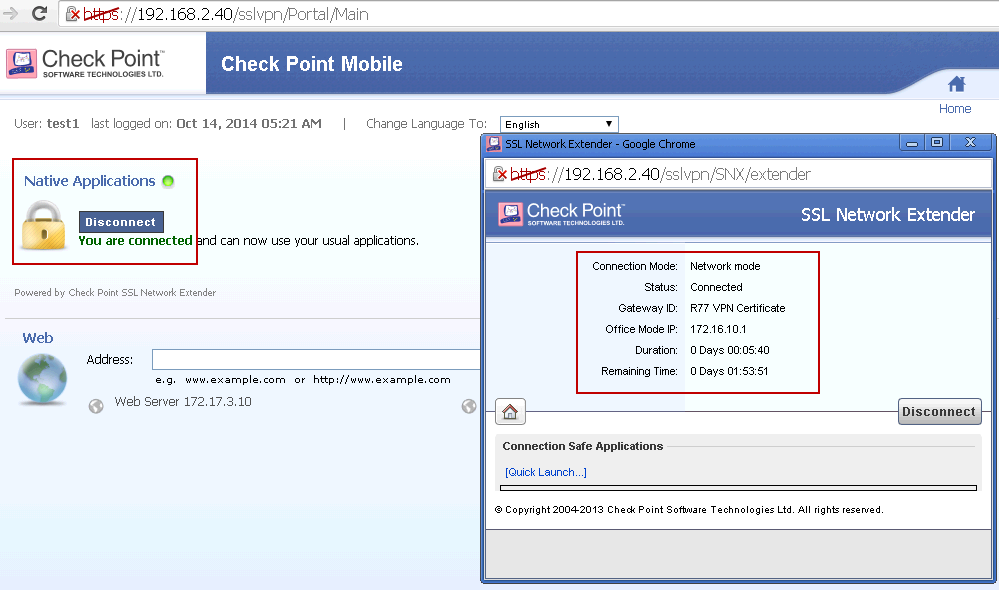
- Step 1. Go to Checkpoint Remote Access Vpn Download website using the links below
- Step 2. Enter your Username and Password and click on Log In
- Step 3. If there are any problems, here are some of our suggestions
Full Answer
How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
How to speed up VPN remote access?
How to speed up a VPN
- Choose another server. Connecting to your nearest server will usually offer the best performance, but there are occasional exceptions.
- Refresh your system. If speeds are notably worse than unusual with several servers, the problem could be closer to home. ...
- Switch protocol. ...
- Tweak protocol settings. ...
- Use a wired connection. ...
- Try split tunneling. ...
How do access remote network with OpenVPN?
Using OpenVPN to Securely Access Your Network Remotely
- Visit http://tplinkwifi.net, and log in with your TP-Link ID or the password you set for the router.
- Go to Advanced > VPN Server > OpenVPN, select the checkbox to enable VPN Server.
- Select the Service Type (communication protocol) for OpenVPN Server: UDP, TCP.
How to activate open VPN?
- Right-click the Start button.
- Click Settings. Source: Windows Central
- Click Network & Internet.
- Click VPN. Source: Windows Central
- Click Add a VPN connection.
- Click the dropdown menu below VPN provider. Source: Windows Central
- Click Windows (built-in).
- Click the Connection name field. ...
- Type a name for the VPN connection. ...
- Click the Server name or address field. ...
See more
How do you troubleshoot a VPN issue in checkpoint?
Things to look for when troubleshooting a Checkpoint VPN connection:VPN domains. Review setup in the topology of an item. ... Encryption Domains. Your firewall contains your networks. ... Rule Setup. ... Pre-shared secret or certificate. ... RuleSet. ... Address Translation. ... TRADITIONAL MODE NOTES. ... SIMPLIFIED MODE NOTES.More items...•
How do I connect to Checkpoint VPN?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What ports does Checkpoint VPN use?
You must change the default remote access port if the Check Point VPN client, Mobile client, or SSL VPN remote access methods are enabled as they use port 443 by default.
What is Checkpoint endpoint Connect?
Endpoint Connect is Check Point's new lightweight remote access client. Providing seamless, secure (IPSec) VPN connectivity to corporate resources, the client works transparently with VPN-1 and Connectra gateways.
What is the difference between site to site VPN and remote access VPNS?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How do I change my Checkpoint VPN password?
To change your User Center password:Log into the User Center at https://usercenter.checkpoint.com/usercenter/index.jsp.Click "Assets/Info".Click "My Profile" under "My Info" option.Click "Change Password" button.Enter your old password.Enter your new password.Confirm your new password.More items...•
How do I configure site to site VPN in Checkpoint r80?
0:0323:04Checkpoint R80.20 Training -IPSEC site to site Lab - YouTubeYouTubeStart of suggested clipEnd of suggested clipFor that you have to follow some steps so that we can configure our ip6 the first step should beMoreFor that you have to follow some steps so that we can configure our ip6 the first step should be enable ipsec on firewall 1 and firewall 2 which you want to perform. Second step is create a vpn.
Is checkpoint a VPN?
VPN-1 is a firewall and VPN product developed by Check Point Software Technologies Ltd. VPN-1 is a stateful firewall which also filters traffic by inspecting the application layer. It was the first commercially available software firewall to use stateful inspection.
How does Checkpoint endpoint security work?
Endpoint protection works via a combination of network and device-level defenses. At the network level, the organization may restrict access to the enterprise network based on a device's compliance with corporate security policies and least privilege.
What is a VPN connection?
A VPN, which stands for virtual private network, is a service that establishes a secure and private connection to the internet. A VPN creates an encrypted tunnel to protect your personal data and communications, hide your IP address, and let you safely use public Wi-Fi networks.
What is a tool for checking dropped packets and reasons?
Another tool we can use is zdebug. This is a tool for checking dropped packets and reasons.#N#Do you wonder why it’s called zdebug? Apparently the person who wrote this program had a name starting with Z.
What happens if GWA does not receive packets?
If GWA does not receive these packets, it will think the tunnel is down. However we could be in a situation where packets from GWA to GWB arrive, but not in the opposite direction (GWB to GWA). We will then see that the tunnel looks to be up from one side, but not the other.
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
What is IPsec path MTU?
IPsec Path MTU is a way of dealing with IPsec packet fragmentation. The Data Link layer imposes an upper limit on the size of the packets that can be sent across the physical network, the Maximum Transmission Unit, or MTU. Before sending a packet, the TCP/IP stack of the operating system queries the local interface to obtain its MTU. The IP layer of the TCP/IP stack compares the MTU of the local interface with the size of the packet and fragments the packet if necessary.
What is passive IPsec PMTU?
Passive IPsec PTMU is a process that occurs when either side receives an ICMP error message resulting from a change in the routing path. Since routes change dynamically on the Internet, if a different router needs to fragment the packet that has the DF bit set, the router discards the packet and generates an ICMP "cannot fragment" error message. The error message is sent to the VPN peer that sent the packet. When the peer receives this error message, the peer decreases the PMTU and retransmits.
How does security gateway and remote peer start the IKE negotiation?
Both Security Gateway and remote peer start the IKE negotiation by proposing a small number of methods for encryption and integrity. The more common methods are included in the small proposals.
What does hide NAT do?
Hide NAT not only changes the IP header but also the port information contained in the UDP header. For example, if the UDP packet is too long, the remote client fragments the packet. The first fragment consists of the IP header plus the UDP header and some portion of the data.
What port is used for visitor mode?
The organization decides that it would like to use a customized port for the Visitor Mode Server other than the typically designated port 443. In this scenario, another port that is mutually agreed upon by all the remote locations and the home organization, can be used for Visitor Mode. This solution works well with business partners; the partner simply agrees to open a port for the visitor Mode connections. If the chosen port is not represented by a pre-defined service in SmartDashboard, this service must be created in order for the port to be used. If a port has been mutually agreed upon, and there is a proxy, configure the proxy to allow traffic destined to this port.
Does VPN have PMTU?
However, the PMTU between the remote client and the Security Gateway will not remain constant, since routing across the Internet is dynamic. The route from Security Gateway to client may not be the same in both directions, hence each direction may have its own PMTU. VPN handles this in two ways: Active IPsec PMTU.
Does the security gateway know the IP address of the NATing device?
If the Security Gateway initiates the connection, the Security Gateway knows the IP address of the NATing device, but cannot supply a port number that translates to the remote client behind the NATing device. (The port number used during previous connections is only temporary, and can quickly change.)