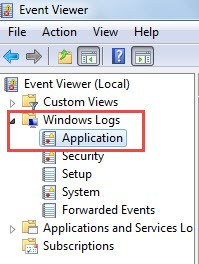
Event Viewer Access Remote Computer
- Log in to the local computer as an administrator.
- Start the Event Viewer. For example, on Windows 10 computer type Event Viewer in the search box ...
- You will be connected to the remote computer right away, but you may not have the rights to view the Event Viewer logs if you don’t connect to the remote ...
- Event Viewer cannot open the event log or custom view. Verify that Event Log service is running or query is too long ...
How to access the event viewer on a remote computer?
Accessing Remote Computer’s Event Viewer 1 Log in to the local computer as an administrator. 2 Start the Event Viewer. ... 3 You will be connected to the remote computer right away, but you may not have the rights to view the Event Viewer logs if you don’t connect to the remote ... More items...
How to view event log from another computer?
How to: Remote Event Log Viewing 1 Open Event Viewer as Admin. Hit start and type event viewer to search for the event viewer. ... 2 Connect to Another Computer 3 Enter the Remote Computer Name or IP. Enter the Remote Computer Name or IP and click OK to connect to it. 4 Browse the Remote Computer Logs. ...
What events appear in the Windows Event Viewer for RDP?
When a user remotely connects to the remote desktop of RDS (RDP), a whole number of events appears in the Windows Event Viewer. There are several different logs where you can find the information about Remote Desktop connections.
How do I view remote user activity in remote access?
You will see the list of users who are connected to the Remote Access server and detailed statistics about them. Click the first row in the list that corresponds to a client. When you select a row, the remote user activity is shown in the preview pane. Windows PowerShell equivalent commands
How do I see who is connected to my remote desktop?
If you want to know which types of connections are used to connect to the remote, simply click on any column of the list, say "Status," then right-click on it and select "Session." The list will then show a session column with the types of connections to remote, such as console, terminal, services, or RDP, and so on.
Can remote desktop be monitored?
A: YES, your employer can and has the right to monitor your Citrix, Terminal, and Remote Desktop sessions.
Is there a log file for RDP connections?
Outgoing RDP Connection Logs in Windows You can also view outgoing RDP connection logs on the client side. They are available in the following event log: Application and Services Logs -> Microsoft -> Windows -> TerminalServices-ClientActiveXCore -> Microsoft-Windows-TerminalServices-RDPClient -> Operational.
How can I tell if my employer is monitoring my computer?
Here are the methods to tell if your employer is monitoring your computer:Search for Suspicious Apps in Application Manager. ... Search for Suspicious Background Processes. ... Check Data Usage for Suspicious Activity. ... Search for Suspicious Programs. ... Check the Firewall Settings.
How do I monitor a remote user?
To monitor remote client activity and statusIn Server Manager, click Tools, and then click Remote Access Management.Click REPORTING to navigate to Remote Access Reporting in the Remote Access Management Console.More items...•
Where are Windows RDS logs stored?
How to collect logs. This file is located in the %windir%\Logs folder.
How do I check my RDP session timeout?
The settings of RDP session timeouts are located in the following GPO section Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Session Time Limits.
Has been disconnected reason code 5?
Code 5 is registered when a user connects to the machine, forcing the disconnection of another current connection. It could be the same username used or that the system simply does not support multiple concurrent sessions.
What is Event ID 1024?
This event is logged when Product Update could not be installed. Resolution. Review the system log file. Microsoft Windows Installer encountered an error while installing, updating, or removing an application. For more information about the error, you will need to open Event Viewer and examine the System log file.
How do I disable Wddm?
Even non-domain joined Windows machines can apply Group Policies locally. With the Group Policy Editor open, expand the editor's directory tree until you locate the Use WDDM graphics display driver for Remote Desktop Connections group policy. Double-click the WDDM group policy and disable it.
Question
We currently have users that login to a session on a Terminal Server 2008 via a 2008 R2 Gateway server, I was wondering whether there is a event log of each time we have to remote control a session?
Answers
In Server 2008 R2 there is more information logged relating to Remote Controls/shadowing. You can see when someone initiates a remote control as well as the target user, and if the remote control was successful or failed. The log does not show you whether or not the user was prompted to allow the remote control.
All replies
You can use TS Gateway Manager to view information about active connections from Terminal Services clients to internal corporate network resources through TS Gateway. This information includes:
Tips
Be aware that your computer may appear to turn on without input to install updates. Many modern computers are set to install system updates automatically, usually at night when the computer is not being used. If your computer appears to turn on without your input when you're not using it, it is likely waking from Sleep mode to install updates.
About This Article
This article was co-authored by Yaffet Meshesha and by wikiHow staff writer, Nicole Levine, MFA. Yaffet Meshesha is a Computer Specialist and the Founder of Techy, a full-service computer pickup, repair, and delivery service. With over eight years of experience, Yaffet specializes in computer repairs and technical support.
Example 1: PowerShell Eventlog on Local Computer
My learning progression is to get a basic example working on the local machine and then adapt the script to interrogate a remote computer.
Example 2: PowerShell Get-Eventlog on Remote Computer
Here is a modification of Example 1 which makes the script ready-to-run on a remote computer.
Example 3: PowerShell Get-Eventlog Remote EventID
PowerShell’s Get-Eventlog is tricky to operate. What makes it easier is focussing on the parameters, especially -Logname and for remoting, -ComputerName. Once you get the basics working there is a wealth of techniques and properties you can apply to this most versatile cmdlet.
Guy Recommends: A Free Trial of the Network Performance Monitor (NPM) v11.5
SolarWinds’ Network Performance Monitor will help you discover what’s happening on your network. This utility will also guide you through troubleshooting; the dashboard will indicate whether the root cause is a broken link, faulty equipment or resource overload.
Guy Recommends: SolarWinds Free Wake-On-LAN Utility
Encouraging computers to sleep when they’re not in use is a great idea – until you are away from your desk and need a file on that remote sleeping machine!
Further Research on PowerShell Get-Eventlog
To get the most out of Get-Eventlog even experts turn to the trusty PowerShell techniques of Get-Help and Get-Member. Once you understand the basics, there is huge enjoyment and satisfaction in getting the right script for the right job.
Research Get-Eventlog Parameters
Checking with Microsoft's help file will reveal useful parameters. Always remember to define the log with -logfile. I particularly like the -Newest, but for detailed research -before or -After maybe more useful.
Network Connection
This section covers the first indications of an RDP logon – the initial network connection to a machine.
Authentication
This section covers the authentication portion of the RDP connection – whether or not the logon is allowed based on success/failure of username/password combo.
Logon
This section covers the ensuing (post-authentication) events that occur upon successful authentication and logon to the system.
Logoff
This section covers the events that occur after a purposeful (Start -> Disconnect, Start -> Logoff) logoff.
Wrap-Up
Hopefully that provides a little better insight into some of the most common and (IME) most empirically useful RDP-related Event logs, when/where you might encounter them, what they mean, what they look like, and (most importantly) how they all fit together.
