How do I grant access to my Azure pipelines from GitHub?
Azure Pipelines must be granted access to your repositories to trigger their builds, and fetch their code during builds. There are 3 authentication types for granting Azure Pipelines access to your GitHub repositories while creating a pipeline. 1. GitHub App 2. OAuth 3. Personal access token (PAT)
Which authentication type should I use for GitHub repositories?
OAuth is the simplest authentication type to get started with for repositories in your personal GitHub account. GitHub status updates will be performed on behalf of your personal GitHub identity. For pipelines to keep working, your repository access must remain active.
Should I install the GitHub app for all repositories?
If you install the GitHub App for all repositories in a GitHub organization, you don't need to worry about Azure Pipelines sending mass emails or automatically setting up pipelines on your behalf. As an alternative to installing the app for all repositories, repository admins can install it one at a time for individual repositories.

Getting started
Clone this repository. Then ensure GoLang 1.16+ is installed before continuing.
Compile
When you are ready to use Pneuma in a real environment, you will want to compile it into a binary by running the build.sh script, passing in any string as your unique (public) randomHash string, which ensures each compiled agent gets a different file hash:
C-Shared library compilation (DLL, SO, DyLib)
Pneuma supports cross compilation to 64-bit C-shared libraries depending upon the platform you are building on. When using a C-Shared library, you must specifically compile in the parameters you want to configure in the util/conf/default.json file (specifically the address and the contact you wish you use).
Use without Operator
While Pneuma is designed to work with Prelude Operator, as an open-source agent you can point it against any command-and-control (C2) listening post you want. To do this, follow these instructions:
CALDERA inspired
As former CALDERA leads, we wrote the MITRE Sandcat and Manx agents. Pneuma is its own thing but it shares characteristics with both of these original agents.
Interested in contributing?
We strongly support contributors to this project. Please fork this repo and submit pull requests for considerations.
How many parts does a Trojan have?
A Trojan generally has two parts Client and Server or Master and Slave. We can say Server is Slave and Client is Master. So a server side is installed on a remote host and the attacker manipulates it with client software.
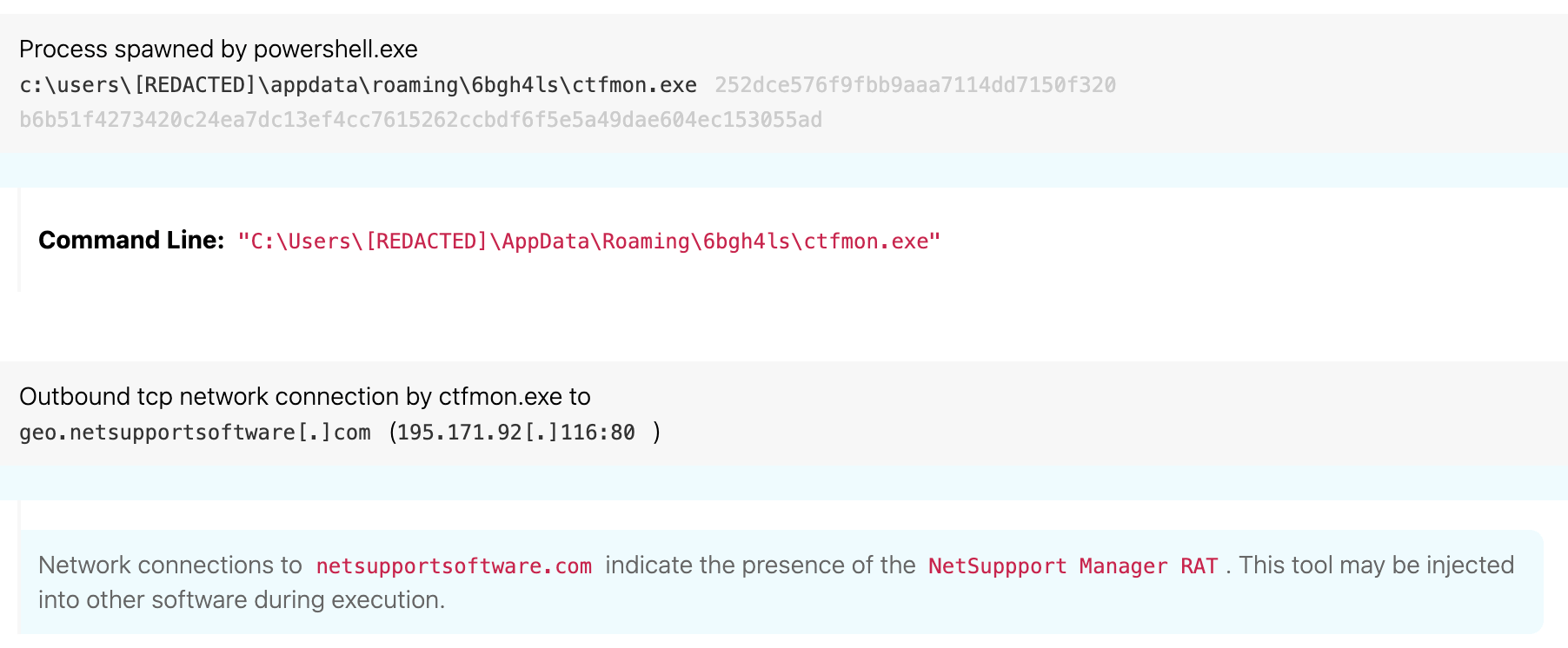
Why is RAT the most dangerous Trojan?
RAT is one of the most dangerous Trojan because it compromises features of all types of Trojans.
How to download Cerberus RAT?
Type “Download Cerberus RAT” in Google search and download Cerberus RAT. Execute Cerberus file and launch program. Accept EULA and following interface will be launched in front of you.
What portal does the bad guy come from?
this realm is your computer the portal the bad guy comes from is your REMOTE ACCESS TROJAN and his computer is the Realm where all they think off is taking over earth, now this portal (REMOTE ACCESS TROJAN) gives the bad guy (Hacker) access to your world (PC) And believe me when i say he can do ANYTHING with your computer when he gains this access. steal saved passwords, keylogging, put on your camera, steal banking credentials, lock your computer and ask for ransom, the list is endless. catch my drift???
How to listen to client Cerberus?
Configuring To Listen On Client: To configure Cerberus to listen on specific port select options and put “Connection Password” and “Connection Ports” that were specified in Server. Wait for victim to execute server and then just right click on listening server and play with options.
How to use C in a server?
Using c I would code both the server and client side code and establish simple message relays. After that all you need to do is send the code to the system (<command>); and send the output back to the socket descriptor.
Is a rat a Trojan?
They can hide themselves in process space of legitimate program and hence never appear in task manager or system monitors. A Trojan generally has two parts Client and Serve. Continue Reading. RAT is used to remotely connect and manage single or multiple computers. RAT is one of the most dangerous Trojan because it compromises features ...
How many slave servers does a botnet have?
This structure is characteristic of what's known as Command & Control botnets. These botnets have one master server and many slave servers. However, this style of botnets is anitquated and can easily be taken down by cutting access to the master domain.
What is the key to a P2P network?
However, the key to P2P network is that the admin/attacker can achieve master control through any node on the network. So, the attacker should have some sort of master key and encrypted logon that allows master control of any node.
What is a botnet?
A botnet is a network of computers that are capable of recieving commands remotely and deploying them locally. Optionally, they can choose to relay information back to other nodes in the network.
How to disguise malware?
One example of what you can do is mask the malware as an image. Let's use an image of a panda. I've added a simple function in utils.c that curls an image of a panda and presents it within Preview. This gives the notion to the user of opening an image of a panda when in actuality, the user is running your malware. To add this, include the following lines of code to bot.c:
Is master slave secure?
The master-slave structure you implemented is not very secure. The slaves can easily be freed by killing the master node. Optimally, you would switch to a P2P design. However, you can also slightly increase the security of master by directing it's commands randomly through a series of attacker-controlled bots before they're deployed onto the botnet. This makes it harder for experts to locate the center of command and trace botnet calls between attacker nodes and client nodes.
How does a RAT toolkit work?
Other elements propagate the RAT by sending out links to infected web pages. These are sent to the social media contacts of an infected user.
What is intrusion detection?
Intrusion detection systems are important tools for blocking software intrusion that can evade detection by antivirus software and firewall utilities. The SolarWinds Security Event Manager is a Host-based Intrusion Detection System. However, there is a section of the tool that works as a Network-based Intrusion Detection System. This is the Snort Log Analyzer. You can read more about Snort below, however, you should know here that it is a widely used packet sniffer. By employing Snort as a data collector to feed into the Snort Log Analyzer, you get both real-time and historic data analysis out of the Security Event Manager.
What can a hacker do with a RAT?
A hacker with a RAT can command power stations, telephone networks, nuclear facilities, or gas pipelines. RATs not only represent a corporate network security risk, but they can also enable belligerent nations to cripple an enemy country.
Who created DarkComet?
French hacker Jean-Pierre Lesueur developed DarkComet in 2008, but the system didn’t really proliferate until 2012. This is another hacker system that targets the Windows operating system from Windows 95 up to Windows 10. It has a very easy-to-use interface and enables those without technical skills to perform hacker attacks.
Can a Remote Access Trojan be installed to BIOS?
Access to the BIOS has been known to the world’s hackers since 2015. Many believe that the NSA was planting RATs and trackers on BIOS even earlier.
How to create a pipeline for GitHub?
To create a pipeline for a GitHub repository with continuous integration and pull request triggers, you must have the required GitHub permissions configured. Otherwise, the repository will not appear in the repository list while creating a pipeline. Depending on the authentication type and ownership of the repository, ensure that the appropriate access is configured.
What are GitHub secrets?
By default with GitHub pipelines, secrets associated with your build pipeline are not made available to pull request builds of forks . These secrets are enabled by default with GitHub Enterprise Server pipelines. Secrets include: A security token with access to your GitHub repository.
How does GitHub app work?
The app works with GitHub Checks to display build, test, and code coverage results in GitHub. To use the GitHub App, install it in your GitHub organization or user account for some or all repositories. The GitHub App can be installed and uninstalled from the app's homepage.
Can you use checkout submodules?
In some cases you can't use the Checkout submodules option. You might have a scenario where a different set of credentials are needed to access the submodules. This can happen, for example, if your main repository and submodule repositories aren't stored in the same Azure DevOps organization, or if your job access token does not have access to the repository in a different project.
Does Windows Agent have git?
The Windows agent comes with its own copy of Git. If you prefer to supply your own Git rather than use the included copy, set System.PreferGitFromPath to true . This setting is always true on non-Windows agents.
Can GitHub fork a repository?
A GitHub user can fork your repository, change it, and create a pull request to propose changes to your repository. This pull request could contain malicious code to run as part of your triggered build. Such code can cause harm in the following ways:
Can you make GitHub public?
If your GitHub repository is open source, you can make your Azure DevOps project public so that anyone can view your pipeline's build results, logs, and test results without signing in. When users outside your organization fork your repository and submit pull requests, they can view the status of builds that automatically validate those pull requests.
Python-Based Trojan Horse Attack
For the ones who didn’t know yet, a Trojan Horse Attack consists of embedding en exploit in an innocent-looking Application, or even in a document. As you might have guessed today we will embed a backdoor into a Kivy-made GUI. This attack is quite simple, the only thing you need to know is just some python and networking basics. Let us get started!
Talk is Cheap, Show me the code
Now it Is the moment to code our Trojan. Basically, we’ll organize using a function (a malicious one), and a class (the GUI). Such a simple code.
