From the Check Point Gateway tree, click Network Management. In VPN Domain, click Set domain for Remote Access Community. Configure Visitor Mode. Select IPSec
IPsec
Internet Protocol Security (IPsec) is a protocol suite for secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. IPsec includes protocols for establishing mutual authentication between agents at the beginning …
- From the Check Point Gateway tree, click Network Management. The default is All IP Addresses behind Gateway are based on Topology information.
- You can change the VPN domain. Click Set domain for Remote Access Community.
How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
How to speed up VPN remote access?
How to speed up a VPN
- Choose another server. Connecting to your nearest server will usually offer the best performance, but there are occasional exceptions.
- Refresh your system. If speeds are notably worse than unusual with several servers, the problem could be closer to home. ...
- Switch protocol. ...
- Tweak protocol settings. ...
- Use a wired connection. ...
- Try split tunneling. ...
How do access remote network with OpenVPN?
Using OpenVPN to Securely Access Your Network Remotely
- Visit http://tplinkwifi.net, and log in with your TP-Link ID or the password you set for the router.
- Go to Advanced > VPN Server > OpenVPN, select the checkbox to enable VPN Server.
- Select the Service Type (communication protocol) for OpenVPN Server: UDP, TCP.
How to activate open VPN?
- Right-click the Start button.
- Click Settings. Source: Windows Central
- Click Network & Internet.
- Click VPN. Source: Windows Central
- Click Add a VPN connection.
- Click the dropdown menu below VPN provider. Source: Windows Central
- Click Windows (built-in).
- Click the Connection name field. ...
- Type a name for the VPN connection. ...
- Click the Server name or address field. ...
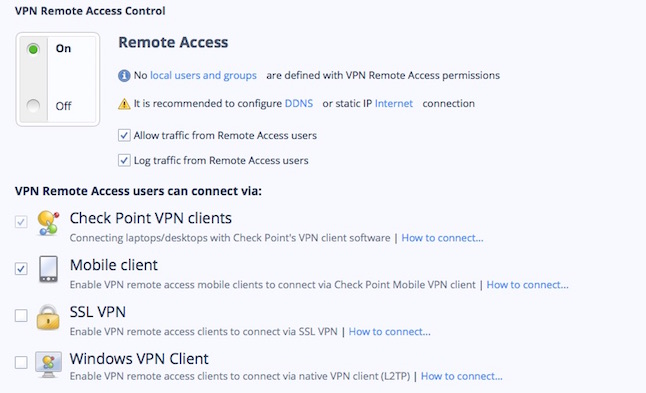
What is VPN domain checkpoint?
Overview of Domain-based VPN Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. or in the VPN routing configuration files on the Security Gateways.
How do I connect to Checkpoint VPN?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
Can I use a VPN for remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How do I create a site to site VPN in checkpoint?
0:0717:26How to Configure Site to Site VPN in Checkpoint Firewall? - YouTubeYouTubeStart of suggested clipEnd of suggested clipHello friends today we will see side to side ppm on firewalls welcome to this video. As you can seeMoreHello friends today we will see side to side ppm on firewalls welcome to this video. As you can see on the screen we'll be doing a vpn between c gcp one and cp2 these are basically two sides which has
What is the difference between site-to-site VPN and remote access VPNs?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does Check Point VPN Work?
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
Which is better VPN or RDP?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Is VPN safer than RDP?
The essential difference when comparing VPNs and RDP is that a VPN doesn't provide your device with any additional functionality the way an RDP does. You're still using the same old device, only that its IP address has changed and it is now a whole lot more secure when accessing the Internet.
How do I create a site to site VPN in CheckPoint r80 20?
0:2723:04Checkpoint R80.20 Training -IPSEC site to site Lab - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd put those firewall put firewall 1 and firewall 2 in that community okay the third step is toMoreAnd put those firewall put firewall 1 and firewall 2 in that community okay the third step is to edit okay the third step is to specify which all are our protected internal networks.
How do I configure site to site VPN on CheckPoint Firewall r77?
16:2329:45Site to Site VPN Configuration - Check Point Gaia R77.30 - YouTubeYouTubeStart of suggested clipEnd of suggested clipWe need to go to the topology. Create the external interface manually. Ok the IP address is 192 168MoreWe need to go to the topology. Create the external interface manually. Ok the IP address is 192 168 1 dot 100 mask 24 bits ok and we need to define the interface.
What is site to site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
Is Check Point a VPN?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
How do I update my Check Point VPN?
Instructions for UserValidate if your Check Point VPN/EndPoint Client version is one of the following: ... If your client version is: Check Point Endpoint VPN E80. ... Reboot your machine.Click on EPPatcher_for_users.exe to install the patch. ... Within a few seconds you will get “Fix has been successfully deployed” pop-up.
What is site to site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
How to enable IPsec VPN?
From SmartConsole, use the Gateways & Servers menu to configure the gateway and blades. Double-click the gateway. The Check Point Gateway window opens. In the Network Security tab at the bottom, select I Psec VPN to enable the blade.
Does any VPN rule apply to all VPN communities?
Any - The rules applies to all VPN Communities. If you configure a new VPN Community after the rule was created, the rule also applies to the new VPN Community. One or more specified VPN communities - For example, RemoteAccess. Right-click in the VPN column of a rule and select Specific VPN Communities.
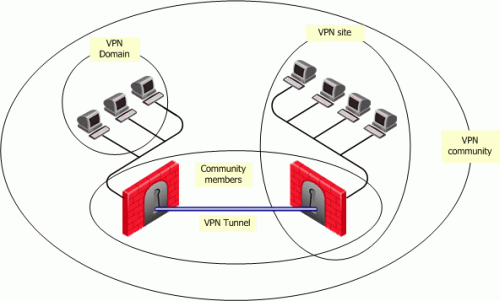
Overview of Domain -based VPN
Domain Based VPN controls how VPN traffic is routed between Security Gateways within a community. To route traffic to a host behind a Security Gateway, you must first define the VPN domain for that Security Gateway. Configuration for VPN routing is done with SmartConsole or in the VPN routing configuration files on the Security Gateways.
VPN Routing and Access Control
VPN routing connections are subject to the same access control rules as any other connection. If VPN routing is correctly configured but a Security Policy rule exists that does not allow the connection, the connection is dropped.
Configuring VPN Routing in Domain Based VPN
Configure most common VPN routing scenarios through a VPN star community in SmartConsole.
The Need for VPN Routing
There are a number of scenarios in which a Security Gateway or remote access clients cannot connect directly to another Security Gateway (or clients). Sometimes, a given Security Gateway or client is incapable of supplying the required level of security. For example:
Check Point Solution for Greater Connectivity and Security
VPN routing provides a way of controlling how VPN traffic is directed. VPN routing can be implemented with Security Gateway modules and remote access clients.
Configuring VPN Routing for Remote Access VPN
Common VPN routing scenarios can be configured through a VPN star community, but not all VPN routing configuration is handled through SmartConsole. VPN routing between Security Gateways (star or mesh) can be also be configured by editing the configuration file $FWDIR/conf/vpn_route.conf
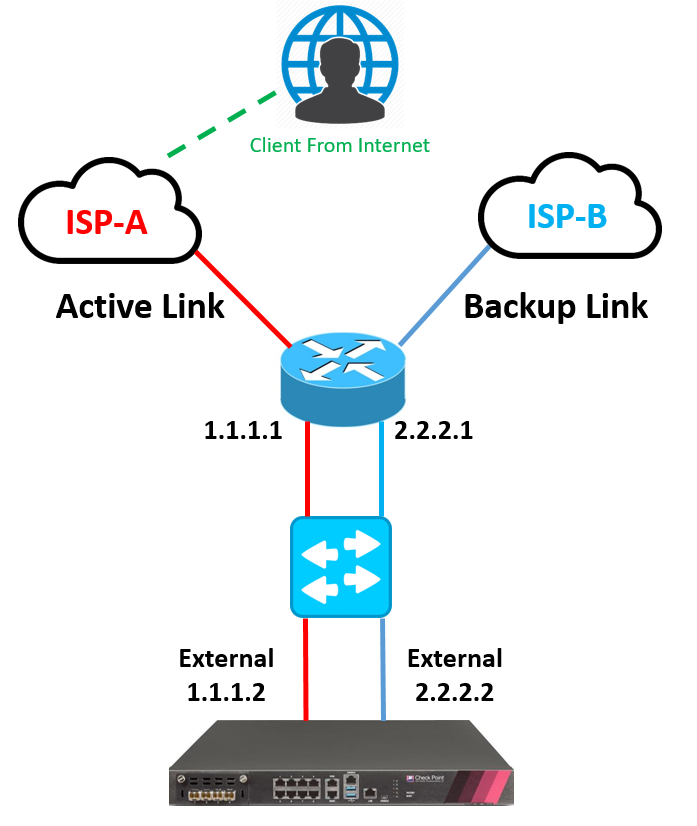
Link Selection for Remote Clients
Link Selection is a method used to determine which interface to use for incoming and outgoing VPN traffic and the best possible path for the traffic. Using Link Selection, you choose which IP addresses are used for VPN traffic on each Security Gateway.
Directional VPN in Remote Access Communities
Directional VPN for Remote Access Communities lets you reject connections to or from a specified network object.
Domain Controller Name Resolution
If clients are configured in Connect Mode and Office Mode, clients automatically resolve the NT domain name using dynamic WINS.
Authentication Timeout and Password Caching
Users consider multiple authentications during the course of a single session to be a nuisance. At the same time, these multiple authentications are an effective means of ensuring that the session has not been hijacked (for example, if the user steps away from the client for a period of time).
Secure Domain Logon (SDL)
When a Remote Access client user logs on to a domain controller, the user has not yet entered credentials and so the connection to the domain controller is not encrypted.
How to Work with non- Check Point Firewalls
If a remote access client is located behind a non- Check Point firewall, the following ports must be opened on the firewall to allow VPN traffic to pass:
Resolving Internal Names with an Internal DNS Server
Remote Access Clients use an internal DNS server to resolve the names of internal hosts (behind the Security Gateway) with non-unique IP addresses.
Split DNS
Split DNS uses a SecuRemote DNS Server, an object that represents an internal DNS server that you can configure to resolve internal names with private IP addresses (RFC 1918). It is best to encrypt the DNS resolution of these internal names.
Overview of Domain-Based Vpn
Vpn Routing and Access Control
- VPN routing connections are subject to the same access control rules as any other connection. If VPN routing is correctly configured but a Security PolicyCollection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. ruleSet of traffic parameters and other conditions in a Rule Base (Security Pol…
Configuring Vpn Routing in Domain Based Vpn
- Configure most common VPN routing scenarios through a VPN star community in SmartConsole. You can also configure VPN routing between Security Gateways in the Security Management ServerDedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Do…