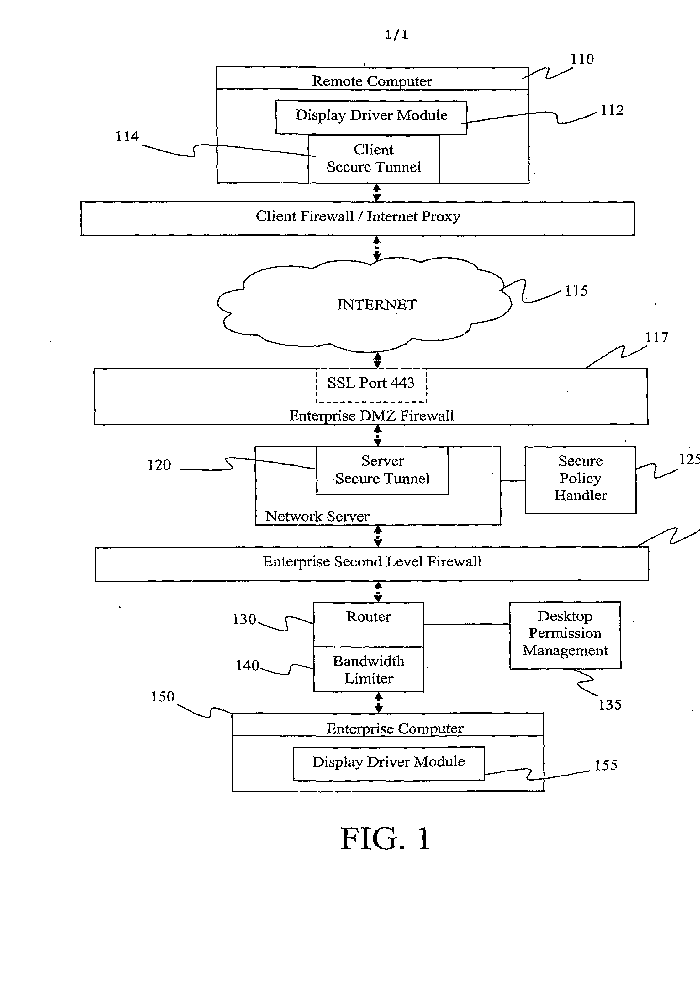
Remote users must be required to authenticate before being granted access to company information. Remote access must be logged in a central database and kept for a period of at least 30 days. Access logs must be reviewed regularly.
Full Answer
What is a remote access policy?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes. What Is a Remote Access (Control) Policy?
Do you need a remote box system for bank access control?
For larger facilities and banks with more employees and customer traffic, an additional layer of bank access control security may be required. Using a remote box system, the key control cabinet can be placed in a secure room.
What is a remote access policy (rap)?
What Is a Network Security Policy? A remote access policy is commonly found as a subsection of a more broad network security policy (NSP). The network security policy provides the rules and policies for access to a business’s network.
What security challenges do banks face with remote working?
Indeed, beyond just being able to connect securely, banks need to be able to insure that their employees have secure hardware as well-and the sudden shift to remote access has definitely created some short-term “equipment challenges,” says Emily Larkin, chief information security officer for Abrigo, a technology provider. “Institutions need to m...

What is in a remote access policy?
A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in the office, e.g., password policy.
How a remote access policy may be used and its purpose?
The purpose of a remote access policy is to outline the expectations of those users' behaviors while connecting to your network in an attempt to safeguard that network from viruses, threats or other security incidents.
What is a remote access standard?
PURPOSE. Remote Access refers to the ability to access UMW network resources while off campus. Security measures for remote access should be implemented based on sensitivity and risk to University systems and data.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
Is IT safe to allow remote access?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
How do you implement remote access?
How to use Remote DesktopSet up the PC you want to connect to so it allows remote connections: Make sure you have Windows 11 Pro. ... Use Remote Desktop to connect to the PC you set up: On your local Windows PC: In the search box on the taskbar, type Remote Desktop Connection, and then select Remote Desktop Connection.
What is an access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
What is remote accessing?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
Which is the secure standard function for remote access?
MFA is imperative to authenticate users for secure remote access. Many regulations and compliance standards require MFA for privileged remote access.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is remote access and its advantages?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
What are two types of remote management?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is the purpose of a privileged access policy?
Privileged access (root, superuser, or administrator) – Gives the user full and unrestricted access rights on the workstation/server. This includes installing any hardware or software, editing the registry, managing the default access accounts, and changing file-level permissions.
What is the purpose of a password policy?
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organization's official regulations and may be taught as part of security awareness training.
What constraints are available for use in a remote access policy?
Once a remote access policy has authorized a connection, it can also set connection restrictions (called constraints) based on the following: Encryption strength. Idle timeout. IP packet filters.
What is an access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
What is VPN policy?
Policies for VPN remote access can be standardized. These policies “shore up” and prevent the use of rogue devices and access by non-authorized users , including the worker's family members or housemates. The policy also enforces proper email protocols to protect information from being sent through unsecured or untrusted sources, and also provides rules that limit or prohibit split tunnel configurations that allow mobile users to access both secure and unsecure networks simultaneously.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
What is unauthorized access policy?
Even if the employee provides their own equipment, laptop, or mobile device, the policy dictates and enforces the minimum-security requirements necessary. The policy can also provide determinations on who is allowed remote access, the level of access, and penalties for misuse.
What Is a Remote Access Policy?
For example, sales personnel can now use tablets and other mobile devices to connect remotely to their office networks while on client calls and bring up data that may be important for closing deals . Recent events have further boosted the number of remote workers to an estimated 42% of the US workforce.
Why Is a Remote Access Policy Important?
If a remote access policy is not in place, such risky behavior could go on unmitigated, without the organization finding out about it until after the occurrence of a breach.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
Why is password policy important?
It helps ensure that only those users who need it are given network access, as long as their devices are also compliant with the guidelines. When implemented properly, it helps safeguard the network from potential security threats.
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
How to ensure that you do not miss anything when updating your remote access policy?
To ensure that you do not miss anything when updating your remote access policy, consider your organizational, legal, contractual and regulatory obligations when you compile the list of policy requirements. After that, identify the procedural and technical controls required to fulfill the policy, making sure to reinforce or replace existing controls that have not been effective.
Can you customize remote access policy?
Always ensure that your remote access policy is not an exact copy of another organization’s template; rather, you should customize it depending on your requirements. Otherwise, it might not be that useful for your organization.
What is remote access?
Remote access refers to the process of connecting to internal resources from an external source (home, hotel, district, or other public area). The ability to securely and reliably connect to business resources from a remote location increases productivity.
Who bears full responsibility for any access misuse?
Users shall bear full responsibility for any access misuse
What is LEP password policy?
All user passwords shall be strong and follow guidelines and procedures in the [LEP] Access Control and Password Policy. Staff shall ensure that devices used for work purposes are not shared in a multi-user capacity, violate AUP conditions, or used in any inappropriate activity.
What is information security?
Information security shall determine the appropriate access methodology and hardening technologies up to and including two factor password authentication, smart card, or PKI technology with strong passphrases
What is LEP policy?
This policy defines standards for staff to connect to the [LEP] network from a remote location. These standards are designed to minimize potential exposures including loss of sensitive information, and limit exposure to security concerns through a consistent and standardized access method.
What happens if a staff member is found in a policy violation?
Staff members found in policy violation may be subject to disciplinary action, up to and including termination.
Can you use personal equipment to connect to a LEP network?
Personal equipment shall not be used to connect to the [LEP] network using remote connection software and exceptions require [Insert Appropriate Role] written approval
How many attacks on banks originate from phishing?
According to recent Aite Group research, 94 percent of attacks on banks originate through phishing emails sent to employees. . “As soon as we move employees to remote connections, during a time of high stress, people are nervous and looking for news [about the pandemic and quarantine]and less likely to look closely,” says Steve Hunt, Aite’s senior analyst for cybersecurity.
How many employees does State Bank have?
Take for example the State Bank Group, a $230-million-asset bank headquartered in Wonder Lake, Ill. With eight locations and 75 employees, President and CEO Michelle Toll describes her institution as “a very traditional community bank”—one that, until March, like many of its counterparts only had “a very small percentage of employees working from home periodically, no one on a regular basis.” Then with the onset of coronavirus concerns, in the space of just a few days the bank needed to rapidly move roughly 70 percent of its staff to remote working situations.
Do banks need to be able to connect securely?
Indeed, beyond just being able to connect securely , banks need to be able to insure that their employees have secure hardware as well—and the sudden shift to remote access has definitely created some short-term “equipment challenges,” says Emily Larkin, chief information security officer for Abrigo, a technology provider. “Institutions need to make sure employees have corporate–owned and managed devices, which are secured through corporate malware protections, vulnerability detection, AV, patching, and local firewalls,” she says, adding that they need to make internal applications available to external remote workers so they do not use their own uncontrolled equipment or applications.
Can banks use internal applications outside the walled garden?
Applications that historically have been protected by the nature of their architecture as internal enterprise applications are now being used outside that walled garden via internet access, Larkin explains. “That brings about a series of unknowns and potential unidentified application security vulnerabilities.” Banks may be forced to shortcut their hardening processes or ensure appropriate cybersecurity testing has been conducted on these apps, she adds.
What is remote access in a company name?
Remote access is defined as any connection to [COMPANY NAME]’s internal network from a location outside of any affiliated company offices.
Why is remote access important?
Today, every organization should have a robust remote access policy that provides employees with clear direction on how to connect securely when at home or on the road. As remote work opportunities increase and travel remains a big part of corporate life, it’s more important than ever for organizations to ensure their employees have a secure means of accessing critical corporate data from any location.
How should VPN usage be monitored?
Monitoring. Remote access and VPN usage should be logged and monitored in a central database and reviewed regularly to detect anomalies and make changes to remote access privileges.
How long do remote users have to log in?
Remote access must be logged in a central database and kept for a period of at least 30 days. Access logs must be reviewed regularly.
What is the purpose of the Company Name policy?
The intent of this policy is to establish guidelines specifically pertaining to remote access to [COMPANY NAME]’s internal network. Preventing unauthorized access to company data from insecure networks is of utmost importance to [COMPANY NAME]. This policy is designed to ensure remote and/or traveling employees have the ability to securely connect to the corporate network without fear of threat and to provide the Company with an additional means of monitoring and controlling access to the internal network.
What to do if your connection is compromised?
If you believe your connection may have been compromised, please immediately report the incident to [RELEVANT CONTACT].
Can a vendor remotely access a company?
Third-party member access should be logged, strictly monitored, and promptly revoked when that access is no longer required. If possible, vendor remote access should be systematically restricted.
What are the key questions that banks need to ask themselves about access control?
Ultimately, banks need to ask themselves how far they are willing to extend themselves for their end users and what level of risk they are willing to assume in the process. Traditionally, banks have erred on the side of risk avoidance, being very reluctant to expose data to outside risks. That has changed dramatically in the past 10 years as the ubiquity of mobile platforms and more powerful apps have made convenience, productivity and accessibility competitive priorities.
What is access control?
Fundamentally, the goal of access control is to oversee and ensure the creation of specific policies and mechanisms designed to control access by authorized individuals and devices, while disallowing access to all others. Authorized individuals may include employees, technology service provider (TSP) employees, vendors, contractors, customers or visitors. Access should be authorized and provided only to individuals whose identity is established and their activities should be limited to the minimum required for business purposes.
What is application access?
Application Access. Access controls in this category should deploy authentication and authorization controls for applications, monitor access rights to ensure minimum required levels and correlate with current user needs (including possible time-of-day limitations on access), log access and security events, and provide rapid analysis of user activities.
What is operating system access?
This begins with securing access to administrative tools/utilities, restricting and monitoring privileged access and logging and monitoring user or program access to sensitive resources. Controls should also provide alerts on critical security events, deliver updated operating systems and security patches and secure all devices (workstations, laptops, tablets, etc.) that can access the operating system.
What is an authorized device?
Authorized devices are those for which placement on the network is approved in accordance with institutional policy. Change controls are typically used for devices inside the external perimeter and to configure institution devices to accept authorized connections from outside the perimeter. Effective access control mechanisms include numerous controls throughout all layers of the network stack to safeguard and limit access to key information system assets.
Can longtime employees have more access?
As a result, longtime employees tend to have much more access than they should have . Temporary solutions – granting someone temporary access in an emergency situation, for example – frequently go uncorrected and can compromise an entire system of access controls. A small exception here, a minor tweak there, and it is all too easy to let it get away from you.
Should remote access be enabled?
Remote communications should be enabled only as needed. Access should be controlled via approvals and reviewed through regular audits; robust, end-to-end controls over remote access configurations should be implemented; all remote access communications should be logged and monitored; remote access devices should be secured;
