If the analyzer is running on a separate computer acting as a router on the path between the compromised machine and the remote machine, then the traffic cannot be hidden from the analyzer. The communication can make use of techniques such covert channels or steganography to make it difficult for you to see what is happening. Share
Full Answer
How can I capture a Wireshark server remotely?
Wireshark can generally capture only on the host it's running on, particularly when using remote desktop packages. Options such as rpcap or ssh do allow remote capture, one example is using pipes, see the wiki page here. Please start posting anonymously - your entry will be published after you log in or create a new account.
How to use sshdump with Wireshark?
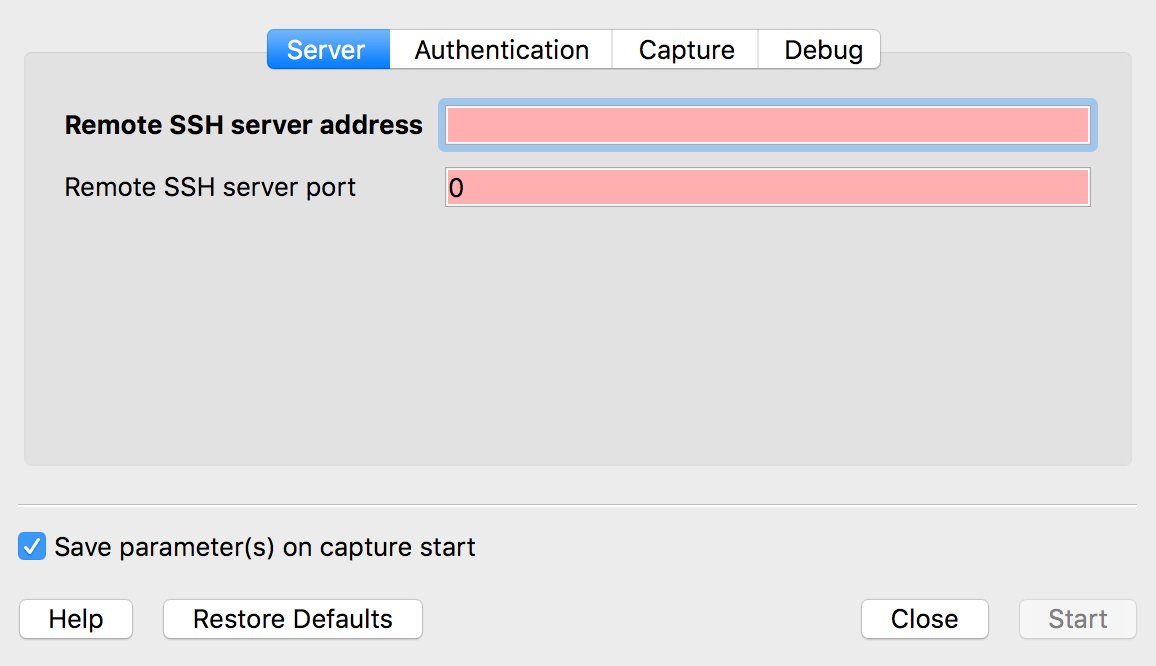
The sshdump manpage is for the extcap binary that is used to make the ssh connection from Wireshark. Normally you won't need to look at that. The above dialog is the UI provided by the extcap and sshdump interface. I think the Remote Capture Command should be the full path to the binary you wish to use on the remote machine, e.g. /usr/sbin/tcpdump
Is it possible to use Wireshark without a computer?
Wireshark is a powerful tool, but it has its limitations. Unless you have professional networking equipment, it’s hard to analyze traffic that doesn’t involve your computer. Sometimes the easiest solution is to use tcpdump to capture traffic on the remote server, and then run Wireshark to take a look at it. What are Wireshark and tcpdump?
Is it possible to use Wireshark to analyze network traffic?
Wireshark is a powerful tool, but it has its limitations. Unless you have professional networking equipment, it’s hard to analyze traffic that doesn’t involve your computer. Sometimes the easiest solution is to use tcpdump to capture traffic on the remote server, and then run Wireshark to take a look at it. Contents.
Can Wireshark capture remote traffic?
In remote capture mode, traffic is sent to the computer running Wireshark through one of the network interfaces. Depending on where the Wireshark tool is located, the traffic can be sent on an Ethernet interface or one of the radios.
Can you detect if someone is using Wireshark?
You can't usually detect Wireshark or any other sniffer that is passively capturing packets on your network, and most of the time that is not a problem at all.
Can you get someones IP from Wireshark?
Wireshark is a powerful tool that can analyze traffic between hosts on your network. But it can also be used to help you discover and monitor unknown hosts, pull their IP addresses, and even learn a little about the device itself.
What can Wireshark reveal?
Wireshark has many uses, including troubleshooting networks that have performance issues. Cybersecurity professionals often use Wireshark to trace connections, view the contents of suspect network transactions and identify bursts of network traffic.
Can you block Wireshark?
To stop a Wireshark capture using the Stop Capture toolbar button: Locate the toolbar button with the help text Stop the running live capture. This should be the fourth toolbar button from the left. Click the Stop Capture toolbar button.
How does Wireshark detect suspicious activity?
2:435:15Wireshark Tip 4: Finding Suspicious Traffic in Protocol HierarchyYouTubeStart of suggested clipEnd of suggested clipThe trace file I'm going to open up is called SE C. - sick client and this is a trace file that youMoreThe trace file I'm going to open up is called SE C. - sick client and this is a trace file that you can download from the Wireshark.
How do I see websites visited in Wireshark?
Type "tcp. port == 80" into the filter box at the top of of the Wireshark window and press "Enter" to filter the packets by Web browsing traffic.
How do you pull someone's IP?
Use an IP lookup tool Starting with the simplest way to find someone's IP address is to use one of the many IP lookup tools available online. Resources such as WhatIsMyIPAddress.com or WhatIsMyIP.com offer tools to enter an IP address and search for its free public registry results.
Can Wireshark automatically resolve the IP address into host names?
Can Wireshark automatically resolve the IP address into host names? Wireshark will resolve ip addresses to hostnames when the capture file contains DNS traffic or when you have a hosts file in your profile that maps ip addresses to hostnames.
What can hackers do with Wireshark?
Wireshark is an open-source, free network packet analyzer, used to capture and analyze network traffic in real-time. It's considered one of the most essential network security tools by ethical hackers. In short, with Wireshark you can capture and view data traveling through your network.
Does a VPN prevent packet sniffing?
Data encryption is an excellent choice for individuals and professionals against sniffing. Tunnel your connectivity using Virtual Private Network (VPN) to protect yourself from packet sniffers. When you browse the internet using a VPN, the data passes through a securely encrypted tunnel.
What can Wireshark not do?
Wireshark will not manipulate things on the network, it will only “measure” things from it. Wireshark doesn't send packets on the network or do other active things (except domain name resolution, but that can be disabled).
How does Wireshark identify network abuse?
Use the combined filter http and ip. addr == [IP address] to see HTTP traffic associated with a specific IP address. Open the Endpoints dialog again and you'll see a list of websites being accessed by that specific IP address. This is all just scratching the surface of what you can do with Wireshark.
How does Wireshark detect malicious traffic?
Open the pcap file with Wireshark. We are going to find: The IP address, MAC address, and host name of the infected Windows host. The Windows user account name of the victim....Traffic Analysis with WiresharkObtain.Strategize.Collect Evidence.Analyze.Report.
How do you identify a network?
Select the Start button, then type settings. Select Settings > Network & internet. The status of your network connection will appear at the top. Windows 10 lets you quickly check your network connection status.
Is Wireshark malware?
A piece of malware calling itself "Wireshark Antivirus" has been infecting computers recently. It attempts to get you to pay for fake antivirus software. To be clear, CACE Technologies and the Wireshark development team do not and have never made antivirus software. Someone is fraudulently using our name.
How do I tcpdump an IP address?
The host filter will reduce the tcpdump to the traffic for just one IP address, use the host filter. This should be followed by the IP address. For...
How do I use tcpdump on a specific port?
You can select all traffic for a specific port with a filter on the tcpdump command. This method will also give you specific protocol traffic just...
What is remote packet capture protocol?
Remote Packet Capture Protocol is a program, called RPCAPD.EXE. This is implemented as a daemon and is part of WinPCap. The Remote Packet Capture P...
Why doesn't tcpdump capture passwords like ftp and ssh unlike Wireshark?
It is possible to capture ftp passwords with tcpdump. Run tcpdump -nn -v port ftp or ftp-data and search the output for USER to get the username an...
What is the command line option for Wireshark?
The -w command-line option enables Wireshark compatible capture output. It takes a single variable, which is the tcpdump output filename. Capture logs saved using this option won’t be human-readable outside of Wireshark, since they’re stored in binary rather than ASCII.
What are Wireshark and tcpdump?
While Wireshark does a great job of capturing every network packet that flows past it, in some cases you’ll need to analyze a session from a remote server. Unless you have special networking equipment, this can be difficult. Sometimes it’s easier to capture traffic on the remote server, then analyze it on your desktop.
Why doesn't tcpdump capture passwords like ftp and ssh unlike Wireshark?
Run tcpdump -nn -v port ftp or ftp-data and search the output for USER to get the username and PASS to get the password. Even Wireshark won’t decrypt an SSH session, including the login credentials without already knowing the key used to encrypt the connection. Neither tcpdump or Wireshark can get the username or password for an SFTP or FTPS session.
How do I use tcpdump on a specific port?
You can select all traffic for a specific port with a filter on the tcpdump command. This method will also give you specific protocol traffic just as long as you know the port used for that protocol. The filter is port and it is possible to specify just TCP or UDP traffic with the options tcp and udp. Examples: tcpdump port 53 or tcpdump udp port 53.
What is remote packet capture protocol?
Remote Packet Capture Protocol is a program, called RPCAPD.EXE. This is implemented as a daemon and is part of WinPCap. The Remote Packet Capture Protocol daemon acts as an agent on one computer, allowing packets to be captured from it according to commands issued on another computer.
How to open tcpdump file in Wireshark?
Start Wireshark, then import the tcpdump captured session using File -> Open and browse for your file. You can also double-click the tcpdump capture file to open it in Wireshark, as long as it has the *.pcap file extension. If you used the -w option when you ran the tcpdump command, the file will load normally and display the traffic.
How to capture traffic with tcpdump?
In order to capture traffic with the tcpdump command, you’ll need to connect to the remote computer through SSH. You will also need root access, otherwise the tcpdump won’t be able to capture traffic and you’ll see an error stating You don’t have permission to capture on that device.
How to capture a remote from Wireshark?
Click the Capture Option s link in Wireshark, then select Remote from the Interface box.
How to use Wireshark in terminal?
Wireshark in a Terminal (TShark) If you don’t have a graphical interface on your system, you can use Wireshark from a terminal with the TShark command. First, issue the tshark -D command. This command will give you the numbers of your network interfaces. Once you have, run the tshark -i # command, replacing # with the number ...
How does TShark work?
TShark acts like Wireshark, printing the traffic it captures to the terminal. Use Ctrl-C when you want to stop the capture. Printing the packets to the terminal isn’t the most useful behavior. If we want to inspect the traffic in more detail, we can have TShark dump it to a file that we can inspect later.
How to make a copy of Wireshark?
Create a copy of Wireshark’s shortcut, right-click it, go into its Properties window and change the command line arguments. Add -i # -k to the end of the shortcut, replacing # with the number of the interface you want to use. The -i option specifies the interface, while the -k option tells Wireshark to start capturing immediately.
What firewalls does Wireshark use?
Use the Product menu to select your firewall type. Wireshark supports Cisco IOS, different types of Linux firewalls, including iptables, and the Windows firewall.
How to enable network name resolution?
You can enable this setting by opening the preferences window from Edit -> Preferences, clicking the Name Resolution panel and clicking the “ Enable Network Name Resolution ” check box.
Can TShark show packets?
TShark won’t show you the packets as they’re being captured, but it will count them as it captures them. You can use the File -> Open option in Wireshark to open the capture file later. For more information about TShark’s command line options, check out its manual page.
1 Answer
Wireshark can generally capture only on the host it's running on, particularly when using remote desktop packages.
Your Answer
Please start posting anonymously - your entry will be published after you log in or create a new account.
What Does Wireshark Do?
Wireshark isn’t a niche tool that’s only used by a few amateurs and underground networks. You could find use cases of Wireshark in the networks of government agencies, commercial corporations, and even non-profit organizations.
What is Wireshark software?
It’s a piece of software that allows you to capture data packets from a private or public network connection. It also gives you the freedom to browse the data traffic going through the network and interact with it in real-time.
How does Wireshark work?
It starts by accessing a network connection and grabbing whole sections of data traffic in real-time. It can capture anywhere from dozens to tens of thousands of data packets at a time.
When was Wireshark first developed?
Wireshark was first developed in 1998 and known under the name Ethereal—its name changed to Wireshark in 2006, almost 10 years after.
Is Wireshark a beginner?
Compared to other packet sniffers, Wireshark has one of the most user- and beginner-friendly interfaces. Not to mention, it still has a largely active online community and countless tutorials and official documentation available for when you run into any walls.
Can Wireshark analyze data?
This free cross-platform packet sniffer can securely analyze data. Here's how you can use Wireshark to troubleshoot network issues.
Is Wireshark compatible with Linux?
Wireshark is also compatible with a wide range of devices. You can use it to access your network regardless of the type of device you mainly use, whether it’s Linux, Windows, Ubuntu, or macOS.
What does the last k mean in wireshark?
The last - before de | is the redirection of that output and is used to standard input by wireshark. The -k option in wireshark means "start inmidiately sniffing
How to capture traffic on a switch?
You connect a physical link from your listening host to that port/hub and then you can see all the traffic crossing the device. Alternatively, you'll need to install your packet capture software in a more strategic location in your network like a border firewall/router.
Can you use file descriptor to connect to and receive packets by ssh and pipe it to wire?
You can use a file descriptor to connect to and receive the packets by ssh and pipe it to wireshark locally:
View or Download the Cheat Sheet JPG image
Right-click on the image below to save the JPG file ( 2500 width x 2096 height in pixels), or click here to open it in a new browser tab. Once the image opens in a new window, you may need to click on the image to zoom in and view the full-sized jpeg.
View or Download the cheat sheet JPG image
Click on the link to download the Cheat Sheet PDF. If it opens in a new browser tab, simply right click on the PDF and navigate to the download selection.
