Can Bomgar be used off-campus?
Can Bomgar be used off-campus? Yes. Both the end-user and the technician can be in any location. Any network connection will work. A connection with VPN is not required. Why is my audio not working in Zoom meetings?
Was ist Bomgar remote support?
Secure Remote Support. IS&T supports BeyondTrust (formerly Bomgar) secure remote desktop access software for Windows, Mac, Linux, iOS, and Android devices. BeyondTrust allows an IT support provider to securely support end users, desktops, and their devices, with access to endpoints from anywhere in the world.
Was ist Bomgar privileged access management?
Bomgar Privileged Account Management and Vault is an agentless, proxy-based appliance that helps secure privileged account access and monitor systems accessed with those accounts.
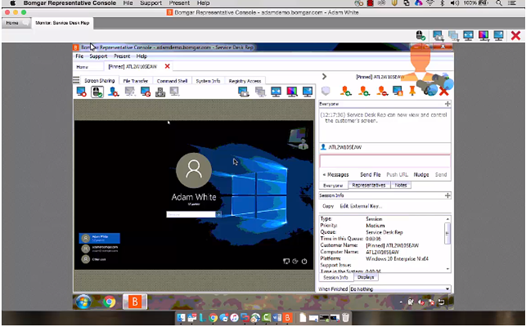
How to start a Bomgar session?
Environment
- Product Family: Software
- Product:
- Component: Bomgar
- Control System:
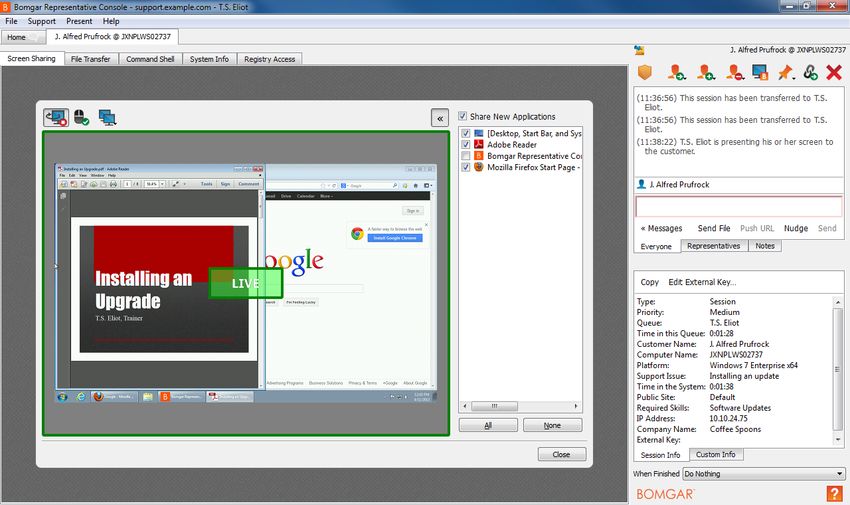
Are Bomgar sessions recorded?
Bomgar records all sessions for quality purposes and are available to administrators and supervisors for 90 days after a session is completed.
How do I transfer files to BeyondTrust?
Transfer files by using the upload and download buttons or by dragging and dropping files. Right-clicking on a file brings up a context sensitive menu from where you can, among other things, create a new directory, rename, open, or delete the file, or download it directly to your machine.
How do I turn off BeyondTrust?
Disable Authenticator App - User Side To disable two-factor authentication, go to /login > My Account > Two Factor Authentication and click Deactivate Two Factor Authentication. Enter your password and code on the app, and then click Deactivate. A message displays confirming the feature has been deactivated.
Is bomgar the same as BeyondTrust?
Bomgar Is Now BeyondTrust, but Some Things Haven't Changed. New Name, Same Leading Support Software. Bomgar is still the most secure remote support software in the world. Now called BeyondTrust Remote Support, it's trusted by more customers than ever before.
How do I transfer files over a remote?
Steps to transfer files remotelyClick the Tools tab.In the Windows Tools section, click Remote Control.Click Connect against the name of a computer to connect remotely to it.On the top of the remote-connection screen, click File Transfer.Select the required file from a folder from your computer.More items...
How do I transfer files from a local remote?
To copy the files you will need to first invoke the SCP, followed by the remote username@IP address, path to file. If you do not specify the path, it is assumed as default in this case which will be the user's home directory, this will be followed the path where the file will be stored locally.
What is Bomgar Jump client passive listening?
Bomgar's “jump” clients remain installed on unattended systems, and have traditionally been “active,” maintaining a persistent connection back to the Bomgar appliance. With Bomgar 11.1, users can now also deploy “passive” jump clients that listen for a request instead of maintaining a persistent connection.
What is BeyondTrust privileged remote access?
BeyondTrust Privileged Remote Access empowers security professionals to control, monitor, and manage privileged users' access to critical systems. Get up and running with admin and user guides. How-To. Secure your software and set up integrations. Updates and Features.
What is BeyondTrust remote support Jump client?
A Jump Client is an installable application that enables a user to access a remote computer, regardless of its location. The remote computer does not need to reside on a known network.
Why did Bomgar become BeyondTrust?
The combination of Bomgar and BeyondTrust will strengthen our position as a global leader in Privileged Access Management (PAM) solutions that protect organizations against today's biggest cyber security threats, while empowering them to push business forward.
When did Bomgar change to BeyondTrust?
20182018 was a game-changing year for the Privileged Access Management market. Lieberman, Avecto and BeyondTrust were all acquired by Bomgar and, in 2019, we will launch the new BeyondTrust.
Who uses Bomgar?
Who uses Bomgar?CompanyFederal Emergency Management AgencyRevenue100M-200MCompany Size500-1000CompanyLorven TechnologiesWebsitelorventech.com25 more rows
How do I use BeyondTrust?
Simply copy the URL and paste it in an email to your customer. Clicking the link will initiate a download of the BeyondTrust Custom Client. Once the user has followed the prompts to run the BeyondTrust Custom Client, his session should appear in your Personal queue on the Sessions tab.
What is the process of transferring files from a computer on the Internet to your computer is called?
The process of transferring files from a computer on the Internet to your computer is called FTP. Uploading is the transmission of a file from one computer system to another, usually larger computer system. ... From an Internet user's point-of-view, downloading is receiving a file from another computer.
What is a Bomgar?
Bomgar lets you apply granular access controls. You can require notification and authorization for privileged access, so that privileged users always have approval before connecting. Define what endpoints users can access, schedule when they can access them, and limit their access to certain applications.
Why is collaboration important?
Collaboration makes your users more efficient and productive. Privileged users can experience desktop-quality access from an iPad, iPhone, or Android device! You can even monitor user activity from your iPad. And you don’t have to re-architect your network to deploy Bomgar.
Can you deploy Bomgar without an endpoint agent?
And you don’t have to re-architect your network to deploy Bomgar. Bomgar enables remote access without VPN tunneling, port-forwarding, or firewall configuration changes. You can deploy Bomgar with or without an endpoint agent.
Can privileged accounts share passwords?
Unfortunately, users with access to privileged accounts often share passwords for remote access tools, use remote tools with known vulnerabilities, or compromise firewall settings to enable remote connections. As recent breaches have shown, each of these practices makes your network more vulnerable to a cyber-attack.
Who accesses critical systems on your network?
Every day, Data Center Operations teams, IT administrators, business users, and remote vendors access critical systems on your network .
What is a Bomgar remote support?
Bomgar Remote Support 18.2 introduces the new Bomgar Vault for Remote Support.
What is Bomgar 18.2?
Bomgar Remote Support 18.2 introduces the redesigned Bomgar Vault for Remote Support, an integrated credential store that protects privileged credentials and identities used by the service desk.
What happens if credentials are stolen?
If credentials are stolen or compromised, cybercriminals can move laterally across your network, expanding the damage beyond the initial breach. Bomgar’s solutions are designed with security in mind, to help organizations safeguard their most critical systems, accounts and credentials to protect their IT networks from today’s threats.”. ...
Where is Bomgar located?
Bomgar is privately held with offices in Atlanta, Austin, Jackson, Los Angeles, Washington D.C., Frankfurt, London, Paris, and Singapore. Connect with Bomgar at www.bomgar.com, the Bomgar Blog, or on Facebook , Twitter and LinkedIn .
What is customizable issue submission field?
Customizable Issue Submission Fields – Define which fields are shown when using issue submission to start a support session, and only capture the necessary information relevant for your organization.
Does Bomgar vault help with productivity?
Administrators can now eliminate the need for technicians to memorize or manually track passwords. Additionally, Bomgar Vault improves productivity as users can inject privileged credentials directly into an endpoint with just one click – without ever knowing or seeing the credentials.
How to download Bomgar?
Click the link shared by the support represenatative via email and download the Bomgar.exe file. Alternatively you can also go to the Adobe Remote Support portal page ( https://screen.share.adobe.com/ ). In the "Session Key" box, enter the session key (seven digit number) provided by the Adobe Customer Support representative, and click the "Submit" button.
What is remote support?
The remote support tool is used by Adobe Customer Support representatives while assisting customers who contact us using Adobe chat or phone support channel.
What is a bomgar?
Bomgar is a remote support solution that allows support technicians to remotely connect to a customer's computer. Using the Bomgar Representative Console, technology support professionals can access and control systems and devices remotely on various platforms. This connection is encrypted to protect your data.
How to view downloaded apps on Mac?
Run the downloaded setup file or Press Ctrl+J to view downloads. If you are unable to locate the downloads folder on your Mac you can refer to this link https://support.apple.com/en-in/guide/safari/sfri40598/mac
What is Bomgar Connect 16.2?
Bomgar has also released Bomgar Connect 16.2, which includes many of the new Remote support features such as Web Rep Console and the new Android Rep Console and customer apps. Bomgar Connect enables organizations with essential remote support needs to quickly connect to and support end users, customers and systems in any location. Offered via Bomgar’s secure Software as a Service (SaaS) platform, Bomgar Connect is extremely easy to buy, download, and use.
What is Bomgar Remote Support 16.2?
Bomgar Remote Support 16.2 offers numerous options for support reps to provide timely and superior support to customers and users. Bomgar’s new Web Rep Console is the first to bring the core remote support features to HTML5 browsers. With no download or plugins required, support reps can provide support from any computer. The latest version also introduces enhancements to the Bomgar InSight mobile camera sharing feature. With new zoom, flashlight, and auto focus capabilities, InSight makes it even easier to support hardware and peripherals that are beyond the screen. Also included are a new Android Rep Console and Customer Mobile Apps that offer a fresh user interface for a better support experience.
What is Bomgar 16.2?
Atlanta, GA – December 6, 2016 – Bomgar, a leader in secure access solutions, today released Bomgar Remote Support 16.2, the latest version of its enterprise-leading remote support software. Bomgar Remote Support enables IT service desks and customer support centers to access and fix nearly any remote device, running any platform, located anywhere in the world. Technicians using Bomgar can quickly connect to, view, and control remote systems and devices, chat and collaborate with end-users or other technicians, all while improving remote access security.
What is enhanced jump client maintenance?
Enhanced Jump Client Maintenance – New settings allow administrators to configure whether or not to show uninstalled Jump Clients making the need to “jump” to remote systems/devices easier and cleaner.
What is improved API authentication?
Improved API Authentication – Removes the need to specify a user name/password with every API call and further controls the permissions associated with API accounts.
Can you use SAML credentials on mobile?
SAML for Mobile – Support reps can now use SAML credentials to login to Mobile Rep Console apps, creating a consistent login process.
How to log into Bomgar?
To log in using the Bomgar Console select SAML Credentials from the "Authenticate Using" dropdown. Click Login and a browser will open that redirects to the Duo Access Gateway login page. Enter your primary directory logon information, approve Duo two-factor authentication. After you've successfully authenticated a special Bomgar file will be downloaded. Click on the Bomgar file and it will log you into the Bomgar Console.
How to use SAML authentication on Bomgar?
Navigate to your Bomgar login page eg. https://support.yourcompany.com/login and click the Use SAML Authentication link. This redirects to the Duo Access Gateway login page. Enter your primary directory logon information, approve Duo two-factor authentication, and get redirected back to the Bomgar site after authenticating.
What is the second step in Bomgar SSO?
Once your AD FS services are up and running, the second step is to configure the SSO partnership between your AD FS service and the external cloud resource , in this case Bomgar. Learn more about configuring Bomgar SSO with AD FS at the Bomgar Support site.
How to add a Bomgar SAML file to Duo?
Click the Choose File button in the "Add Application" section of the page and locate the Bomgar SAML application JSON file you downloaded from the Duo Admin Panel earlier. Click the Upload button after selecting the JSON configuration file.
What attribute does Bomgar use?
Bomgar uses the Mail attribute, First Name attribute, and Last Name attribute when authenticating. We've mapped Mail attribute, First Name attribute, and Last Name attribute to DAG supported authentication source attributes as follows:
How to protect application in Bomgar?
Click Protect an Application and locate the entry for Bomgar with a protection type of "2FA with SSO self-hosted (Duo Access Gateway)" in the applications list. Click Protect to the far-right to start configuring Bomgar. See Protecting Applications for more information about protecting applications in Duo and additional application options.
How to get a DAG file?
This is the information you need to provide to Bomgar when configuring SSO. Click the Download XML metadata link to obtain the DAG metadata file (the downloaded file is named "dag.xml").
Why are passwords and accounts prime targets in cyberattacks?
Privileged accounts and passwords are prime targets in cyberattacks because they allow hackers to utilize legitimate credentials with elevated permissions to access other areas of the network. If credentials are stolen or compromised, cybercriminals can move laterally across your network, expanding the damage beyond the initial breach.
Does Bomgar Vault have a discovery feature?
Additionally, Bomgar Vault improves productivity as users can inject privileged credentials directly into an endpoint with just one click – without ever knowing or seeing the credentials. The new Bomgar Vault also includes a discovery feature to automatically find and protect AD and local administrator credentials.
What is customizable issue submission field?
Customizable Issue Submission Fields – Define which fields are shown when using issue submission to start a support session, and only capture the necessary information relevant for your organization.
Who needs privileged access to support users and sensitive systems?
An organization’s insiders, such as IT administrators and service desk technicians, need privileged access to support users and sensitive systems. However, such access is often granted in uncontrollable and untraceable ways making the organization more vulnerable to attacks
What is privileged remote access?
Privileged Remote Access gives you the ability to centrally secure and manage access across all of your environments, even sensitive systems in the Cloud.
What is advanced web access?
Advanced Web Access can be configured to work across any solution that leverages a web interface for management including; Amazon Web Services, Google Cloud, VMware vSphere, Citrix XenServer, Microsoft Hyper-V, Microsoft Azure, IBM Softlayer, and Rackspace.
What is zero trust security?
A zero trust security posture reduces the threat surface and minimizes the threat windows during which attackers can inflict damage, helping to protect against everything from simple malware to advanced persistent threats.
Can you store credentials in endpoint?
Instead of requiring privileged users to know usernames and passwords for each endpoint, we can store those credentials securely. With Credential Injection, those credentials are retrieved and injected directly into a session.
