The following example shows how to specify the ASA 5505 as an Easy VPN server: hostname (config)# no vpnclient enable hostname (config)# After entering the no version of this command, configure the ASA 5505 as you would any other ASA, beginning with "Getting Started" in the general operations configuration guide.
Full Answer
Why Cisco ASA 5505 is used as border firewall?
A very popular scenario for small networks is to have a Cisco ASA 5505 as border firewall connecting the LAN to the Internet. Administrators in such networks are usually encountered with requests from their users that are not very security conscious.
How to use AnyConnect VPN with Asa?
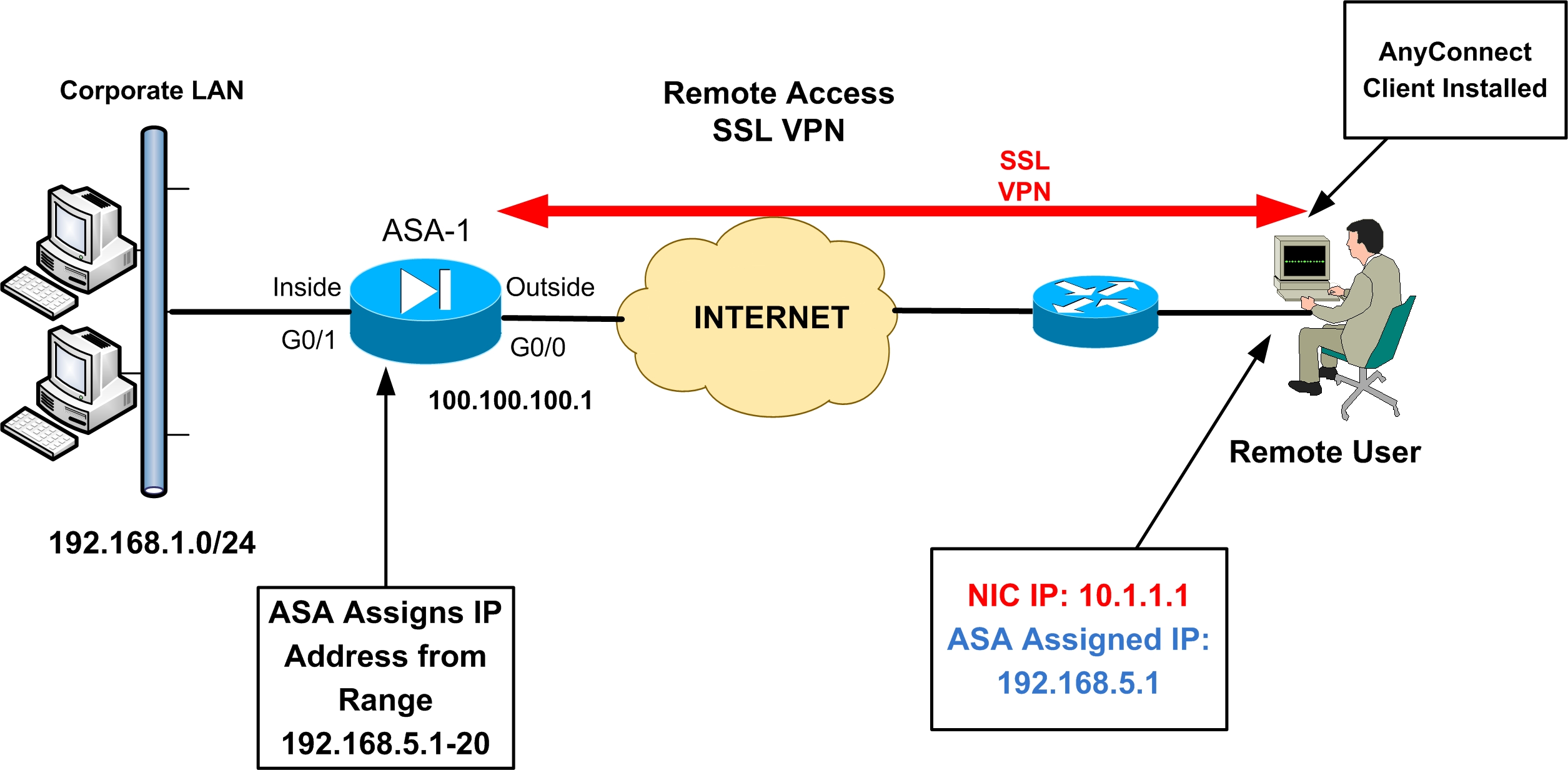
The remote user will open a web browser, enters the IP address of the ASA and then it will automatically download the anyconnect VPN client and establishes the connection. Here’s the topology that we will use:
How does the ASA assign IP addresses to remote users?
The ASA will assign IP addresses to all remote users that connect with the anyconnect VPN client. We’ll configure a pool with IP addresses for this: Remote users will get an IP address from the pool above, we’ll use IP address range 192.168.10.100 – 200.
How to use clientless WebVPN with Asa?
The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, enter the IP address of the ASA and you will get access through a web portal. You only have limited access to a number of applications, for example: There is no full network access when you use clientless WebVPN.
What is Cisco ASA 5505?
The Cisco ASA 5505, operating as an Easy VPN hardware client, supports management access using SSH or HTTPS, with or without a second layer of additional encryption. You can configure the Cisco ASA 5505 to require IPsec encryption within the SSH or HTTPS encryption.
Which interface has the highest security level?
In this scenario, the security appliance builds the tunnel only for vlan1, the interface with the highest security level. If you want to encrypt traffic from vlan12, you must change the security level of interface vlan1 to a lower value than that of vlan 12.
Can Cisco ASA 5505 be used as a VPN?
When configuring the Cisco ASA 5505 as an Easy VPN hardware client, you can specify a tunnel group or trustpoint configured on the Easy VPN server, depending on the Easy VPN server configuration. See the section that names the option you want to use:
Does Easy VPN use UDP?
By default, the Easy VPN hardware client and server encapsulate IPsec in User Datagram Protocol (UDP) packets. Some environments, such as those with certain firewall rules, or NAT and PAT devices, prohibit UDP. To use standard Encapsulating Security Protocol (ESP, Protocol 50) or Internet Key Exchange (IKE, UDP 500) in such environments, you must configure the client and the server to encapsulate IPsec within TCP packets to enable secure tunneling. If your environment allows UDP, however, configuring IPsec over TCP adds unnecessary overhead.
Can Cisco devices be used for authentication?
Devices such as Cisco IP phones, wireless access points, and printers are incapable of performing authentication . Enter the following command in global configuration mode to exempt such devices from authentication, thereby providing network access to them, if individual user authentication is enabled:
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change them but not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
Is transparent mode supported in firewall?
Supported only in routed firewall mode. Transparent mode is not supported.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
What is ASA 5505?
A very popular scenario for small networks is to have a Cisco ASA 5505 as border firewall connecting the LAN to the Internet. Administrators in such networks are usually encountered with requests from their users that are not very security conscious.
Can a remote desktop be attacked by a password?
Remote Desktop machines are very prone to attacks, especially brute- force password attacks. In windows, the administrator account does not get locked-out by default. So a brute force administrator password attack on the RDP server from remote attackers can be successful especially if the administrator password is weak.
Is the IP address of an ASA fixed?
Assume that the ASA receives IP address dynamically from the ISP (via DHCP protocol). So the outside IP of the ASA is not fixed.
Can you create 3 DMZ vlans?
However, companies with limited budget might have purchased a Cisco ASA 5505 with basic license which restricts the creation of a DMZ Vlan (although you can create 3 Vlans, the third Vlan can only communicate with one of the other two Vlans but not both).
What is AnyConnect VPN?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. AnyConnect VPN. The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, ...
When remote users connect to our WebVPN, do they have to use HTTPS?
The following option is not required but useful, whenever someone accesses the ASA through HTTP then they will be redirected to HTTPS:
What happens when a VPN user terminates a session?
Normally when the remote VPN user terminates the session, the anyconnect installer will be uninstalled. The anyconnect keep-installer installed command leaves it installed on the user’s computer.
What happens when you have an inbound access list?
When you have an inbound access-list on the outside interface then all your decrypted traffic from the SSL WebVPN has to match the inbound access-list. You can either create some permit statements for the decrypted traffic or you can just tell the ASA to let this traffic bypass the access-list:
Why does my client tries to download AnyConnect?
The client tries to download the Anyconnect automatically, this is because of the anyconnect ask none default anyconnect command that we used. Since we are using a self-signed certificate you will get the following error message:
What is the IP address of AnyConnect?
You can see that we received IP address 192.168.10.100 (the first IP address from the VPN pool). Anyconnect creates an additional interface, just like the legacy Cisco VPN client does.
What is an ayconnECT_policy?
The group policy is called “ANYCONNECT_POLICY” and it’s an internal group policy which means that we configure it locally on the ASA. An external group policy could be on a RADIUS server.
1. Check Cisco firewall ASA version
Make sure you have ASA 8.2.2 and up. You cannot connect your Windows clients if you have ASA 8.2.1 because of the Cisco software bug.
2. Start Cisco firewall IPsec VPN Wizard
Login to your Cisco firewall ASA5500 ASDM and go to Wizard > IPsec VPN Wizard ... and follow up the screens.
3. Add Transform Set
Go to Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPSec > Crypto Maps. Edit the IPSec rules and add "TRANS_ESP_3DES_SHA" and click "Ok" button.