What is secure remote access?
How does ZTNA improve security?
What is Zscaler private access?
How does a VPN work?
Why are IPs never exposed to the internet?
Can IoT services be hosted on premises?
Can a VPN attack be zero trust?
See more
About this website

Why do we need secure remote access?
Secure remote access includes keeping users safe from web-based malware threats such as ransomware and phishing attacks. Raises awareness of security issues – An increasingly mobile workforce presents many new security challenges, and for many of them education is the best cure.
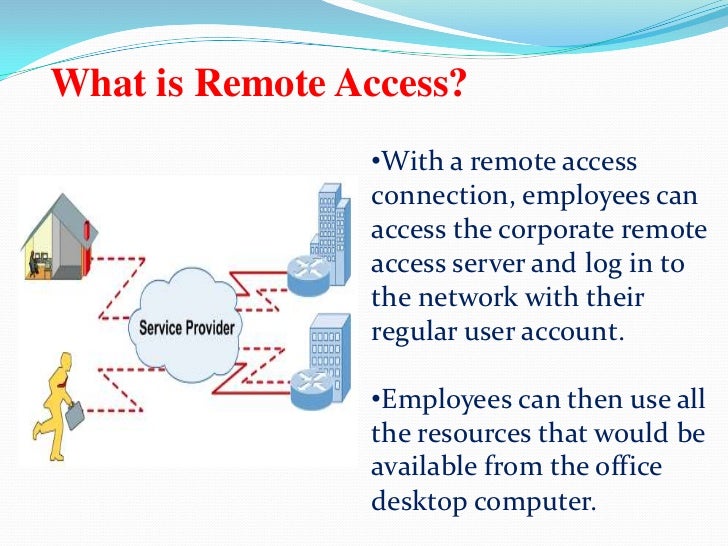
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What are the advantages and disadvantages of remote access?
Advantages of Remote Access1) Flexible Access. ... 2) Flexible Set-Up and Costs. ... 3) Full Control on Authorization and Access. ... 4) Centralized Storage and Backups. ... 5) Shared Resources; Greater Efficiency and Collaboration. ... 1) Security Issues. ... 2) Version Problems and Data Liabilities. ... 3) Hardware Issues Still Need On-Site Work.More items...•
What are the advantages of remote administration?
Top 5 Proven Benefits of Remote AdministrationRebooting or shutting other computers down over a network.Remotely connect to the machine to troubleshoot its issues.To install software on another machine.To monitor or supervise others for assistance.
How do you secure remote access to employees?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
Which is the secure standard function for remote access?
MFA is imperative to authenticate users for secure remote access. Many regulations and compliance standards require MFA for privileged remote access.
Should I give remote access to my computer?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
What are the types of remote access?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What are the security threats with remote access and how can it be secured?
Many remote access security risks abound, but below is a list of the ones that jump out.Lack of information. ... Password sharing. ... Software. ... Personal devices. ... Patching. ... Vulnerable backups. ... Device hygiene. ... Phishing attacks.
Fast, direct, secure private app access for all users, devices, and ...
Zscaler Private Access ™ Fast, direct, secure private app access for all users, devices, and locations Data Sheet 2022 Zscaler, Inc. All rights reserved.
What is Secure Remote Access? - Citrix
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.. Pushing out security software and updates to every personal device and controlling every internet ...
Zscaler FAQs | What does Zscaler do and more
Zscaler provides the technology and expertise to guide and secure organizations on their digital transformation journeys. We help them move away from appliance-based network and security infrastructure models, replacing traditional inbound and outbound gateways with modern cloud-delivered services built for today’s business.
What is Secure Remote Access? - Definition | VMware Glossary
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization’s digital assets and prevent the loss of sensitive data.Secure remote access can encompass a number of methodologies such as VPN, multifactor authentication, and endpoint protection, amongst others.
What is secure remote access?
Secure remote access describes the ability to securely access networks, devices, and applications from a “remote” location, which means “off the network.”
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
What is Zscaler private access?
Looking more closely, Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them. ZPA is a true software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers.
How does a VPN work?
VPNs work by extending the internal network to external users so they can access resources on the network. Opening the network in this way enables it to be “found” by your remote users, but it also means it can be found by adversaries. They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data.
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
Can IoT services be hosted on premises?
IoT services that are hosted on-premises can benefit from optimized speeds. Performance speeds can increase if local users do not have to connect out to the internet to access apps that are hosted on-premises. The other option is ZTNA as a service, such as Zscaler Private Access.
Can a VPN attack be zero trust?
They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data. In contrast, the zero trust approach treats all traffic, including traffic already inside the perimeter, as hostile.
How does secure remote access work?
A well-designed remote access tool can enable secure connections to target systems and prevent unauthorized access. The following steps define a general secure remote access process, and are applicable for most of the enterprise remote access architectures.
What are the benefits of adopting secure remote access methods?
Implementing a secure remote access solution as part of their cybersecurity program helps enterprises mitigate security risks, reduce operational complexity, improve visibility into privileged access, and adhere to compliance standards.
What is ManageEngine Access Manager Plus?
ManageEngine Access Manager Plus is a secure remote access solution built to take care of administrative access to remote endpoints and other critical IT systems. The solution's gateway server routes all remote connections through an encrypted channel, protecting enterprise networks from malware and cybercrime. Through robust authentication, granular controls, and session management capabilities, Access Manager Plus minimizes deliberate and unintentional access misuse risks while also letting enterprises choose and design a utilitarian remote access strategy.
What is the most common form of remote access?
VPNs are the most common form of remote access. They use authentication and encryption to establish a secure connection to a private network over the internet.
Why is privileged session monitoring important?
Privileged session monitoring and recording promote organizational transparency and enable IT admins to view and, if necessary, interrupt and terminate a malicious privileged session.
What are the challenges of remote working?
Remote working also presents new challenges, notably employees being caught by sophisticated phishing scams and hacking attempts. Cybercriminals leverage weak and vulnerable points in insecure remote access methods and VPNs to wreak havoc.
Why do organizations use VPNs?
Most organizations use VPNs to enable remote access to remote systems outside the corporate network , which allows too much lateral movement. VPNs don’t provide granular controls, and using them to facilitate remote administrative access increases the vulnerability to breaches, insider threats, and compromised credential risks.
Why is remote access important?
Taking the last benefit one step further, having remote access makes it possible to access that key process data from anywhere in the world, all from one place. Whether that's from your laptop as you lay in bed at 2 am in your pajamas worrying about a decision you need to make that will affect your global operations or from a centralized operations center, having the ability to know everything about your operations on a global scale is key to making the right decisions for an enterprise as a whole.
What is the most basic requirement of those needing access to their company's industrial control system?
The most basic requirement of those needing access to their company's industrial control system is access and visibility to the actual data, whether that is the current level in a tank, the temperature of a piece of equipment or the production level for some period of time. Access to timely information for those making the daily decisions in a business is critical to making the right decisions.
Does security rest on physical possession?
Security, though, ultimately rests in who has physical possession of a device. Attack surfaces multiply relative to the number of connected devices, increasing the risk that a connected device could be compromised and used for a cyber-attack. But there is a better way.
Does an open firewall port allow cyber attacks?
The problem with that architecture is that it requires your IT department to open at least one firewall port, possibly more to enable that access. An open firewall port, no matter how many security rules have been applied to it, is still an open path for a cyber threat to worm its way onto your process network .
Is it necessary to have all of your industrial process data available to big data?
Additionally, making all of your industrial process data (or even a subset of it) available to big data, analytics or even historian systems might be necessary as part of corporate initiatives. Having a means of exposing the required data to those systems without compromising the security of your process network is imperative.
Is VPN a security measure?
VPN is considered the security measure, when in fact VPN is not a security measure but a secure path. Such a method still ultimately requires open firewall ports and direct access to the control system.
Is remote access to industrial control systems secure?
It's undeniable that secure remote access to industrial control systems is beneficial for many companies. But the "how" of that remote access is a gray area of pitfalls. As I mentioned earlier, it has traditionally been the accepted practice to simply have VPN access to the industrial network and just directly access the system.
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
Why do organizations need remote access?
On a more granular level, organizations have several reasons for enabling remote access to their OT environments. Software Toolbox identified three such factors: 1 Empowering decision-makers with data access and visibility: Decision-makers need access to and visibility over data if they are to safeguard the organization’s interests. They need timely information to make the right decisions. 2 Centralizing access across geographically distributed systems: Many organizations that own or operate OT environments have assets that are scattered across different countries and continents. This makes it difficult for people like remote workers to monitor those devices all at once. Remote access solves this problem by enabling an authenticated user to access those systems from anywhere in the world. Alternatively, organizations can centralize these access sessions within a single operations center. 3 Streamlining work with third parties: Organizations that own or operate OT environments need to be able to work with their third-party vendors, contractors and suppliers. This can be difficult depending on the scope of the supply chain. As a result, organizations could use remote access to share key important data with third parties rather than grant them full access to their entire environments. 4 Facilitating the implementation of updates: Per Security Week, many industrial control systems come with a contract through which equipment manufacturers are responsible for providing remote maintenance. It’s therefore critical that organizations ensure there’s remote access available to these device manufacturers. Otherwise, they could risk those OT assets not receiving an important update or fix when it’s misbehaving, for example.
Why do decision makers need access to data?
Empowering decision-makers with data access and visibility: Decision-makers need access to and visibility over data if they are to safeguard the organization’s interests. They need timely information to make the right decisions.
Why Is Secure Remote Access Important?
Secure remote access is important for three reasons: to safeguard and protect intellectual property; to increase employee productivity, and to enhance an organization’s competitive advantage. Organizations can confidently deliver on their current goals and innovate to achieve new ones when employees can work securely from everywhere.
What is remote desktop access?
Remote desktop access is an older and still popular method for accessing resources, typically on a corporate LAN. In this case, a user will connect to a physical or virtual computing instance located on the LAN. Popular examples include Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC).
Why do people use VPNs?
Organizations, governments, and businesses of all sizes use VPNs for secure remote access to data center resources or corporate local area networks (LAN). Personal VPNs have also become widely popular as they keep users’ locations private, ...
Is Google Chrome secure?
Most web browsers, like Google Chrome, provide some level of security for a secure web browsing experience. However, a successful secure remote access strategy provides organizations more control of the web browsing experience, eliminating reliance solely on web browser vendors for a secure web browsing experience.
Why is secure remote access important?
The number of companies operating fully or partially remotely has skyrocketed since the start of the COVID-19 pandemic, and many employers intend to keep it that way. A 2021 PwC survey found that 83% of employers say their shift to remote work has been successful, and 55% of employees say they would prefer to be remote at least three days a week post-pandemic.
How does remote access work?
Before you can remotely log on to a device or program, you'll need to install software on both the device you're using and the device you want to access. Once the application is installed, both devices need to be turned on. You then log in to the software and select the device you want to access, and then the software will mirror that device's screen.
What are the different types of secure remote access systems?
There are several options for securely accessing a device or program from a different location, and some may be used concurrently, depending on the level of access and security required. These are some of the most common types of secure remote access systems:
What is endpoint security?
Endpoint security: An endpoint security system secures a company's various devices on a network. These devices can include mobile devices, laptops, desktops and servers.
Why is it important to have security measures in place?
If you're granting your team members access to company devices or systems , it's important to have security measures in place to prevent any unauthorized access to your programs and data. Secure remote access systems involve a mix of different strategies, technologies, and applications that protect computers and networks from falling into the wrong hands.
Is RemotePC safe for small businesses?
Perfect for small businesses, RemotePC is easy to implement and offers several plans to fit the size of your company and number of devices. One of its biggest advantages is that you don't need to configure firewalls or proxy servers; once you're connected, you are already secure and can get to work.
Who is the CEO of RemoteTeam?
Sahin Boydas, CEO and founder of RemoteTeam.com, says employers with distributed teams should look for remote access solutions that have all the functions the business needs but are still simple to use.
Why Use a Vpn - 6 Challenges and How to Overcome Them
While VPN is more widely used today and meets the general needs of interconnecting remote networks, it has several drawbacks when compared to a modern, secure remote access approach:
Benefits of Secure Remote Access
Although the complexity cannot be removed from current processes completely, a secure remote access solution requires far less technical knowledge than traditional VPN concentrators.
How to Know if Secure Remote Access Is Right for You
Knowing the benefits of secure remote access is meaningless unless you can identify opportunities to implement it in your applications or networks.
Conclusion
Although there are many remote access solutions on the market, most started as IT solutions and are now being shoehorned into industrial environments. Solutions such as these are complex for all administrators and users and a far cry from the simplicity offered by a sophisticated industrial secure remote access solution.
What is secure remote access?
Secure remote access describes the ability to securely access networks, devices, and applications from a “remote” location, which means “off the network.”
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
What is Zscaler private access?
Looking more closely, Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them. ZPA is a true software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers.
How does a VPN work?
VPNs work by extending the internal network to external users so they can access resources on the network. Opening the network in this way enables it to be “found” by your remote users, but it also means it can be found by adversaries. They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data.
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
Can IoT services be hosted on premises?
IoT services that are hosted on-premises can benefit from optimized speeds. Performance speeds can increase if local users do not have to connect out to the internet to access apps that are hosted on-premises. The other option is ZTNA as a service, such as Zscaler Private Access.
Can a VPN attack be zero trust?
They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data. In contrast, the zero trust approach treats all traffic, including traffic already inside the perimeter, as hostile.