How does remote access work with Check Point?
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser. Provides full access to the corporate network with a VPN client. Provides web-based access without the need to install a VPN client.
What are remote access clients?
Introduction to Remote Access Clients. Remote Access Clients provide a simple and secure way for endpoints to connect remotely to corporate resources over the Internet, through a VPN tunnel. Check Point offers 3 enterprise-grade flavors of Remote Access to fit a wide variety of organizational needs.
What is check point IPsec VPN?
Check Point Mobile for Windows - An easy to use IPsec VPN client to connect securely to corporate resources. Together with the Check Point Mobile clients for iPhone and Android, and the Check Point SSL VPN portal, this client offers a simple experience that is primarily targeted for non-managed machines.
How does check point ensure privacy and integrity of sensitive information?
Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data. Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.

How do I configure Checkpoint VPN client?
Go to VPN > Authentication Servers. Click Configure to add a RADIUS server. See Configuring Remote Access Authentication Servers. Click permissions for RADIUS users to set access permissions....Configuring Remote Access VPNCheck Point VPN clients.Check Point Mobile clients.Check Point SSL VPN.L2TP VPN client.
How do I configure site to site VPN in Checkpoint firewall?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
What is remote access VPN checkpoint?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
How do I check VPN logs in checkpoints?
To collect client logs: Right-click on 'the client icon > Display Overview - Remote Access VPN > Manage settings > Advanced > collect logs' and click "Close".
How do I troubleshoot my VPN checkpoint?
Things to look for when troubleshooting a Checkpoint VPN connection:VPN domains. Review setup in the topology of an item. ... Encryption Domains. Your firewall contains your networks. ... Rule Setup. ... Pre-shared secret or certificate. ... RuleSet. ... Address Translation. ... TRADITIONAL MODE NOTES. ... SIMPLIFIED MODE NOTES.More items...•
How do I configure site to site VPN on Checkpoint Firewall r77?
16:2329:45Site to Site VPN Configuration - Check Point Gaia R77.30 - YouTubeYouTubeStart of suggested clipEnd of suggested clipWe need to go to the topology. Create the external interface manually. Ok the IP address is 192 168MoreWe need to go to the topology. Create the external interface manually. Ok the IP address is 192 168 1 dot 100 mask 24 bits ok and we need to define the interface.
How does Checkpoint endpoint security work?
Endpoint protection works via a combination of network and device-level defenses. At the network level, the organization may restrict access to the enterprise network based on a device's compliance with corporate security policies and least privilege.
Who makes Checkpoint VPN?
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks.
What is remote secure access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
How do I monitor VPN tunnel?
The VPN monitoring device must be set to the VPN-monitor option so that endpoint IP addresses using the VPN tunnel can be monitored. Pings are sent only when there is outgoing traffic and no incoming traffic through the VPN tunnel. The tunnel is deemed active if it detects incoming traffic through the VPN tunnel.
Where are checkpoint logs stored?
Logs can be stored on a: Management Server that receives logs from the managed Security Gateways / Clusters. This is the default. Log Server.
How do I make IPsec VPN in checkpoint?
Define the Network Object(s) of the Security Gateways that are internally managed. In the General Properties page of the Security Gateway object, in the Network Security tab, select IPsec VPN. In the Network Management page, define the Topology. In the Network Management > VPN Domain page, define the VPN Domain.
What is site to site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
What is a VPN encryption domain?
In domain based VPN, traffic is encrypted when it originates in one encryption domain and is transmitted to a different domain. The local encryption domain defines: The internal networks that encrypted traffic from remote sites and networks can get access.
What is remote access client?
Remote Access Clients Selective Routing lets you define different encryption domains for each VPN site-to- site community and Remote Access (RA) Community. You must have a VPN domain configured. The domain includes participating Security Gateways.
What is location awareness remote access?
Location Awareness Remote Access Clients intelligently detects if it is in the VPN domain (Enterprise LAN), and automatically connects or disconnects as required. If the client senses that it is in the internal network, the VPN connection is terminated. In Always-Connect mode, the VPN connection is established whenever the client exits the internal network.
What is SCV policy?
The SCV policy inspects elements of the client configuration, and returns the compliance status of the client. During installation, Remote Access Clients register their SCV DLLs as SCV plug-ins in the system registry.
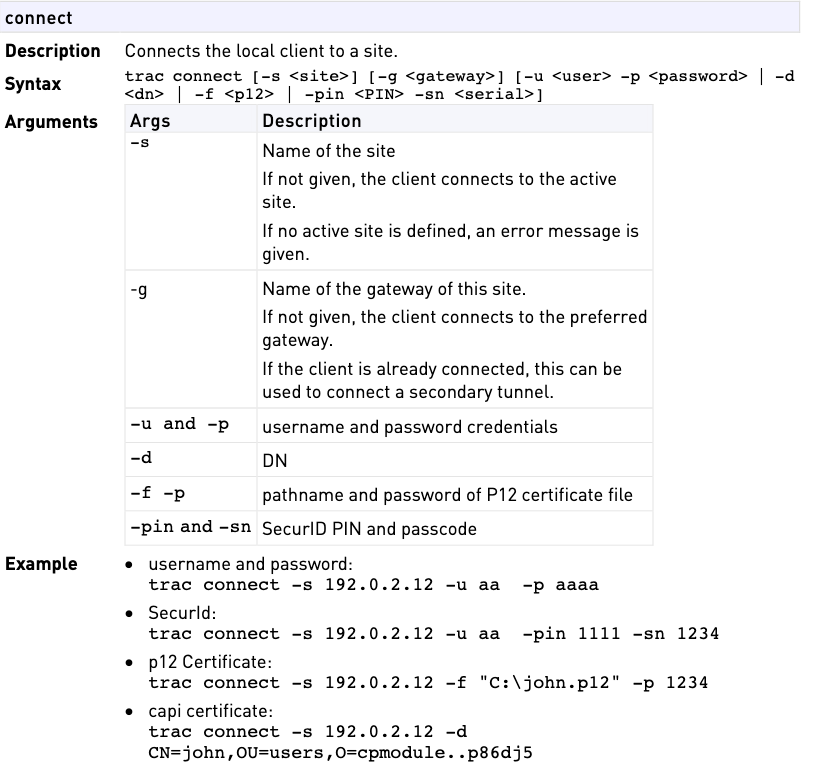
What is PKCS#12 certificate?
Remote Access Clients support user authentication through PKCS#12 certificates. A PKCS#12 certificate can be accessed directly when stored as a .p12 file or imported to the CAPI store.
What is SAA authentication?
Secure Authentication API (SAA) lets you use third- party authentication technologies with Remote Access Clients. When you configure SAA for a site, users authenticate to the site with an authentication scheme specific to your organization. For example, if your organization uses biometric authentication, users can use the same biometric authentication to authenticate to the site.
What is extended DHCP parameter?
Extended DHCP ParametersWhen using Office Mode from a DHCP server, the Remote Access Clients gateway sends data that it got from the client to the DHCP server in the correct format - Hostname, FQDN, Vendor Class, and User Class.
Is Checkpoint a continuous effort?
Check Point is engaged in a continuous effort to improve its documentation. Please help us by sending your comments (mailto:cp_techpub_feedback@checkpoint.com?subject=Feedback on Remote Access Clients for Windows 32-bit/64-bit E75.10 Administration Guide).
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
What is SCV in VPN?
Compliance Policy - Secure Configuration Verification (SCV) SCV monitors the configuration of remote computers, to confirm that the configuration complies with organization Security Policy, and the gateway blocks connectivity for computers that do not comply. It is available in Endpoint Security VPN and Check Point Mobile for Windows.
What is VPN firewall?
Desktop FirewallEndpoint Security VPN enforces a Desktop Firewall on remote clients. The administrator defines the Desktop Security Policy in the form of a Rule Base. Rules can be assigned to either specific user groups or all users; this permits the definition of flexible policies.
What is a MEP gateway?
Multiple Entry PointProvides a gateway High Availability and Load Sharing solution for VPN connections. For Remote Access Clients, in an environment with MEP, more than one gateway protects and gives access to the same VPN domain. MEP lets the Remote Access Clients connect to the VPN from multiple gateways.
What is location awareness remote access?
Location Awareness Remote Access Clients intelligently detects if it is in the VPN domain (Enterprise LAN), and automatically connects or disconnects as required. If the client senses that it is in the internal network, the VPN connection is terminated. In Always-Connect mode, the VPN connection is established whenever the client exits the internal network.
What is policy server?
The Policy Server functionality in a gateway is the Desktop Security Policy management. If you do not enable a Policy Server, the Desktop rule base and the SCV checks will not be applied.
What is proxy detection?
Proxy DetectionProxy servers between the client and the gateway are automatically detected and authenticated to if necessary
How long does it take to renew an IP address?
If the IP lease duration time is set to 60 minutes, a renewal request is sent after 30 minutes. If a renewal is given, the client will request a renewal again after 30 minutes. If the renewal fails, the client attempts again after half of the remaining time, for example, 15 minutes, then 7.5 minutes, and so on. If no renewal is given and the 60 minutes of the lease duration times out, the tunnel link terminates. To renew the connection the remote user must reconnect to the Security Gateway. Upon reconnection, an IKE renegotiation is initiated and a new tunnel created.
What is a smart console?
The SmartConsole for Endpoint Security Server allows the Administrator to connect to the Endpoint Security Server and to manage the new Endpoint Security Software Blades.
What is zero phishing?
Zero Phishing - Improved resilience for networking issues that may cause the site to not respond in the first scan.
What is backup optimization?
Backup - Optimizations of the backup database size for performance improvements.
Do you need endpoint security server for stand alone?
Note: These Standalone clients do not require Endpoint Security Server installation as part of their deployment.
When are forensic reports correctly displayed?
Forensics reports are now correctly displayed when there is an Anti-Exploit detection.
When is SK171213 no longer supported?
Important: This version is no longer supported and is expired as of 1-Jan-2021. Follow instructions in sk171213
