What are remote access trojans (RATs)?
According to our cybersecurity glossary, Remote Access Trojans (RATs) use the victim’s access permissions and infect computers to give cyberattackers unlimited access to the data on the PC. Cybercriminals can use RATs to exfiltrate confidential information.
How many Trojans are enough for your average cyberattacker?
It seems that one or two Trojans aren't enough for your average cyberattacker. Charlie Osborne is a cybersecurity journalist and photographer who writes for ZDNet and CNET from London. A recent campaign leveraging public cloud infrastructure is deploying not one, but three commercial Remote Access Trojans (RATs).
What are the most common Trojan strains?
Netwire, Nanocore, and AsyncRAT are popular commercial Trojan strains that are widely used by threat actors to remotely access and hijack vulnerable machines, steal user data, and conduct surveillance by means including audio and camera capture.
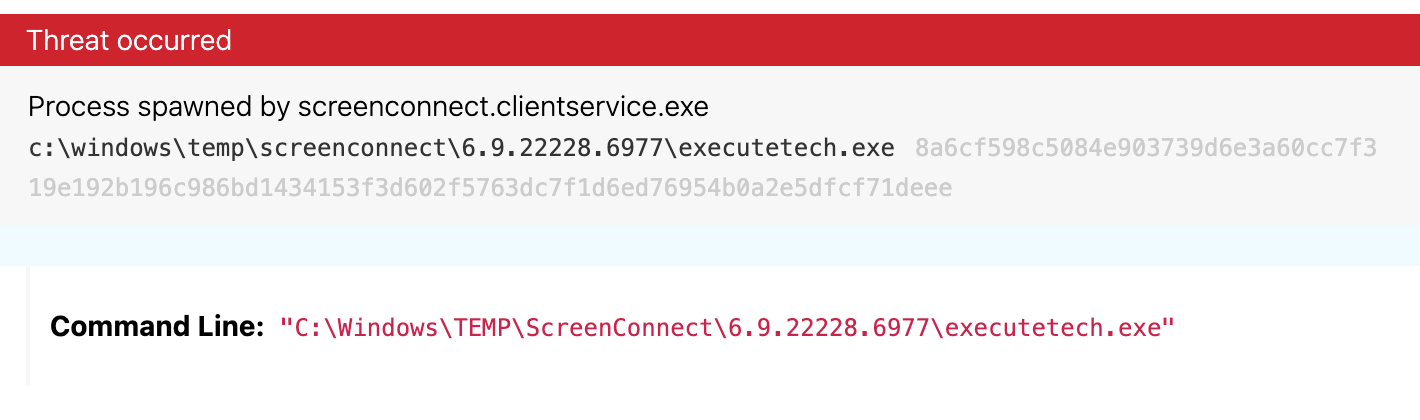
What can a Remote Access Trojan do?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
Can a Trojan virus spread?
A virus is a program that spreads by attaching itself to other software, while a trojan spreads by pretending to be useful software or content. Many experts consider spyware programs, which track user activity and send logs or data back to the attacker, as a type of trojan.
Can remote access Trojans be detected?
As you might imagine, this can lead to sticky situations. A Remote Access Trojan paired with a keylogger, for instance, can easily acquire login information for bank and credit card accounts.
Can a Trojan steal your data?
Backdoor Trojan: A backdoor Trojan enables an attacker to gain remote access to a computer and take control of it using a backdoor. This enables the malicious actor to do whatever they want on the device, such as deleting files, rebooting the computer, stealing data, or uploading malware.
Can you remove a trojan virus?
Trojan viruses can be removed in various ways. If you know which software contains the malware, you can simply uninstall it. However, the most effective way to remove all traces of a Trojan virus is to install antivirus software capable of detecting and removing Trojans.
How does Trojan spread from one computer to another?
Computer viruses usually spread in one of three ways: from removable media; from downloads off the Internet; and from e-mail attachments. Although the Internet gets a bad rap as a source of viruses, you're no more likely to contract a virus from the Web than you are from packaged software.
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Can an Iphone get a Remote Access Trojan?
The only way to get a Remote Access Trojan on an iOS device would be to jailbreak it to remove the inherent iOS limitations of file system and app sandboxes and to open restricted ports (that are blocked by iOS itself by default).
What is the best Remote Access Trojan?
What is Remote Access and Administration?...10 Best Remote Access Software (Remote Control Software) In 2022Comparison of Top Remote Access Tools.#1) NinjaOne (Formerly NinjaRMM)#2) SolarWinds Dameware Remote Support.#3) Atera.#4) Supremo.#5) ManageEngine Remote Access Plus.#6) RemotePC.#7) TeamViewer.More items...•
Does factory reset remove Trojans?
In short, yes, a factory reset will usually remove viruses … but (there's always a 'but' isn't there?) not always. Due to the wide variety and ever evolving nature of computer viruses, it's impossible to say for sure that a factory reset will be the answer to curing your device from a malware infection.
Can Windows Defender remove Trojan?
Windows Defender comes packed with the Windows 10 update and offers top-notch antimalware protection to keep your device and data safe. Although, Windows Defender is not capable of handling all kinds of viruses, malware, trojan, and other security threats.
What is the most damaging computer virus?
Top 10 Most Destructive Computer Viruses of All TimeILOVEYOU. The ILOVEYOU virus posed as a love confession. ... Code Red. Code Red targeted Microsoft IIS users and even the White House website was hit. ... Melissa. This virus started in 1999 as an infected word document. ... Storm Trojan. ... Sasser. ... My Doom. ... Zeus. ... Conficker.More items...
How do I know if I have a Trojan virus?
If you notice any new programs running on your system that you did not install, it could be a trojan. Try removing the program and restarting your computer to see if your computer's performance improves.
How do I remove a Trojan virus from my iPhone?
Restart your iPhone. The easiest way to get rid of an iPhone virus is to restart your phone. ... Update iOS. ... Clear your iPhone's browsing history and data. ... Remove suspicious apps from your iPhone. ... Restore your iPhone to a previous backup version. ... Factory reset your iPhone.
Can Trojan virus be removed by factory reset?
In short, yes, a factory reset will usually remove viruses … but (there's always a 'but' isn't there?) not always. Due to the wide variety and ever evolving nature of computer viruses, it's impossible to say for sure that a factory reset will be the answer to curing your device from a malware infection.
Can an iPhone get a Trojan virus?
Malicious software includes Trojan horses, viruses, and spyware programs. Although viruses are uncommon on the iPhone, it's possible to get infected with an iPhone Trojan or spyware that can expose your phone's activity to a third party. Keeping your iOS up to date can greatly reduce the chances of this happening.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
How Does A Remote Access Trojan Work?
A Remote Access Trojan (RAT) infects a computer with a virus that gives cyberattackers unrestricted access to the data on the PC by using the victim’s access permissions. A RAT can include backdoors into the computer system, which can be used to create a botnet and spread to other devices as well.
What Is The Use Of Remote Access Trojan?
Malware developers use Remote Access Trojan (RAT) tools to gain full access and control over a user’s computer, including mouse and keyboard control, file access, and network resources.
What Damage Can A Trojan Do?
In general, a Trojan is designed to damage, disrupt, steal, or in general cause some other harm to your data or network. You are fooled by a Trojan by pretending to be a legitimate application or file.
What Is The Best Trojan Remote Access?
Hackers commonly use Blackshades to gain remote access to computers. Windows-based operating systems are frequently targeted by this tool. The Trojan has infected 500,000 systems worldwide until now.
What Is The Purpose Of A Trojan Horse?
In general, a Trojan is designed to damage, disrupt, steal, or in general cause some other harm to your data or network.
What Is Trojan Ddos?
An infected computer is used to launch a DoS attack from a pre-defined address using this type of malicious program. The malicious user infects a number of computers with this type of Trojan in advance (for example, as part of a mass spam mailing) in order to conduct a successful DoS attack.
Is Remote Access Detectable?
Could the website detect that Desktop 2 is being remotely operated? Desktop 1 cannot be detected, but remote operations can be. There is no way they can do it. In theory, if they have access to your home ISP, they could see the inbound/outbound connections between your home PC and the server.
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
What Does a RAT Virus Do?
Since a remote access trojan enables administrative control , it is able to do almost everything on the victim machine.
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
Why is Darkcomet no longer available?
The reason is due to its usage in the Syrian civil war to monitor activists as well as its author’s fear of being arrested for unnamed reasons.
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
Why is email at risk?
Since an attacker remotely accesses the computer, authenticated accounts such as email are at risk. Attackers can use email, for example, to send malicious messages to other potential victims using the authenticated email account on the remotely controlled device. Using a trusted email account gives attackers a better chance of tricking an email recipient into installing malware or running a malicious attachment.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
What is a remote access Trojan?
There are several remote access systems that may have legitimate applications , but they are known as tools that hackers use primarily as part of a Trojan; these are classified as remote access Trojans.
What is a Remote Access Trojan and How it Works, Exactly?
A remote access Trojan, more popularly known as RAT, is a type of malware that can carry out covert surveillance on a victim’s computer.
What is botnet hacking?
Essentially, a botnet allows a hacker to use a computer’s resources for tasks like DDOS attacks, Bitcoin mining, file hosting, and torrenting.
Why are obfuscation methods used in parallel programs?
The obfuscation methods used by parallel programs to hide RAT procedures make them very difficult to detect.
What is backdoor access?
Backdoor access provides virtually complete access to the machine, allows you to change settings, control user behavior, use the computer’s Internet connection, and even access other computers on the victim’s network.
What is the meaning of "moving the cursor around the screen in real time"?
From downloading software, opening documents, moving the cursor around the screen in real-time, being able to collect information from anyone without their knowledge.
Can hackers hack your computer?
Hackers can also control your computer remotely to perform illegal actions online on your behalf or use your home network as a proxy server to commit crimes anonymously.
What are the consequences of installing remote access Trojans?
If attackers succeed in installing Remote Access Trojans say in power stations, traffic control systems, or telephone networks, they can gain powerful control over them and even take down communities, cities, and nations. In this regard, we remember the 2008 war between Russia and Georgia, when Russia used a coordinated campaign of physical and cyber warfare to seize territory from the neighboring Republic of Georgia.
What percentage of Georgia's internet was affected by the Russian invasion?
Thirty-five percent of Georgia’s Internet networks suffered decreased functionality during the attacks, with the highest levels of online activity coinciding with the Russian invasion of South Ossetia on August 8, 9, and 10. Even the National Bank of Georgia had to suspend all electronic services from August 8–19.
Can a RAT be paired with a keylogger?
For example, if a RAT is paired with a keylogger, it can easily gain login information for financial and personal accounts. To make matters worse, they can stealthily activate a computer’s camera or microphone, and even access private photos and documents, or use your home network as a proxy server, to commit crimes anonymously.
Is antivirus enough to keep a company secure?
Antivirus is no longer enough to keep an organization’s systems secure.
How Do Remote Access Trojans Spread?
As with most malware infections, RATs typically come through malspam, phishing and spearphishing campaigns. For example, a user may receive a phishing email carrying a malicious pdf or Word document, or the mail may contain a URL that takes the victim to a webpage for a fake software plugin and a message that a required tool is missing or needs updating. Adobe Flash, Adobe Reader and similar popular products are often spoofed for just this kind of trick due to their wide adoption across platforms.
What is a Remote Access Trojan?
Sometimes referred to as a “remote administration tool” due to their similarity to legitimate IT admin tools like TeamViewer and LogMeIn, a remote access trojan is essentially a hidden backdoor into another user’s computer. This backdoor gives the person operating the RAT a whole range of different functions that can be used for malicious purposes, depending on which particular RAT platform they’re utilizing.
How Do Threat Actors Use RATs Against The Enterprise?
While there’s certainly been cases of “lone wolf” actors targeting individuals and organizations and remaining undetected for over a decade, until recently the main threat to enterprise from RATs came from APT campaigns, including those targeting the most sensitive of installations such as a nuclear power plant in India (targeted by the DTrack RAT), oil and gas companies in the Middle East, telecoms across Africa and Asia ( DanBot RAT ), government agencies around the globe ( Calypso RAT ), and most recently an energy-sector organization in Europe ( PupyRAT ).
How Can CISOs Protect Against Remote Access Trojans?
In the past, RATs were difficult to develop and required a high degree of proficiency to operate. They were anything but “fire-and-forget” tools. They required threat actors to invest time and effort in inserting the malware into victims’ systems, manually operate the connection and then carry out whatever nefarious activities they had planned. As we have seen, things have changed more recently, and like other crimeware such as ransomware as a service, malware developers have seen and grasped the opportunity to make profit by selling easy access to tools that others do not have the skill to make for themselves.
Can you disable RDP?
Aside from that, disable Remote Desktop Protocol (RDP) and any similar remote access protocols across your fleet where they are not needed. Except for machines that require a constant remote connection, endpoints are typically better off only enabling RDP and similar services on a temporary “as needed” basis.
Can a RAT go undetected?
This ability to blend in with normal or expected traffic can allow a RAT to go undetected for months or years, which makes the RAT a perfect tool for all kinds of malicious actors, from APT and nation-state hackers to criminals looking for financial reward.
Executive Summary
Recorded Future analysts continue to monitor the activities of the FIN7 group as they adapt and expand their cybercrime operations. Gemini has conducted a more in-depth investigation into these types of attack after a Gemini source provided analysts with the file “sketch_jul31a.ino”, which was linked to FIN7’s BadUSB attacks.
Key Findings
FIN7 used an Arduino sketch file called “sketch_jul31a.ino” to install malware on USB devices as part of BadUSB attacks.
Attack Analysis
Gemini specialists conducted the analysis of the file “sketch_jul31a.ino”. “.INO” is a file extension associated with the Arduino microcontroller programming platform, while “sketch” is the platform’s term for a program.
Outlook and Conclusions
The use of trojanized USB devices for keystroke injection is not a new technique, even for FIN7. Typically the attack targets specific persons with access to the computer systems of the intended victim company.
What port does Ttint use?
Ttint implements a single instance by binding port 57322, by killing the process using this port, it can exit itself.
Where did the attacker use the Google Cloud?
About the infrastructure, the attacker first used a Google cloud service IP, and then switched to a hosting provider in Hong Kong. When we looked up the website certificate, sample, domain name and IP in our DNSmon system Later, we were able to see more infrastructure IPs, samples, and more C2 domain names.
What protocol does Mirai use?
In addition, at the C2 communication level, it uses the WSS (WebSocket over TLS) protocol. Doing this can circumvent the typical Mirai traffic detection at the traffic level, and it also provides secure encrypted communication for C2.
Can Ttint hijack a network?
The result of this is that the author of Ttint can hijack any network access of users under the affected routing device to possibly monitor or steal sensitive information .
ZDNet Recommends
A roundup of the best software and apps for Windows and Mac computers, as well as iOS and Android devices, to keep yourself safe from malware and viruses.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0