How does remote access work with Check Point?
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser. Provides full access to the corporate network with a VPN client. Provides web-based access without the need to install a VPN client.
What VPN licenses does check point offer?
Check Point offers the following licenses for VPN products: The IPSec VPN Software Blade enables Check Point Security Gateways to allow encrypted traffic to traverse the enforcement point in general. This encrypted traffic passes over Site-to-Site VPN tunnels, as well as, over VPN tunnels established by SecuRemote.
How is the license enforced for Check Point endpoint clients?
This license is enforced based on installed endpoint clients. Both online (actively connected via VPN) and offline (not currently actively connected via VPN) endpoint clients require a license. An Endpoint is defined as a computer instance in the Check Point secured environment.
What is the office mode IP for the check point mobile client?
The Check Point Mobile client offers an Office Mode IP. This client uses the Mobile Access blade license on the gateway itself. By default, a gateway comes with a license for 5 users.
See more

Where is the license for Check Point mobile users installed?
The Check Point Mobile client offers an Office Mode IP. This client uses the Mobile Access blade license on the gateway itself. By default, a gateway comes with a license for 5 users. Then you can attach a larger blade if more users are required.
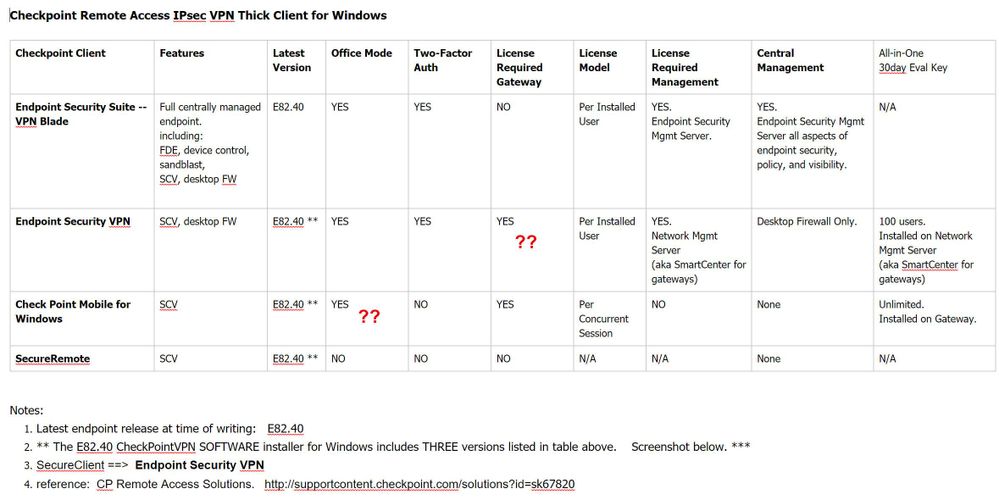
What is Check Point Endpoint Security VPN?
Check Point endpoint security includes data security, network security, advanced threat prevention, forensics, endpoint detection and response (EDR), and remote access VPN solutions.
What is the difference between site to site VPN and remote access VPNs?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Is Check Point a VPN?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
What is a remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Who makes Check Point VPN?
Check Point Software Technologies Ltd. For the last three decades, Check Point Software Technologies Ltd. (www.checkpoint.com) has set the standard for Cyber Security.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
How do I install Check Point VPN?
Installation InstructionsStep 1: Download Checkpoint VPN E84.30. Download and save the VPN client installation file from this link. ... Step 2: Remove currently installed version. To uninstall the currently installed version of Check Point VPN Client: ... Step 3: Install new version.
What is mobile Check Point VPN?
Check Point Mobile VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using the L3 IPSec/SSL VPN Tunnel. The application is available in the Google Play Store: https://play.google.com/store/apps/details? id=com.checkpoint.VPN&hl=en.
How do you create a route based VPN in Check Point?
Note: Route-based VPN requires an empty group (Simple Group), created and assigned as the VPN Domain.Go to "Manage" menu - click on "Network Objects...".Select the Check Point Gateway, and click on "Edit".Go to "Topology".In the "VPN Domain" section, select "Manually defined".More items...•
What is Check Point endpoint Connect?
Endpoint Connect is Check Point's new lightweight remote access client. Providing seamless, secure (IPSec) VPN connectivity to corporate resources, the client works transparently with VPN-1 and Connectra gateways.
What is mobile Check Point VPN?
Check Point Mobile VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using the L3 IPSec/SSL VPN Tunnel. The application is available in the Google Play Store: https://play.google.com/store/apps/details? id=com.checkpoint.VPN&hl=en.
How does Checkpoint Firewall work?
The Check Point firewall will control IP forwarding by enabling it after its services are started. The firewall also loads a default filter during the boot process, which essentially denies all inbound traffic but allows outbound traffic.
How do I uninstall Check Point Endpoint Security VPN?
On the Windows computer, go to the Add or remove programs system setting, select the Endpoint Security, and click Uninstall. A Check Point Endpoint Security challenge-response window opens.
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.