When you connect to a VPN server
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g…
Can my ISP see if I use a VPN?
It’s important to note that your ISP or an online service seeing that you use a VPN isn’t bad news. That’s because it doesn’t mean that they can see what you’re sharing. When you connect to the internet through a VPN, your IP address appears that of a VPN, so your real IP address cannot be tracked.
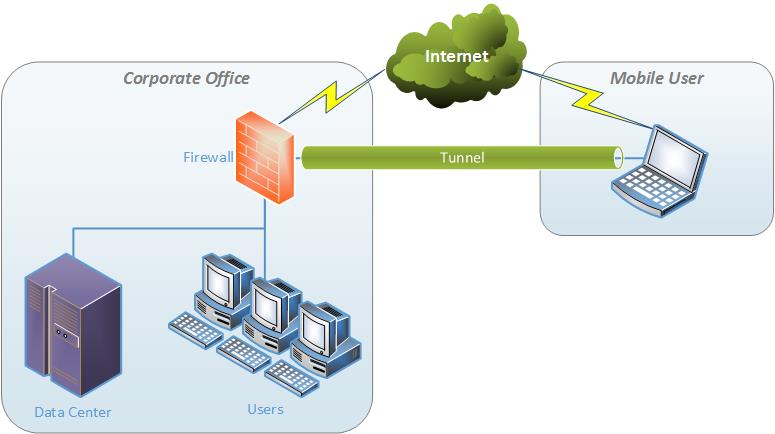
What is a remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
Can I use my personal VPN on my company network?
Since all your “personal” traffic goes through your ISP’s servers, it won’t bog down the company network. In fact, companies using corporate VPN solutions may already implement split-tunneling for this exact reason. Mind you, this is a pretty specific scenario. Don’t start suggesting ways of slacking off to your boss.
What is the difference between a site-to-site VPN and remote access VPN?
A site-to-site VPN and a remote access VPN both offer similar benefits but they actually have different use cases. A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location.

What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
Why is VPN important for business?
The most important benefit though is data security. When an offsite employee sends data through a VPN, it is encrypted, so even if a hacker is able to intercept that data, they won’t be able to use it. This is particularly important if an employee accesses their companies’ network using public Wi-Fi while traveling because traffic sent over these networks is usually not encrypted.
What is a network access server?
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Why do businesses use VPNs?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is it good to work remotely?
The ability to work remotely is one of the perks that many businesses offer employees to help sweeten the deal. The recent coronavirus outbreak has only exacerbated that, leading many more organizations to allow their employees to work remotely. While this is good news for employees, it could end up causing a great deal of disruption to organizations that aren’t prepared and one way to do so is to look into remote access VPN solutions.
Why do businesses use VPNs?
Since the pandemic took over, businesses are needing to find a way for their employees to access the company ’s network from home. VPNs provide the most secure way for companies to access their networks and private resources.
Why are VPNs important?
VPNs encrypt web traffic so no one is able to see your data, whether it’s a hacker, corporation, or government. VPNs were originally created to connect businesses securely online so they’ll be able to login from home. Now that 80% of Americans are required to stay home, VPNs are necessary for remote work.
What is a VPN?
Virtual Private Networks (VPN) are designed to protect your online identity by connecting your device to a secure server rather than your typical ISP. The goal is keeping your private information private. VPNs encrypt web traffic so no one is able to see your data, whether it’s a hacker, corporation, or government.
Why do ISC SANS recommend that companies examine the logs of their VPN authentications?
ISC SANS instructors are recommending that companies examine the logs of their VPN authentications to ensure only authorized users have access, which is a monotonous task.
Why is VPN end to end encryption important?
VPN End-to-End Encryption is Critical for Secure Communication. E2EE is vital for remote work because even if a hacker is able to access the network and steal information, anything they get would be worthless. Without E2EE, your message will be able to be decrypted by a mid-point server, meaning your web traffic and IP is visible.
How to use certificates for VPN?
To use certificates for VPN, you just need to do a couple things. Enroll end devices or security keys for Client Certificates. Upload a Root or Intermediate CA on your Firewall, VPN Gateway, or RADIUS Server.
What is remote access?
Remote access is incredibly convenient but also relies on employees having access to company data at home. There are protocols in place, like Windows Remote Desktop Protocol, that allow users to access their company’s network from anywhere.
How do I request remote access VPN?
You or an UC Davis Health employee will need to submit an "Online Access Request Form". Instructions can be found by selecting the VPN Request Procedure link. Once you have been authorized and account setup completed, you will receive instructions on where to get the client and how to install it on your computer.
What software do I need for remote Access VPN?
UC Davis Health uses the SSL based Cisco Secure Anyconnect Mobility client. Operating system native clients, PPTP, L2TP and so on are not supported.
What happens when you connect to a VPN server?
When you connect to a VPN server, it creates an encrypted tunnel for all your internet traffic to pass through. You also get an alternative IP address that your ISP cannot access.
Why do we need VPN?
A VPN can be used for many reasons, from cybersecurity to online privacy and unlocking geo-restricted content.
What is a VPN?
When you connect to the internet, you do so via your IP address. Your internet service provider (ISP) can track your browsing activity through your IP address. For example, an ISP can track what sites you visit, where and what you stream, etc.
What does VPN do for torrents?
With a VPN, you can ensure that your torrent files and the sites they are hosted on are safe. An encrypted connection on a VPN can also automatically block malware and ads.
What is VPN encryption?
Using encryption, a VPN provider turns your information into a secret code that is only accessible to authorized personnel.
Which is the best VPN?
ExpressVPN has been topping “Best VPN” lists for the last three years. It’s arguably the most popular choice for most users. This isn’t surprising considering its never-ending feature list that combines efficient security measures with protocols and server networks that provide lightning speeds.
Why do ISPs throttle connections?
ISPs also throttle connections to regulate network traffic and minimize bandwidth congestion. This practice is also known as traffic shaping.
What is a VPN client?
The VPN client may have a split-tunneling feature that allows your employer to choose what data goes through their network. Let’s say you use the following things in an average work day: A chat app like Slack or Skype. A browser to look up work-related info, use Google Docs, etc.
Can you use a laptop for remote work?
Using your personal laptop, PC, or phone for remote work can be a security and privacy nightmare. For one, you never know whether your devices are infected with some new strain of malware.
Can my employer see my traffic while using VPN?
Moreover, unauthorized acquisition of personal data can get your employer in trouble in all 50 states and unincorporated territories. If they don’t install any such software, then your employer should only see your traffic while connected to the company VPN.
Do corporate VPNs have tracking software?
You should always assume that your employer has installed some kind of tracking software on the company devices. Corporate VPNs also have a dashboard through which employers can monitor traffic passing through their network.
What is VPN firewall policy?
When connecting to a corporate network via VPN, you will be subject to company firewall policy. This policy denies access to websites that are deemed to be dangerous, controversial, inappropriate, or unproductive.
Can I make my printer work with a VPN?
David - I've never been able to make printers work over a VPN. They work a little differently than other network resources. You may also want to look at how your firewall is configured because that could be part of the issue too. Every network is different so its tough to say why this isn't working for you.
Why is it so hard to track a VPN?
It’s really difficult to track a VPN because your IP (Internet Protocol) address is changed and your online activity is encrypted. Some internet service providers (ISPs) or websites may know that you’re using a VPN, but they can’t see your actual online activity.
Where are VPN servers located?
The servers are usually located in two different countries, e.g., the UK and Australia. It further establishes secure internet connections, making it harder to access your data. Obfuscated servers.
How to avoid DNS leaks?
To avoid DNS leaks, use a VPN that provides you with their own DNS addresses. Doxxing. Doxxing is a malicious practice that people use to expose someone’s private information, like their home address or workplace. As you can see, an IP address isn’t the only identifier on the internet.
What happens if you don't use security software?
If you don’t use security software, you might end up getting your login credentials stolen.
Can you be tracked with a VPN?
If you use a VPN, your IP address is changed and your online activity is encrypted, so you cannot be tracked. Some internet service providers (ISPs) or websites may know that you’re using a VPN, but they can’t see your actual online activity. So, you should use a VPN to minimize your chances of being tracked online.
Is my real IP address visible?
IP address. Unless you use a VPN, a proxy, a Tor browser, or any other privacy protection tool, your real IP address is visible to websites you visit.
Is VPN safe from phishing?
Apart from anti-virus programs, we should also be cautious about suspicious links and emails. Phishing is as old as the internet. And no one is really safe from it because modern phishing tactics can be seamless.
