Can Bomgar be used off-campus?
Bomgar is a remote support tool that allows Information Technology Services (ITS) to provide remote assistance to our customers both on and off campus. ITS can control Windows, Mac, and Linux desktops anywhere there is a network connection, but only with the customer's permission. Departments outside ITS have also purchased licenses in order to securely provide remote assistance to their customers.
Was ist Bomgar remote support?
- Dual processors
- Dual power supplies
- RAID 6 – Six solid state drives, supports the loss of up to two drives without losing data
- Drive failure notification
- Failover capable
Was ist Bomgar privileged access management?
• Bomgar is a leading provider of next-level identity and access management solutions that proactively defend against privileged access vulnerabilities. The company provides automated technology that discover, manage, and protect privileged accounts and access pathways at the speed and scale required by large enterprises.
Is Bomgar client support a safe app to install?
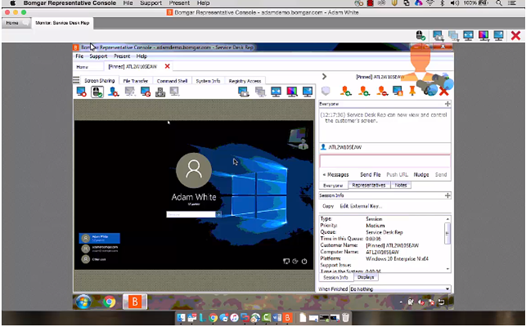
Support reps can securely chat, co-browse a web site or app on the end user's mobile device, view screen shots that the end user captures, and even push status updates to mobile employees and end users right from the BeyondTrust Rep Console.
See more

What is Bomgar remote access?
BeyondTrust Remote Support (formerly Bomgar) enables you to remotely access and fix nearly any device, running any platform, located anywhere in the world.
Is bomgar secure?
Bomgar is still the most secure remote support software in the world, only now it's called BeyondTrust Remote Support. Remote Support enables help desk teams to quickly and securely access and fix any remote device anywhere, on any platform, with a single solution.
How does bomgar work?
0:442:42How Bomgar Remote Support Software Works? - YouTubeYouTubeStart of suggested clipEnd of suggested clipYou can start saying yes the Bomgar remote support solution enables you to remotely access and fixMoreYou can start saying yes the Bomgar remote support solution enables you to remotely access and fix nearly any device running any platform located anywhere in the world. Access.
What is secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
Who uses Bomgar?
Who uses Bomgar?CompanyFederal Emergency Management AgencyRevenue100M-200MCompany Size500-1000CompanyLorven TechnologiesWebsitelorventech.com25 more rows
What does bomgar stand for?
0:172:18What is BOMGAR? What does BOMGAR mean ... - YouTubeYouTubeStart of suggested clipEnd of suggested clipBonger is a remote support solution that allows support technicians to remotely connect to end-user.MoreBonger is a remote support solution that allows support technicians to remotely connect to end-user. Systems through firewalls from their computer or mobile.
Does Bomgar work on phones?
Bomgar is a single, centralized solution that allows you to support all of your systems, including Windows, Mac, Linux, iOS, Android, and more. Plus, it allows you to conduct multiple sessions simultaneously and collaborate with other reps within sessions, allowing you to be more productive and resolve issues faster.”
Is bomgar RDP?
This competitive document details the key advantages Bomgar provides over Windows' built-in remote access tools, including the ability to run RDP sessions securely through the Bomgar Box.
How do I log into Bomgar?
By default, in Windows, you can access the console from Start Menu > All Programs > Bomgar > access.example.com, where access.example.com is the hostname of the site from which you downloaded the console. If the Login Agreement has been enabled, you must click Accept to proceed.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Should I give remote access to my computer?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
How do you secure remote access to employees?
Require employees and vendors to use secure connections when connecting remotely to your network. They should: Use a router with WPA2 or WPA3 encryption when connecting from their homes. Encryption protects information sent over a network so that outsiders can't read it.
Who owns Bomgar Corporation?
Francisco PartnersIn April 2018, Francisco Partners announced that it acquired Bomgar from Thoma Bravo, which owned Bomgar since June 2016.
What protocol does bomgar use?
From the Bomgar Support Documentation: Ports 80, 443, and 8200 need to be open for outbound TCP traffic on the customer's and representative's firewalls.
Does Bomgar use RDP?
This competitive document details the key advantages Bomgar provides over Windows' built-in remote access tools, including the ability to run RDP sessions securely through the Bomgar Box.
How do I get rid of Bomgar SCC EXE?
Uninstalling this variant: If problems with Bomgar Jump Client 13.1. 2 [s or Bomgar Jump Client 17.1. 3 [r occur, you can uninstall the associated program (Start > Control Panel > Uninstall a Program) or contact www.bomgar.com Customer Service. Important: Some malware camouflages itself as bomgar-scc.exe.
What is Bomgar Remote Access?
Bomgar Remote Access is part of the lucky ones in having a partnership with this big fish. This collaboration allows technicians and users to solve problems remotely at OS level.
Why is Bomgar important?
Bomgar ensures a secure channel for remote access from where you can fully use your files and systems. This is a particularly useful advantage to save valuable time when giving or receiving technical assistance.
Can you share tools between remote PC and local device?
This is particularly necessary during chats and web conferences, or even to keep a log of events.
Secure Remote Access for Employees and Vendors
Traditional remote access methods, such as RDP, Virtual Private Networks, and legacy remote desktop tools lack granular access management controls. These processes enable easy exploits via stolen credentials and session hijacking. Extending remote access to your vendors makes matters even worse.
Privileged Remote Access: Use Cases
BeyondTrust Privileged Remote Access controls, manages, and audits remote privileged access to critical IT systems by authorized employees and third-party vendors. No VPN required.
Remote Support: Use Cases
BeyondTrust Remote Support allows help desk teams to securely access and fix any remote device on any platform, located anywhere in the world. All with the same solution.
Secure Remote Access and Remote Support Features
BeyondTrust Remote Support and Privileged Remote Access solutions work hand-in-hand to secure remote access points within the enterprise, including employees, vendors, third-parties, and more.
What is remote support?
Remote support software that extends to all of your systems over the web, even if they are behind firewalls you don’t control. All supported platforms are included in the core product, so you can consolidate and standardize support, improving incident handling time and support rep productivity.
Why is remote access important for support teams?
The security of their remote access tools is crucial in protecting your network from threats and meeting compliance regulations.
What is granular control?
Granular control over role and permissions settings and session policies, ensuring users have the right amount of access per their role.
System Security
All remote access sessions are encrypted and logged, including actual recording of each session for a complete and detailed audit trail. Role-based access to specific systems with control over access timeframes, required approvals, and permitted features to maintain control of access.
Bomgar Cloud Data Centers
Bomgar data centers have advanced networking capabilities and provide the following features:
What is privileged remote access?
Privileged Remote Access gives you the ability to centrally secure and manage access across all of your environments, even sensitive systems in the Cloud.
What is advanced web access?
Advanced Web Access can be configured to work across any solution that leverages a web interface for management including; Amazon Web Services, Google Cloud, VMware vSphere, Citrix XenServer, Microsoft Hyper-V, Microsoft Azure, IBM Softlayer, and Rackspace.
What is zero trust security?
A zero trust security posture reduces the threat surface and minimizes the threat windows during which attackers can inflict damage, helping to protect against everything from simple malware to advanced persistent threats.
Why is it important to compare Bomgar and RDP?
That is why a comparison like Bomgar Vs RDP is necessary to determine which tool is best for you in the security arena.
Does Bomgar work on Windows?
It is also the only one of the two that works on different platforms: Windows, Mac, Chromebook, Linux, Network Devices and POS Systems. While RDP only has support on Windows, Network Devices and POS Systems. RDP also does not offer the features needed to support a mobile user base. Bomgar, on the other hand, does support the mobile operating systems: iOS and Android.
Is Bomgar a good remote access solution?
However, for it to work properly and not expose the company to cyberattacks, it is essential to know how to choose the best tool. Bomgar and RDP (Remote Desktop Protocol) are two widely used solutions. Both have similarities, but they are not equally complete or functional.
Is Bomgar Vault secure?
After knowing the characteristics of each solution, Bomgar Vault is presented as the most complete and secure solution for organizations that want to have remote access. This tool, in addition to data encryption, offers a virtual security vault where it is possible to store and protect data and accesses without having to mediate VPN. You also don’t have to change firewall settings.