How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
How to unlock checkpoint admin account?
How to Unlock Checkpoint Admin Account? Use below command to see locked admin. Use -u to unlock specific admin or -ua for all. fwm lock_admin -v // View locked admins fwm lock_admin -u <admin> // Unlock a specific admin fwm lock_admin -ua // Unlock all admins.
How to lock down TeamViewer for more secure remote access?
- access to your authenticator. Security: easy access, strong passwords and whitelists
- Our next stop is the security section. Select "Security" on the left panel. ...
- Some people prefer to manually set a very reliable password for their computer (and not rely on the randomly generated, which TeamViewer uses by default). ...
How to access a remote disk?
- IN THIS TASK
- Summary. This step-by-step article describes how to gain access to local files when you are using a Remote Desktop session to a Windows XP or Windows Server 2003 host computer.
- References

How do I connect to Checkpoint VPN?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
Is checkpoint a VPN?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
How does Checkpoint VPN Work?
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels.
What is mobile checkpoint VPN?
Check Point Mobile VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using the L3 IPSec/SSL VPN Tunnel. The application is available in the Google Play Store: https://play.google.com/store/apps/details? id=com.checkpoint.VPN&hl=en.
What is remote access VPN Check Point?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
What is the difference between site to site VPN and remote access VPNS?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What are the 3 types of VPN?
VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
What are 2 types of VPN?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
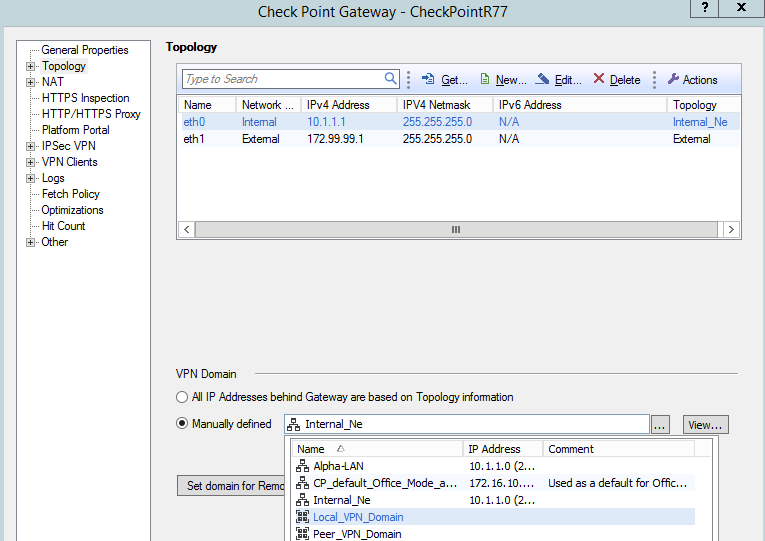
How do you create a route based VPN in Check Point?
Note: Route-based VPN requires an empty group (Simple Group), created and assigned as the VPN Domain.Go to "Manage" menu - click on "Network Objects...".Select the Check Point Gateway, and click on "Edit".Go to "Topology".In the "VPN Domain" section, select "Manually defined".More items...•
How do I use checkpoint mobile VPN?
0:1010:30Check Point Remote Access VPN Setup and Config - YouTubeYouTubeStart of suggested clipEnd of suggested clipNow as i mentioned it's really easy and simple to set up the vpn. There's a little tab on the leftMoreNow as i mentioned it's really easy and simple to set up the vpn. There's a little tab on the left hand side which says vpn. And then you're left with three sections. Which is remote.
What is Check Point mobile Access?
Check Point Mobile Access is the safe and easy solution to securely connect to corporate applications over the Internet with your Smartphone, tablet or personal computer (PC). Mobile Access allows remote and mobile workers to simply and securely connect to email, calendar, contacts and corporate applications.
Who makes Checkpoint VPN?
Check Point Software Technologies Ltd. For the last three decades, Check Point Software Technologies Ltd. (www.checkpoint.com) has set the standard for Cyber Security.
Is Cisco secure endpoint a VPN?
It not only provides VPN access through Secure Sockets Layer (SSL) and IPsec IKEv2 but also offers enhanced security through various built-in modules.
What is a VPN endpoint?
VPN goes between a computer and a network (client-to-server), or a LAN and a network using two routers (server-to-server). Each end of the connection is an VPN "endpoint", the connection between them is a "VPN tunnel".
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
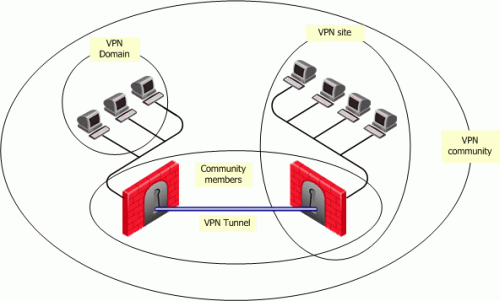
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
The Remote Access Workflow
Use the Gateways & Servers menu to configure the gateway and enable blades.
Examples of VPN Access Rules for Remote Access
This rule allows traffic from all VPN Communities to the internal network on all services:
Basic Gateway Configuration
As a best practice, use these gateway settings for most remote access clients. See the documentation for your client for more details.
Including Users in the Remote Access Community
By default, the Remote Access VPN Community includes a user group, All Users, that includes all defined users. You can use this group or add different user groups to the Remote Access VPN Community. The community can contain users defined in LDAP, which includes Active Directory, or users defined on the Security Management Server.
Configuring User Authentication
Users must authenticate to the VPN gateway with a supported authentication method. You can configure authentication methods for the remote access gateway in:
Examples of VPN Access Rules for Remote Access
This rule allows traffic from all VPN Communities to the internal network on all services:
Deploying Remote Access Clients
See the documentation for your remote access client for deployment instructions.
Configuring Remote Access Policy
Configure Remote Access VPN policy in the Unified Access Control Policy Rule Base.
Defining Access Control Rules
Access control is a layer of security not connected with VPN. When there is a Remote Access Community, it does not mean that members of that community have free, automatic access to the network. Security rules have to be created in the Access Control Policy Rule Base blocking or allowing specific services.
Access Roles for Remote Access
For Security Gateways R80.10 and higher, create Access Roles for Remote Access and VPN Clients to include them in rules in the Access Control Rule Base. This applies to Mobile Access and IPsec clients. When an Access Role for a client is in the Source column of a rule, the rule applies to traffic that originates from that client.
Policy Definition for Remote Access
There must be a rule in the Security Policy Rule Base that grants remote users access to the LAN. Consider which services are allowed. Restrict those services that need to be restricted with an explicit rule in the Security Policy Rule Base.
Modifying Encryption Properties for Remote Access VPN
The encryption properties of the users participating in a Remote Access community are set by default. If you must modify the encryption algorithm, the data integrity method and/or the Diffie-Hellman group, you can either do this globally for all users or configure the properties per user.
Installing the Policy
Install the policy and instruct the users to create or update the site topology.
IPsec and IKE for Remote Access
For Remote users, the IKE settings are configured in Global Properties > Remote Access > VPN Authentication and Encryption.