What is a remote access trojan and how does it work?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response. How Does a Remote Access Trojan Work? RATS can infect computers like any other type of malware.
What is rat Trojan and how does it work?
It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim. RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload.
Who is brute of Troy?
Not to be confused with Brutus Greenshield. Brutus, or Brute of Troy, is a legendary descendant of the Trojan hero Aeneas, known in medieval British history as the eponymous founder and first king of Britain.

What can Remote Access Trojan do?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What is the best Remote Access Trojan?
What is Remote Access and Administration?...10 Best Remote Access Software (Remote Control Software) In 2022Comparison of Top Remote Access Tools.#1) NinjaOne (Formerly NinjaRMM)#2) SolarWinds Dameware Remote Support.#3) Atera.#4) Supremo.#5) ManageEngine Remote Access Plus.#6) RemotePC.#7) TeamViewer.More items...•
Can remote access Trojans be detected?
As you might imagine, this can lead to sticky situations. A Remote Access Trojan paired with a keylogger, for instance, can easily acquire login information for bank and credit card accounts.
How is Remote Access Trojan delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
What is smart RAT switch?
RAT infected Android devices can be remotely zombified by the perpetrator, allowing virtually unlimited access to photos, data and messages on the device. The Dendroid RAT provides full access to infected devices' camera and microphone, and can place calls or listen in on a user's phone conversations or text messages.
Can MalwareBytes remove RATs?
SolarWinds Security Event Manager (FREE TRIAL) provides advanced threat protection against some of the most persistent RATs on the web. SEM can even take automated action to clean and remove any RATs found on infected computers. MalwareBytes Anti-Malware can remove most of some of the most common threats found online.
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Can an Iphone get a Remote Access Trojan?
The only way to get a Remote Access Trojan on an iOS device would be to jailbreak it to remove the inherent iOS limitations of file system and app sandboxes and to open restricted ports (that are blocked by iOS itself by default).
What is a Remote Access Trojan which is installed by SMS spoofing used for?
Malware may also be used to install a backdoor to a system by taking advantage of some vulnerability in the software. For example, Remote Access Trojans are used to create such backdoors, allowing the attacker access to your system from a remote location.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
What was the first remote access Trojan?
The oldest RAT was first developed in 1996 [10], however legitimate remote access tools were first created in 1989 [11]. Since then, the number of RATs has grown rapidly. The first phase was marked by home-made RATs. In these years, everyone made their own RAT, however these did not prosper and were not heavily used.
What can computer worms do?
Worms can modify and delete files, and they can even inject additional malicious software onto a computer. Sometimes a computer worm's purpose is only to make copies of itself over and over — depleting system resources, such as hard drive space or bandwidth, by overloading a shared network.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
What are the variant of remote access Trojan?
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Is Remcos a virus?
Remcos or Remote Control and Surveillance, marketed as a legitimate software by a Germany-based firm Breaking Security for remotely managing Windows systems is now widely used in multiple malicious campaigns by threat actors....Anti Spam.Pattern Branch/VersionRelease DateAS Pattern 5300March 18, 2020
Can Remotepc be hacked?
Remote Desktop Protocol (RDP) has been known since 2016 as a way to attack some computers and networks. Malicious cyber actors, hackers, have developed methods of identifying and exploiting vulnerable RDP sessions via the Internet to steal identities, login credentials and install and launch ransomeware attacks.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
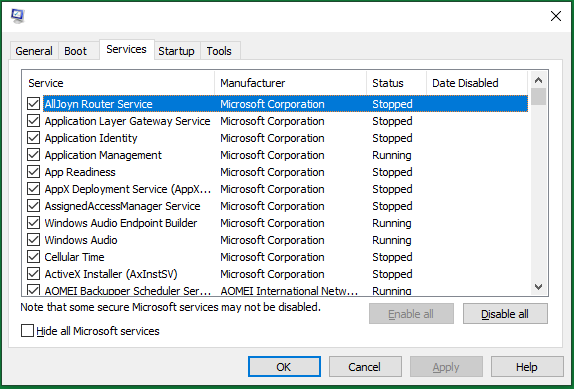
Can malware writers name processes?
For most applications and processes, you can identify any suspicious content in this window, but malware writers name processes to make them look official. If you find any suspicious executables and processes, search online to determine if the process could be a RAT or other type of malware.
How do remote access Trojans work?
The Remote Access Trojans get themselves downloaded on a device if the victims click on any attachment in an email or from a game. It enables the attacker to get control over the device and monitor the activities or gaining remote access. This RAT makes itself undetected on the device, and they remain in the device for a longer period of time for getting data that may be confidential.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.
How Does a Remote Access Trojan Work?
RATS can infect computers like any other type of malware. They might be attached to an email, be hosted on a malicious website, or exploit a vulnerability in an unpatched machine.
The Threat of the RAT
Different attacks require different levels of access to a target system, and the amount of access that an attacker gains determines what they can accomplish during a cyberattack.
How to Protect Against a Remote Access Trojan
RATs are designed to hide themselves on infected machines, providing secret access to an attacker. They often accomplish this by piggybacking malicious functionality on a seemingly legitimate application. For example, a pirated video game or business application may be available for free because it has been modified to include malware.
Prevent RAT Infections with Check Point
Protecting against RAT infections requires solutions that can identify and block malware before it gains access to an organization’s systems.
What is remote access trojan?
Remote Access Trojans are programs that provide the capability to allow covert surveillance or the ability to gain unauthorized access to a victim PC. Remote Access Trojans often mimic similar behaviors of keylogger applications by allowing the automated collection of keystrokes, usernames, passwords, screenshots, browser history, emails, chat lots, etc. Remote Access Trojans differ from keyloggers in that they provide the capability for an attacker to gain unauthorized remote access to the victim machine via specially configured communication protocols which are set up upon initial infection of the victim computer. This backdoor into the victim machine can allow an attacker unfettered access, including the ability to monitor user behavior, change computer settings, browse and copy files, utilize the bandwidth (Internet connection) for possible criminal activity, access connected systems, and more.
How can remote access Trojans be installed?
Specially crafted email attachments, web-links, download packages, or .torrent files could be used as a mechanism for installation of the software. Targeted attacks by a motivated attacker may deceive desired targets into installing such software via social engineering tactics, or even via temporary physical access of the desired computer.
What is botnet in computer?
Botnets are networks of computers infected by a botnet agent that are under hidden control of a third party. They are used to execute various commands ordered by the attacker. Most common uses of botnets are criminal operations that require distributed resources, such as DDoS attacks on selected targets, spam campaigns, and performing click fraud. Often, the botnet agent is ordered to download and install additional payloads or to steal data from the local computer.
What is browser hijacker?
Browser hijackers, or simply hijackers, are a type of malware created for the purpose of modifying Internet browser settings without the user’s knowledge or consent. Typically, hijackers change the homepage and default search settings. However, some are known to inject advertisements—thus, they are qualified to be called adware, automatically redirecting users to potentially malicious destinations when they visit certain sites, and sometimes making drastic changes to the affected system. Some hijackers also contain keyloggers, which are capable of recording user keystrokes to gather potentially valuable information they enter into websites, such as account credentials.
How do botnets communicate?
From the moment of infection, botnet agents keep in touch with their remote Command-and-Control server (C&C). The communication can be carried by various means, and cybercriminals keep on inventing in new methods to hide their data transmission channels. There have been some unusual ways via social media like Twitter or reddit to send commands. However, the most common implementation of the C&C is a web-application, contacted by the client via simple HTTP requests.
What is a rogue scanner?
Rogue scanners, also known as fake scanners, fake AV, or rogueware, are pieces of code injected into legitimate sites or housed in fake sites. Their social engineering tactic normally involve displaying fictitious security scan results, threat notices, and other deceptive tactics in an effort to manipulate users into purchasing fake security software or licenses in order to remove potential threats that have supposedly infected their systems. Their warnings were deliberately crafted to closely resemble interfaces of legitimate AV or anti-malware software, further increasing the likelihood that users who see them will fall for the ploy. These malware can target and affect PCs and Mac systems alike. In 2011, known names in the security industry have noted the dramatic decline of rogue scanners, both in detection of new variants and search engine results for their solutions.
What are the different types of POS malware?
POS malware may come in three types: keyloggers, memory dumpers, and network sniffers.
What Is The Best Trojan Remote Access?
Hackers commonly use Blackshades to gain remote access to computers. Windows-based operating systems are frequently targeted by this tool. The Trojan has infected 500,000 systems worldwide until now.
Where Are Remote Access Trojans Used?
Malware developers use Remote Access Trojan (RAT) tools to gain full access and control over a user’s computer, including mouse and keyboard control, file access, and network resources.
What Can You Do With A Remote Access Tool?
The remote access programs and tools (sometimes called RATs) allow remote access and manipulation of systems from another location. All types of users can use remote access programs to access files and data on remote computers, and many of them are legitimate tools.
What Is Trojan Ddos?
An infected computer is used to launch a DoS attack from a pre-defined address using this type of malicious program. The malicious user infects a number of computers with this type of Trojan in advance (for example, as part of a mass spam mailing) in order to conduct a successful DoS attack.
What Is The Purpose Of A Trojan Horse?
In general, a Trojan is designed to damage, disrupt, steal, or in general cause some other harm to your data or network.
What is the title of the book Brut y Tywysogion?
Brut y Tywysogion ("Chronicle of the Princes "), a major chronicle for the Welsh rulers from the 7th century to loss of independence, is a purely historical work containing no legendary material but the title reflects the influence of Geoffrey's work and, in one sense, can be seen as a "sequel" to it.
Who is the brutus of Troy?
Brutus of Troy. Not to be confused with Brutus Greenshield. Brutus, or Brute of Troy, is a legendary descendant of the Trojan hero Aeneas, known in medieval British history as the eponymous founder and first king of Britain.
What is the name of the city that Brutus found?
Corineus throws him over a cliff to his death. Brutus then founds a city on the banks of the River Thames, which he calls Troia Nova, or New Troy. The name is in time corrupted to Trinovantum, and the city is later called London. He creates laws for his people and rules for twenty-four years.
Where did brutus land in Troy?
Brutus is an important character in the book series The Troy Game by Sara Douglass . Geoffrey's Historia says that Brutus and his followers landed at Totnes in Devon. A stone on Fore Street in Totnes, known as the "Brutus Stone", commemorates this.
Where did the Trojans land?
The Trojans land on a deserted island and discover an abandoned temple to Diana. After performing the appropriate ritual, Brutus falls asleep in front of the goddess's statue and is given a vision of the land where he is destined to settle, an island in the western ocean inhabited only by a few giants.
Who was the warrior that led the Trojans?
After some adventures in north Africa and a close encounter with the Sirens, Brutus discovers another group of exiled Trojans living on the shores of the Tyrrhenian Sea, led by the prodigious warrior Corineus. In Gaul, Corineus provokes a war with Goffarius Pictus, king of Aquitaine, after hunting in the king's forests without permission.
Who were the brothers of Brutus?
This Brutus's brothers were Francus, Alamanus and Romanus, also ancestors of significant European nations.