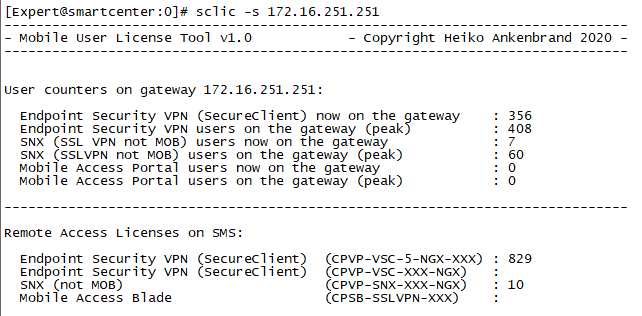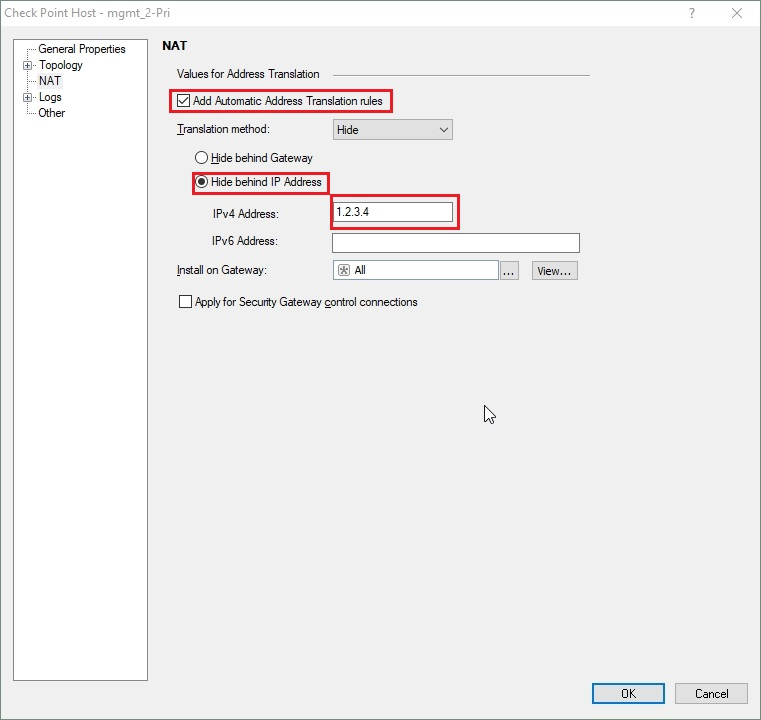
Configuring Check Point VPN Clients to split tunnel Office 365 traffic Open SmartConsole and go to Global Properties > Remote Access > Endpoint Connect. Change Route all traffic to gateway to No. Click OK.
- In SmartConsole, in the Objects tree, select New > More > Server> More> SecuRemote DNS. ...
- In the General tab, enter a name for the server and select the host on which it runs.
- In the Domains tab, click Add to add the domains that will be resolved by the server.
How do I set up the check point Remote Access Gateway?
The Check Point Gateway window opens. In the Network Security tab at the bottom, select I Psec VPN to enable the blade. Note - Some clients also require the Mobile Access blade. See the Required Licenses for your client in Check Point Remote Access Solutions. Add the gateway to the Remote Access VPN Community.
How do I configure Visitor mode in check point VPN?
Configure Visitor Mode. From the Check Point Gateway tree, select VPN Clients > Remote Access. Select Support Visitor Mode. In Machine's Interface, keep All Interfaces selected. Optional - Select the Visitor Mode Service, which defines the protocol and port of client connections to the gateway.
What is check point IPsec VPN?
Check Point Mobile for Windows - An easy to use IPsec VPN client to connect securely to corporate resources. Together with the Check Point Mobile clients for iPhone and Android, and the Check Point SSL VPN portal, this client offers a simple experience that is primarily targeted for non-managed machines.
How do I configure remote access clients with VPN configuration utility?
To learn how to implement the above options, refer to the E80.71 Remote Access Clients Administration Guide. Download the VPN Configuration Utility for Endpoint Security sk122574 zip file and extract VPNConfig.exe and features.xml to the same folder. Double-click on VPNConfig.exe to start working with the tool.
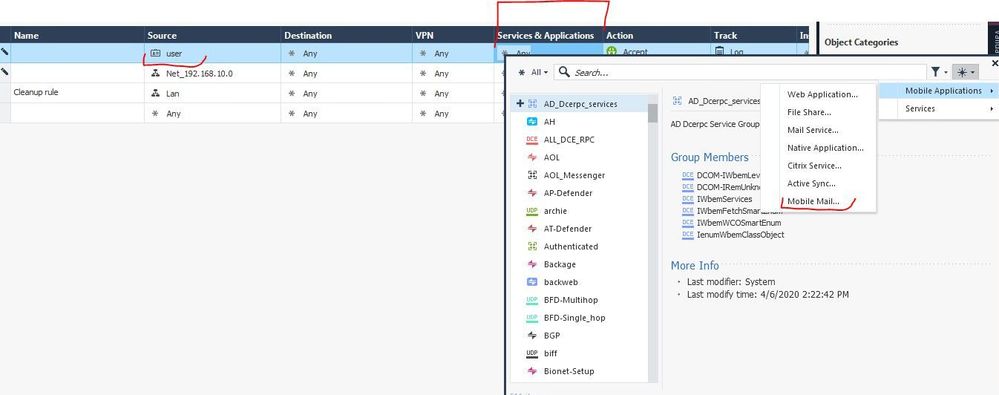
How do I configure Check Point VPN client?
Go to VPN > Authentication Servers. Click Configure to add a RADIUS server. See Configuring Remote Access Authentication Servers. Click permissions for RADIUS users to set access permissions....Configuring Remote Access VPNCheck Point VPN clients.Check Point Mobile clients.Check Point SSL VPN.L2TP VPN client.
What is remote access VPN Check Point?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
How do I enable visitor mode in Check Point?
Configure Visitor Mode.Select IPSec VPN > VPN Clients > Remote Access.Select Support Visitor Mode and keep All Interfaces selected.Optional: Select the Visitor Mode Service, which defines the protocol and port of client connections to the Security Gateway.
What ports does Check Point VPN use?
UDP Port 259 is used in FWZ encryption to manage the encrypted session (SecuRemote and FireWall-1 to FireWall-1 VPNs). UDP Port 260 and UDP Port 161 are used for the SNMP daemon that Check Point FireWall-1 Provides. TCP Port 262 is used by netsod, which is the Single Sign-on Daemon.
How do I configure site to site VPN in Checkpoint firewall?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
How do I configure site to site VPN in Checkpoint r80?
Getting Started with Site-to-Site VPNCreate the gateway objects in SmartConsole and make sure that IPsec VPN is enabled on each one.Generate internal CA certificates for each gateway (done automatically).Create the VPN Community.Define the VPN Domain.More items...
How do you open checkpoint endpoint security?
Right-click the Endpoint Security icon in your taskbar notification area and select Display Overview. The Endpoint Security Main Page opens.
How do I enable ports in Checkpoint firewall?
Configuring the Check Point Gateway for Port MirroringOpen the VMware Security Gateway.From the command line, run. ... Select Network Connections.Select Configure Connections.Select the interface to configure as the mirror port. ... Select Define as connected to a mirror port.More items...
How do I change my Checkpoint VPN password?
To change your User Center password:Log into the User Center at https://usercenter.checkpoint.com/usercenter/index.jsp.Click "Assets/Info".Click "My Profile" under "My Info" option.Click "Change Password" button.Enter your old password.Enter your new password.Confirm your new password.More items...•
What is a VPN endpoint?
VPN goes between a computer and a network (client-to-server), or a LAN and a network using two routers (server-to-server). Each end of the connection is an VPN "endpoint", the connection between them is a "VPN tunnel".
What is mobile checkpoint VPN?
Check Point Mobile VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using the L3 IPSec/SSL VPN Tunnel. The application is available in the Google Play Store: https://play.google.com/store/apps/details? id=com.checkpoint.VPN&hl=en.
How does Checkpoint endpoint security work?
Endpoint protection works via a combination of network and device-level defenses. At the network level, the organization may restrict access to the enterprise network based on a device's compliance with corporate security policies and least privilege.
How do I find my VPN location?
It's easy to check if yours is giving you this basic level of protection — or if you have a VPN leak.First, identify your actual IP address. ... Turn on your VPN and connect to any server. ... Search “what is my IP” again in Google (or use an IP lookup site) and check the result against your VPN's virtual IP address.
What happens when a remote access client logs on to a domain controller?
When the Remote Access client computer successfully logs on to a domain controller, the user's profile is saved in cache. This cached information will be used if subsequent logons to the domain controller fail, for whatever reason.
How to add domains to a SecuRemote server?
In the General tab, enter a name for the server and select the host on which it runs. In the Domains tab, click Add to add the domains that will be resolved by the server. The Domain window opens, Enter the Domain Suffix for the domain that the SecuRemote DNS server will resolve, for example, checkpoint.com.
Why do we need multiple authentications?
At the same time, these multiple authentications are an effective means of ensuring that the session has not been hijacked (for example, if the user steps away from the client for a period of time).
What mode is used for Endpoint Security VPN?
For Endpoint Security VPN and Check Point Mobile for Windows, use Office mode.
Can you have multiple SecuRemote DNS servers?
You can configure multiple SecuRemote DNS servers for different domains.
Can you cache multiple passwords?
Password caching is possible only for multiple-use passwords. If the user's authentication scheme implement one-time passwords (for example, SecurID), then passwords cannot be cached, and the user will be asked to re-authenticate when the authentication time-out expires. For these schemes, this feature should not be implemented.
Is split DNS enabled?
Split DNS is automatically enabled. On Endpoint Security VPN and Check Point Mobile for Windows, you can edit a parameter in the trac_client_1.ttm configuration file to set if Split DNS is enabled, disabled, or depends on the client settings.
What is a remote access VPN community?
By default, the Remote Access VPN Community includes a user group, All Users, that includes all defined users. You can use this group or add different user groups to the Remote Access VPN Community. The community can contain users defined in LDAP, which includes Active Directory, or users defined on the Security Management Server.
Which service defines the protocol and port of client connections to the gateway?
Optional - Select the Visitor Mode Service, which defines the protocol and port of client connections to the gateway.
How to enable IPsec VPN?
From SmartConsole, use the Gateways & Servers menu to configure the gateway and blades. Double-click the gateway. The Check Point Gateway window opens. In the Network Security tab at the bottom, select I Psec VPN to enable the blade.
What happens when no authentication methods are defined for the gateway?
If no authentication methods are defined for the gateway, users select an authentication method from the client.
Does any VPN rule apply to all VPN communities?
Any - The rules applies to all VPN Communities. If you configure a new VPN Community after the rule was created, the rule also applies to the new VPN Community. One or more specified VPN communities - For example, RemoteAccess. Right-click in the VPN column of a rule and select Specific VPN Communities.
Do you need to authenticate to a VPN gateway?
Users must authenticate to the VPN gateway with a supported authentication method. You can configure authentication methods for the remote access gateway in:
Background
For the safety of their organizations, and to help stop the spread of COVID-19/Coronavirus, our customers have moved all non-essential employees to work from home.
Configure Check Point VPN Clients to split tunnel Office 365 traffic
1. Open SmartConsole and go to Global Properties > Remote Access > Endpoint Connect.
Additional References
This solution has been verified for the specific scenario, described by the combination of Product, Version and Symptoms. It may not work in other scenarios.
What is remote access client?
Remote Access Clients Selective Routing lets you define different encryption domains for each VPN site-to- site community and Remote Access (RA) Community. You must have a VPN domain configured. The domain includes participating Security Gateways.
What is location awareness remote access?
Location Awareness Remote Access Clients intelligently detects if it is in the VPN domain (Enterprise LAN), and automatically connects or disconnects as required. If the client senses that it is in the internal network, the VPN connection is terminated. In Always-Connect mode, the VPN connection is established whenever the client exits the internal network.
What is PKCS#12 certificate?
Remote Access Clients support user authentication through PKCS#12 certificates. A PKCS#12 certificate can be accessed directly when stored as a .p12 file or imported to the CAPI store.
What port is WebUI on?
If Visitor mode is configured on port 443 and WebUI is enabled on the gateway, the WebUI must listen on a port other than 443. Otherwise, Remote Access Clients cannot connect.
What is extended DHCP parameter?
Extended DHCP ParametersWhen using Office Mode from a DHCP server, the Remote Access Clients gateway sends data that it got from the client to the DHCP server in the correct format - Hostname, FQDN, Vendor Class, and User Class.
Is Checkpoint a continuous effort?
Check Point is engaged in a continuous effort to improve its documentation. Please help us by sending your comments (mailto:cp_techpub_feedback@checkpoint.com?subject=Feedback on Remote Access Clients for Windows 32-bit/64-bit E75.10 Administration Guide).
Can you create a remote access package?
You can create packages of the Remote Access Clients with pre-defined settings, such as which client to install, a VPN site and authentication methods. When you deploy the package to users, it is easier for them to connect quickly.
What is location awareness remote access?
Location Awareness Remote Access Clients intelligently detects if it is in the VPN domain (Enterprise LAN), and automatically connects or disconnects as required. If the client senses that it is in the internal network, the VPN connection is terminated. In Always-Connect mode, the VPN connection is established whenever the client exits the internal network.
What is policy server?
The Policy Server functionality in a gateway is the Desktop Security Policy management. If you do not enable a Policy Server, the Desktop rule base and the SCV checks will not be applied.
What is proxy detection?
Proxy DetectionProxy servers between the client and the gateway are automatically detected and authenticated to if necessary
When do clients get upgrade packages?
Clients can automatically get an upgrade package when they connect to the gateway.
Is Checkpoint a continuous effort?
Check Point is engaged in a continuous effort to improve its documentation. Please help us by sending your comments (mailto:cp_techpub_feedback@checkpoint.com?subject=Feedback on Remote Access Clients for Windows 32-bit/64-bit E75.20 Administration Guide).
Can you create a predefined client installation package?
You can create a predefined client installation package for easy provisioning.