
See more
What is BeyondTrust privileged remote access?
BeyondTrust Privileged Remote Access empowers security professionals to control, monitor, and manage privileged users' access to critical systems. Get up and running with admin and user guides. How-To. Secure your software and set up integrations. Updates and Features.
How does BeyondTrust remote support work?
BeyondTrust connects support reps with remote desktops, servers, laptops and network devices wherever they are. Support reps can see the screen, control the mouse and work as if physically in front of the remote desktop, speeding time to resolution.
What does BeyondTrust privilege management do?
BeyondTrust Privilege Management for Windows Servers reduces the risk of privilege misuse by assigning admin privileges to only authorized tasks that require them, controlling application and script usage, and logging and monitoring on privileged activities.
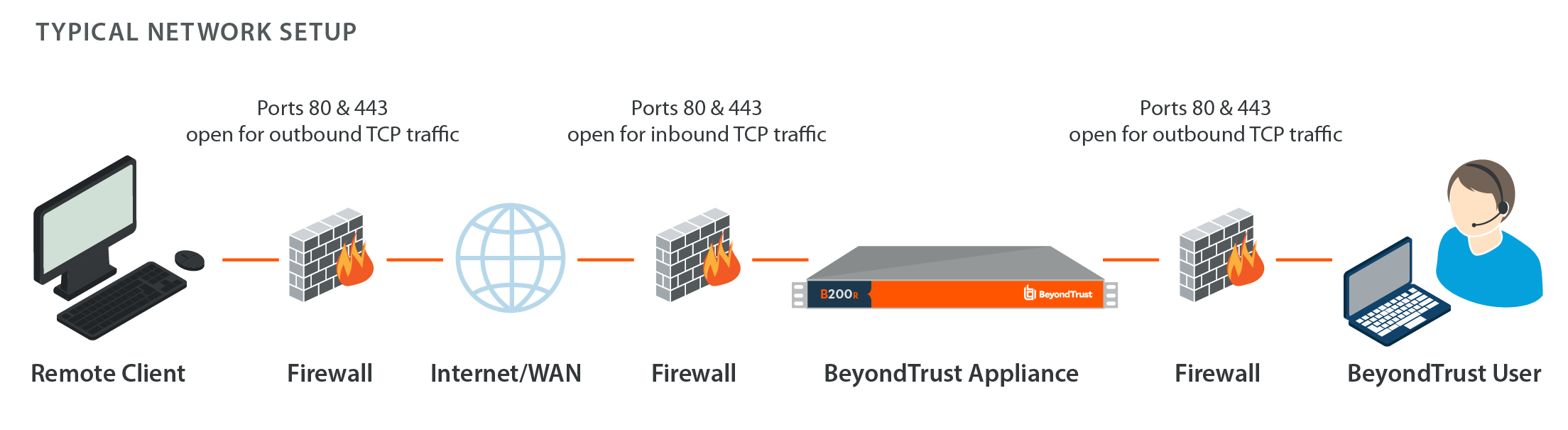
How do you use BeyondTrust?
Simply copy the URL and paste it in an email to your customer. Clicking the link will initiate a download of the BeyondTrust Custom Client. Once the user has followed the prompts to run the BeyondTrust Custom Client, his session should appear in your Personal queue on the Sessions tab.
What is BeyondTrust remote support Jump client?
A Jump Client is an installable application that enables a user to access a remote computer, regardless of its location. The remote computer does not need to reside on a known network.
What is BeyondTrust remote client?
The BeyondTrust Customer Client enables customers to interact with representatives during remote support, chat or presentation sessions. Because it is the most secure remote support solution, BeyondTrust places a top priority on user controls. Customers Can Override Remote Control.
How do I know if BeyondTrust privilege is working?
The easiest way to determine the client is installed and functioning is to check for the existence of the BeyondTrust Privilege Management Service in the Services Privilege Management Policy Editor. Ensure this service is both present and started.
What is difference between CyberArk and BeyondTrust?
BeyondTrust features. In general, CyberArk is account-focused, whereas BeyondTrust is asset-focused. This difference in philosophy represents two notably different security paradigms. CyberArk's account-focused approach relies on privileged access management, account user behavior and account privileges.
What is BeyondTrust session monitoring?
Session monitoring records the actions of a user while they access your password-protected managed systems. The actions are recorded in real time with the ability to bypass inactivity in the session. This allows you to view only the actions of the user.
What is BeyondTrust tool?
The BeyondTrust Privileged Access Management portfolio is an integrated solution that provides visibility and control over all privileged accounts and users.
How do you use a Bomgar remote?
0:442:42How Bomgar Remote Support Software Works? - YouTubeYouTubeStart of suggested clipEnd of suggested clipSee the screen control the mouse and fix the system as if you were standing directly in front of itMoreSee the screen control the mouse and fix the system as if you were standing directly in front of it you can do all this from your office or from your mobile device on the beach.
What does privileged access management do?
Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. Like all other infosec solutions, PAM works through a combination of people, processes and technology.
How do you use a Bomgar remote?
0:442:42How Bomgar Remote Support Software Works? - YouTubeYouTubeStart of suggested clipEnd of suggested clipSee the screen control the mouse and fix the system as if you were standing directly in front of itMoreSee the screen control the mouse and fix the system as if you were standing directly in front of it you can do all this from your office or from your mobile device on the beach.
What does privileged access management do?
Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. Like all other infosec solutions, PAM works through a combination of people, processes and technology.
What is BeyondTrust push service?
Give customers a push-button way to request remote support. BeyondTrust Buttons can be deployed on remote desktops or embedded in Windows applications.
How do you remote into a computer?
Access a computer remotelyOn your Android phone or tablet, open the Chrome Remote Desktop app. . ... Tap the computer you want to access from the list. If a computer is dimmed, it's offline or unavailable.You can control the computer in two different modes. To switch between modes, tap the icon in the toolbar.