
What is check point remote secure access VPN?
Check Point Remote Secure Access VPN provides users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. You can enable two-factor authentication (2FA) for your Check Point SSL VPN managed active directory to increase the security level.
How to configure 2fa/mfa for Check Point VPN end-users?
Configure 2FA/MFA for End-Users To enable 2FA/MFA for Check Point VPN endusers, go to 2-Factor Authentication >> 2FA for end users. Select default Two-Factor authentication method for end users.
How do I enable multi-factor authentication in check point security gateway?
Open the Check Point Security Gateway object settings in the VPN Clients/Mobile Access -> Authentication section: Use Username and Password as a first factor and RADIUS (Multifactor) as the second factor; Use RADIUS (Multifactor) as the first and second factors.
Does checkpoint VPN with Microsoft 2-factor authenticat use cookies?
Checkpoint VPN with Microsoft 2-Factor Authenticat... - Check Point CheckMates This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies. Now Available on CheckMates for Beginners! Start Learning! Checkpoint VPN with Microsoft 2-Factor Authenticat...
Can you use MFA with RDP?
On the highest level, multi factor authentication can be added on top of RDP by using: A multi factor authentication vendor/product such as Duo Security, OKTA MFA, … and many more; Using an external Identity Provider (IdP) and the MFA services linked to this IdP.
What is MFA remote access?
Multi-factor authentication (MFA) is a more secure access control procedure that combines multiple credentials unique to an individual to verify the user's identity.
How do I enable two factor authen?
How do I enable 2FA?Go to the ACCOUNT page.Click the PASSWORD & SECURITY tab.Under the 'TWO-FACTOR AUTHENTICATION' header, click the 2FA option you want to enable: THIRD-PARTY AUTHENTICATOR APP: Use an Authenticator App as your Two-Factor Authentication (2FA). ... Verify that 2FA is enabled.
What is the point of two factor authentication?
Two factor authentication (2FA) can improve security for anyone using an online service or accessing corporate resources. Basically, it requires the user to provide two different types of information to authenticate or prove they are who they say they are before access is granted.
Is VPN multi-factor authentication?
Use Multi-Factor Authentication (MFA) to Secure VPN MFA prevents attackers from accessing your account even if they obtain your username and password. For example, if you create a multi-layered mechanism, an unauthorized user would have to defeat all layers to gain access.
How do I secure my remote desktop connection?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
How can I get verification code without phone?
0:172:06Use 2-Step Verification without your phone - YouTubeYouTubeStart of suggested clipEnd of suggested clipYou can generate a set of ten backup codes on the security. Section of your account page. They workMoreYou can generate a set of ten backup codes on the security. Section of your account page. They work just like the codes you receive on your phone.
How do I get the 6 digit code from Authenticator app?
To receive a one-time-passcode on your cellphone via text message, click Send Code Check your cellphone. You should have received a text message like the image below with a 6-digit verification code: Enter the 6-digit code received via text message on the Extranet login site Click Verify Code.
How do I login to Instagram if I lost my phone with two-factor authentication?
If you have waited until your phone gets lost and have not written down the one-use codes provided earlier, then there are some solutions for you. – Get help from Instagram support: If you have the Instagram username and password, contact Instagram and ask them to recover your account. This might take a few days.
What's a potential downside of using 2FA?
The only real drawback of 2FA is time. It takes time to set up and extra time to login. Also, one of the most common forms of backup — a code sent as a text message — isn't as secure as it should be. Hackers can steal your phone number and redirect codes so that they can access your accounts.
Can you bypass 2 step verification?
Hackers can now bypass two-factor authentication with a new kind of phishing scam. Two-factor authentication, the added security step that requires people enter a code sent to their phone or email, has traditionally worked to keep usernames and passwords safe from phishing attacks.
What is more secure than 2FA?
First: All other things being equal, MFA is always more secure than 2FA. 2FA is MFA, but not all MFA is 2FA.
What is MFA Azure?
Azure AD multifactor authentication (MFA) helps safeguard access to data and apps while maintaining simplicity for users. It provides additional security by requiring a second form of verification and delivers strong authentication through a range of easy-to-use validation methods.
How do I enable MFA on RDS?
To configure integration of Azure AD MFA with RDS, you need to specify the use of a central store. On the RD Gateway server, open Server Manager. On the menu, click Tools, point to Remote Desktop Services, and then click Remote Desktop Gateway Manager.
Is UserLock a decision?
UserLock is a great software that allows us to verify each users' identity, stop password sharing and help avoid security breaches. In a flash, I can control my users' login experience, find/identify users computers and remote in for support.
Does SecureLink use MFA?
SecureLink Integrations | LDAP/AD, CRM, MFA, PAM & SAML.
What is 2FA authentication?
Two factor authentication (2FA) can improve security for anyone using an online service or accessing corporate resources. Basically, it requires the user to provide two different types of information to authenticate or prove they are who they say they are before access is granted. Remote Access Demo. Authentication Factors.
How to set up 2FA?
For SMS or email-based 2FA, the only setup requirement is to provide a phone number or email address to send codes to. For TOTP-based 2FA, installation of an authenticator app (like Authy or Google Authenticator) or the use of a USB-based security key may be necessary.
How Does Two Factor Authentication (2FA) Work?
2FA works by presenting a login page that requires multiple input requests to a user. Commonly, this is a request for a password and a one-time access code.
What is check point?
Check Point offers easy solutions for deploying 2FA across your organization. This includes support for secure remote access and secure access service edge (SASE) solutions. To see Check Point solutions in action, please request a demonstration.
What happens when a user attempts to log into a service?
If a user attempts to log into a service, they provide the current value provided by their authentication device to the site, which compares it to its current value and authorizes the connection if they match. However, the space of possible values is large enough that an attacker is extremely unlikely to guess the correct code while it is still valid.
Is 2FA good for consumers?
Two-factor authentication is not only beneficial for consumers. Enabling 2FA for access to corporate resources can help to protect against the impacts of compromised user passwords, especially in this remote work world.
Is a one time access code secure?
This one-time access code can be acquired in a number of ways. One common option is to have it sent as an SMS or email. However, this approach is less secure because it is vulnerable to interception or SIM-swapping attacks.
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
Setting up Remote Access VPN in Check Point
Open the Check Point Security Gateway object settings in the VPN Clients/Mobile Access -> Authentication section:
Configure new Access Role
Under objects section select New > More > User > Access Role. Set the parameters for the new object and specify the source of user data.
Configure Access Policy
Under Security Policies > Policy > create a new policy for Remote Access VPN users to access the internal network:
Who can define which method will be used in the Microsoft portal?
The user can define which method will be used in the Microsoft portal.
When did Microsoft stop offering MFA?
I saw in some posts that this was possible by using MFA Server, but Microsoft stopped offering MFA Server on July 1, 2019. 1 - Office 365 users with MFA enabled. 2 - Dedicated NPS Server. All Radius requests made to this server will have MFA directed to Microsoft.
Does Radius have MFA?
All Radius requests made to this server will have MFA directed to Microsoft.
Is NPS Extension good for Azure MFA?
So for sites that have Remote Access users relying on Secondary Connect to access resources distributed across the globe using the NPS Extension for Azure MFA is not the best user experience.
What is checkpoint VPN?
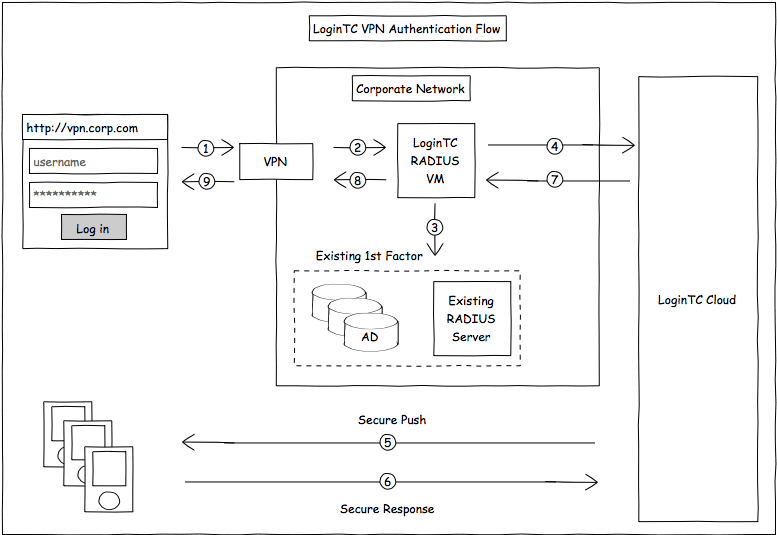
Check Point Remote Secure Access VPN provides users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. You can enable two-factor authentication (2FA) for your Check Point SSL VPN managed active directory to increase the security level. When you enable 2FA, your users enter their username and password (first factor) as usual, and as a second factor they have to enter an authentication code which will be shared virtually on their device or in the form of a hardware token. This 2FA/MFA solution adds an additional security measure to prevent unwanted users getting access to your Check Point SSL VPN access.
What happens when a user's first level of authentication gets validated?
Once the user's first level of authentication gets validated AD sends the confirmation to RADIUS Server.
What is primary authentication?
Primary authentication initiates with the user submitting his Username and Password for Check Point VPN.
Can admin change the second factor of the end user from the user list?
Admin can change the second factor of the End user from the User List.
What is a secret in authentication?
A secret to be shared between the Authentication Proxy and your existing RADIUS server. If you're on Windows and would like to encrypt this secret, see Encrypting Passwords in the full Authentication Proxy documentation.
How to use LDAP as primary authenticator?
To use Active Directory/LDAP as your primary authenticator, add an [ad_client] section to the top of your config file. Add the following properties to the section:
Where is the duo authentication proxy located?
The Duo Authentication Proxy configuration file is named authproxy.cfg, and is located in the conf subdirectory of the proxy installation. With default installation paths, the proxy configuration file will be located at:
How does Duo Push work?
Once configured, Duo sends your users an automatic authentication request via Duo Push notification to a mobile device or phone call after successful primary login.
What port is Radius preconfigured for?
The NEW-RADIUS service is preconfigured by Check Point for UDP port 1812. If you configured the Duo Authentication Proxy to use a different port, you will need to modify the existing RADIUS or NEW-RADIUS services or create a new service to use your desired port. Please refer to the Security Gateway Technical Administration Guide for your Check Point release.
What is the authproxyctl executable?
Authentication Proxy v5.1.0 and later includes the authproxyctl executable, which shows the connectivity tool output when starting the service. The installer adds the Authentication Proxy C:Program FilesDuo Security Authentication Proxybin to your system path automatically, so you should not need to specify the full path to authproxyctl to run it.
How much RAM is needed for Duo authentication?
The Duo Authentication Proxy can be installed on a physical or virtual host. We recommend a system with at least 1 CPU, 200 MB disk space, and 4 GB RAM (although 1 GB RAM is usually sufficient).
