What are the different types of remote access authentication?
Remote access authentication options. Remote access servers can be configured as dial-in servers or VPN servers. Dial-in servers use the Point-to-Point Protocol (PPP) or in the case of some older servers, the Serial Line Internet Protocol (SLIP) as the link layer protocol.
What authentication methods are supported by OpenWindows remote access servers?
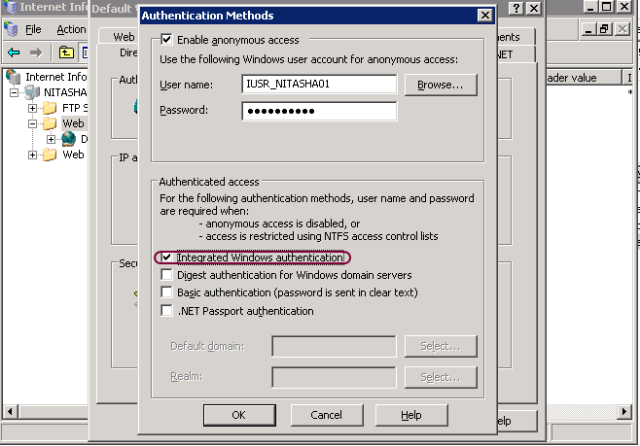
Windows remote access servers support the following set of authentication methods: Extensible Authentication Protocol/Transport Layer Security (EAP/TLS) For security purposes, PAP can be excluded as a viable option for most businesses because it sends passwords across the phone line or Internet in plain text.
What is the best free Remote Access app?
Our 6 Top Picks. 1 RemotePC. $3.95 for One-Year Two PCs Plan. at RemotePC. See It. RemotePC is one of the best low-frills remote-access apps, offering identical features ... 2 TeamViewer. 3 LogMeIn. 4 GoToMyPC. 5 VNC Connect. More items
What is the best Authenticator app for Android?
There are dozens of authenticator apps on the market, but a few that we would recommend are Authy, Microsoft Authenticator, LastPass and 1Password. Google Authenticator is another popular option, but seeing as it doesn’t require either a password or biometric login, it’s a potential security gap in a process that is trying to eliminate them.

Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
What is the strongest authentication method?
Experts believe that U2F/WebAuthn Security Keys are the most secure method of authentication. Security keys that support biometrics combine the Possession Factor (what you have) with the Inherence Factor (who you are) to create a very secure method of verifying user identities.
Which 2 methods of authentication can be used for remote access connections?
remote access servers support the following set of authentication methods:Password. Authentication Protocol (PAP)Challenge. Handshake Authentication Protocol (CHAP)Microsoft's. implementation of CHAP (MS-CHAP)Updated. version of MS-CHAP (MS-CHAP2)Extensible. Authentication Protocol/Transport Layer Security (EAP/TLS)
Which authentication service is best?
The top ten User Authentication and Access Management platforms include: Prove MFA | DUO Access | HID Global IAM | ESET Secure Authentication | Ping Identity | TypingDNA Verify 2FA | Thales SafeNet Trusted Access | Entrust Identity Enterprise | Okta Adaptive Multi-Factor Authentication | SecureAuth Identity Platform.
What is more secure than MFA?
2FA uses two factors and multi-factor uses more. Multi-factor is becoming more popular today, because it is inherently more secure. It can still be implemented poorly. There are more things to consider, of course, than just security.
Which two-factor authentication is best?
Duo Mobile The most powerful authentication apps for Android devices have been given to us by Duo Security LLC. Duo Mobile is designed to keep your login safe and secure. It comes with a two-factor authentication service that you may use with any app or website.
What are the 3 methods of authentication?
Authentication factors can be classified into three groups: something you know: a password or personal identification number (PIN); something you have: a token, such as bank card; something you are: biometrics, such as fingerprints and voice recognition.
What is the most commonly used form of authentication?
Passwords are the most common methods of authentication. Passwords can be in the form of a string of letters, numbers, or special characters.
What are the 4 general forms of authentication?
Four-factor authentication (4FA) is the use of four types of identity-confirming credentials, typically categorized as knowledge, possession, inherence and location factors.
Who are Auth0 competitors?
Top 10 Alternatives to Auth0OneLogin.Okta.Ping Identity.JumpCloud.Microsoft Azure Active Directory.Duo Security.LastPass.ForgeRock.
What is the difference between Okta and Auth0?
Both Auth0 and Okta include in-depth security measures to help businesses protect their data. Auth0 includes defenses such as incident response, security monitoring and data encryption while at rest and in transit. Okta also provides end-to-end encryption as well as monitoring through ThreatInsight.
What is the most popular IDP?
Popular IdPs for enterprise/corporate use include the following: AD....Popular identity providersGoogle.Facebook.Apple.Fitbit.Microsoft.Box.Amazon Web Services (AWS)
Which of the following is the most secure method of authentication?
Nowadays, the usage of biometric devices such as hand scanners and retinal scanners is becoming more common in the business environment. It is the most secure method of authentication.
Which authentication factor provides the highest level of security?
Biometric and possession-based authentication factors may be the strongest means of securing a network or application against unauthorized access.
What are the three types of authentication?
The three authentication factors are:Knowledge Factor – something you know, e.g., password.Possession Factor – something you have, e.g., mobile phone.Inherence Factor – something you are, e.g., fingerprint.
What is the best authentication method for wireless?
WiFi Protected Access: WPA / WPA2 / WPA3 This authentication method uses different encryption algorithms to encrypt the transport. Therefore, this type of network cannot be forged easily, unlike open networks, and users get privacy. Today, WPA2 is probably the most commonly used method to secure WiFi networks.
What is remote access server?
Remote access servers can be configured as dial-in servers or VPN servers. Dial-in servers use the Point-to-Point Protocol (PPP) or in the case of some older servers, the Serial Line Internet Protocol (SLIP) as the link layer protocol. VPN servers can use the Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), or IPSec tunnel mode to establish a secure "tunnel" over the Internet. Windows remote access servers support the following set of authentication methods: 1 Password Authentication Protocol (PAP) 2 Challenge Handshake Authentication Protocol (CHAP) 3 Microsoft's implementation of CHAP (MS-CHAP) 4 Updated version of MS-CHAP (MS-CHAP2) 5 Extensible Authentication Protocol/Transport Layer Security (EAP/TLS)
What does authenticator do?
The authenticator also calculates the hash value and compares the client's response with its own calculation. If the values match, the connection is established.
What is EAP TLS?
EAP/TLS provides for use of more secure authentication methods such as smart cards, Kerberos, and digital certificates, which are much more secure than the user name/password authentication methods above. It's defined in RFC 2716.
What is the protocol used for dial in VPN?
Dial-in servers use the Point-to-Point Protocol (PPP) or in the case of some older servers, the Serial Line Internet Protocol (SLIP) as the link layer protocol. VPN servers can use the Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), or IPSec tunnel mode to establish a secure "tunnel" over the Internet. ...
What is a RADIUS authorization?
Authorization refers to granting specific services to users based on their authenticated identity; restrictions can be imposed on certain users. Accounting refers to tracking the use of the network by users and can be done for billing, management, or security purposes. RADIUS is defined in RFCs 2865 and 2866.
Is MS-CHAP v2 secure?
Version 2 adds such features as mutual (two-way) authentication of both client and server, as well as stronger encryption keys. MS-CHAP v2 is more secure than CHAP for Windows systems.
Can you have multiple remote access servers on Windows 2003?
Windows 2003 Server Enterprise Edition's IAS implementation puts no limits on the number of RADIUS clients you can configure or on the number of RADIUS server groups you can have. Even more importantly, a single RADIUS server can support many remote access servers, so that as you add additional dial-in and/or VPN servers, their users are all still authenticated through one central point: the RADIUS server. The fact that the authentication server is separate from the access server (s) makes this both more secure and more scalable than other authentication methods.
What is the easiest program to use for remote access?
AeroAdmin is probably the easiest program to use for free remote access. There are hardly any settings, and everything is quick and to the point, which is perfect for spontaneous support.
How to access remote computer?
There are a couple of ways to access the remote computer. If you logged in to your account in the host program, then you have permanent access which means you can visit the link below to log in to the same account in a web browser to access the other computer.
What is Zoho Assist?
Zoho Assist is yet another remote access tool that has a free edition for both personal and commercial use. You can share screens and files, and chat remotely with the other user through a unique session ID and password.
How to connect to a host browser?
To connect to the host browser, sign on to Chrome Remote Desktop through another web browser using the same Google credentials or using a temporary access code generated by the host computer.
How to enable remote desktop access to a computer?
To enable connections to a computer with Windows Remote Desktop, you must open the System Properties settings (accessible via Settings (W11) or Control Panel) and allow remote connections via a particular Windows user.
How does remote utility work?
It works by pairing two remote computers together with an Internet ID. Control a total of 10 computers with Remote Utilities.
What is the other program in a host?
The other program, called Viewer, is installed for the client to connect to the host. Once the host computer has produced an ID, the client should enter it from the Connect by ID option in the Connection menu to establish a remote connection to the other computer.
What is the best remote desktop software?
RemotePC is the best remote desktop software right now. RemotePC is another stellar product from the team at iDrive (we also recommend its excellent cloud storage solution). RemotePC uses top-notch cloud tech to deliver class-leading remote access. Web, desktop, and mobile apps provide the access.
What is remote PC?
RemotePC is a hugely-popular remote computer access application that’s suitable for both home and—in particular—for business users. It uses cloud technology to deliver class-leading remote access solutions through an intuitive web application and native desktop and mobile apps. It also includes collaboration features such as voice chat.
What is remote desktop manager?
Remote Desktop Manager is a powerful remote computer access program offering scalable solutions for large businesses. It’s compatible with both Android and iOS devices and comes with a selection of impressive security features.
What is Zoho Assist?
Cloud-based Zoho Assist is one of our favorite remote access tools because it enables you to access almost any device. It provides specialized remote support and unattended access plans designed to streamline workflow processes.
What is Connectwise Control?
ConnectWise Control provides highly specialized remote access solutions targeted at specific users. Its three Support plans come with some remote access features, and include powerful tools to help IT staff and support technicians solve problems remotely. The Access plan caters for 25 devices and is aimed at those who want to connect with numerous remote devices.
Where does RDS run?
Typically, the machine that hosts RDS runs in the same physical location - such as the same office building - as the computers from which users access the remote desktop environments. It is also possible, however, to install RDS on a server running in the cloud and share desktops from the cloud.
How long does it take to set up a remote access?
Using remote access software is simple. They generally take no more than a few minutes to set up, and you will usually have to install the software on the computer or other device you want to access the remote computer with.
GoToMyPC LogMeIn
GoToMyPC is a remote access software product that gives you the freedom to work on your PC or Macintosh from anywhere in the world. All it takes to get started is a single download. The app installs, launches, and configures itself without restarting your computer.
TightVNC TightVNC
TightVNC is a cross-platform remote access software that allows you to connect to another computer remotely. The software uses a secure RFB protocol to establish a virtual network connection to the host.
Splashtop Business Access Splashtop Inc
Splashtop Business Access is remote access software that helps you manage workstations and other devices contained within your organization’s IT ecosystem. The product comes with tools to monitor multiple remote machines and can record each session.
Remote Access Software Overview
Remote desktop software allows full access to a target device remotely via the internet and through a secure network connection. This can be accomplished either from within an organization’s network out to a remote desktop client, or from the remote client back inside to the company servers and workstations.
What is an authenticator app?
Authenticator apps offer a more secure way to log into your sites and web services with two-factor authentication (2FA). We evaluate each of the most popular mobile authenticator apps to help you choose the best one.
Can you do 2FA on a banking site?
Yes, you can implement MFA simply by having your banking site send you a text message with a code you then enter into the site to gain access. However, that turns out not to be the best way to do 2FA. A vulnerability in SMS messaging recently came to light that let crooks reroute text messages.
Does Microsoft Authenticator work with schools?
Microsoft’s entry now includes secure password generation, and it lets you log in to Microsoft accounts with a button press. The Authenticator app also lets schools and workplaces who use it register users’ devices. Account recovery is an important feature that you should turn on if you use the app. That way, when you get a new phone, after you install Microsoft Authenticator, you’ll see an option to recover by signing into your Microsoft account and providing more verifications.
Is 2FA secure?
Leaks and hacks we’ve read about in recent years make it clear that passwords alone don't provide enough security to protect your online bank account or social media accounts. Two-factor authentication (2FA or MFA, for multifactor authentication) adds another layer of protection, and PCMag writers frequently exhort our audience to use it. Authenticator apps, such as Authy, Google Authenticator, or Microsoft Authenticator, enable one of the more-secure forms of 2FA. Using one of these apps can even help protect you against stealthy attacks like stalkerware.
Does Google Authenticator back up your phone?
Authy, Duo Mobile, LastPass Authenticator, and Microsoft Authenticator offer this, while Google Authenticator does not .
Can you use authenticator on phone?
You can simply sync with the Microsoft account you associated with the authenticator, and after that, you’ll see the logins you’ve saved and synced from the Edge browser. In addition, you can simply use Authenticator as a password filler/saver utility on your phone. Advertisement.
What is remote access?
Remote PC access methods, such as desktop sharing, connect a remote computer to the host computer from a secondary location outside of the office. This setup means the operator has the ability to access local files on the host computer as if they were physically present in the office.
How to protect data with passwords?
To enact one-time-use credentials, create a log of passwords in a spreadsheet acting as a “safe.” When you a single-use password for business reasons, have the user label the password in the spreadsheet as “checked out.” Upon completion of the task, have the user check-in the password again and retire it.
Why is encryption important?
As important as it is to choose an access method for your online workers , it’s equally important those methods use encryption to secure remote employees’ data and connections. Simply put, encryption is the process of converting data into code or ciphertext.
Why use AES encryption?
As it stands, most businesses have the security protocol to use Advanced Encryption Standard (AES) to secure data due to its compatibility with a wide variety of applications. It uses symmetric key encryption, meaning the receiver uses a key to decode the sender’s data. The benefit of its use over asymmetric encryption is it’s faster to use. Look for encryption software that uses AES to secure company data.
How to secure work online?
Your options are using either remote computer access, virtual private networks, or direct application access. Each method has its benefits and drawbacks. Choose the method that works best for your organization.
Is remote work a trend?
As remote work is becoming a more prevalent trend in business and considering the recent COVID-19 outbreak, there’s no better time for employees and companies alike to make strides in securing remote work.
Can a business be hacked remotely?
Most companies nowadays store data online on cloud storage services that are protected by encryption; although, regularly backing-up to a physical drive is also encouraged, as they cannot be hacked remotely.
What is two-factor authentication?
Multi-factor authentication (MFA) is a digital authentication method used to confirm the identity of a user to allow them access to a website or app through at least two pieces of evidence.
What are the best authenticator apps?
There are dozens of authenticator apps on the market, but a few that we would recommend are Authy, Microsoft Authenticator, LastPass and 1Password. Google Authenticator is another popular option, but seeing as it doesn’t require either a password or biometric login, it’s a potential security gap in a process that is trying to eliminate them.