Configuration Procedure Complete these steps to configure the Cisco router as a remote VPN server using SDM. Select Configure > VPN > Easy VPN Server from the Home window and click Launch Easy VPN Server Wizard. AAA must be enabled on the router before the Easy VPN Server configuration starts.
Full Answer
What is the scenario in table 4-1 for Cisco secure VPN?
Table 4-1 lists the physical elements of the scenario. Using Cisco Secure VPN Client software, a remote user can access the corporate headquarters network through a secure IPSec tunnel. Although Cisco IOS VPN gateways support Cisco Secure VPN Client software, this guide does not explain how to configure your gateway for use with it.
How do I Configure my Cisco IOS VPN gateway for virtual-access interfaces?
To configure your Cisco IOS VPN gateway to create virtual-access interfaces from a virtual template for incoming PPTP calls, use the following commands beginning in global configuration mode: Creates the virtual template that is used to clone virtual-access interfaces. Specifies the IP address of the interface the virtual-access interfaces uses.
What is the Cisco secure VPN client software?
Using Cisco Secure VPN Client software, a remote user can access the corporate headquarters network through a secure IPSec tunnel. Although Cisco IOS VPN gateways support Cisco Secure VPN Client software, this guide does not explain how to configure your gateway for use with it.
How to manage remote devices with a VPN?
Remote devices need to be managed through a VPN from the central site when operating on a centralized IT model. VPN devices support numerous configuration options to determine the tunnel endpoint and, depending on the method chosen, these options may impact the manageability of the network.
What is 1800 VPN?
What is site to site IPSEC VPN?
What is the authentication line that you mentioned about?
What is Cisco Secure Endpoint?
Does remote VPN work on 1841 router?
About this website

How do I set up VPN server for remote access?
5 Steps to Setting up a VPNGet a router appropriate for your needs. ... Use the Quick Start Wizard Guide to set up. ... Choose security settings. ... Enable users. ... Connect. ... Solution 1: Static IP Address. ... Solution 2: Register Your Own Name + Dynamic DNS. ... Solution 3: Use A Free Name.More items...
How do I setup a VPN on my Cisco router?
Steps for setting up a VPNStep 1: Line up key VPN components. ... Step 2: Prep devices. ... Step 3: Download and install VPN clients. ... Step 4: Find a setup tutorial. ... Step 5: Log in to the VPN. ... Step 6: Choose VPN protocols. ... Step 7: Troubleshoot. ... Step 8: Fine-tune the connection.
How do I setup a Cisco site to site VPN?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
Can I use a VPN for remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Where is Cisco VPN client configuration file?
Hello, in Windows OS the . pcf files is located at C:\Programs files\Cisco Systems\VPN Client\Profiles.
What is a VPN configuration?
A VPN, or Virtual Private Network, routes all of your internet activity through a secure, encrypted connection, which prevents others from seeing what you're doing online and from where you're doing it. Basically, a VPN provides an extra layer of security and privacy for all of your online activities.
How do I find my VPN connection details?
Open your phone's Settings app.Tap Network & internet. VPN. If you can't find it, search for "VPN." If you still can't find it, get help from your device manufacturer.Tap the VPN you want.Enter your username and password.Tap Connect. If you use a VPN app, the app opens.
What is IPSec configuration?
Internet Protocol Security (IPsec) is a set of security protocols used to transfer IP packets confidentially across the Internet. IPsec is mandatory for all IPv6 implementations and optional for IPv4.
What is IPSec VPN Cisco?
Cisco IPsec Technologies IPsec uses encryption technology to provide data confidentiality, integrity, and authenticity between participating peers in a private network. Cisco provides full Encapsulating Security Payload (ESP) and Authentication Header (AH) support. • Internet Key Exchange (IKE)
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What is the difference between VPN and remote access?
While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer. If you want to have full control over a local computer from a remote location, VPN won't let you achieve that.
How do I enable Cisco Anyconnect VPN through remote desktop?
The steps would be:Log into the ASDM.Go to Configuration, Remote Access VPN, Anyconnect Client Profile.Click Add and create a new profile and choose the Group Policy it should apply to.Click OK, and then at the Profile screen click "Apply" at the bottom (important)More items...•
How do I create a VPN?
Android:Tap the Settings icon.Tap Network & internet.Tap Advanced.Tap VPN.Tap Add.Enter the information including Name, Type, Server Address, Username, and Password.Tap Save.Again, tap the Settings icon.More items...•
What is Cisco Easy VPN?
Easy VPN server-enabled devices allow remote routers to act as Easy VPN Remote nodes. The Cisco Easy VPN client feature can be configured in one of two modes—client mode or network extension mode.
What command to use to verify PPTP?
After you complete a connection, enter the show vpdn tunnel command or the show vpdn session command to verify your PPTP and MPPE configuration.The following example contains typical output:
What is Cisco IOS firewall proxy?
Using the Cisco IOS firewall authentication proxy feature , network administrators can apply specific security policies on a per-user basis. Users can be identified and authorized on the basis of their per-user policy, and access privileges tailored on an individual basis are possible, in contrast with general policy applied across multiple users.
What is VPN on Cisco router?
This chapter explains the basic tasks for configuring an IP-based, remote access Virtual Private Network (VPN) on a Cisco 7200 series router. In the remote access VPN business scenario, a remote user running VPN client software on a PC establishes a connection to the headquarters Cisco 7200 series router.
What is the radiusserverkey command?
Sets the authentication and encryption key for communications between the router and the AAA server. For RADIUS servers use the radiusserverkey command.
What is authentication proxy?
With the authentication proxy feature, users can log into the network or access the Internet via HTTP, and their specific access profiles are automatically retrieved and applied from an authentication server. The user profiles are active only when there is active traffic from the authenticated users.
How to verify that authentication proxy is successfully configured on the router?
To verify that the authentication proxy is successfully configured on the router, ask a user to initiate an HTTP connection through the router. The user must have authentication and authorization configured at the AAA server. If the user authentication is successful, the firewall completes the HTTP connection for the user. If the authentication is unsuccessful, check the access list and the AAA server configurations.
How to display user authentication entries?
Display the user authentication entries using the show ip auth-proxy cache command in privileged EXEC mode. The authentication proxy cache lists the host IP address, the source port number, the timeout value for the authentication proxy, and the state of the connection. If the authentication proxy state is HTTP_ESTAB, the user authentication was successful.
How does IPSec work?
In IPSec tunnel mode, the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPSec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPSec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. Tunnel mode protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the packets passing through the tunnel, even if they are the same as the tunnel endpoints.
What is IPSEC security?
IPSec is a framework of open standards, developed by the Internet Engineering Task Force (IETF), that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer; it uses IKE to handle negotiation of protocols and algorithms based on local policy, and to generate the encryption and authentication keys to be used by IPSec. IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 7200 series routers, or between a security Cisco 7200 series router and a host.
Why use tunneling in GRE?
Tunneling allows for the encryption and the transportation of multiprotocol traffic across the VPN since the tunneled packets appear to the IP network as an IP unicast frame between the tunnel endpoints. If all connectivity must go through the home Cisco 7200 series router , tunnels also enable the use of private network addressing across a service provider's backbone without the need for running the Network Address Translation (NAT) feature.
What is Cisco IOS firewall?
Cisco IOS software provides an extensive set of security features with which you can configure a simple or elaborate firewall, according to your particular requirements. When you configure Cisco IOS firewall features on your Cisco router, you turn your router into an effective, robust firewall.
How does extranet work?
In the extranet scenario, the headquarters and business partner are connected through a secure IPSec tunnel and the business partner is given access only to the headquarters public server to perform various IP-based network tasks, such as placing and managing product orders.
What is Figure 3-1?
Figure 3-1 shows a headquarters network providing a remote office access to the corporate intranet. In this scenario , the headquarters and remote office are connected through a secure GRE tunnel that is established over an IP infrastructure (the Internet). Employees in the remote office are able to access internal, private web pages and perform various IP-based network tasks.
What is tunneling in transport?
Tunneling provides a way to encapsulate packets inside of a transport protocol. Tunneling is implemented as a virtual interface to provide a simple interface for configuration. The tunnel interface is not tied to specific "passenger" or "transport" protocols, but rather, it is an architecture that is designed to provide the services necessary to implement any standard point-to-point encapsulation scheme. Because tunnels are point-to-point links, you must configure a separate tunnel for each link.
What router is used for the branch 1 callout?
The Internet, represented by the cloud. The Headquarters location (callout 1) uses a Cisco 3845 router with these characteristics: The Branch 1 location (callout 8) uses a Cisco 1841 router with these characteristics: The Branch 2 location (callout 9) uses a Cisco 2811 router with these characteristics:
What is DPD in VPN?
DPD —Dead peer detection. An implementation of a client keepalive functionality, to check the availability of the VPN device on the other end of an IPSec tunnel.
How to know if IPSEC is successful?
One of the first indications of successful IPSec negotiation is a message displayed on the Virtual Private Network (VPN) concentrator console. Upon successful IPSec negotiation by the EzVPN clients, a message similar to the following is displayed on the VPN concentrator console, indicating the establishment of crypto connections to the remote EzVPN clients.
What router does Cisco use?
One branch uses a Cisco 2800 series router and employs a network-mode EzVPN client with a serial interface, while another branch uses a Cisco 1800 series router and uses client mode EzVPN with an SHDSL interface.
What is IPSEC security?
IPSec —IP Security. A framework of open standards that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer. IPSec uses IKE to handle the negotiation of protocols and algorithms based on local policy and to generate the encryption and authentication keys to be used by IPSec. IPSec can protect one or more data flows between a pair of hosts, between a pair of security gateways, or between a security gateway and a host.
What is ATM transfer mode?
ATM —Asynchronous Transfer Mode. A connection switching protocol that organizes data into 53-byte cell units, transmitting them via digital signals. Each cell is processed asynchronously (hence the name) relative to the transmission or arrival of other cells within a single message. Cells are also queued before being transmitted in a multiplexing fashion. ATM can be used for many different services, including voice, video, or data.
What is 1800 VPN?
1800 as Easy VPN client eliminates the use of VPN clients at the Remote Network (Brach Office PCs below).
What is site to site IPSEC VPN?
Site to Site IPSec VPN with Dynamic IP Endpoint is typically used when we have a branch sites which obtains a dynamic public IP from the Internet ISP. For example an ADSL connection.One important note is that Site-to-Site VPN with Dynamic remote routers P... view more
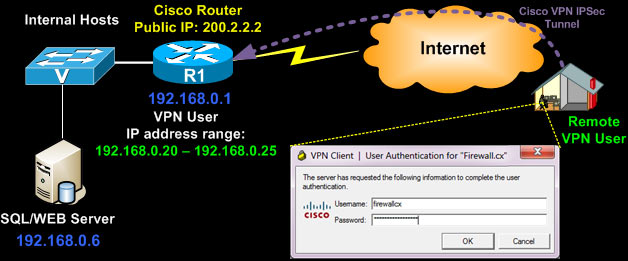
What is the authentication line that you mentioned about?
the authentication line that you mentioned about is to suggest that we are using local database user authentication. if you have an external aaa server like tacacs+ or radius you can specify that instead of local, local is a keyword to suggest local authentication.
What is Cisco Secure Endpoint?
Cisco Secure Endpoint New packages fit for every organization Every Cisco Secure Endpoint (formerly AMP for Endpoints) package comes with Cisco SecureX built-in. It’s our cloud-native platform that integrates all your security solutions into one view wit... view more
Does remote VPN work on 1841 router?
Thk you very much. i got my remote vpn to work on my 1841 router with site to site still working.