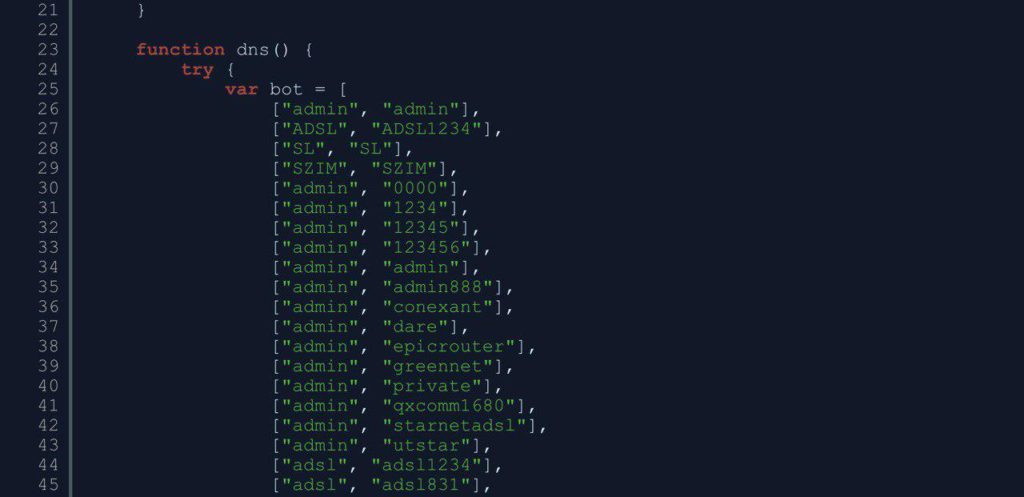
Remote access to the victim’s computer is gained by using brute-force techniques which can effectively crack weak passwords. Typically, the attacker scans a list of IP ranges for RDP port 3389 (default RDP port) which are open for connection. Once an attacker finds a port, they launch the brute-force attack.
Full Answer
Are brute-force attack attempts blocked by ESET brute force attack protection?
BRATISLAVA – ESET researchers, based on telemetry, confirm a significant uptick in the number of unique clients who have reported brute-force attack attempts blocked via ESET’s Network Attack Protection and its new layer, ESET Brute-Force Attack Protection. The trend has been observed since the onset of the global pandemic.
What is a brute-force attack?
The search can be based on combinations of random characters or a dictionary of popular or compromised passwords. A successful attack gives the cybercriminal remote access to the target computer in the network. Brute-force attackers are not surgical in their approach, but operate by area.
How do I protect RDP from brute force attacks?
Use a VPN. RDP can be protected from brute force attacks by forcing users connect to it over a Virtual Private Network (VPN). This hides RDP from the Internet but exposes the VPN, leaving it vulnerable to attack, so it also needs to be properly secured.
How many brute force attempts on Windows servers?
As you can see, the number is growing daily. That's exponentially more than the hundreds (some times low thousands) brute force attempts we see via SSH logs from vanilla Linux servers. This lead us to believe that Windows servers are more desirable targets than their Linux counterparts.
What is RDP brute force attack?
Hackers figure out RDP passwords using a technique called “brute force guessing,” which is as basic as it sounds. They simply use a computer program that will try a password and see if it works.
Is it possible to brute force SSH?
One of the most reliable methods to gain SSH access is by brute-forcing credentials. There are various methods to perform a brute force ssh attack that ultimately discover valid login credentials.
What is an example of brute force attack?
A simple brute force attack uses automation and scripts to guess passwords. Typical brute force attacks make a few hundred guesses every second. Simple passwords, such as those lacking a mix of upper- and lowercase letters and those using common expressions like '123456' or 'password,' can be cracked in minutes.
Can ransomware spread through RDP?
Once the user's offsite computer connects to the infected onsite server, the attacker gains access to the offsite computer by traversing the RDP connection. With access granted, the ransomware attack commences.
Do hackers use SSH?
Hackers use SSH to control connected devices for brute-force attacks.
What is arguably the most common tool for brute-forcing SSH?
SSB. Secure Shell Bruteforcer (SSB) is one of the fastest and simplest tools for brute-force SSH servers. Using the secure shell of SSB gives you an appropriate interface, unlike the other tools that crack the password of an SSH server.
How do hackers brute force?
The hacker tries multiple usernames and passwords, often using a computer to test a wide range of combinations, until they find the correct login information. The name "brute force" comes from attackers using excessively forceful attempts to gain access to user accounts.
How is brute force attack achieved?
One of the least advanced but most successful techniques used by hackers to break into a network, a brute force attack is achieved by employing a trial-and-error method of entering different username and password combinations with an automated tool or bot until access is granted.
How easy is it to brute force a password?
If a password is only four or five characters (whether they are just numbers or a combination of numbers, letters and symbols), there's a very high chance that it will be hacked instantly. However, if a password is only numbers and up to 18 characters, it could take a hacker up to nine months to crack the code.
Why do hackers use RDP?
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
Is RDP secure without VPN?
No, but they serve a similar function. A VPN lets you access a secure network. RDP lets you remotely access a specific computer. Both will (usually) encrypt your traffic in one way or another, and both will grant you private access to a server or device that might be thousands of miles away.
Can ransomware spread through VPN?
Many believe a Virtual Private Network (VPN) significantly protects against ransomware attacks. Not only is this myth incorrect, but your VPN is actually a potential attack vector for malicious actors.
What is SSH Patator?
Patator is a multi-purpose brute-forcer, with a modular design and a flexible usage. Currently it supports the following modules: ftp_login : Brute-force FTP. ssh_login : Brute-force SSH.
What can Hydra brute force?
Hydra is one of the favorite tools in a hacker's toolkit. It is an excellent tool for performing brute force attacks and can be used from a red team perspective to break into systems as well as from a blue team perspective to audit and test ssh passwords against common password lists like rockyou.
How do I find my SSH password?
Recovering your SSH key passphraseIn Finder, search for the Keychain Access app.In Keychain Access, search for SSH.Double click on the entry for your SSH key to open a new dialog box.In the lower-left corner, select Show password.You'll be prompted for your administrative password. ... Your password will be revealed.
How do I use SSH Hostkey?
Using SSH Client KeysCreate an SSH client key pair by selecting Keys > SSH Client Keys > Create Key Pair from the top menu bar.Export the public key from the newly-created SSH Client key pair into a file by selecting Keys > SSH Client Keys > Export Public Key from the top menu bar.More items...
How to secure remote access?
Finally, ESET offers several tips for effectively configuring and securing your remote access accounts and services: 1 Disable internet-facing RDP. If that's not possible, minimize the number of users allowed to connect directly to the organization's servers over the internet. 2 Require strong and complex passwords for all accounts that can be logged into via RDP. 3 Use an additional layer of authentication (MFA/2FA). 4 Install a virtual private network (VPN) gateway to broker all RDP connections from outside your local network. 5 At the perimeter firewall, disallow external connections to local machines on port 3389 (TCP/UDP) or any other RDP port. 6 Protect your endpoint security software from tampering or uninstallation by password-protecting its settings. 7 #N#Isolate any insecure or outdated computers that need to be accessed from the internet using RDP and replace them as soon as possible.#N#Apply all of these best practices to FTP, SMB, SSH, SQL, TeamViewer, VNC, and other services as well.#N#Set up your RDP correctly using the advice shared in this ESET report from December 2019.
What are the actions of an attacker following an RDP breach?
Other actions performed by attackers following an RDP breach include clearing out log files to remove evidence of their activity, installing tools and malware on compromised machines, disabling or deleting scheduled backups, and exfiltrating data from the server.
What are the types of attacks that can follow an RDP compromise?
However, ransomware and extortion aren't the only types of attacks that can follow an RDP compromise, according to ESET. Often, attackers will try to install coin-mining malware or even create a backdoor, which can be then used if their unauthorized RDP access is ever identified and shut down.
What tools should be used to back up passwords?
But even strong passwords should be backed up by such tools as multifactor authentication and security analytics.
Is RDP more exploitable than ever?
Of course, cybercriminals have pounced on this transition, which is why RDP is more exploitable than ever. A report published on Monday by ESET discusses how attackers take advantage of RDP and what organizations can do to combat them.
Is RDP a security risk?
Though Remote Desktop Protocol can be enough of a security risk on its own, organizations often compound the vulnerabilities by failing to properly secure RDP accounts and services. Accounts with RDP privileges may have a weak password or no additional layers of security. Those flaws open the door for brute force attacks in which cybercriminals use automated tools to obtain the account password. If successful, the attackers can then invade a network, elevate their rights with administrative access, disable security products, and even run ransomware to encrypt critical data and hold it hostage.
Which countries have the most brute force attacks?
In the period between January 2020 and May 2020, the United States, China, Russia, Germany and France topped the list of countries with most IPs used for brute-force attacks.
Which countries have the most blocked IP addresses?
Countries that had the largest proportion of targeted IPs were Russia, Germany, Japan, Brazil and Hungary. Figure 2: Countries with the largest number of all blocked IP addresses (between Jan. 1 and May 31, 2020) RDP has become a popular attack vector in the past few years, especially among ransomware gangs.
Does remote access attract ransomware?
Poorly secured remote access attracts ransomware gangs, but used to implant coin miners and backdoors too#N#BRATISLAVA – ESET researchers, based on telemetry, confirm a significant uptick in the number of unique clients who have reported brute-force attack attempts blocked via ESET’s Network Attack Protection and its new layer, ESET Brute-Force Attack Protection. The trend has been observed since the onset of the global pandemic. The COVID-19 crisis has radically changed the nature of everyday work, forcing employees to manage large parts of their jobs via remote access. Cybercriminals – especially ransomware operators – are aware of the shift and attempt to exploit the new opportunities and increase their illicit earnings. In the period between January 2020 and May 2020, the United States, China, Russia, Germany and France topped the list of countries with most IPs used for brute-force attacks.#N#“Before the lockdown, most employees worked from the office and used infrastructure monitored and controlled by their IT department. But the coronavirus pandemic has brought a major shift to the status quo. Today, a huge proportion of ‘office’ work occurs via home devices, with workers accessing sensitive company systems through Windows’ Remote Desktop Protocol (RDP), a proprietary solution created by Microsoft to allow connecting to the corporate network from remote computers,” explains Ondrej Kubovič, ESET Security Research & Awareness Specialist.#N#“Despite the increasing importance of RDP, as well as other remote access services, organizations often neglect its settings and protection. Employees use easy-to-guess passwords, and without additional layers of authentication or protection, there is little that can stop cybercriminals from compromising an organization’s systems,” Kubovič continues.
Is RDP a threat to ransomware?
RDP has become a popular attack vector in the past few years, especially among ransomware gangs. These cybercriminals often brute-force their way into a poorly secured network, elevate their rights to admin level, disable or uninstall security solutions, and then run ransomware to encrypt crucial company data.
How to protect RDP from brute force attacks?
Use a VPN. RDP can be protected from brute force attacks by forcing users connect to it over a Virtual Private Network (VPN). This hides RDP from the Internet but exposes the VPN, leaving it vulnerable to attack, so it also needs to be properly secured. This is the approach taken by a lot of organizations, but is likely to be beyond the patience or technical ability of many home users.
How to lock out brute force?
Limit the number of guesses. The simplest way to lock out brute force attackers is to limit the number of password guesses they can make. If a legitimate user gets their password wrong, they normally only need a few extra guesses to get it right. There is no need to give somebody the luxury of making tens- or hundreds-of-thousands of guesses if you only need a handful. Locking out users who make too many wrong guesses, or limiting the number of guesses users can make has the effect of making weak passwords much, much stronger. (It’s how bank cards and smartphones get away with using simple four- or six-digit PINs to protect themselves.)
How do hackers figure out RDP passwords?
Hackers figure out RDP passwords using a technique called “brute force guessing,” which is as basic as it sounds. They simply use a computer program that will try a password and see if it works. If it doesn’t, it will try another, and another, and another, until it guesses a password correctly or decides it’s time to try its list of passwords on a different computer. The guesses aren’t random. Some passwords are far more popular than others, so criminals use lists of the most commonly used passwords, starting with the most popular.
How to protect yourself from RDP attacks?
Turn it off. The simplest way to protect yourself from RDP brute force attacks is to just turn off RDP permanently, if you don’t need it.
Can you break into a computer remotely?
While there are lots of ways to break into a computer that’s connected to the Internet, one of the most popular targets is the Remote Desktop Protocol (RDP), a feature of Microsoft Windows that allows somebody to use it remotely. It’s a front door to your computer that can be opened from the Internet by anyone with the right password.
Is my computer address a secret?
Reading that you might think that you’re safe as long as nobody knows your computer’s address. Unfortunately, your computer’s address isn’t a secret, even if you’ve never told anyone what it is.
Is RDP a threat?
RDP brute force attacks represent a serious, on-going danger to Internet-connected Windows computers. However, there are a number of ways to protect yourself against them. As in all areas of computer security, defence in depth is the best approach, so aim to do as many things on this list as you reasonably can.
How does brute force work?
In a brute force attack an attacker attempts to gain access to a computer by guessing the username and password of one of its users. Some attacks will try a limited number of usernames and passwords on as many computers as possible, while others will try tens of thousands of usernames and passwords on a single computer. Attacks are automated and relentless, and can start within hours of a computer being connected to the Internet.
What is brute force protection?
Malwarebytes’ Brute Force Protection blocks brute force RDP attacks on Windows workstations and servers by blocking IP addresses that exceed a threshold of invalid login attempts.
What is RDP attack?
Remote Desktop Protocol (RDP) attacks are rising as more organizations work from home. Brute force RDP attacks from across the globe seek to gain access to an Internet-connected computer, and then use it to infect other devices and servers on the network.
What is the best way to restrict access to RDP?
Use a virtual private network (VPN) to restrict access to RDP.
What does it mean to hold your company hostage?
Hold your company hostage . Attackers take full control of your company’s network and hold it, and your data, hostage.
How to defend against brute force attacks?
The best way to defend against brute force attacks that target passwords is to make passwords as tough as possible to crack. End-users have a key role to play in protecting their and their organization's data by using stronger passwords and following strict password best practices.
What is brute force attack?
What is a Brute Force Attack? A brute force attack is a hacking method that uses trial and error to crack passwords, login credentials, and encryption keys. It is a simple yet reliable tactic for gaining unauthorized access to individual accounts and organizations’ systems and networks.
What is hybrid brute force?
A hybrid brute force attack is when a hacker combines a dictionary attack method with a simple brute force attack. It begins with the hacker knowing a username, then carrying out a dictionary attack and simple brute force methods to discover an account login combination.
How long does brute force hacking take?
Brute force hacking requires plenty of patience because it may take months or even years for an attacker to successfully crack a password or encryption key. However, the potential rewards are huge.
What is dictionary attack?
A dictionary attack is a basic form of brute force hacking in which the attacker selects a target, then tests possible passwords against that individual’s username. The attack method itself is not technically considered a brute force attack, but it can play an important role in a bad actor’s password-cracking process.
How do hackers find passwords?
The attacker starts with a list of potential words, then experiments with character, letter, and number combinations to find the correct password . This approach allows hackers to discover passwords that combine common or popular words with numbers, years, or random characters, such as "SanDiego123" or "Rover2020."
Why is brute force called brute force?
The name "brute force" comes from attackers using excessively forceful attempts to gain access to user accounts.
What are brute force attacks and why are they so dangerous?
Brute forcing is a type of cyber attack that relies on the trial-and-error method: a malicious actor submits loads of passwords until they guess the correct character combination and gain access to a trusted user’s account. Such attacks are incredibly widespread for two reasons:
6 indicators of a brute force attack
You can detect hints of an upcoming attack in increased network activity, access violations, and unusual user behavior. Brute force indicators differ slightly depending on the type of attack and toolset a hacker uses. The good news is you can detect all of them with the same set of cybersecurity tools and practices.
8 ways to detect and prevent a brute force attack
Weak user passwords are what make brute force attacks successful. No matter how many cybersecurity awareness training sessions you conduct for your employees and how many policies you enforce, there will always be an employee that uses a “1234” password.
Conclusion
Hackers can leverage simple passwords and a weak cybersecurity posture to gain access to protected resources. It’s an old yet simple and effective hacking method.
What is an RDP brute force attack?
Imagine a burglar who has a key ring with a few hundred thousand keys on it. The criminal uses the keys one after the other in an attempt to unlock your front door. The better your lock, the longer it will take them to get inside. However, sooner or later, they’ll probably find the right key and once they’re inside they can do what they want – disable your alarm, steal your jewelry, vandalize your home or change the locks and demand you pay a ransom to get back inside. This is the basic premise of an RDP attack.
How many login attempts does brute force require?
As noted, brute force RDP attacks require hundreds, thousands or even millions of login attempts. You can slow the attacks by setting up a simple policy that locks users out after a certain number of attempts for a specified amount of time.
How can you protect your business against RDP brute force attacks?
With this in mind, you need to primarily focus on preventing initial access by minimising remote desktop security risks. This can be achieved in a number of ways:
How does brute force work?
In an RDP brute force attack, hackers use network scanners such as Masscan (which can scan the entire Internet in less than six minutes) to identify IP and TCP port ranges that are used by RDP servers. After tracking one down, the criminals try to gain access to the machine (typically as an administrator) by using brute force tools that automatically attempt to login over and over again using countless username and password combinations. During this time, server performance may take a hit as the attacks consume system resources.
What can an attacker do with RDP?
Once an attacker has access via RDP, they can do pretty much anything within the hacked account’s privilege limits. Criminals who have gained administrator access can do more or less anything they want, including disable antivirus software, install malware, steal company data, encrypt files and much more.
How many lockouts for 3 invalid attempts?
Three minute lockouts for three invalid attempts is a good place to start if you’re not sure of an acceptable attempt threshold.
Can an RDP attack have a major impact on a business?
Regardless of the criminal’s reasoning, there’s no denying that an RDP attack can have major consequences for businesses of any size .
When did bruteforce.generic.rdp attack?
Since the beginning of March, the number of Bruteforce.Generic.RDP attacks has rocketed across almost the entire planet: Growth in the number of attacks by the Bruteforce.Generic.RDP family, February–April 2019 ( download)
How to protect your company from hackers?
Companies need to closely monitor programs in use and update them on all corporate devices in a timely manner. This is no easy task for many companies at present, because the hasty transition to remote working has forced many to allow employees to work with or connect to company resources from their home computers, which often fall short of corporate cybersecurity standards. Our advice is as follows: 1 Give employees training in the basics of digital security. 2 Use different strong passwords to access different corporate resources. 3 Update all software on employee devices to the latest version. 4 Where possible, use encryption on devices used for work purposes. 5 Make backup copies of critical data. 6 Install security solutions on all employee devices, as well as solutions for tracking equipment in case of loss.
What to do if you don't use RDP?
If you don’t use RDP, disable it and close port 3389. Use a reliable security solution. If you use a different remote-access protocol, you still cannot relax: at the end of last year, Kaspersky experts found 37 vulnerabilities in various clients that connected via the VNC protocol, which, like RDP, is used for remote access.