What is remote access network?
An increasing number of companies are designing and implementing Remote Access Networks, which allow users who are not physically connected to a Wide Area Network (WAN) or Local Area Network (LAN) to access the network's servers, applications and databases or to participate in video conferencing and conference calls. The ability for a remote user to function as if they were in the next office dramatically improves overall efficiency while reducing total cost of ownership. Cisco Systems, the world's largest internetworking vendor, is the pioneer of the enabling technologies for Remote Access Networks. This book will identify and explain all of the Cisco products necessary for designing and building a remote access network and integrating it with legacy systems.
Why is NAT important for remote access?
NAT is a feature within the Cisco lOS that permits an organization's IP address structure to appear differently to outside networks than the actual address space it is using. This allows organizations to connect to the Internet without using globally unique addressing schemes internally. Cisco uses a concept called Easy IP to provide easy Internet access to small remote offices. Basically, the router at the premises is configured as a DHCP server to automatically allocate IP addresses to the hosts. In this manner, the router handles administration of addresses automatically. The router is next configured to use PAT to NAT all the internal hosts to a single inside global address that is obtained automatically from a remote access server only if there is traffic to send. So, using Easy IP, IP address allocation, NAT translation, and router IP address selection are all handled automatically.
What are the problems that network administrators face?
Security and access control is one of the problems that today's network administrators are facing. As networks expand and more networking devices need to be managed, scalability issues arise, particularly if access to these devices is to be centrally managed. As telecommuting becomes more popular, remote access solutions such as dial-up Public Switched Telephone Network (PSTN) and Integrated Services Digital Network (ISDN) connections on network access servers (NAS) need to be managed; the need to keep information internal and private is becoming an absolute necessity due to competitiveness in businesses. This can be accomplished by implementing a security solution known as a firewall— a network device that controls and monitors access to areas of a network—which determines the type of traffic that can enter or leave the network and that can get into the network from the outside. The way Cisco has made it possible to run a software package that includes a built-in firewall is presented.
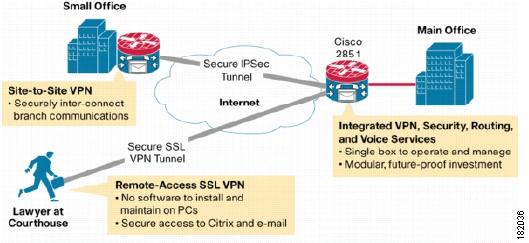
What is VPN technology?
VPN technology allows private secure networking over public network infrastructures. The different types of VPN solutions and the important factors to consider when determining whether a VPN solution is right for a specific environment are described. VPN technology can be used to create remote access networks over various public or private infrastructures, from the Public Switched Telephone Network using dial-up connections to secure communications across the Internet and point-to-point leased lines; to leverage current topology and in-place communications lines, which is easy to configure and has minimal costs associated with implementation; and to secure communications between hosts, between host and network, or between networks. Implementation will likely accelerate at an increased rate as more personnel gain the knowledge to configure these networks.
What is WAN connection?
Wide Area Network (WAN) connections are used to connect geographically separate networks. When a device on one network wants to communicate with a device on a different network or remote site, traffic has to traverse one or more WAN links. Unlike a local area network (LAN), a service provider typically provides the physical WAN connections. In this chapter, the study is conducted on the WAN connection requirements, topologies, and specifications. The Cisco Access Server product line, the routers that are currently available, and where the products fall within the Cisco product set are reviewed. Some of the remote access options that are currently available are also reviewed. The issues when planning the design, implementation, and installation of a Cisco remote access network, as well as identifying suitable equipment for each site that should be considered are detailed.
What is ISDN and DDR?
ISDN stands for Integrated Services Digital Network and is an International Telecommunication Union Telecommunication Standardization (ITU-T) term for a digital technology that replaces traditional analog telephone equipment with new high-speed digital equipment. ISDN was developed to overcome problems with the PSTN analog network. This chapter discusses the advantage of ISDN and dial-on-demand routing (DDR) to enhance remote connectivity. DDR can be used with technologies such as ISDN and Public Switched Telephone Networks (PSTN) and allows connections to be established and disconnected on an as-needed basis, which can result in substantial cost savings. There are two types of DDR configuration: legacy DDR and dialer profiles. The routing issues that occur when implementing DDR solutions and the various options available for maintaining routing tables without a permanent connection are presented in the end.
Purchase options
Easy - Download and start reading immediately. There’s no activation process to access eBooks; all eBooks are fully searchable, and enabled for copying, pasting, and printing.
Description
An increasing number of companies are designing and implementing Remote Access Networks, which allow users who are not physically connected to a Wide Area Network (WAN) or Local Area Network (LAN) to access the network's servers, applications and databases or to participate in video conferencing and conference calls.
About the Author
Wayne A. Lawson II (CCIE # 5244) currently with iPexpert, Inc., formerly a Systems Engineer with Cisco Systems in Southfield, Michigan.