Remote Access Solution Comparison
| Layer 3 VPN Tunnel Clients | Supported Operating Systems | Client or Clientless | Encryption Protocol | Security Verification for Endpoint Devic ... |
| Capsule Connect for iOS (previously Mobi ... | iOS | Client | IPsec / SSL | MDM Cooperative Enforcement (sk98201) |
| Capsule VPN for Android (previously Mobi ... | Android | Client | IPsec /SSL | MDM Cooperative Enforcement (sk98201) |
| Check Point VPN Plugin for Windows 8.1 | Windows 8.1 | Pre- installed client | SSL | |
| Check Point Capsule VPN for Windows 10 | Windows 10 | Client | SSL |
Full Answer
How to secure your remote access?
- In-session file transfer
- Out-of-session file transfer
- Remote print
- Text copy/paste
- Remote wake
- Remote Reboot
- Out-of-session chat
- Session recording
- Concurrent remote sessions
- Remote command
How can I access my PC remotely?
On a computer running Windows 10 Pro or Enterprise follow these steps:
- Click the Start button on the bottom left of your screen.
- Hit the Settings button on the left-hand side.
- Click on System.
- Now select Remote Desktop, and turn on Enable Remote Desktop.
- Make a note of the name of this PC as it appears under How to connect to this PC. ...
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
How to protect remote access?
To enable Remote Access in your UniFi Protect application:
- Access the UniFi OS Console hosting Protect via its IP address. ...
- Log in to your Ubiquiti SSO account.
- Go to the System Settings > Advanced menu, and enable the Remote Access toggle.
See more
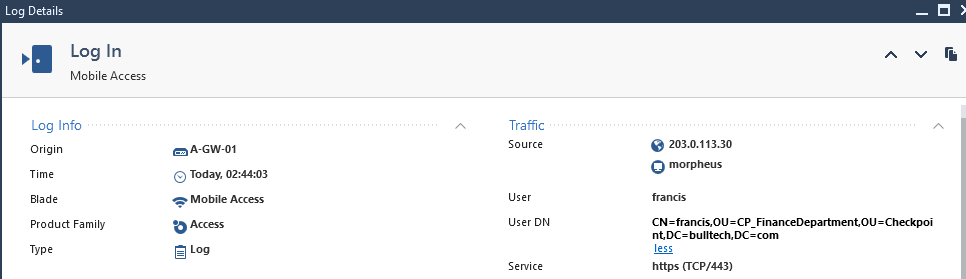
What is Checkpoint VPN used for?
A secure, encrypted connection between networks and remote clients on a public infrastructure, to give authenticated remote users and sites secured access to an organization's network and resources.
What is Checkpoint mobile client?
Check Point Mobile Access is the safe and easy solution to securely connect to corporate applications over the Internet with your Smartphone, tablet or personal computer (PC). Mobile Access allows remote and mobile workers to simply and securely connect to email, calendar, contacts and corporate applications.
How do I install Checkpoint VPN?
Installation InstructionsStep 1: Download Checkpoint VPN E84.30. Download and save the VPN client installation file from this link. ... Step 2: Remove currently installed version. To uninstall the currently installed version of Check Point VPN Client: ... Step 3: Install new version.
How do I use checkpoint Mobile VPN?
0:1010:30Check Point Remote Access VPN Setup and Config - YouTubeYouTubeStart of suggested clipEnd of suggested clipNow as i mentioned it's really easy and simple to set up the vpn. There's a little tab on the leftMoreNow as i mentioned it's really easy and simple to set up the vpn. There's a little tab on the left hand side which says vpn. And then you're left with three sections. Which is remote.
Is Check Point a VPN?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
Is endpoint security a VPN?
Check Point endpoint security includes data security, network security, advanced threat prevention, forensics, endpoint detection and response (EDR), and remote access VPN solutions.
How does Checkpoint Firewall work?
The Check Point firewall will control IP forwarding by enabling it after its services are started. The firewall also loads a default filter during the boot process, which essentially denies all inbound traffic but allows outbound traffic.
What is a remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is the difference between site to site VPN and remote access VPNS?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What is mobile checkpoint operation?
A mobile checkpoint is a test operation that checks whether the specified UI element is displayed on the mobile device screen. In image-based tests, this may be necessary if you want to ensure that a control is visible on screen before simulating user actions over it.
What is mobile access control?
What Is a Mobile Access Control System? Mobile access control takes mobile phones, smartphones, tablets, and wearable electronic devices and allows them to function as a user's credentials to enter offices or other business facilities.
What is the difference between SSL VPN and IPsec VPN checkpoint?
Whereas an IPsec VPN enables connections between an authorized remote host and any system inside the enterprise perimeter, an SSL VPN can be configured to enable connections only between authorized remote hosts and specific services offered inside the enterprise perimeter.
Where is the license for Check Point mobile users installed?
The Check Point Mobile client offers an Office Mode IP. This client uses the Mobile Access blade license on the gateway itself. By default, a gateway comes with a license for 5 users. Then you can attach a larger blade if more users are required.
What is Check Point Mobile?
Check Point Mobile for Windows is an IPsec VPN client. It is best for medium to large enterprises that do not require an Endpoint Security policy.
What is endpoint security suite?
The Endpoint Security Suite simplifies Endpoint Security Management by unifying all endpoint security capabilities in a single console and a single client. Endpoint Security Software Blades include: Desktop Firewall and Security Verification, Full Disk Encryption, Media Encryption and Port Protection, SandBlast Agent, Anti-Malware and Program Control, WebCheck browser virtualization and Remote Access VPN.
What is mobile access portal?
Introduction. The Mobile Access Portal is a clientless SSL VPN solution. It is recommended for users who require access to corporate resources from home, an internet kiosk, or another unmanaged computer. The Mobile Access Portal can also be used with managed devices.
Does Check Point Mobile support two factor authentication?
Check Point Mobile for Windows, Check Point VPN Plugin for Windows 8.1 and Check Point Capsule VPN for Windows 10 do not support "two factor user authentication". (The limitation applies only to E80.64 and earlier in the context of Check Point Mobile for Windows.)
Is remote access a weak point?
Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
Does Endpoint Security VPN include firewall?
Note: Endpoint Security VPN for Mac OS X includes a Desktop Firewall, but not Security Verification.
What is checkpoint remote access?
Check Point remote access solutions use IPsec and SSL encryption protocols to create secure connections. All Check Point clients can work through NAT devices, hotspots, and proxies in situations with complex topologies, such as airports or hotels. These are the types of installations for remote access solutions:
What is secure connectivity?
Secure Connectivity - Traffic is encrypted between the client and VPN Security Gateway. After users authenticate, they can access the corporate resources that are permitted to them in the access policy. All Check Point solutions supply this.
What is security verification?
Security Verification for Endpoint computers - Makes sure that devices connecting to the Security Gateway meet security requirements. Endpoint machines that are not compliant with the security policy have limited or no connectivity to corporate resources. Some Check Point solutions supply this.
What is client based application?
Client-based - Client application installed on endpoint computers and devices. The client supplies access to most types of corporate resources according to the access privileges of the user.
What is an on demand client?
On demand client - Users connect through a web browser and a client is installed when necessary. The client supplies access to most types of corporate resources according to the access privileges of the user.
Is remote access a weak point?
Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
Can you combine secure connectivity with additional features to protect the network or endpoint computers?
You can combine secure connectivity with additional features to protect the network or endpoint computers.
What is endpoint security VPN?
Endpoint Security VPN combines Remote Access VPN with Endpoint Security in a client that is installed on endpoint computers. It is recommended for managed endpoints that require a simple and transparent remote access experience together with Desktop Firewall rules. It includes:
Is remote access a weak point?
Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
What is odo access?
Odo is a leading player in the Zero Trust Network Access space, introducing a seamless way to securely connect to any organizational resource, hosted anywhere, through any device, from any location. Odo’s solution, OdoAccess, is a centralized clientless and agentless SaaS platform that can be deployed in minutes. It enhances security by blocking any unauthorized access, eliminating all network layer access and preventing lateral movement within the organization. OdoAccess also provides full visibility on all user activity, including the ability to create complex policies and block user actions in real-time
What is zero trust architecture?
Zero Trust Architecture to define granular access policy to give the right people in the right context, the least privileged access to applications and reduce the attack surface.
What is checkpoint mobile access?
Check Point Mobile Access is the safe and easy solution to securely connect to corporate applications over the Internet with your Smartphone, tablet or PC. Integrated into the Check Point Next Generation Firewalls (NGFW), Mobile Access provides enterprise-grade remote access via both Layer-3 VPN and SSL/TLS VPN, allowing you to simply and securely connect to your email, calendar, contacts and corporate applications.
What is check point security?
Security teams must be able to isolate, secure, and control every device on the network at all times . Check Point solutions provide you with the ability to block infected devices from accessing corporate data and assets, including employees’ mobile devices and workstations, IoT devices and Industrial Control Systems. Integrated into the Check Point Infinity Architecture, Mobile Access secures connections to corporate applications over the Internet with your Smartphone, tablet or PC.
What is easy access for mobile workers?
Easy access for mobile workers – simply connect from mobile devices to secure connectivity for smartphones, tablets, PCs and laptops
What is mobile access?
Mobile Access can be configured to send a One-Time Password (OTP) to an end-user communication device (such as a mobile phone) via an SMS message. Or even with SMS two-factor authentication providing an extra level of security while eliminating the difficulties associated with managing hardware tokens.
What is a remote access VPN community?
By default, the Remote Access VPN Community includes a user group, All Users, that includes all defined users. You can use this group or add different user groups to the Remote Access VPN Community. The community can contain users defined in LDAP, which includes Active Directory, or users defined on the Security Management Server.
Which service defines the protocol and port of client connections to the gateway?
Optional - Select the Visitor Mode Service, which defines the protocol and port of client connections to the gateway.
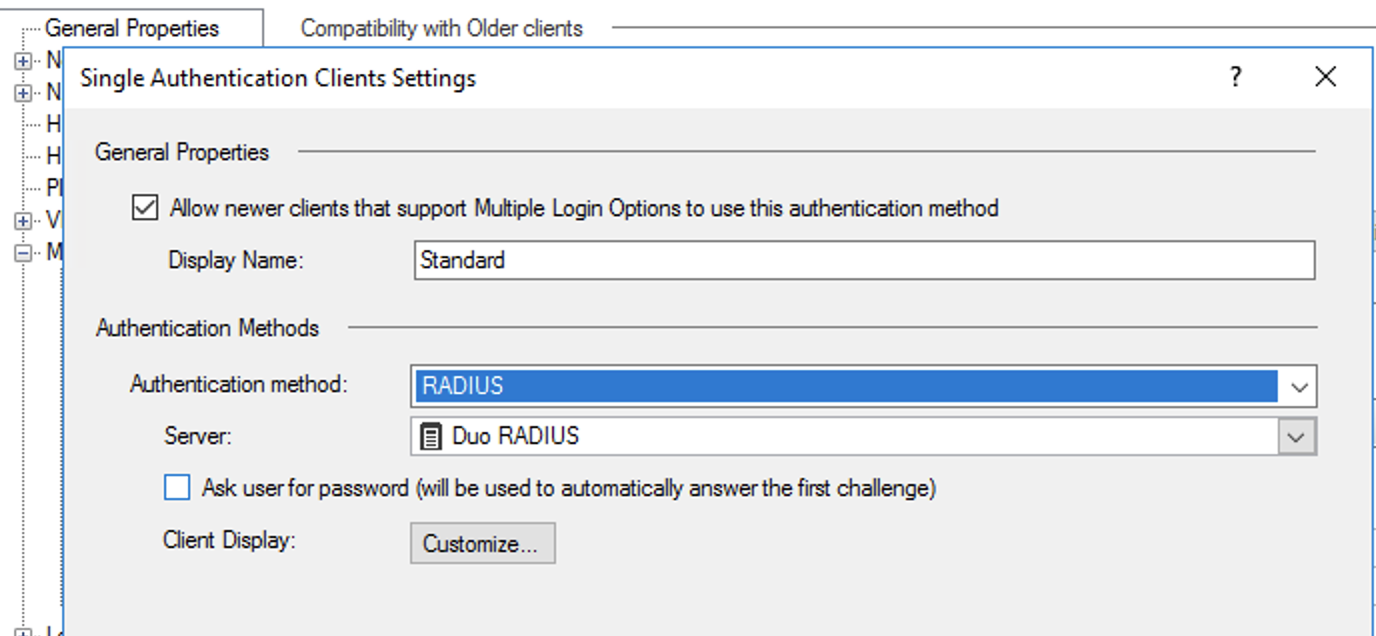
What happens when no authentication methods are defined for the gateway?
If no authentication methods are defined for the gateway, users select an authentication method from the client.
How to enable IPsec VPN?
From SmartConsole, use the Gateways & Servers menu to configure the gateway and blades. Double-click the gateway. The Check Point Gateway window opens. In the Network Security tab at the bottom, select I Psec VPN to enable the blade.