
| Client Version | Operating System | Endpoint Security Client Build Number | Remote Access VPN Stand-alone Client Bui ... |
| E86.30 E86.30 | Windows Mac | 86.30.0145 86.30.1214 | 98.61.3820 98.62.0503 |
| E86.26 | Windows | 86.26.6008 | 98.61.3717 |
| E86.25 | Windows | 86.25.5060 | 98.61.3717 |
| E86.20 | Windows MacOS | 86.20.0119 86.20.1113 | 98.61.3717 98.62.0408 |
Full Answer
How to enable 2FA for checkpoint VPN endpoint security?
To configure the Security Gateway for Remote Access:
- In R80 SmartConsole, click Gateways & Servers and double-click the Security Gateway. ...
- From the navigation tree, click IPsec VPN. ...
- To add the Security Gateway to a community: Click Add. ...
- From the navigation tree, click Network Management > VPN Domain.
- Configure the VPN Domain.
- Configure the settings for Visitor Mode.
How to bypass checkpoint endpoint security?
from Check Point, Inc
- Overview. Check Point Endpoint Security is a software program developed by Check Point, Inc. ...
- Program details. URL: www.checkpoint.com (The Windows Installer is used for the installation, maintenance, and removal.)
- Files installed by Check Point Endpoint Security. ...
- Behaviors exhibited. ...
- Windows. ...
- Geography. ...
- PC manufacturers. ...
What to look for in Endpoint Security?
Malware Threats
- Virus. This type of malware infects existing files on your device and copies itself each time an infected program is executed.
- Worm. Worms are like viruses that don’t need any existing files or programs to multiply itself within your system.
- Bot. Bots are used to automate a task online that a user would ordinarily perform. ...
- Trojan. ...
How to check VPN tunnel uptime in checkpoint?
- Non-English Discussions
- Español
- Français
- Português
- Russian
- Taiwan 論壇
- Japanese 日本語
- Member Exclusives Exclusive Content CPX 360 2021 Content R8x Training Videos
- Message Views Recent Messages Recent Threads
- Contests How-To Video Contest CheckMates Everywhere
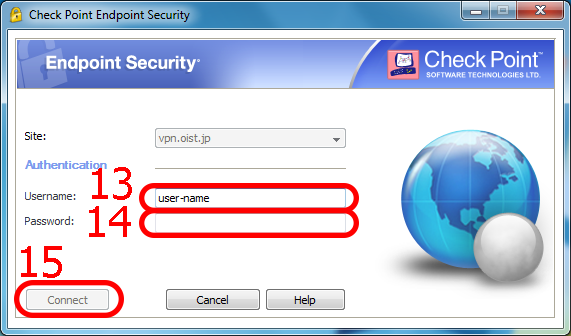
What is Check Point Endpoint Security VPN?
Check Point endpoint security includes data security, network security, advanced threat prevention, forensics, endpoint detection and response (EDR), and remote access VPN solutions.
What is remote access VPN Check Point?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
How do you check VPN on Check Point?
0:0710:3510.Check Point Remote Access VPN. VPN users monitoring - YouTubeYouTubeStart of suggested clipEnd of suggested clipВозможно вы хотите оценить. Если у вас еще запас по подключением в рамках текущей лицензии напомнюMoreВозможно вы хотите оценить. Если у вас еще запас по подключением в рамках текущей лицензии напомню что лицензии конкурентной то есть они считают только. Одновременных подключений у вас может быть.
Is Check Point a VPN?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
How do I configure Check Point VPN?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
How does Checkpoint Firewall work?
The Check Point firewall will control IP forwarding by enabling it after its services are started. The firewall also loads a default filter during the boot process, which essentially denies all inbound traffic but allows outbound traffic.
How do I change my Checkpoint VPN password?
To change your User Center password:Log into the User Center at https://usercenter.checkpoint.com/usercenter/index.jsp.Click "Assets/Info".Click "My Profile" under "My Info" option.Click "Change Password" button.Enter your old password.Enter your new password.Confirm your new password.More items...•
How do I enable MFA in Checkpoint firewall?
Configure 2FA/MFA for End-Users To enable 2FA/MFA for Check Point VPN endusers, go to 2-Factor Authentication >> 2FA Options For EndUsers. Select default Two-Factor authentication method for end users.
What is the difference between site to site VPN and remote access VPNS?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Who makes Check Point VPN?
Check Point Software Technologies Ltd. For the last three decades, Check Point Software Technologies Ltd. (www.checkpoint.com) has set the standard for Cyber Security.
Is Cisco secure Endpoint a VPN?
It not only provides VPN access through Secure Sockets Layer (SSL) and IPsec IKEv2 but also offers enhanced security through various built-in modules.
What ports does Checkpoint VPN use?
You must change the default remote access port if the Check Point VPN client, Mobile client, or SSL VPN remote access methods are enabled as they use port 443 by default.
How does f5 VPN Work?
IPsec VPN – Establishes a VPN over the public Internet using the standard IPsec mechanism. SSL VPN – Uses Secure Sockets Layer protocol, an authentication and encryption technology built into every web browser, to create a secure and encrypted connection over a less secure network, like the Internet.
What is a VPN connection?
A VPN, which stands for virtual private network, is a service that establishes a secure and private connection to the internet. A VPN creates an encrypted tunnel to protect your personal data and communications, hide your IP address, and let you safely use public Wi-Fi networks.
What is remote access VPN?
For a relatively low price, a remote secure access VPN helps both small and medium-sized businesses give their remote workers secure and convenient access to the company’s private servers and reduce a possible exposure to cyberattacks.
What is VPN benefit?
VPN Benefits. Encryption of all transmitted data can be done within in a single session between the client and server using TLS. This is the widely used client to server standard used to secure web traffic to banks, hospitals, web search, etc. Another method is to create a Virtual Private Network ...
Why do businesses use VPN?
The end result is the same. Businesses use remote secure access VPN to make sure the connections between their networks, offices and remote devices are secure. The main advantage of remote secure access is the ability to provide individual users a way to remotely and securely connect to a computer network through an encrypted tunnel ...
