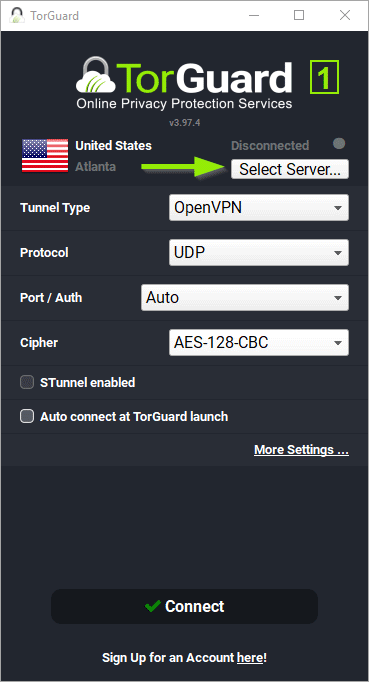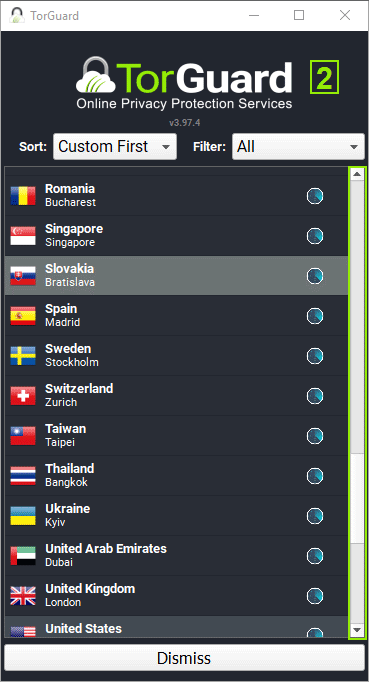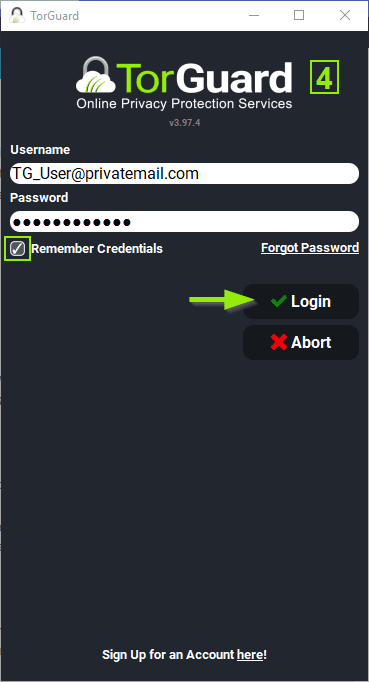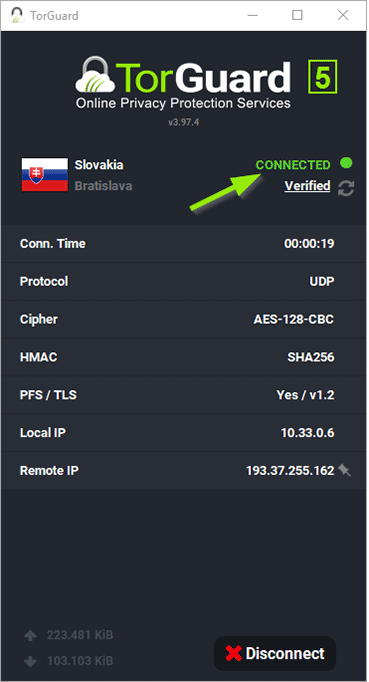
What are endpoint security remote access VPN clients?
Starting from Endpoint Security E80.41, Remote Access VPN Clients are part of the Endpoint Security offering, providing the next release of E75.30, including all flavors. The E75 Remote Access Clients series was previously known as Endpoint Security VPN R75.
Does the check point desktop firewall work with Endpoint Security VPN clients?
Note- The Check Point Desktop Firewall works with the Endpoint Security VPN client. It does not work with SecuRemote or Check Point Mobile for Windows. Configuring Client Features Remote Access Clients for Windows 32/64-bit Administration Guide E75.30 | 50
Can I upgrade securemote to Endpoint Security VPN or check point mobile?
Remote Access Clients for Windows 32/64-bit Administration Guide E75.30 | 15 Environments with SecureClient already deployed can be easily upgraded to Endpoint Security VPN or Check Point Mobile for Windows. Clients who had SecuRemote client can use the same steps to upgrade to SecuRemote E75.30.
How does remote access work with Check Point?
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser. Provides full access to the corporate network with a VPN client. Provides web-based access without the need to install a VPN client.

Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
What is remote access client?
Remote Access Clients provide a simple and secure way for endpoints to connect remotely to corporate resources over the Internet, through a VPN tunnel. Check Point offers 3 enterprise-grade flavors of Remote Access to fit a wide variety of organizational needs.
What is a certificate in remote access?
certificate is a digital ID card. It is issued by a trusted third party known as a Certification Authority (CA). Remote Access Clients can use the digital certificates issued by the gateway, which has its own Internal Certificate Authority (ICA). A digital certificate has:
What is a key fob?
key fob is a small hardware device with built-in authentication mechanisms that control access to network services and information. While a password can be stolen without the owner realizing it, a missing key fob is immediately apparent. Key fobs provide the same two-factor authentication as other SecurID devices. The user has a personal identification number (PIN), which authenticates that person as the owner of the device; after the user enters the correct PIN, the device displays a number which allows the user to log on to the network. The SecurID SID700 key fob is a typical example of such a device.
What is RSA SecurID?
The RSA SecurID authentication mechanism consists of either hardware (FOB, USB token) or software (softID) that generates an authentication code at fixed intervals (usually one minute), with a built-in clock and encoded random key.
What is policy server?
The Policy Server functionality in a gateway is the Desktop Security Policy management. If you do not enable a Policy Server, the Desktop rule base and the SCV checks will not be applied.
What is PKCS#12 certificate?
Remote Access Clients support user authentication through PKCS#12 certificates. A PKCS#12 certificate can be accessed directly when stored as a .p12 file or imported to the CAPI store.
Do gateways have to belong to the same VPN domain?
For implicit MEP (the method used by SecureClient), the gateways have to belong to the same VPN domain for MEP to function. For Remote Access Clients , if they are configured with Manual MEP , the gateways do not have to belong to the same VPN domain. Configure the TTM file of each gateway.
Why do I need to authenticate with PKCS#12?
For security reasons, your system administrator might require you to authenticate directly with the PKCS#12 certificate and not from the certificate stored in the CAPI. For example, if you use several desktop workstations and laptops, you might not want to leave your certificate on different computers. If the PKCS#12 certificate is in the CAPI store and someone steals your laptop, they can use the client to connect to the site. For increased security, your administrator might instruct you to save the PKCS#12 certificate to a USB stick or other storage device.
What is SAA in remote access?
Secure Authentication API (SAA) lets you use third- party authentication technologies with your Remote Access client. To work, it requires a DLL file that is installed on your client.
What is RSA SecurID?
The RSA SecurID authentication mechanism consists of either hardware (FOB, USB token) or software (softID) that generates an authentication code at fixed intervals (usually one minute), with a built-in clock and encoded random key.
Does VPN compliance work in the background?
The compliance check always works in the background, if you are connected to the VPN or not. At any time it can report that your computer has failed a check and is not compliant.
Can a client find a proxy?
If you are at a remote site which has a proxy server, the client must be configured to go through the proxy server. Usually the client can find proxy settings automatically. If not, you can configure it.
Additional Requirements
Remote Access Clients cannot be installed on the same device as Check Point Endpoint Security R73 or E80. If ZoneAlarm is installed on a device, you can install Check Point Mobile for Windows and SecuRemote but not Endpoint Security VPN.
Remote Access Clients Installation for Windows
You can create packages of the Remote Access Clients with pre-defined settings, such as which client to install, a VPN site and authentication methods. When you deploy the package to users, it is easier for them to connect quickly.
Supported Upgrades for Remote Access client VPN Client for ATMs
Upgrade to E83.00 Remote Access client VPN client for ATMs is available from: