
What is BeyondTrust privileged access management?
Experience the industry’s most innovative, comprehensive platform for privileged access management. The BeyondTrust Privileged Access Management portfolio is an integrated solution that provides visibility and control over all privileged accounts and users.
What is privileged remote access and how does it work?
Privileged Remote Access enables security professionals to control, monitor, and manage privileged access to critical systems. Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault.
What is universal privilege management?
Our innovative Universal Privilege Management approach secures every user, asset, and session across your entire enterprise. Control, manage, and audit access for privileged remote employees and third-party vendors—no VPN needed.
What are the benefits of remote access?
Accessibility from any mobile device or web browser. Satisfy compliance requirements with comprehensive audit trails and session forensics. Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access.
See more
What is BeyondTrust privileged remote access?
BeyondTrust Privileged Remote Access empowers security professionals to control, monitor, and manage privileged users' access to critical systems. Get up and running with admin and user guides. How-To. Secure your software and set up integrations. Updates and Features.
What is BeyondTrust cloud?
BeyondTrust offers Cloud without Compromise Capabilities include remote control of computers and mobile devices, chat support, skills-based routing, ITSM integration, smart collaboration, embeddable chat and support components, and reporting insights.
What does BeyondTrust privilege management do?
BeyondTrust Privilege Management for Windows Servers reduces the risk of privilege misuse by assigning admin privileges to only authorized tasks that require them, controlling application and script usage, and logging and monitoring on privileged activities.
What does BeyondTrust remote support do?
BeyondTrust Remote Support Software enables support organizations to access and support nearly any remote computer or mobile device. Troubleshoot PCs and servers, provide remote assistance, train remote employees, or perform system maintenance . . . all with the highest levels of security.
Is BeyondTrust a SaaS?
Atlanta, GA – October 6, 2020 - BeyondTrust, the worldwide leader in Privileged Access Management (PAM), today announced its flagship Privileged Password Management solution is available as SaaS (software-as-a-service).
Is BeyondTrust secure?
BeyondTrust has always been designed with security at the forefront. Not only is the product architecture superior from a security standpoint, the product itself includes a number of features that strengthen the security of your organization on a day to day basis.
What is difference between CyberArk and BeyondTrust?
BeyondTrust features. In general, CyberArk is account-focused, whereas BeyondTrust is asset-focused. This difference in philosophy represents two notably different security paradigms. CyberArk's account-focused approach relies on privileged access management, account user behavior and account privileges.
How do I know if BeyondTrust privilege is working?
The easiest way to determine the client is installed and functioning is to check for the existence of the BeyondTrust Privilege Management Service in the Services Privilege Management Policy Editor. Ensure this service is both present and started.
What is BeyondTrust session monitoring?
Session monitoring records the actions of a user while they access your password-protected managed systems. The actions are recorded in real time with the ability to bypass inactivity in the session. This allows you to view only the actions of the user.
What does privileged access management do?
Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. Like all other infosec solutions, PAM works through a combination of people, processes and technology.
Is BeyondTrust the same as Bomgar?
Bomgar Is Now BeyondTrust, but Some Things Haven't Changed. New Name, Same Leading Support Software. Bomgar is still the most secure remote support software in the world. Now called BeyondTrust Remote Support, it's trusted by more customers than ever before.
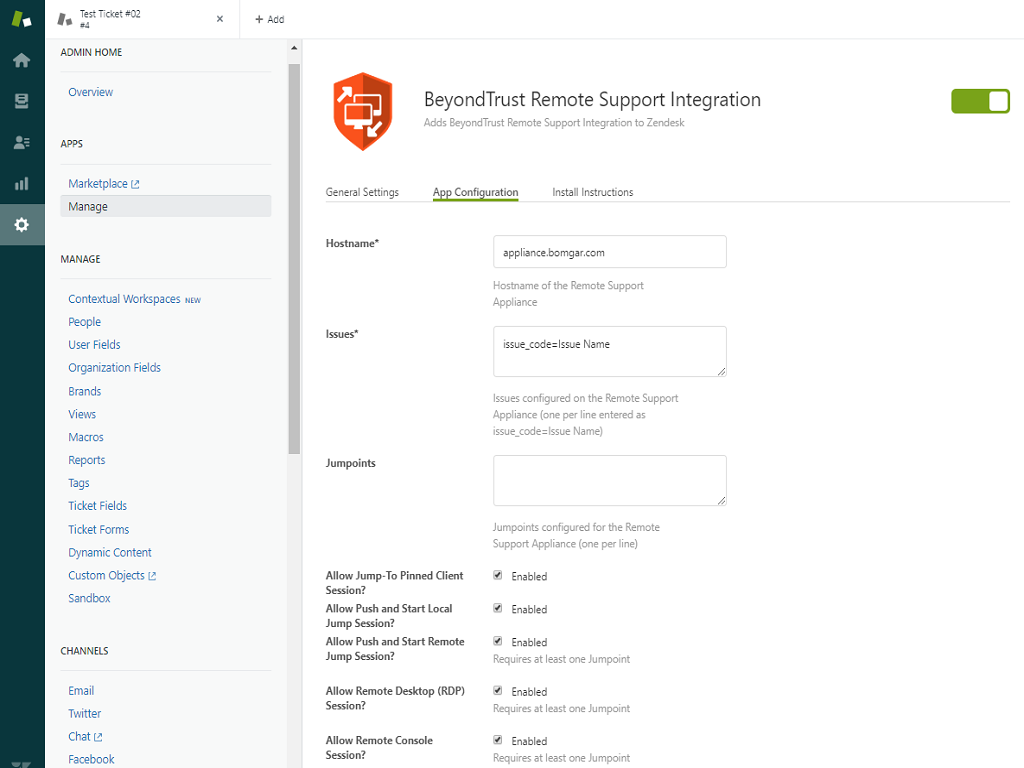
What is BeyondTrust remote support Jump client?
A Jump Client is an installable application that enables a user to access a remote computer, regardless of its location. The remote computer does not need to reside on a known network.
How much is a Bomgar license?
Bomgar Pricing Plans Bomgar offers trial/premium subscriptions with paid plans starting from $683.00/month. Bomgar doesn't offer any free plans, but a trial that allows you to try the solution before opting for a paid subscription. No credit card is necessary to try Bomgar.
How do I log into Bomgar?
By default, in Windows, you can access the console from Start Menu > All Programs > Bomgar > access.example.com, where access.example.com is the hostname of the site from which you downloaded the console. If the Login Agreement has been enabled, you must click Accept to proceed.
Upgrades, Uptime, and Downtime
- What is BeyondTrust’s Service Level Agreement (SLA) for Solution Availability?
BeyondTrust’s Availability SLA shall be ninety-nine and nine-tenths percent (99.9%) during a calendar month. For more information, please see the "Availability Service Level" section of the Cloud Service Guide. - Are Upgrades or System Changes Installed During Off-Peak Hours or in a Manner That Will Not I…
Yes, you can reference the BeyondTrustCloud Service Guide for more detailed information. When notified of an upcoming upgrade, you can reply to BeyondTrust Technical Supportto schedule the upgrade within your change window, if preferred. For more information, please see the Cloud Ser…
Vulnerability and Penetration Testing
- Does the Solution Undergo Frequent Vulnerability and Penetration Testing?
Yes, BeyondTrust performs regular, internal vulnerability scanning and penetration testing on all product solutions. Also, BeyondTrustcontracts with third-party vendors to perform periodic penetration tests on the platform to identify risks and remediation that help secure the solution. … - Can I Perform My Own Penetration Testing Against the Solution?
Yes, you must notify BeyondTrust in advance of any test by submitting a request using the BeyondTrustOnline Support Portal and completing a penetration testing agreement. This activity can be performed only once per calendar year. For more information, please see the "Penetratio…
Data and Access
- Does the Solution Support Role-Based Access for End Users and System Administrators?
Yes, this is a core component of the solution that can be configured and managed. - Who Can Access My Data?
Access to cloud services by BeyondTrust employees is protected by authentication and authorization mechanisms, and BeyondTrusthas implemented an access control authentication approach based on need to know and separation of duties. For more information, please see th…