
7 Best Practices For Securing Remote Access for Employees
- Develop a Cybersecurity Policy For Remote Workers. If your business allows remote work, you must have a clear cybersecurity policy in place so that every employee’s access to company ...
- Choose a Remote Access Software. When telecommuting, there are three primary ways to secure your work online. ...
- Use Encryption. As important as it is to choose an access method for your online workers, it’s equally important those methods use encryption to secure remote employees’ data and ...
- Implement a Password Management Software. Since most data breaches occur due to the use of illegally acquired credentials, password management software is an invaluable solution to remote work security.
- Apply Two-factor Authentication. Authenticating the identity of a user is an essential aspect of access control. To gain access, typically, one would require a username and password.
- Employ the Principle of Least Privilege. An effective method to mitigate security risk is to limit the privileges of your workers. ...
- Create Employee Cybersecurity Training
- Enable encryption. ...
- Install antivirus and anti-malware. ...
- Ensure all operating systems and applications are up to date. ...
- Enforce a strong password policy. ...
- Use Mobile Device Management (MDM) ...
- Use Virtual Private Network (VPN) ...
- Use two-factor authentication.
What are the best remote access programs?
The best free remote desktop software
- Dameware Remote Everywhere (FREE TRIAL)
- ISL Online (FREE TRIAL)
- ManageEngine Remote Access Plus (FREE TRIAL)
- Zoho Assist (FREE TRIAL)
- N-able Take Control (FREE TRIAL)
- TeamViewer
- Atera
- Chrome Remote Desktop
- Microsoft Remote Desktop
- Remmina
How to develop a successful remote work access strategy?
Work from home prep checklist
- Cross-train employees
- Develop a list of critical business functions and essential personnel
- Create and disseminate temporary authority back up designations
- Have a communication tree with updated contact information and directions
- Determine alternative sources of supplies
- Review insurance policies and opportunities for adjustment or enhancement
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
How do you enable remote desktop access?
To enable remote connections on Windows 10, use these steps:
- Open Control Panel.
- Click on System and Security.
- Under the “System” section, click the Allow remote access option ...
- Click the Remote tab.
- Under the “Remote Desktop” section, check the Allow remote connections to this computer option.
What is the line of defense for remote access?
What is remote access VPN?
Why is IPSec VPN important?
Why is IPSEC used?
What is client side VPN?
What do people use in an office?
Should a company use IPSEC VPN?
See more
About this website
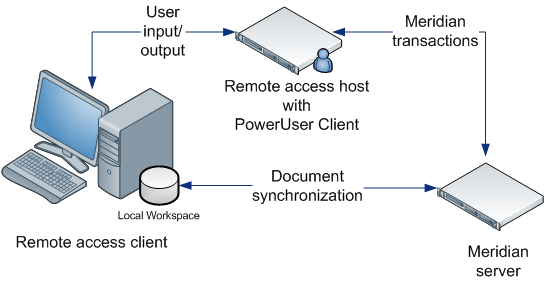
What is a best practice for compliance in the remote access domain?
Instead, a best practice is to adopt the principle of least privilege, which means that access for all users should be blocked by default and enabled only for the specific accounts that require it. This will require more configuration, but it is well worth the added security benefits.
What are security requirements for remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
Why is a remote access policy definition a best practice for handling remote employees and authorized users who require remote access from home or on business trips?
A remote access policy aims to keep corporate data safe from exposure to hackers, malware, and other cybersecurity risks while allowing employees the flexibility to work from remote locations.
How do I make remote access secure?
Basic Security Tips for Remote DesktopUse strong passwords.Use Two-factor authentication.Update your software.Restrict access using firewalls.Enable Network Level Authentication.Limit users who can log in using Remote Desktop.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Why RDP is not secure?
The risks of such exposure are far too high. RDP is meant to be used only across a local area network (LAN). Since RDP hosts support a listening port awaiting inbound connections, even the most secure installations can be profiled as a Windows Operating System and its version.
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
Why is it a best practice of remote access policy definition to require employees and fill in a separate VPN remote access authorization form?
Why is it a best practice of a remote access policy definition to require employees and users to fill in a separate VPN remote access authorization form? It is best practice of a remote access policy as it makes sure there are no repudiation of the user so that only authorized person can access the important documents.
What should a company consider when looking at adding remote employees?
These expectations should include work hours, availability, deadlines, meeting scheduling and attendance, work submission and more. When setting these requirements consider the differences between remote and in-house workers.
Who is more secure protocol for remote login?
Virtual private networks (VPNs) are a commonly used remote-access solution. They are designed to provide an encrypted tunnel for network traffic between a remote user and the enterprise network. VPNs also support security solutions like MFA that help to mitigate the threat of compromised accounts.
What is the difference between SSH and RDP?
A Major Difference between RDP and SSH RDP and SSH are designed to provide two distinct solutions for connecting to remote computer systems. RDP furnishes users with a tool for managing remote connections via a GUI. SSH offers a Secure Shell and is used for text-based management of remote machines.
What security considerations do you think are important for users accessing their company desktops remotely?
These are the top remote work security issues businesses should be wary of.Managing All Devices and Employees.Insecure Passwords.Phishing Emails.Using Unsecured Personal Devices & Networks.Video Attacks.Weak Backup and Recovery Systems.Require employees to connect over VPNs.Install multi-factor authentication.More items...
What is a remote access standard?
PURPOSE. Remote Access refers to the ability to access UMW network resources while off campus. Security measures for remote access should be implemented based on sensitivity and risk to University systems and data.
How can students secure remote access?
What schools can do to minimise cyber risksUse a reliable virtual private network (VPN) ... Provide phishing training to staff and students. ... Avoid sharing resources for work/learning and personal use. ... Install cyber security tools such as firewall and AV on home networks. ... Educate students on good password hygiene.
Five Remote Access Security Risks And How To Protect Against Them
COVID-19 has upended our way of life, and in doing so, has unleashed a Pandora’s box of new cyber threats. Security teams not only face the universal challenges imposed by this crisis, but must also overcome unique obstacles such as protecting a newly remote workforce and stopping pernicious attacks targeting remote users.
How to Secure Remote Access for Employees {Checklist}
How do you maintain security when employees work remotely, and your team is transitioning to a remote workforce? As remote work is becoming a more prevalent trend in business and considering the recent COVID-19 outbreak, there’s no better time for employees and companies alike to make strides in securing remote work.
Presentation - Security Concerns with Remote Access
Remote Access Security General remote access security SP 800-46, Security for Telecommuting and Broadband Communications Use virtual private networks
Guide to Enterprise Telework, Remote Access, and Bring Your Own Device ...
NIST Special Publication 800-46 . Revision 2. Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security . Murugiah Souppaya
What is remote access?
Remote PC access methods, such as desktop sharing, connect a remote computer to the host computer from a secondary location outside of the office. This setup means the operator has the ability to access local files on the host computer as if they were physically present in the office.
How to secure work online?
Your options are using either remote computer access, virtual private networks, or direct application access. Each method has its benefits and drawbacks. Choose the method that works best for your organization.
How to protect data with passwords?
To enact one-time-use credentials, create a log of passwords in a spreadsheet acting as a “safe.” When you a single-use password for business reasons, have the user label the password in the spreadsheet as “checked out.” Upon completion of the task, have the user check-in the password again and retire it.
How does a VPN work?
A virtual private network (VPN) is software that creates a secure connection over the internet by encrypting data. Through the process of using tunneling protocols to encrypt and decrypt messages from sender to receiver, remote workers can protect their data transmissions from external parties.
Can you use multiple security measures to thwart cyber threats?
Employing only one of the following security measures will not be enough to thwart cyber threats. Each security measure, in isolation, will not guarantee secure remote work; however, when used in tandem with multiple measures, it creates a compounding effect for your cybersecurity. 1.
Can a business be hacked remotely?
Most companies nowadays store data online on cloud storage services that are protected by encryption; although, regularly backing-up to a physical drive is also encouraged, as they cannot be hacked remotely.
How to allow remote access to a network?
Allowing access to an organization’s resources from outside the corporate network may be necessary for some businesses. Logically, when this kind of remote access is allowed, your organization takes on additional risks, and the access should be handled as securely as possible by: 1 Ensuring the remote access is encrypted (SSL, IPSec, etc.) 2 Ensuring there is strong authentication for remote access (Multi-factor Authentication or MFA) 3 Ensuring that strong passwords are required for remote access 4 If possible, require remote users to use company-provided hardware that has been secured to your company standards. Otherwise, ensure that employees understand the reasonable standards they should be taking (e.g., antivirus, passwords, etc.)
Is it necessary to allow access to resources outside the corporate network?
Allowing access to an organization’s resources from outside the corporate network may be necessary for some businesses . Logically, when this kind of remote access is allowed, your organization takes on additional risks, and the access should be handled as securely as possible by:
Is MFA enough for RDP?
If RDP or RDWeb are business-critical, using MFA isn't enough. They must also be used with a VPN. Remote technologies to use with extreme caution: Remote Desktop Protocol ( Never expose directly to the Internet) RDWeb (remote desktop over the web) Limit and review who has access.
What is remote access software?
MSPs with remote access software can perform system configurations, issue maintenance, and deliver service management for a slew of customers —all without ever leaving their desk. Remote access tools are gateways to their customers’ resources. That means not only their machines, but their IP and, ultimately, their data.
What does remote monitoring mean for MSPs?
The ability to monitor systems remotely also means MSPs are equipped to provide the 24/7 support their customers expect. Simply put, remote access software is a win-win for all.
Is remote access good for cyber security?
Remote Access Best Practices. Remote access comes with a range of benefits, but it’s not without risks. Cyberattackers often prey on exposed remote connections, waiting to infiltrate and spread viruses. To prevent successful cyberattacks, it’s important for MSPs to do everything in their power to keep their customers safe.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is IPSec VPN important?
IPSec VPN connections are also important for an employee who needs widespread access to the company’s network. A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is client side VPN?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data. RAS VPNs are appropriate for small companies, requiring a remote access for a few employees. However, most serious businesses have moved on from this basic form of VPN connection.
What do people use in an office?
Most, if not all, of the day-to-day tasks performed in offices today rely heavily on technology, mainly computers, laptops , tablets & smart devices. As the world and the global economy become increasingly interconnected, members of the staff too are required to go mobile. Sometimes, the need arises to work from home or somewhere away from the office, plus, a lot of companies have more than one office, in different parts of the world, and that requires them to have secure communications and exchange of data between offices.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
