What is BYOD and how does it work?
BYOD represents an opportunity between employees and employers. Typically, an organization will develop a BYOD policy that addresses security concerns, the types of allowable devices and other important considerations. Employees should read and understand their employer's policy before agreeing to it.
How do I access kindred workspace from a mobile device?
To access Kindred Workspace from a mobile device, you must download the VMware Horizon Client app from your device’s app store. Once installed, you need to allow your device, when prompted, to open the Horizon client to begin your remote access session.
What is remote access and how does it work?
Most teleworkers use remote access, which is the ability to access their organization's non-public computing resources from locations other than the organization's facilities.
What is the kindred remote access menu?
Employee Remote Access Menu Kindred provides employees the ability to access a variety of company resources while working in a home office or while on-the-go. As a reminder, Kindred employees must follow our Acceptable Use Policy to ensure the safety and security of our data and information, even when working remotely. Company Laptop & VPN

What is BYOD access?
BYOD stands for bring your own device, and the most commonly accepted BYOD meaning is when employees use their own personal devices to connect to the organization's network and access what they need to do their jobs. This includes data and information that could be potentially sensitive or confidential.
What can my company see on my BYOD phone?
Technically speaking, a company can see the wireless carrier, country, make and model, operating system version, battery level, phone number, location, storage use, corporate email and corporate data. The company can also see the names of all the apps on the device, both personal and work-related.
How do I control BYOD devices?
Here are five tips any organization can use to implement a secure BYOD policy.Establish Security Policies for All Devices. ... Define Acceptable Use Guidelines. ... Use a Mobile Device Management (MDM) Software. ... Communicate BYOD Policies to All Parties. ... Set Up an Employee Exit Plan.
Is BYOD good for security?
This means BYOD security is top of mind for IT and security leadership. Personal devices are more likely to be used to break into corporate networks, whether or not they are approved by IT, because they are less secured and more likely to contain security vulnerabilities compared to corporate devices.
How can I tell if my employer is monitoring my phone?
You can go to Settings, General, Profiles and Device Management to see how they are monitoring the phone. For Android phones, Google allows organizations to "manage, secure, and monitor," activity, even if they're not on company-issued devices.
Can my employer track my activity if I am connected to their VPN?
Because You Have A VPN A holistic protection from employers monitoring your personal computer or phone is by using a VPN or Virtual Private Network. A VPN basically works like a mask – your employer won't be able to see you so they can't see what you are doing on your personal computer.
How do I monitor BYOD?
How to Manage and Monitor BYOD (Bring Your Own Device)Step 1: Understand the Benefits of BYOD. ... Step 2: Consider BYOD Risks. ... Step 3: Determine Which Employees Will Be Permitted to Use BYOD and What Type of Use Will Be Permitted. ... Step 4: Establish a BYOD Policy. ... Step 5: Provide BYOD Training to Employees and Supervisors.More items...
Why is BYOD a security threat?
Each day, smartphone users inadvertently download malicious software to their devices, allowing malevolent actors to pinpoint their location, steal sensitive data and even uninstall security programs on the fly. The same security risks are present in the enterprise with BYOD units.
What is an example of BYOD?
Bring Your Own Device (BYOD) is a growing trend, in which devices owned by employees are used within the enterprise. Smartphones are the most common example, but employees may also bring their own tablets, laptops and USB drives.
What are the pros and cons of BYOD?
This Article Contains:5 Key BYOD Pros. Cost Savings. Up-to-date Technology. No Training Required. A Happier Workforce. Increased Productivity.5 Major BYOD Cons. Lack of Uniformity in Devices. Increased Distraction. Higher Security Risk. Difficult Data Retrieval. Legal Issues.
What are the advantages of BYOD?
Advantages of BYOD increase efficiency and productivity. raise employee satisfaction. allow greater choice in device type. cut hardware spend and software licencing costs.
Why do companies use BYOD?
BYOD means that employers save money, since they don't have to buy devices for each of their employees. An added benefit of this is that employees are more likely to take better care of the devices, since they own them.
Can my employer see my text messages on my personal phone?
The Electric Communications Privacy Act of 1986 forbids “unauthorized interception” of or access to electronic communications. Employers need your permission before they can monitor texts on a personal device.
Can my employer see my text messages on company phone?
Can my employer read my text messages? If you have a company-provided cell phone, your employer probably has the right to view your text messages, as well as other phone content and activities, such as your contacts and even what you do on social media.
Can your company spy on your personal phone?
Personal Phones: Employers generally cannot monitor or obtain texts and voicemails on an employee's personal cell phone.
Can my company access my personal phone?
Private employers do not have a legal right to access your personal cell phone in most cases, according to privacy attorneys, but a business cell phone, even when used for personal use, is a different matter.
How does BYOD work?
Typically, an organization will develop a BYOD policy that addresses security concerns, the types of allowable devices and other important considerations. Employees should read and understand their employer's policy before agreeing to it.
What is a BYOD policy?
Typically, an organization will develop a BYOD policy that addresses security concerns, the types of allowable devices and other important considerations. Employees should read and understand their employer's policy before agreeing to it.
What are the potential BYOD risks?
Any employee-owned devices that are not sanctioned by the employer are known as shadow IT, and these pose a security threat to the organization. Devices not visible to stakeholders cannot be monitored or protected from malware and other security risks. Therefore, a strong device policy will identify which personal devices may be used for work as well as when employees should rely on company-owned assets.
What is Citrix byOD?
Citrix products allow employees to access all of their apps and data on any device while giving IT the means to maintain security with uniform policy enforcement, full compliance and efficient control. Citrix products for BYOD allow organizations to:
What is shadow IT?
Any employee-owned devices that are not sanctioned by the employer are known as shadow IT, and these pose a security threat to the organization. Devices not visible to stakeholders cannot be monitored nor protected from malicious actors. Therefore, a strong BYOD policy will identify which personal devices may be used for work as well as when employees should rely on company-owned assets.
What is a "Bring Your Own Device"?
What is BYOD (Bring Your Own Device)? Bring your own device, BYOD, is the evolving trend of employees using their personal devices for work purposes. The device referred to here could be a laptop, smartphone, tablet, portable hard drive or any consumer piece of information technology. Companies may utilize BYOD or a subset of the trend, ...
When is a BYOD policy best implemented?
BYOD policy is best implemented when company stakeholders understand the pain point they are addressing. Stakeholders should build policy around the problem, then work with employees to implement the solution in a mutually beneficial manner.
What is a BYOD security?
BYOD security is the set of tools used to reduce risks from bring your own device (BYOD)— the practice of using a personal device, instead of a company-issued one, for work purposes. Any desktop or mobile device, from a laptop to a smartphone, can be used for BYOD. These BYOD endpoints may connect to company networks, hardware, and software—and cause significant security risks.
How are BYOD security policies enforced?
In terms of how security teams and IT departments enforce BYOD policies, many cybersecurity options are available . Common options include:
What are the pros and cons of BYOD?
Overall, proper BYOD security is integral to ensuring that BYOD pros outweigh its obvious cons. BYOD has inherent risks (cons) due to the fact that employees own the hardware in question and have more discretion over how it’s used. But the right BYOD security solutions can make each BYOD personal device safe enough for corporate use, while also providing extra convenience and comfort for employees (pros).
What is the security posture of BYOD endpoints themselves against?
The security posture of BYOD endpoints themselves against malware infections, phishing campaigns, and other security threats that could compromise sensitive data and spread laterally.
Why is it important to have a good byod?
BYOD security is important because BYOD itself is a widespread practice, especially in the context of increasingly popular remote and hybrid working environments. Each personal employee device connecting to a corporate application or WAN is a potential liability if not properly secured.
Is it safe to use a byod device?
But the right BYOD security solutions can make each BYOD personal device safe enough for corporate use, while also providing extra convenience and comfort for employees (pros).
Is BYOD a security issue?
Security vulnerabilities: Data leakage and malware infection are always front-and-center security concerns with BYOD, especially for devices that don't have anti-virus software installed
Executive summary
Malware on unmanaged and BYO devices can pose a serious risk to corporate resources
Protect against malware
Malware that lives on unmanaged and BYO devices can pose a serious risk to corporate resources, with the potential to infect entire networks. Malware attacks are up an astounding 358%, 1 and six in ten organizations have had systems infected with malware through web browsers.
Protect your network
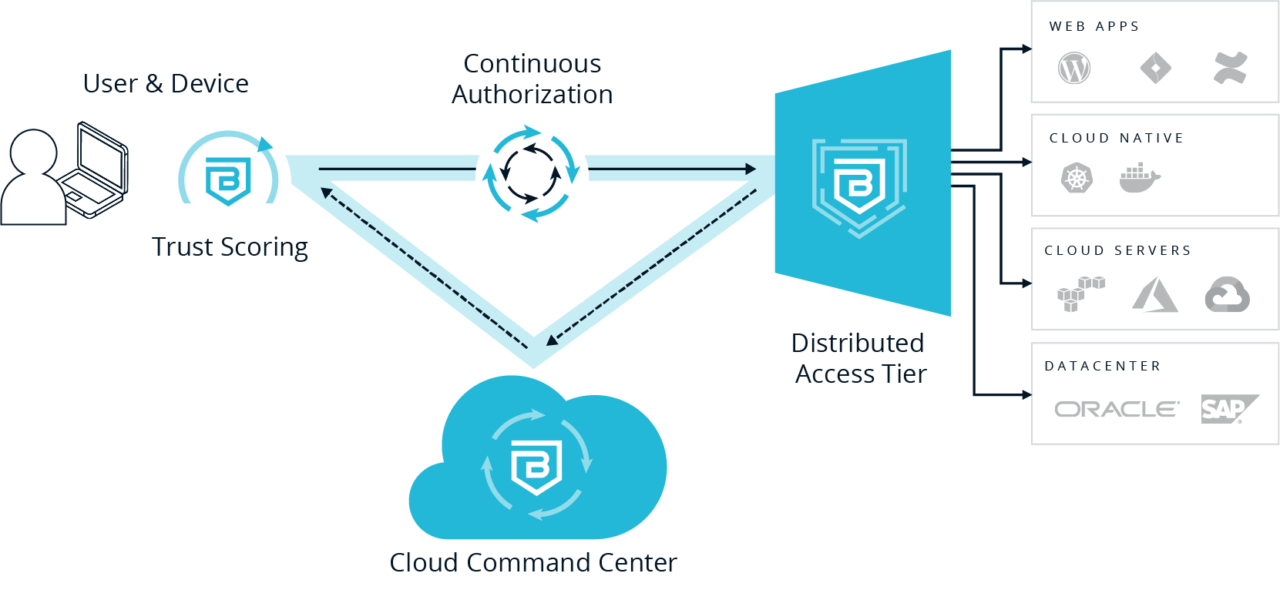
Browsing the internet can expose your data to all kinds of vulnerabilities. An estimated 53% of employees are using personal laptops for work, often with no new tools to secure them 3, causing constant concerns over data leakage, dangerous app downloads, and unsafe content. 4 With Citrix Secure Private Access, you won’t have to worry.
Get the secure authentication you need
More of the world’s employees are working from home than ever before, and the vast majority are using personal devices to access the cloud. Traffic from unmanaged and BYO devices has doubled as a result, leading to massive growth in corporate cloud attacks. 5 You could reduce your risks by limiting access.
How to access Kindred Workspace?
To access Kindred Workspace from a mobile device, you must download the VMware Horizon Client app from your device’s app store. Once installed, you need to allow your device, when prompted, to open the Horizon client to begin your remote access session.
What is Kindred's use policy?
As a reminder, Kindred employees must follow our Acceptable Use Policy to ensure the safety and security of our data and information, even when working remotely.