From the Check Point Gateway tree, click Network Management. In VPN Domain, click Set domain for Remote Access Community. Configure Visitor Mode. Select IPSec VPN > VPN Clients > Remote Access. Select Support Visitor Mode and keep All Interfaces selected.
Full Answer
How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
How to speed up VPN remote access?
How to speed up a VPN
- Choose another server. Connecting to your nearest server will usually offer the best performance, but there are occasional exceptions.
- Refresh your system. If speeds are notably worse than unusual with several servers, the problem could be closer to home. ...
- Switch protocol. ...
- Tweak protocol settings. ...
- Use a wired connection. ...
- Try split tunneling. ...
How to activate open VPN?
- Right-click the Start button.
- Click Settings. Source: Windows Central
- Click Network & Internet.
- Click VPN. Source: Windows Central
- Click Add a VPN connection.
- Click the dropdown menu below VPN provider. Source: Windows Central
- Click Windows (built-in).
- Click the Connection name field. ...
- Type a name for the VPN connection. ...
- Click the Server name or address field. ...
Can connect to VPN, cannot access remote resources?
If you cannot access some resources using only the VPN (e.g., it’s behind a departmental firewall), Millward said you should connect to the GlobalProtect client first to verify your identity, then use your preferred remote access management client.

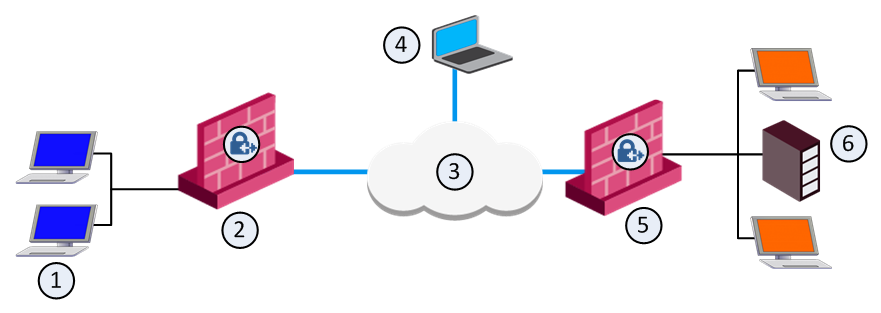
What is remote access VPN checkpoint?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
How do you check VPN on checkpoint?
0:0710:3510.Check Point Remote Access VPN. VPN users monitoring - YouTubeYouTubeStart of suggested clipEnd of suggested clipВозможно вы хотите оценить. Если у вас еще запас по подключением в рамках текущей лицензии напомнюMoreВозможно вы хотите оценить. Если у вас еще запас по подключением в рамках текущей лицензии напомню что лицензии конкурентной то есть они считают только. Одновременных подключений у вас может быть.
How do I download Check Point VPN client?
Follow these instructions in order to install the latest version:Step 1: Download Checkpoint VPN E84.30. Download and save the VPN client installation file from this link. ... Step 2: Remove currently installed version. To uninstall the currently installed version of Check Point VPN Client: ... Step 3: Install new version.
What is mobile checkpoint VPN?
Check Point Mobile VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using the L3 IPSec/SSL VPN Tunnel. The application is available in the Google Play Store: https://play.google.com/store/apps/details? id=com.checkpoint.VPN&hl=en.
What type of VPN is Check Point?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
How do I change my CheckPoint VPN password?
To change your User Center password:Log into the User Center at https://usercenter.checkpoint.com/usercenter/index.jsp.Click "Assets/Info".Click "My Profile" under "My Info" option.Click "Change Password" button.Enter your old password.Enter your new password.Confirm your new password.More items...•
Who makes Checkpoint VPN?
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks.
What is a VPN endpoint?
VPN goes between a computer and a network (client-to-server), or a LAN and a network using two routers (server-to-server). Each end of the connection is an VPN "endpoint", the connection between them is a "VPN tunnel".
What is Check Point Endpoint Security?
Check Point Endpoint Security™ is the first single agent for total endpoint security that combines the highest-rated firewall, network access control (NAC), program control, antivirus, anti-spyware, data security, and remote access.
How do I use checkpoint mobile VPN?
5:5410:30Check Point Remote Access VPN Setup and Config - YouTubeYouTubeStart of suggested clipEnd of suggested clipUp. We click trust. And continue then it's going to ask you what vpn client you're going to use theMoreUp. We click trust. And continue then it's going to ask you what vpn client you're going to use the default. One we're going to use a username and password. And then we click finish.
How do I configure site to site VPN in Checkpoint firewall?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
What is Checkpoint mobile access?
Check Point Capsule Connect and Capsule VPN (for iOS and Android) Check Point Connect for iOS and Capsule VPN for Android are simple client-to-site VPN clients available on mobile devices. Simply set up the site and connections to assets protected by the site gateway are secured by an IPsec or SSL VPN.
How check VPN tunnel status Checkpoint r80?
Click Logs & Monitor > New Tab. From the bottom of the window, click Tunnel and User Monitoring. Click the gateway to see IPsec VPN traffic and tunnels opened.
How do I troubleshoot Checkpoint VPN?
Things to look for when troubleshooting a Checkpoint VPN connection:VPN domains. Review setup in the topology of an item. ... Encryption Domains. Your firewall contains your networks. ... Rule Setup. ... Pre-shared secret or certificate. ... RuleSet. ... Address Translation. ... TRADITIONAL MODE NOTES. ... SIMPLIFIED MODE NOTES.More items...•
What is a VPN endpoint?
VPN goes between a computer and a network (client-to-server), or a LAN and a network using two routers (server-to-server). Each end of the connection is an VPN "endpoint", the connection between them is a "VPN tunnel".
How do I know if my Ispsec tunnel monitoring is working?
To check if the tunnel monitoring is up or down, use the following command:> show vpn flow.id name state monitor local-ip peer-ip tunnel-i/f.------------------------------------------------------------------------------------1 tunnel-to-remote active up 10.66.24.94 10.66.24.95 tunnel.2.More items...•
Client- Security Gateway Authentication Schemes
Authentication is a key factor in establishing a secure communication channel among Security Gateways and remote clients. Various authentication methods are available, for example:
Multiple Login Options for R80 .xx Gateways
On Mobile Access and IPsec VPN Security Gateways that run R80.10 and higher versions, you can configure multiple login options. The options can be different for each Security Gateway and each supported Software Blade, and for some client types. Users select one of the available options to log in with a supported client.
Internal User Database vs. External User Database
Remote Access functionality includes a flexible user management scheme. Users are managed in a number of ways:
Defining User and Authentication Methods in LDAP
Obtain and install a license that enables the VPN module to retrieve information from an LDAP server.
Using a Pre-Shared Secret
When using pre-shared secrets, the remote user and Security Gateway authenticate each other by verifying that the other party knows the shared secret: the user's password.
Working with RSA Hard and Soft Tokens
If you use SecurID for authentication, you must manage the users on RSA's ACE management server. ACE manages the database of RSA users and their assigned hard or soft tokens. The client contacts the site's Security Gateway. The Security Gateway contacts the ACE Server for user authentication information. This means:
Enabling Hybrid Mode and Methods of Authentication
Hybrid mode allows the Security Gateway and remote access client to use different methods of authentication.
Check Point Remote Access VPN Pricing Advice
"My understanding is that the pricing and licensing are very competitive, and it's not one of their more expensive products. We buy licenses for the solution and have licenses for the endpoint servers."
Check Point Remote Access VPN Reviews
We use a Check Point Endpoint Remote Access VPN client along with Check Point SSL VPN, which allows users to connect to our firewall who don't have the client, e.g., if they have a MacBook, then we don't have a client for them. We allow them to connect to the firewall over the browser.
Scenario description
In this tutorial, you configure and test Azure AD SSO in a test environment.
Adding Check Point Remote Secure Access VPN from the gallery
To configure the integration of Check Point Remote Secure Access VPN into Azure AD, you need to add Check Point Remote Secure Access VPN from the gallery to your list of managed SaaS apps.
Configure and test Azure AD SSO for Check Point Remote Secure Access VPN
Configure and test Azure AD SSO with Check Point Remote Secure Access VPN using a test user called B.Simon. For SSO to work, you need to establish a link relationship between an Azure AD user and the related user in Check Point Remote Secure Access VPN.
Configure Check Point Remote Secure Access VPN SSO
This section is needed only if you do not want to use an on-premises Active Directory (LDAP).
Next steps
Once you configure Check Point Remote Secure Access VPN you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.
Setting up Remote Access VPN in Check Point
Open the Check Point Security Gateway object settings in the VPN Clients/Mobile Access -> Authentication section:
Configure new Access Role
Under objects section select New > More > User > Access Role. Set the parameters for the new object and specify the source of user data.
Configure Access Policy
Under Security Policies > Policy > create a new policy for Remote Access VPN users to access the internal network:
