What is BeyondTrust privileged access management?
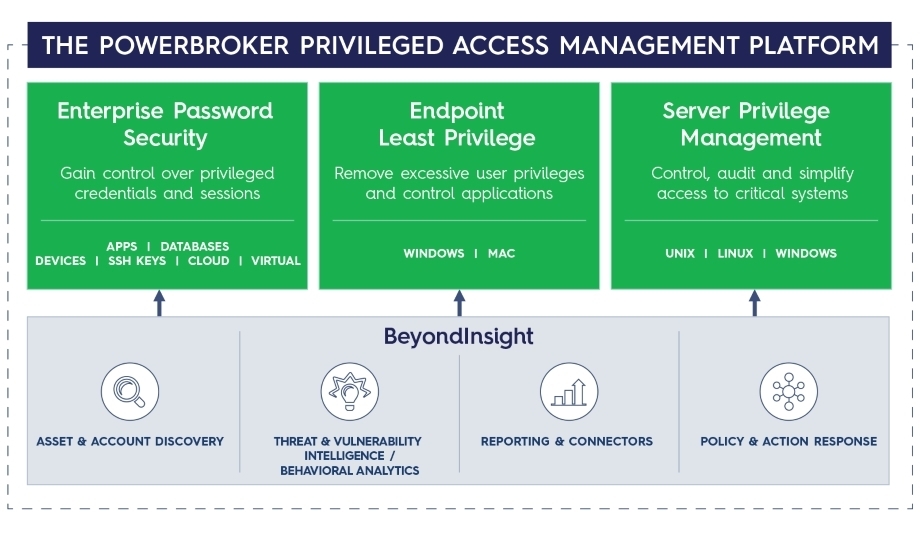
The BeyondTrust Privileged Access Management portfolio is an integrated solution that provides visibility and control over all privileged accounts and users. Our innovative Universal Privilege Management approach secures every user, asset, and session across your entire enterprise.
What is privileged remote access and how does it work?
Privileged Remote Access enables security professionals to control, monitor, and manage privileged access to critical systems. Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault.
What are the benefits of remote access?
Accessibility from any mobile device or web browser. Satisfy compliance requirements with comprehensive audit trails and session forensics. Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access.
What is universal privilege management?
Our innovative Universal Privilege Management approach secures every user, asset, and session across your entire enterprise. Our competitive pricing model scales to your organization's exact needs—nothing more for nothing less.
See more
What is BeyondTrust privileged remote access?
BeyondTrust Privileged Remote Access empowers security professionals to control, monitor, and manage privileged users' access to critical systems. Get up and running with admin and user guides. How-To. Secure your software and set up integrations. Updates and Features.
How much is a Bomgar license?
Bomgar Pricing Plans Bomgar offers trial/premium subscriptions with paid plans starting from $683.00/month. Bomgar doesn't offer any free plans, but a trial that allows you to try the solution before opting for a paid subscription. No credit card is necessary to try Bomgar.
What is BeyondTrust privilege management?
BeyondTrust Privilege Management for Windows Servers reduces the risk of privilege misuse by assigning admin privileges to only authorized tasks that require them, controlling application and script usage, and logging and monitoring on privileged activities.
Is bomgar the same as BeyondTrust?
Bomgar Is Now BeyondTrust, but Some Things Haven't Changed. New Name, Same Leading Support Software. Bomgar is still the most secure remote support software in the world. Now called BeyondTrust Remote Support, it's trusted by more customers than ever before.
How much is TeamViewer per year?
$610.80 per yearTeamViewer Pricing Plans. TeamViewer's cheapest plan costs $50.90 per month, billed annually for $610.80 per year. TeamViewer also offers two other plans, which allow more participants, devices and controls, starting at $102.90 per month and $206.90 per month.
How much is ConnectWise?
ConnectWise Control offers free trial for new users, after which the software is available across three pricing tiers on monthly and annual subscriptions as follows: One: $29 per month (billed monthly), $24 per month (billed annually) Standard: $49 per month (billed monthly), $39 per month (billed annually) Premium: ...
What is difference between CyberArk and BeyondTrust?
BeyondTrust features. In general, CyberArk is account-focused, whereas BeyondTrust is asset-focused. This difference in philosophy represents two notably different security paradigms. CyberArk's account-focused approach relies on privileged access management, account user behavior and account privileges.
What is BeyondTrust shared service?
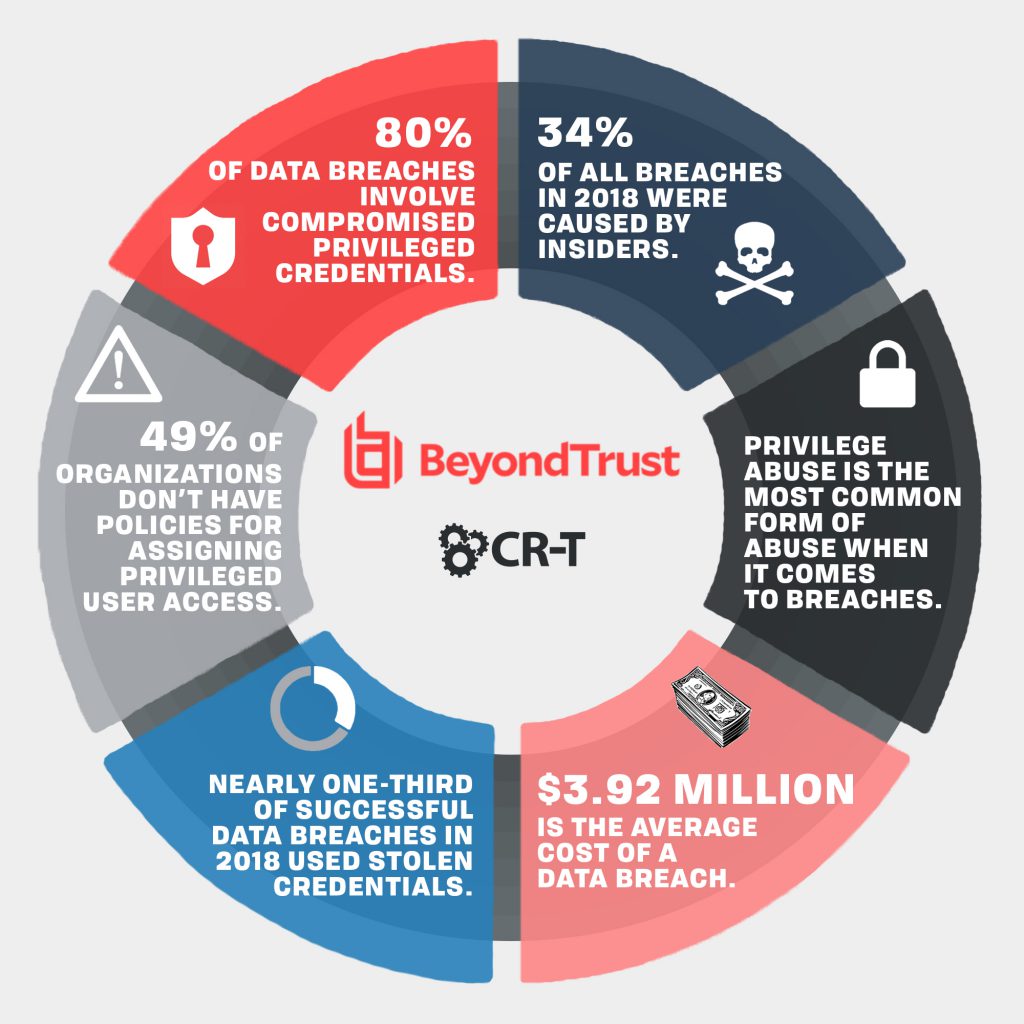
BeyondTrust is the worldwide leader in Privileged Access Management, offering the most seamless approach to preventing data breaches related to stolen credentials, misused privileges, and compromised remote access.
How do I know if BeyondTrust privilege is working?
The easiest way to determine the client is installed and functioning is to check for the existence of the BeyondTrust Privilege Management Service in the Services Privilege Management Policy Editor. Ensure this service is both present and started.
How much is BeyondTrust worth?
September 2014: Veritas Capital acquires BeyondTrust for $310 million. October 2018: Bomgar acquires BeyondTrust from Veritas.
Is BeyondTrust used to spy on employees?
Allowing employees to work from home can be risky. The risks are heightened if the employee isn't too apt when it comes to online security. With BeyondTrust, companies will be capable of monitoring the actions of their workers, thus preventing them from taking actions that could jeopardize the company's assets.
Why did Bomgar become BeyondTrust?
The combination of Bomgar and BeyondTrust will strengthen our position as a global leader in Privileged Access Management (PAM) solutions that protect organizations against today's biggest cyber security threats, while empowering them to push business forward.
What does privileged access management do?
Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. Like all other infosec solutions, PAM works through a combination of people, processes and technology.
How do I turn off privilege management in BeyondTrust?
You can enable and disable Privilege Management for Unix & Linux Servers rules from the Create PowerBroker Server Policy Rules Properties dialog box. Check the Enable box to enable the rules you want to be active. Clear the Enable box to disable a rule.
What is BeyondTrust session monitoring?
Session monitoring records the actions of a user while they access your password-protected managed systems. The actions are recorded in real time with the ability to bypass inactivity in the session. This allows you to view only the actions of the user.
What is Microsoft privileged access management?
Microsoft Purview Privileged Access Management allows granular access control over privileged admin tasks in Office 365. It can help protect your organization from breaches that use existing privileged admin accounts with standing access to sensitive data or access to critical configuration settings.
Control and Secure Privileged Remote Access for Insiders and Vendors
Give vendors, operators, and remote workers granular access to critical assets without giving them a VPN.
A Zero Trust Approach to Secure Access
A zero trust security posture reduces the threat surface and minimizes the threat windows during which attackers can inflict damage, helping to protect against everything from simple malware to advanced persistent threats.
Highlighted Features
Prevent “privilege creep” and quickly enforce least privilege to protect your IT/OT environments.
Password Safe and Privileged Remote Access
Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault, or integrated into PRA with BeyondTrust Password Safe or another password management solution.
Vendor Onboarding
The Privileged Remote Access API seamlessly integrates privileged access with existing workflows for identity, change, and event management.
The Expanding Universe of Privileges: Why Cloud PAM Matters
Privileged Remote Access centrally secures and manages access across all IT environments—cloud and hybrid included.
About BeyondTrust Privileged Remote Access
Secure, manage, and audit vendor and internal remote privileged access without a VPN. Watch demo. Give legitimate users the access they need to be productive, while keeping attackers out. Give contractors and vendors privileged access to critical assets without giving them a VPN.
Other Useful Business Software
So many networks and devices. So little time. When you’re low on resources, it can be hard keeping a watchful eye on all your clients. The more tickets that come in, the worse the headaches become. Cut through the noise with ConnectWise RMM.
BeyondTrust Privileged Remote Access Frequently Asked Questions
Q: What kinds of users and organization types does BeyondTrust Privileged Remote Access work with?
Secure Architecture
BeyondTrust offers the greatest number of deployment options, so you can select the choice that corresponds with the security requirements of your business. From on-premises and virtual appliances to SaaS, get the best deployment option for your business.
No VPN
BeyondTrust works with firewalls without VPN tunneling, keeping your perimeter security intact. Outbound only session traffic uses TCP Port 443 protecting your users and endpoints from external threats. BeyondTrust's infrastructure has very minimal port exposure, which drastically reduces the potential attack surface.
Seamless Integrations
BeyondTrust seamlessly integrates with external user directories, such as Active Directory, for simple and secure privileged user management.
Granular Access Controls and Permissions
Grant access with even more granularity so that just the right levels of access are granted to those who need it, enforcing the concept of “least privilege” in your organization. BeyondTrust enables administrators to control which specific functions a privileged insider or vendor can access.
Native Two-Factor Authentication
Two factor authentication increases the security of remote access by requiring a second factor (one-time passcode) to login, in addition to the password. It’s available for every BeyondTrust user at no additional cost, and is simple for the administrator to enable for all users.
Data Encryption
BeyondTrust enforces the use of SSL for every connection made to the site. We encrypt all data in transit using TLSv1.2, and data at rest encryption can be enabled with your organization’s key management solution. Available cipher suites can be enabled or disabled and reordered as needed to meet the needs of your organization.
Session Audit and Monitoring
Session logging allows for the review of all end system and network interactions. This log includes users involved, which endpoints they connected to, and system information. In addition to log reports, BeyondTrust also records videos of each session. These video recordings capture every action taken in each remote desktop, SSH, or Telnet session.
Powerful Privileged Access Control
Enforce a policy of least privilege by giving users just the right level of access needed for their roles. For shared accounts, easily establish individual user accountability.
Productivity Balanced Security
Privileged Remote Access increases user security without impacting daily workflows, and can deploy in just a few days. Automate processes with features like credential injection and SIEM integrations.
Consolidated Access Pathways
Administrators and IT teams can consolidate the tracking, approval, and auditing of privileged accounts in one place.
Universal Cloud & Virtualization Security
Effectively manage privileged access to business assets that leverage web-based management consoles. This includes IaaS servers, hypervisor environments, and web-based configuration interfaces for core network infrastructure.
Easy-to-Access Mobile & Web Consoles
Use mobile apps or a web-based console for privileged access anytime, anywhere. In addition to desktop consoles for Windows, Mac, and Linux, BeyondTrust Privileged Remote Access includes mobile apps and a browser console.
Simplified Audit & Compliance
Satisfy internal and external compliance requirements with comprehensive audit trails, session forensics and other reporting features. Capture detailed session data for real time or post session review.
Seamless Credential Injection
Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Store passwords in the on-appliance vault. Or, integrate with BeyondTrust Password Safe or another Password Management Solution.
